Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Design and Analysis of ONLINE Voting System
Authors: Merugu Vigneshwar , Soumik Podder
DOI Link: https://doi.org/10.22214/ijraset.2024.62169
Certificate: View Certificate
Abstract
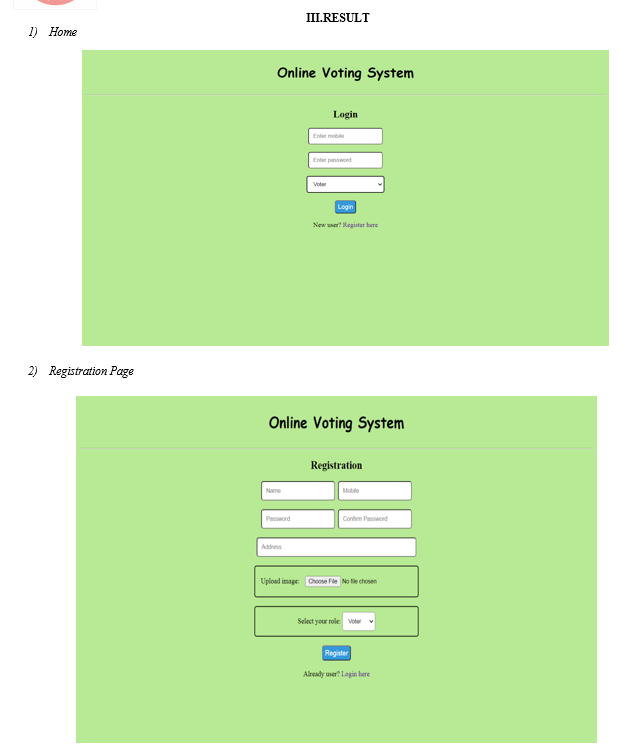
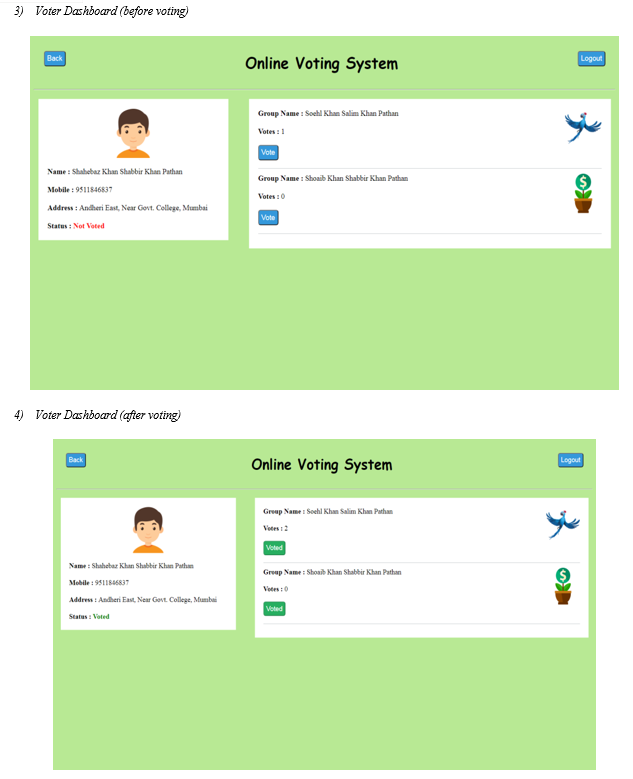
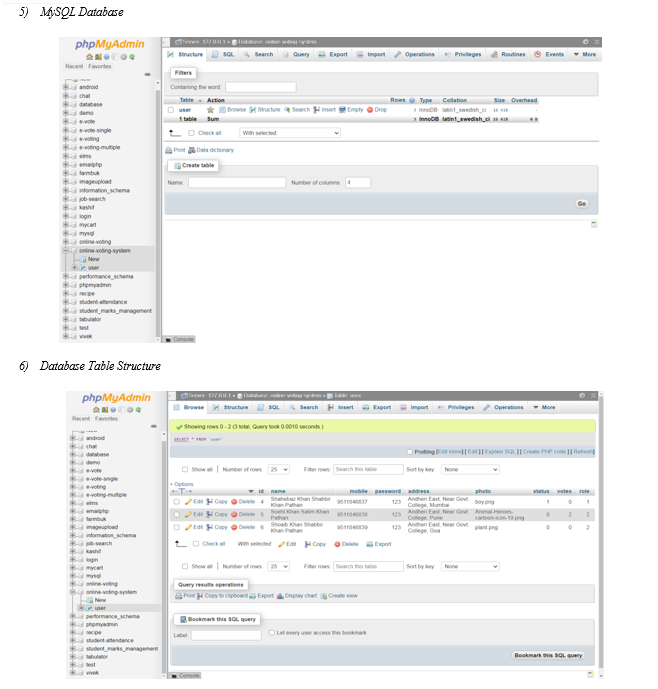
Abstract: A democratic country encourages voting system to decide the future leader. Traditional voting system offers lack of user friendliness in review of votes and voters’ identity security. In this present work, for the first time, a web-based voting architecture is designed and developed. The system has a login page, registration page, and dashboard page for voters to access in a user-friendly manner. The login page is the first page that users see when they access the system through registered mobile number, password, and role. The role is used to distinguish between voters and groups or candidates. The dashboard page is the display unit to exhibit voters’ profile information such as name, image, voting status, and mobile number on the left side of the page. On the right side of the page, there will be a list of groups or candidates whom they can cast their votes. In our proposed system, it is ensured that each voter can only vote once and that duplicate voting is not possible. The system uses password protected voting system and Black Box to administer the security issues for inculcating integrity of the voting process. The system is designed to provide a secure and user-friendly interface for voters to cast their votes online and henceforth the architecture will save the time, energy, and costs. The system is challenged by physical interaction between the voters and the election officials. With this system, voters can participate in the voting process without sacrificing their comfortable life at home and busy schedule at office.
Introduction
I. INTRODUCTION
In the traditional voting system, physical space and effective human resource are of prime interest especially to setup voting booths in multiple areas around city or village. Voter must visit the place where voting booth is arranged. Sometimes, voter needs to stand in a queue for a long time. Further manpower is required for volunteering and assistant of voters at the place of voting. Voting process is done manually on voting machine. Vote counting is done with the manual process. Then there is a gap of few days for results to be displayed. Also the security is one of the major challenges in this case. Often it is observed that during the conduction of voting or after the voting, the ruling party members showed supremacy and put many manipulated fake votes in order to win the election. This painstaking phenomenon can be overcome by the introduction of online voting system where the system should be password protected and the entry and exit of voters can be monitored frequently. In the present work, such type of online voting system is developed and its functionalities are analyzed. In present global scenario, internet plays a pivotal role in every sector like money transfer, shopping, booking, teaching, data sharing, admissions, job search, etc. Cloud computation, Machine learning and Artificial Intelligence, Data analytics, Online teaching and learning pedagogy all are rolled up by internet. So with the easy access and use of internet, the existing voting system can reach out on advance level. In the present work, an online platform with high security is aimed to develop where the traditional voting process will be executed without wasting time, afford and energy.
