Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Advancing Wireless Sensor Network Security through the Implementation of Homomorphic Encryption for Secure and Private Image Processing
Authors: Imam Adam Idris, Fadilul-lah Yassaanah issahku
DOI Link: https://doi.org/10.22214/ijraset.2024.58180
Certificate: View Certificate
Abstract
Data security and privacy in image processing are of utmost concern. This paper presents an innovative architecture for integrating Homomorphic Encryption (HE) in Wireless Sensor Networks (WSNs), focusing on enhancing data security and privacy in image processing. Central to this architecture are sensor nodes equipped with Paillier Homomorphic Encryption capabilities, ensuring data confidentiality from the collection point. The network features intermediate aggregator nodes that perform homomorphic computations, such as summing or averaging, on encrypted data, maintaining its confidentiality. The central server, equipped with the private key, decrypts the aggregated data and is pivotal for complex data analyses, ensuring secrecy until the final stage. This architecture, characterized by the implementation of Homomorphic Encryption, allows for secure data encryption at the sensor nodes and its subsequent processing in an encrypted form. The design is bolstered by a robust mathematical framework, enhancing the system\'s security and effectiveness. This approach secures data within WSNs and harnesses the advanced capabilities of Homomorphic Encryption for data privacy and safety throughout the network\'s lifecycle.
Introduction
I. INTRODUCTION
Wireless Sensor Networks (WSNs) have emerged as a pivotal technology for various applications, ranging from environmental monitoring to industrial automation. These networks consist of spatially distributed autonomous sensors that cooperatively monitor physical or environmental conditions, such as temperature, sound, vibration, pressure, motion, or pollutants. They also pass their data through the network to a central location.
The importance of WSNs in data collection and transmission cannot be overstated. They offer a unique blend of flexibility, cost-effectiveness, and ease of deployment, making them ideal for dynamic environments and applications where traditional wired networks are impractical or too expensive.
Recent advancements in WSNs focus on enhancing their efficiency and effectiveness. Chen and Tang (2022) introduced an energy-saving framework for heterogeneous WSNs, utilizing Unmanned Aerial Vehicles (UAVs) to assist in data collection. Their approach dynamically adjusts the working mode of sensor nodes based on their residual energy, optimizing energy thresholds and cluster head selection to minimize energy consumption while ensuring successful data transmission and adhering to UAV trajectory constraints [1].
Similarly, Jiao et al. proposed a novel data collection policy in wireless rechargeable sensor networks. Their strategy involves using a mobile vehicle as a data collector and an energy replenisher. This dual role of the mobile vehicle helps minimize energy consumption and improve data transmission performance, thereby enhancing the overall efficiency of the network [2].
Addressing the challenges of limited energy and unbalanced energy consumption in mobile wireless sensor networks, Yue et al. (2022) developed a path optimization mechanism based on an improved dragonfly optimization algorithm. This method minimizes energy consumption and improves reliability under time-delay constraints, enhancing the network's service quality and reliability [3].
Furthermore, Bilal, Munir, and Alarfaj (2022) contributed to this field by proposing a hybrid clustering and routing algorithm for heterogeneous WSNs.
Their model, which includes threshold-based data collection, aims to reduce unnecessary data transmissions and extend network stability in dense areas [4]. This approach has shown significant improvements in load balancing and end-to-end delay compared to other energy-efficient protocols.
WSNs play a crucial role in modern data collection and transmission, with ongoing research focusing on optimizing their energy efficiency, reliability, and overall performance. These networks are integral to advancing various sectors, including environmental monitoring, healthcare, and industrial automation.
The increasing deployment of Wireless Sensor Networks (WSNs) in sensitive domains such as surveillance, military operations, healthcare, and environmental monitoring underscores the critical need for secure image processing. In these applications, WSNs capture and transmit images, often containing sensitive information, necessitating stringent security measures during processing and transmission [5].