In the proposed system, initially voters and groups/candidates are required to register on online voting system. Once registration is done, voter can easily vote to their respected candidate or group by just signing in with the comfort of his/her home. Likewise, groups/candidates can do the same as well as also monitor their status with the comfort of home. By this way, the proposed system will save a lot of time, energy, and afford for both voters and groups. There are significant works on development of online voting system as governments and organizations around the world seek to modernize and improve the traditional voting process. The background of our work herein lies on the detailed analysis of existing scientific reports on the development of online voting system. This literature survey essentially becomes helpful in identifying the research gaps and motivating to develop some kind of novel aspects of the online voting system. A. Shehu and A. Idris had investigated the perspective of electronic voting system for Nigeria as majority of the inhabitants are illiterate and out of touch from modernization. Their study explores the impact of Card reader and PVC machine in justification of electronic voting system in the year of 2015 where significant election frauds were detected easily in the general election and also their investigation indicated that due to incorporation of electronic voting system, non performer leaders were voted out and prospective candidates got the opportunity to serve the nation via infrastructural development, civic upgradation and poverty intervention implementation etc. The major challenge for this case is the failure of Card reader machine but proper training of ad hoc personnel might ensure the good maintenance and servicing of the machine. [1]
Zissis et.al. had opened up a new avenue for data security and transparency in electronic voting system by the Incorporation of cloud architecture. The ICT enabled electronic voting essentially overcome the challenges in the cloud based system such as integrity, authenticity, confidentiality, and availability of data and communications. The centralized structure might provide a uniform and consistent pathway for managing risk. SaS and a couple of different tools like email, security tools are incorporated. The encryption was provided by PKI-based cryptography. There was regular monitoring and updation in system’s performance. Data was replicated over on and off cloud and across available zones for data so that any loss of data could not be able to shut down the system.[2]
Qadah et. el. had thoroughly analysed the requirement, design and implementation of electronic voting system especially for university voting where students can cast their votes anytime and from any locations just by using the electronic gadgets like personal computers, mobile phones, personal digital assistants. The security concern was solved by providing the unique student ID and password. The web security as well as unwanted replication was prevented by the use of Extensible Markup Language (XML) and the personalized voting on electronic gadgets [3] In the electronic voting, apart from security, there is another important issue is aroused- Anonymity. This important issue can be well realised by Grontas and his group’s work. They had developed U-BPRIV model that maintained anonymity and everlasting security.[4] Recently Blockchain based electronic voting is becoming an attractive pro-active area where the high end data privacy, self-tallying, balancing between anonymity and accountability are introduced. [4]
II. EXPERIMENTAL
A. Proposed Methodology
- System Design

a. Voters
Voters are the people who will first sign up on online voting panel. And then at the time of voting, they will login and do vote to their respective group or candidate via system. At the time of registration, following data from voter side will be provided to the system.
- Name
- Mobile
- Address
- Status
- Votes
- Role (voter/group)
- Photo
- Password
After successful registration, voters have to sign in to the system for casting vote. Successful log in of the voters might lead to casting vote without any hassle.
b. System
System is an online platform where election process is held. So the voters and groups are registered here. And with the help of system, voters can do voting and groups can monitor their status.
System Responsibilities
- Registration of both voter and candidate
- Display of registered candidates with respective votes on homepage
- Display of registered candidates on voter dashboard if any
- Display of profile info and voting status on voter dashboard
- Display of profile info, voting status, and votes on candidate dashboard
- Maintaining record for each candidate and voter without making any duplicate record.
c. Groups
Groups/Candidates/Parties are those who will be given votes at the time of voting. And they can monitor their status by just doing login into system.
Following data from group/party side will be provided to the system at the time of registration:
- Name
- Mobile
- Address
- Status
- Votes
- Role (voter/group)
- Photo
- Password
2. Hardware & Software Requirement Specification
a. Hardware Requirements
- Processor: Intel Core i3 or higher
- RAM: 4 GB or more
- Hard Disk: 500 GB or more
- Display: 1366 x 768 resolution or higher
- Internet Connection: Broadband or 4G
b. Software Requirements
- Operating System: Windows 7 or higher, or Linux
- Web Server: Apache or Nginx
- Database: MySQL
- Programming Languages: HTML, CSS, JavaScript, PHP
- Development Tools: Code editor (e.g. Visual Studio Code, Sublime Text), MySQL Workbench
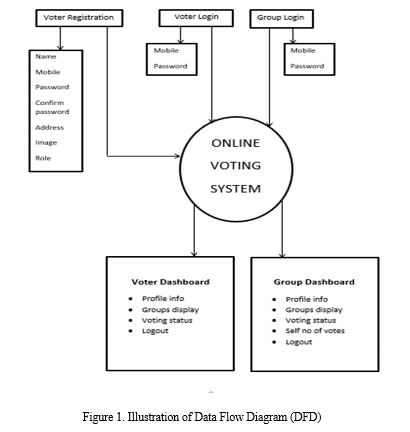
3. Data Flow Diagram [DFD]
Data flow Diagram depicts (Figure. 1) the entire information flow for online voting system. Initial stage is voter registration where a set of data are to be fed to the system as discussed in the voter section. After the successful registration, the data stored into the system will be stored into its database and when the voter will login, immediately those data will be fetched to identify the voter. Similarly group login also become possible after giving password and mobile number to the system.