The primary concern in secure image processing within WSNs is safeguarding privacy and confidentiality. Particularly in healthcare and surveillance, the images captured by sensor nodes may contain private information. Protecting this data from unauthorized access is essential to maintain individual privacy and the confidentiality of sensitive information. Furthermore, the integrity of image data is crucial, especially in applications like military surveillance or environmental monitoring, where the authenticity and accuracy of data are paramount. Secure image processing mechanisms play a vital role in ensuring data integrity preventing tampering and alteration of the data [6].
Another critical aspect of secure image processing in WSNs is protecting against cyber attacks, including interception, tampering, and spoofing. Implementing robust encryption and other security measures is vital to shield the network from these threats, ensuring the secure transmission of images from sensor nodes to the base station. Moreover, compliance with stringent data security regulations in various industries necessitates the adoption of secure image processing practices in WSNs [7].
However, implementing effective security measures in WSNs faces challenges due to sensor nodes' limited computational power and energy resources. Given the potentially large number of sensor nodes in WSNs, the need for scalable security solutions is also pronounced. Additionally, the complexity of designing efficient and effective security protocols, considering the diverse applications and environments of WSNs, adds to the challenge. Balancing high-level security with network performance, particularly regarding speed and energy efficiency, is a significant concern. This balance is crucial, given the sensitive nature of the data handled by these networks and their varied applications [6], [8].
Homomorphic encryption is emerging as a transformative approach in data security, particularly within Wireless Sensor Networks (WSNs). This advanced cryptographic technique allows for computations on encrypted data without decryption, offering substantial benefits in terms of security and privacy within WSNs [9].
In WSNs, where sensor nodes collect and transmit potentially sensitive data, traditional encryption methods necessitate decryption for data processing or analysis, posing significant security risks. Homomorphic encryption addresses this by enabling data processing in its encrypted form, thus maintaining data confidentiality even during analysis [10].
Integrating homomorphic encryption into WSNs enhances data security by keeping the data encrypted throughout its journey, significantly reducing the risks associated with data breaches and eavesdropping. This is particularly crucial in applications involving personal data, such as healthcare monitoring systems, or in scenarios demanding high confidentiality, like military surveillance [11].
Moreover, homomorphic encryption contributes to the preservation of privacy in WSNs. It allows for the aggregation and analysis of data without exposing the actual data content, which is especially relevant in scenarios where WSNs collect personal or sensitive information. User privacy is upheld by ensuring the data remains encrypted [12].
However, the implementation of homomorphic encryption in WSNs faces challenges, mainly due to the computational complexity associated with this form of encryption, which might strain the limited computational resources of sensor nodes. Balancing the security benefits with the computational overhead is a crucial area of ongoing research in applying homomorphic encryption in WSNs [9].
Integrating homomorphic encryption into Wireless Sensor Networks offers a promising pathway to enhance data security and privacy, potentially improving network efficiency. As this technology continues to evolve, its application in WSNs could become a cornerstone in pursuing more secure and efficient wireless sensor networks.
The primary objective of our paper is to explore and establish the efficacy of homomorphic encryption to enhance security and privacy in Wireless Sensor Networks (WSNs), particularly in the context of image processing.
This research addresses the dual challenges of maintaining data confidentiality and ensuring the integrity of image data transmitted across WSNs.
The specific objectives of the paper are:
- To investigate the application of homomorphic encryption in WSNs, thus, the theoretical and practical aspects of implementing homomorphic encryption in WSNs, assessing its feasibility and performance in real-world scenarios.
- To demonstrate the effectiveness of homomorphic encryption for image data through experimental analysis and simulations to showcase how homomorphic encryption can securely handle image data in WSNs without compromising data privacy.
Main contributions
a. Provides a detailed analysis of the security challenges in WSNs, mainly focusing on the vulnerabilities in image data transmission and processing.
b. Introduces a novel approach to employing homomorphic encryption in WSNs for image processing, contributing to the body of knowledge in cryptographic applications in sensor networks.
c. By implementing homomorphic encryption, the paper demonstrates a significant enhancement in the privacy and security of image data in WSNs, addressing a critical gap in current security protocols.
II. LITERATURE REVIEW
Integrating Homomorphic Encryption (HE) into Wireless Sensor Networks (WSNs), several studies have laid the groundwork, each contributing unique perspectives and methodologies. Raju Ranjan and Vinay Kumar Ahlawat explored using the Paillier homomorphic cryptosystem in WSNs, focusing on encrypting individual transmissions from sensor nodes and employing a digital signature method for authentication [13]. While emphasizing data security, their approach does not delve into the distributed processing of encrypted data across the network.
Mukesh Kumar et al. presented an End-to-End Homomorphic Encryption (EEHE) system for IoT-based WSNs, concentrating on secure data aggregation and the application of aggregator functions on encrypted messages [14]. This study shares a conceptual similarity with our proposed methodology regarding using HE for secure data aggregation. However, the architectural specifics differ, particularly in the roles assigned to various network components and the emphasis on scalability and computational distribution.
In a more specialized context, Usha et al. developed a Secure Cross-Layer Routing Protocol (SCLRP) for Underwater Acoustic Sensor Networks (UASNs) using homomorphic encryption combined with fuzzy logic [15] to target a specific type of WSN and incorporates fuzzy logic, which is not a feature of our proposed system architecture.
Hong et al. explored homomorphic encryption with Elliptic Curve Cryptography (ECC) to enhance mobile wireless network security and minimize communication overhead. While focusing on network security, their protocol presents a different application of HE and does not explicitly address the unique challenges of WSNs in distributed data processing [16].
Despite these significant contributions, there remains a research gap in the application of HE in WSNs, particularly in developing a system architecture that efficiently balances security, computational overhead, and scalability. Our proposed methodology addresses this gap by introducing a novel system architecture with sensor nodes equipped with data encryption capabilities, intermediate aggregator nodes performing homomorphic computations, and a central server for complex computations and data decryption. This architecture is designed to distribute the computational load effectively across the network, thereby enhancing the efficiency and scalability of the WSN while maintaining robust data security and privacy.
By focusing on a distributed approach to processing encrypted data, our methodology offers a comprehensive solution adaptable to various WSN scenarios, unlike the more specialized or limited-focus approaches in the existing literature. The integration of HE in this manner presents a promising avenue for advancing the security and functionality of WSNs, paving the way for more secure, efficient, and scalable sensor network applications.
Top of Form
III. BACKGROUNDBottom of Form
A. Homomorphic Encryption: Principles and Applications
Homomorphic encryption is a form of encryption that allows computations to be performed on ciphertexts, generating an encrypted result that, when decrypted, matches the result of operations performed on the plaintext. This property makes it a powerful tool for secure data processing in environments where confidentiality is paramount, such as in Wireless Sensor Networks (WSNs).
The mathematical underpinnings of homomorphic encryption are rooted in number theory and algebra. We need to delve into some key concepts and equations to understand them.


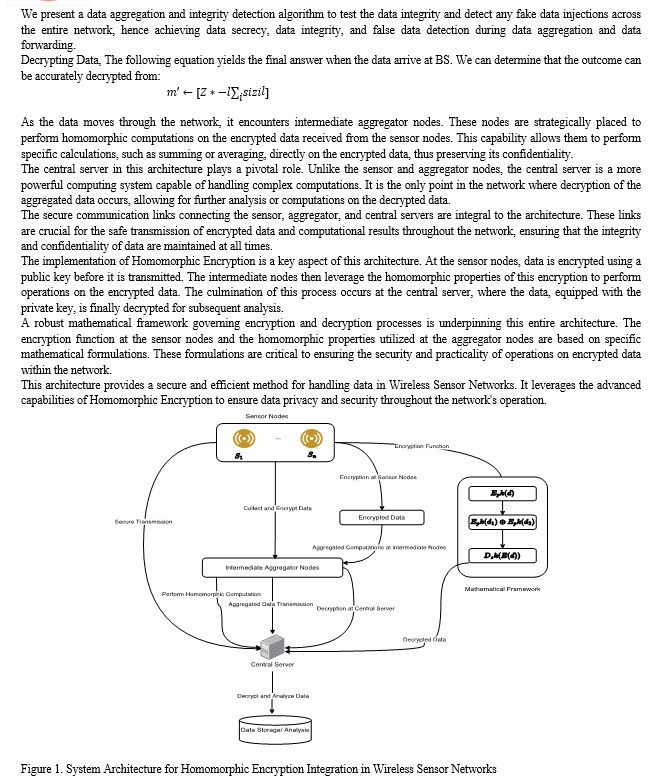



Similarly, the decryption phase at the central server involved substantial computation, especially given the need to handle aggregated data. Despite leveraging parallel processing techniques to mitigate the computational load, the overall process was still more demanding than conventional encryption methods.