After successful login for both individual voter as well as group the dashboard will display the voting status of voter and the group.
The DFD astoundingly intimate the present status of a voter as well as group.
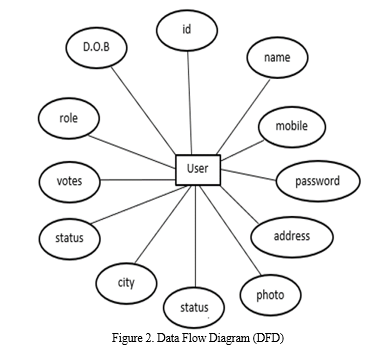
4. ER Diagram
The Entity Relational Diagram (ERD) is a model for recognizing entities in the database and also the illustration of their inter-relationship. It also illuminates the overall logical structure of a database in a graphical fashion. ERD explains the relationship among the entities present in the database. In the proposed work, the ER diagram (Figure 2) depicts the interrelation between the user and its different attributes such as name, ID, password, votes, address, city, mobile, D.O.B, status etc. The ER diagram essentially helps to design the online voter database that can store the data of voter along with his/her attributes.
B. Implementation of the DFD and ER using Different Technologies
- HTML
HTML stands for HyperText Markup Language. It is used to design web pages using a markup language. HTML is the combination of Hypertext and Markup language. Hypertext defines the link between the web pages. A markup language is used to define the text document within tag which defines the structure of web pages. This language is used to annotate (make notes for the computer) text so that a machine can understand it and manipulate text accordingly.
Most markup languages (e.g. HTML) are human-readable. The language uses tags to define what manipulation has to be done on the text. HTML is a markup language used by the browser to manipulate text, images, and other content, in order to display it in the required format. HTML was created by Tim Berners-Lee in 1991. The first-ever version of HTML was HTML 1.0, but the first standard version was HTML 2.0, published in 1999.
Elements and Tags: HTML uses predefined tags and elements which tell the browser how to properly display the content. Remember to include closing tags. If omitted, the browser applies the effect of the opening tag until the end of the page.
HTML page structure: The basic structure of an HTML page is laid out below. It contains the essential building-block elements (i.e. doctype declaration, HTML, head, title, and body elements) upon which all web pages are created.
<DOCTYPE! html>: This is the document type declaration (not technically a tag). It declares a document as being an HTML document. The doctype declaration is not case-sensitive.
<html>: This is called the HTML root element. All other elements are contained within it.
<head>: The head tag contains the “behind the scenes” elements for a webpage. Elements within the head aren’t visible on the front-end of a webpage. HTML elements used inside the <head> element include:
<body>: The body tag is used to enclose all the visible content of a webpage. In other words, the body content is what the browser will show on the front-end.
An HTML document can be created using any text editor. Save the text file using .html or .htm. Once saved as an HTML document, the file can be opened as a webpage in the browser.
Note: Basic/built-in text editors are Notepad (Windows) and TextEdit (Macs). Basic text editors are entirely sufficient for when you’re just getting started. As you progress, there are many feature-rich text editors available which allow for greater function and flexibility.
2. CSS
Cascading Style Sheets (CSS) is a style sheet language used for describing the presentation of a document written in a markup language such as HTML. CSS is a cornerstone technology of the World Wide Web, alongside HTML and JavaScript.
CSS is designed to enable the separation of presentation and content, including layout, colors, and fonts.[3] This separation can improve content accessibility, provide more flexibility and control in the specification of presentation characteristics, enable multiple web pages to share formatting by specifying the relevant CSS in a separate .css file which reduces complexity and repetition in the structural content as well as enabling the .css file to be cached to improve the page load speed between the pages that share the file and its formatting.
Separation of formatting and content also makes it feasible to present the same markup page in different styles for different rendering methods, such as on-screen, in print, by voice (via speech-based browser or screen reader), and on Braille-based tactile devices. CSS also has rules for alternate formatting if the content is accessed on a mobile device.[4]
The name cascading comes from the specified priority scheme to determine which style rule applies if more than one rule matches a particular element. This cascading priority scheme is predictable.
The CSS specifications are maintained by the World Wide Web Consortium (W3C). Internet media type (MIME type) text/css is registered for use with CSS by RFC 2318 (March 1998). The W3C operates a free CSS validation service for CSS documents.[5]
In addition to HTML, other markup languages support the use of CSS including XHTML, plain XML, SVG, and XUL.
3. JavaScript
- JavaScript (/?d???v??skr?pt/),[6] often abbreviated as JS, is a programming language that conforms to the ECMAScript specification.[7] JavaScript is high-level, often just-in-time compiled, and multi-paradigm. It has curly-bracket syntax, dynamic typing, prototype-based object-orientation, and first-class functions.
- Alongside HTML and CSS, JavaScript is one of the core technologies of the World Wide Web.[8] JavaScript enables interactive web pages and is an essential part of web applications. The vast majority of websites use it for client-side page behavior,[9] and all major web browsers have a dedicated JavaScript engine to execute it.
- As a multi-paradigm language, JavaScript supports event-driven, functional, and imperative programming styles. It has application programming interfaces (APIs) for working with text, dates, regular expressions, standard data structures, and the Document Object Model (DOM). However, the language itself does not include any input/output (I/O), such as networking, storage, or graphics facilities, as the host environment (usually a web browser) provides those APIs.
- JavaScript engines were originally used only in web browsers, but they are now embedded in some servers, usually via Node.js. They are also embedded in a variety of applications created with frameworks such as Electron and Cordova.
- Although there are similarities between JavaScript and Java, including language name, syntax, and respective standard libraries, the two languages are distinct and differ greatly in design.
a. Client-Side JavaScript
Client-side JavaScript is the most common form of the language. The script should be included in or referenced by an HTML document for the code to be interpreted by the browser. It means that a web page need not be a static HTML, but can include programs that interact with the user, control the browser, and dynamically create HTML content.
The JavaScript client-side mechanism provides many advantages over traditional CGI server-side scripts. For example, you might use JavaScript to check if the user has entered a valid e-mail address in a form field.
The JavaScript code is executed when the user submits the form, and only if all the entries are valid, they would be submitted to the Web Server.
JavaScript can be used to trap user-initiated events such as button clicks, link navigation, and other actions that the user initiates explicitly or implicitly.
b. Advantages of JavaScript
The merits of using JavaScript are −
- Less server interaction − You can validate user input before sending the page off to the server. This saves server traffic, which means less load on your server.
- Immediate feedback to the visitors − They don't have to wait for a page reload to see if they have forgotten to enter something.
- Increased interactivity − You can create interfaces that react when the user hovers over them with a mouse or activates them via the keyboard.
- Richer interfaces − You can use JavaScript to include such items as drag-and-drop components and sliders to give a Rich Interface to your site visitors.
c. Limitations of JavaScript
We cannot treat JavaScript as a full-fledged programming language. It lacks the following important features −
- Client-side JavaScript does not allow the reading or writing of files. This has been kept for security reason.
- JavaScript cannot be used for networking applications because there is no such support available.
- JavaScript doesn't have any multi-threading or multiprocessor capabilities.
Once again, JavaScript is a lightweight, interpreted programming language that allows you to build interactivity into otherwise static HTML pages.
d. JavaScript Development Tools
One of major strengths of JavaScript is that it does not require expensive development tools. You can start with a simple text editor such as Notepad. Since it is an interpreted language inside the context of a web browser, you don't even need to buy a compiler.
To make our life simpler, various vendors have come up with very nice JavaScript editing tools.