The outcome of image processing after decrypting the aggregated data was particularly intriguing. The resultant image, a summation of pixel values from a human and a dog image, did not retain any meaningful visual content. However, it significantly demonstrated the ability to conduct computations on encrypted data, a pivotal aspect of Homomorphic Encryption.
Regarding security, the Paillier scheme provided robust protection, ensuring data privacy throughout transmission and processing. The encrypted data was secure from standard cryptographic attacks, rooted in the computational difficulty of solving complex mathematical problems, such as factoring large numbers. A standout feature of Homomorphic Encryption is its ability to process data while keeping it encrypted, thereby enhancing confidentiality.
Homomorphic Encryption stands out for its processing capabilities compared to traditional encryption methods. Unlike conventional methods that necessitate decryption before any data processing, Homomorphic Encryption allows for specific computations on encrypted data. While traditional encryption is generally faster and less resource-intensive, it lacks the capability for processing encrypted data. This distinction makes Homomorphic Encryption particularly valuable for sensitive WSN applications, where maintaining data privacy during processing is crucial.
Our experiment underscored the potential of Homomorphic Encryption in bolstering data security and privacy in WSNs. The capacity to process encrypted data without decryption is a considerable advantage in maintaining confidentiality, especially in sensitive environments. However, this comes at the cost of increased computational overhead, a trade-off that may be justified in scenarios where data privacy is paramount.
This technology holds particular promise in remote surveillance, environmental monitoring, and healthcare, where safeguarding data confidentiality is paramount. Our findings also highlight the necessity for continued research in this domain, focusing on optimizing Homomorphic Encryption techniques to reduce computational demands and develop more efficient algorithms suitable for WSNs.
A. Challenges and Limitations
Implementing Homomorphic Encryption (HE) in Wireless Sensor Networks (WSNs) presented notable challenges, primarily in computational complexity. Encrypting data, especially images, at the sensor nodes and performing homomorphic operations at intermediary points demanded substantial computational resources, leading to increased processing times. This complexity posed significant challenges in resource-constrained environments typical of WSNs. Additionally, the current study faced limitations in efficiently handling large volumes of data, a critical aspect for broader applicability in real-world scenarios. Future improvements could focus on optimizing encryption algorithms and developing more efficient processing techniques to reduce computational load. Enhancing the system's scalability to handle larger datasets with minimal resource expenditure remains crucial for further research and development.
Conclusion
Our study on integrating Homomorphic Encryption (HE) in Wireless Sensor Networks (WSNs) reveals significant advancements in securing network data, particularly in image processing applications. The HE implementation substantially enhances data security and privacy, mitigating risks associated with data transmission and processing within WSNs. This approach notably elevates the potential for secure image processing in such networks, enabling sensitive applications like surveillance and environmental monitoring to maintain data confidentiality. The implications of our findings are profound for WSN security, establishing a framework where data can be processed in encrypted form, thus preserving privacy without compromising the utility of the data. However, the challenges of computational complexity and resource constraints highlight the need for continued research. Future research should optimize encryption algorithms and processing methods to make HE more feasible for large-scale and real-world applications. Developing solutions that balance security, efficiency, and practicality will be crucial in advancing the field of secure data processing in WSNs.