Some of them are listed here −
- Microsoft FrontPage − Microsoft has developed a popular HTML editor called FrontPage. FrontPage also provides web developers with a number of JavaScript tools to assist in the creation of interactive websites.
- Macromedia Dreamweaver MX − Macromedia Dreamweaver MX is a very popular HTML and JavaScript editor in the professional web development crowd. It provides several handy prebuilt JavaScript components, integrates well with databases, and conforms to new standards such as XHTML and XML.
- Macromedia HomeSite 5 − HomeSite 5 is a well-liked HTML and JavaScript editor from Macromedia that can be used to manage personal websites effectively.
4. PHP
- Hypertext Preprocessor is a server side scripting language designed for web development and also used as a general purpose programming language. It was originally created by Rasmus Lerdorf in 1994. The php reference is now produced by the php group. Php originally stood for personal home page. But now it stands for recursive initialism php hypertext preprocessor.
- Php code may be embedded into html code. It can be used in combination with various web template systems, web content management systems, and web frameworks. Php code is usually processed by a php interpreter implemented as a module in the web server or as a common gateway interface executable. The web server combines the results of interpreted and executed php code, which may be any type of data, including images, with the generated web page. Php code may also be executed with a command line interface and can be used to implement standalone graphical applications.
- The standard php interpreter, powered by the Zend engine, is free software released under the php license. Php has been widely ported and can be deployed on most web servers on almost every operating system and platform, free of charge.
- The php language evolved without a written formal specification or standard until 2014, with the original implementation acting as the de facto standard which other implementations aimed to follow. Since 2014 work has gone on to create a formal PHP specification
5. MYSQL
MYSQL is an open source software. It is actually a relational database management system(RDBMS). This SQL stands for Structured Query Language.It is the most popular and best RDBMS used for developing a variety of web-based software applications. With the help of MYSQL, it is possible to organize the information, manage, retrieve and update the data whenever you wish to do.
6. XAMPP
XAMPP is an open source free software developed by Apache friends. XAMPP software package contains Apache distributions for Apache server, MariaDB, PHP, and Perl. And it is basically a local host or a local server. This local server works on your own desktop or laptop computer. You can just install this software on your laptop or desktop and test the clients or your website before uploading it to the remote web server or computer. This XAMPP server software gives you suitable environment for testing MYSQL, PHP, Apache and Perl projects on the local computer.
The full form of XAMPP is X stands for Cross-platform, (A) Apache server, (M) MariaDB, (P) PHP and (P)Perl. The Cross-platform usually means that it can run on any computer with any operating system.
Next MariaDB is the most famous database server and it is developed by MYSQL team. PHP usually provides a space for web development. PHP is a server-side scripting language. And the last Perl is a programming language and is used to develop a web application.
What are the Main Tools of XAMPP and its definition?
XAMPP contains tools such as Apache, MYSQL, PHP, and Perl. We will see these tools.
e. APACHE
Apache server is an open source free software which is initially developed by a group of software developers and now it is maintained by Apache software foundation. Apache HTTP is a remote server(computer) if someone request files, images or documents using their browser they will serve those files to clients using HTTP servers. Mainly hosting companies use this application to create a VPS server and shared hosting for their clients.
f. MYSQL
MYSQL is an open source software. It is actually a relational database management system(RDBMS). This SQL stands for Structured Query Language.It is the most popular and best RDBMS used for developing a variety of web-based software applications. With the help of MYSQL, it is possible to organize the information, manage, retrieve and update the data whenever you wish to do.
PHP
The full form of PHP is Hypertext Preprocessor. It is a server-side scripting language that helps you to create dynamic websites. This language is mainly used to build web-based software applications. It is an open source software and works fine with MYSQL. What actually happens is, the PHP code will be executed on the server and at the browser side its HTML code will be displayed.
g. PERL
Perl is usually said to be general purpose programming language. This Perl language is interpreted and Actually, this language is used for web development, GUI development, system administration etc. Perl is capable of working with HTML, XML and other markup languages. In the latest version of XAMPP, there are additional tools such as Mail server Mercury, OpenSSL, phpMyAdmin etc. With the above tools, you can create a full-fledged desktop server.
C. XAMPP Screen View
D. Testing Cases
- Outputs And Reports Testing
Test Plan:
The online voting system must be tested thoroughly to ensure that it is free from bugs, errors, and security vulnerabilities. The testing process involves different types of testing such as black box testing, white box testing, and functional validation testing. The following is the test plan for the online voting system:
a. Black Box Testing
- Test login functionality using valid and invalid credentials.
- Test registration functionality by entering valid and invalid inputs.
- Test the voter dashboard functionality by ensuring that the voter can view their profile information and can cast their vote.
- Test the group/candidate dashboard functionality by ensuring that the group/candidate can view their profile information and can view the votes they have received.
- Test the voting functionality by ensuring that the user can vote only once.
- Test the validation messages by ensuring that appropriate messages are displayed when invalid inputs are entered.
b. White Box Testing
- Test the server-side code to ensure that it is secure and free from SQL injection and cross-site scripting (XSS) vulnerabilities.
- Test the client-side code to ensure that it is responsive and works well on different devices and screen sizes.
- Test the code for scalability, performance, and robustness.
c. Functional Validation Testing
- Test the registration functionality by ensuring that the user can register successfully and their details are stored in the database.
- Test the login functionality by ensuring that the user can login successfully with valid credentials.
- Test the voting functionality by ensuring that the user can cast their vote successfully and the vote is recorded in the database.
- Test the vote count functionality by ensuring that the vote count is incremented whenever a vote is cast.
2. Data Validation Test Cases
The following are the data validation test cases for the online voting system:
a. Test case ID: TC001
Test case description: Test registration with valid inputs.
Test data:
- Name: John Doe
- Mobile: 1234567890
- Password: Abc@123
- Confirm Password: Abc@123
- Address: 123 Main Street, City, State
- Image: sample.jpg
- Role: Voter
Expected result: User should be registered successfully.
b. Test case ID: TC002
Test case description: Test registration with invalid inputs.
Test data:
- Name: John Doe
- Mobile: 1234567890
- Password: Abc@123
- Confirm Password: xyz@123
- Address: 123 Main Street, City, State
- Image: sample.jpg
- Role: Voter
Expected result: Error message should be displayed - Password and Confirm Password do not match.
c. Test case ID: TC003
Test case description: Test login with valid credentials.
Test data:
- Mobile: 1234567890
- Password: Abc@123
Expected result: User should be logged in successfully.
d. Test case ID: TC004
Test case description: Test login with invalid credentials.
Test data:
- Mobile: 1234567899
- Password: xyz@123
Expected result: Error message should be displayed - Invalid mobile number or password.
3. White Box Testing
a. Test case ID: TC005
Test case description: Test server-side code for SQL injection vulnerability.
Expected result: Server should reject SQL injection queries.
b. Test case ID: TC006
Test case description: Test client-side code for responsiveness on different devices.
Expected result: The user interface should be responsive and work well on different devices and screen sizes.
Here are some more functional validation test cases and results:
4. Functional Validation Test Cases
a. Test Case ID: FVT_04
Test Case Description: Verify if the voter is allowed to cast the vote only once.
Precondition: The voter is registered and logged in to the system.
Test Steps:
1. The voter selects a candidate/group to cast his/her vote.
2. The voter attempts to cast the vote for the same candidate/group again.
Expected Result: The system should not allow the voter to cast the vote again and should display an error message.
b. Test Case ID: FVT_05
Test Case Description: Verify if the system displays the correct voting status for the voter.
Precondition: The voter is registered and logged in to the system.
Test Steps:
1. The voter logs in to the system.
2. The voter checks the voting status on the dashboard.
Expected Result: The system should display the correct voting status for the voter, i.e., whether the voter has already cast the vote or not.
???????E. Results
a. Test Case ID: FVT_04
Test Case Description: Verify if the voter is allowed to cast the vote only once.
Result: Pass/Fail
Observation: The system does not allow the voter to cast the vote again, and an error message is displayed.
b. Test Case ID: FVT_05
Test Case Description: Verify if the system displays the correct voting status for the voter.