References
[1] J. Chen and J. Tang, \"UAV-assisted data collection for dynamic and heterogeneous wireless sensor networks,\" IEEE Wireless Communications Letters, vol. 11, no. 6, pp. 1288–1292, 2022. [2] W. Jiao, M. Tian, and Y. Xu, \"A combining strategy of energy replenishment and data collection in wireless sensor networks,\" IEEE Sens J, vol. 22, no. 7, pp. 7411–7426, 2022. [3] Y. Yue et al., \"A data collection method for mobile wireless sensor networks based on improved dragonfly algorithm,\" Comput Intell Neurosci, vol. 2022, 2022. [4] M. Bilal, E. U. Munir, and F. K. Alarfaj, \"Hybrid clustering and routing algorithm with threshold-based data collection for heterogeneous wireless sensor networks,\" Sensors, vol. 22, no. 15, p. 5471, 2022. [5] A. Z. Abualkishik, A. A. Alwan, and others, \"Trust aware aquila optimizer based secure data transmission for information management in wireless sensor networks,\" Journal of Cybersecurity and Information Management, vol. 9, no. 1, pp. 40–51, 2022. [6] M. S. Abood, H. Wang, H. F. Mahdi, M. M. Hamdi, and A. S. Abdullah, \"Review on secure data aggregation in Wireless Sensor Networks,\" in IOP Conference Series: Materials Science and Engineering, 2021, p. 12053. [7] L. Kocharla and B. Veeramallu, \"Secure Energy-Efficient Load Balancing and Routing in Wireless Sensor Networks With Mediative Micro-ANN Fuzzy Logic,\" International Journal of Fuzzy System Applications (IJFSA), vol. 11, no. 3, pp. 1–16, 2022. [8] M. Elhoseny, A. Farouk, J. Batle, A. Shehab, and A. E. Hassanien, \"Secure image processing and transmission schema in cluster-based wireless sensor network,\" in Sensor Technology: Concepts, Methodologies, Tools, and Applications, IGI Global, 2020, pp. 698–715. [9] S. V Phakade, C. R. Singla, and O. Rajankar, \"Design of Privacy and Energy-Efficient DATA Aggregators for Wireless Sensor Networks,\" in 2022 2nd Asian Conference on Innovation in Technology (ASIANCON), 2022, pp. 1–5. [10] H. Ma, Z. Zhang, H. Li, S. Yin, and C. Zhao, \"A Provable Private Data Aggregation Scheme Based on Digital Signatures and Homomorphic Encryption for Wireless Sensor Networks.,\" J. Inf. Hiding Multim. Signal Process., vol. 8, no. 3, pp. 536–543, 2017. [11] A. Singh, R. R. K. Chaudhary, and K. Chatterjee, \"A novel privacy preservation mechanism for wireless medical sensor networks,\" in International Conference on Emerging Trends and Advances in Electrical Engineering and Renewable Energy, 2020, pp. 173–182. [12] M. S. Huque and A. S. Kaurav, \"A Novella Framework for Secure Data Aggregation in Wireless Sensor Networks using Symmetric Homomorphic Encryption Scheme (SHES)\". [13] J. Vijayan and G. Raju, \"A New approach to Requirements Elicitation Using Paper Prototype,\" International Journal of Advanced Science and Technology, vol. 28, 2011. [14] M. Kumar, M. Sethi, S. Rani, D. K. Sah, S. A. AlQahtani, and M. S. Al-Rakhami, \"Secure Data Aggregation Based on End-to-End Homomorphic Encryption in IoT-Based Wireless Sensor Networks,\" Sensors, vol. 23, no. 13, 2023, doi: 10.3390/s23136181. [15] M. Usha, R. Ashween, and others, \"SCLRP-Architecture for Secure Cross-Layer Routing Protocol for Underwater Acoustic Sensor Networks using Fuzzy Logic and Enhanced Algebra Homomorphic Encryption,\" 2021. [16] M. Hong, P.-Y. Wang, and W.-B. Zhao, \"Homomorphic encryption scheme based on elliptic curve cryptography for privacy protection of cloud computing,\" in 2016 IEEE 2nd International Conference on Big Data Security on Cloud (BigDataSecurity), IEEE International Conference on High Performance and Smart Computing (HPSC), and IEEE International Conference on Intelligent Data and Security (IDS), 2016, pp. 152–157.
Copyright
Copyright © 2024 Imam Adam Idris, Fadilul-lah Yassaanah issahku. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET58180
Publish Date : 2024-01-25
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