Result: Pass/Fail
Observation: The system displays the correct voting status for the voter, i.e., whether the voter has already cast the vote or not.
???????F. Data Validation Test Cases
a. Test Case ID: DVT_01
Test Case Description: Verify if the system displays an error message if the voter enters an invalid mobile number.
Precondition: The voter is registering for the first time.
Test Steps:
1. The voter enters an invalid mobile number in the registration form.
2. The voter clicks on the submit button.
Expected Result: The system should display an error message and should not allow the voter to register with an invalid mobile number.
b. Test Case ID: DVT_02
Test Case Description: Verify if the system displays an error message if the voter enters an invalid password.
Precondition: The voter is registering for the first time.
Test Steps:
1. The voter enters an invalid password in the registration form.
2. The voter clicks on the submit button.
Expected Result: The system should display an error message and should not allow the voter to register with an invalid password.
V. FUTURE SCOPES
The Online Voting System has immense potential for future development and expansion. Some potential future scope areas are:
- Integration with blockchain technology to enhance security and transparency in the voting process.
- Development of a mobile application to provide more flexibility and accessibility to users.
- Expansion to support multiple languages and internationalization to enable voting across different countries and regions.
- Integration with biometric authentication technologies to ensure the identity of voters and prevent fraud.
- Use of artificial intelligence and machine learning algorithms to improve the accuracy and reliability of the voting process.
- Integration with social media platforms to increase user engagement and participation in the voting process.
- Development of analytics and reporting features to provide insights and trends on voting patterns and.
By incorporating these future scope areas, the Online Voting System can continue to evolve and provide a reliable, secure, and efficient platform for conducting voting processes over the internet, while addressing the changing needs and expectations of users.
Conclusion
In conclusion, the Online Voting System is a robust and efficient solution for conducting voting processes over the internet. The system provides various features such as user registration, login, and voting options, and ensures security and data privacy. The development of the system involved extensive research and analysis of existing systems, and the implementation of various software design and development principles. The project team carried out thorough testing of the system, including black box testing, data validation test cases, white box testing, and functional validation test cases. The testing was successful, and the system met all the expected standards and requirements. Overall, the Online Voting System is a highly useful and innovative solution that can help save time, energy, and cost associated with traditional voting methods. It has the potential to improve the efficiency and transparency of voting processes, making it a valuable tool for governments, organizations, and communities. Based on the project implementation and testing, the following recommendations are made: 1) The system should be further optimized for better performance, especially during peak usage periods. 2) The user interface can be further improved to enhance the user experience and make it more user-friendly. 3) Additional security measures can be implemented to ensure that the system is resistant to hacking attempts and unauthorized access. 4) The system can be scaled up to support larger groups of users, such as in national or international elections. 5) The project team should consider implementing a feedback mechanism for users to provide suggestions for improvement or report any issues. Overall, the Online Voting System has significant potential for wider implementation and adoption. By incorporating these recommendations, the system can be further improved to provide a reliable, secure, and efficient platform for conducting voting processes over the internet.
References
[1] S. AHMED Shehu, A. Idris, Electronic Voting System and Infrastructural Development: The Nigeria Perspective, Lapai International Journal of Administration LIJAD, 236-247., 2016 [2] D. Zissis, D. Lekkas, Securing e-Government and e-Voting with an open cloud computing architecture, Government Information Quarterly, 28 , 239–251,2011, doi:10.1016/j.giq.2010.05.010., [3] G.Z. Qadah, R.Taha, “Electronic voting systems: Requirements, design, and implementation,” Computer Standards & Interfaces 29 , 376–386, 2007 [4] P. Grontas, A. Pagourtzis, Anonymity and everlasting privacy in electronic voting, International Journal of Information Security ,22,Issue 4Aug pp 819–832https://doi.org/10.1007/s10207-023-00666-2
Copyright
Copyright © 2024 Merugu Vigneshwar , Soumik Podder. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET62169
Publish Date : 2024-05-15
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

