Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Artificial Intelligence in Cybersecurity
Authors: Abhishek Khot, Omkar Potadar, Prof. Pavan Mitragotri
DOI Link: https://doi.org/10.22214/ijraset.2024.63434
Certificate: View Certificate
Abstract
Artificial Intelligence (AI) has become integral to cybersecurity, offering advanced solutions for monitoring, detecting, reporting, and countering cyber threats. As cyberattacks grow in number and sophistication, traditional security measures prove inadequate. AI\'s ability to quickly adapt and learn makes it a vital tool in defending against these evolving threats. It automates routine tasks, accelerates threat detection and response, and improves the accuracy of security measures. However, AI also presents risks, such as potential misuse by cybercriminals, necessitating continuous human oversight. The increasing incidence of cyberattacks highlights the need for robust AI-enabled cybersecurity systems to protect sensitive data across industries.
Introduction
I. INTRODUCTION
In today's interconnected digital world, cybersecurity has become more critical than ever. Cybersecurity refers to a set of technologies, processes, and practices aimed at safeguarding networks, devices, software, and data from various forms of cyber threats, including unauthorized access, damage, or attacks. With the exponential growth of interconnected devices, systems, and networks, the complexity of cybersecurity challenges has increased significantly.
Intelligence-driven cybersecurity involves leveraging advanced analytics and intelligence to defend against ever-evolving cyber threats effectively. By swiftly analyzing millions of events and tracking various cyber threats, AI technologies can anticipate and respond to potential security breaches before they escalate. As a result, AI is increasingly being integrated into cybersecurity strategies, where it automates security tasks or supports the efforts of human security teams.
The integration of AI into cybersecurity practices has led to a flourishing field of research, with experts from both AI and cybersecurity collaborating to develop innovative solutions. Numerous studies have been conducted to solve problems related to identifying, protecting, detecting, responding to, and recovering from cyberattacks. While several reviews on cybersecurity and AI applications have been published in recent years, there remains a need for a comprehensive overview that covers the state-of-the-art research in this area.
In summary, as cyber threats continue to evolve and escalate, intelligence-driven cybersecurity approaches, powered by AI technologies, play a crucial role in defending against these threats. By leveraging advanced analytics and intelligence, organizations can better protect their networks, devices, software, and data from cyberattacks, ultimately safeguarding their operations and ensuring the security of their digital assets.
II. ROLE OF ARTIFICIAL INTELLIGENCE IN CYBERSECURITY DEFENSES
A. Introduction to AI Technologies in Cybersecurity
The fight against cyberthreats in today's digitally connected world is fought on several fronts, including Attackers are always changing their strategies to get past defenses. Artificial intelligence (AI) is emerging as a potent ally in strengthening cybersecurity defenses during this continuing arms race. Artificial Intelligence (AI) is a collection of technologies that allow computers to do tasks like learning, reasoning, and problem-solving that have historically required human intelligence. AI enables enterprises to identify, evaluate, and respond to risks with previously unheard-of speed, precision, and efficiency when it comes to cybersecurity.
B. Applications of AI in Threat Detection and Prevention
The use of AI in threat detection and prevention is among the most significant uses in cybersecurity. Conventional security measures are vulnerable to evasion strategies used by crafty adversaries because they rely on established rules and signatures to identify malicious actions. AI-powered methods,On the other side, use machine learning algorithms to instantly evaluate massive volumes of data and identify trends and abnormalities that point to potential security vulnerabilities. AI systems are able to spot risks that were previously unseen with surprising precision, preventing attacks before they cause harm.
This is achieved by continuously learning from fresh data and adapting to shifting attack vectors.Additionally, AI improves threat prevention by learning the typical behavior patterns of individuals, devices, and networks through behavior-based analysis.
C. AI-Driven Solutions for Incident Response and Mitigation
AI is essential for incident response and mitigation, not just for enhancing threat identification and prevention but also for assisting enterprises in quickly containing and eliminating cyberattacks. By automating repetitive processes like log analysis, threat correlation, and remediation procedures, these AI-driven solutions support human analysts by freeing them up to concentrate on high-priority and strategic decision-making duties. Additionally, by offering contextual insights and predictive analytics, AI improves incident response efficiency by helping firms foresee future risks and proactively strengthen their defenses.
D. Case Studies Demonstrating the Effectiveness of AI in Cybersecurity
Numerous real-world case studies witness to AI's transformative influence on increasing organizational resilience against cyber attacks, demonstrating its usefulness in cybersecurity beyond theory. Similar to this, a multinational healthcare provider used threat intelligence platforms driven by AI to protect sensitive patient data from advanced persistent threats (APTs). Protecting patient privacy and guaranteeing regulatory compliance, the business was able to proactively identify and neutralize APTs before they could exfiltrate sensitive information by evaluating massive amounts of threat data and identifying indicators of compromise across various sources.
III. AI TECHNIQUES IN CYBERSECURITY
A brief introduction to AI learning algorithms, which are essential to the discipline, is provided in this section. Key AI subfields that are frequently used in cybersecurity applications are introduced, including expert systems, machine learning, deep learning, and biologically inspired computation.
A. Machine Learning (ML) and Deep Learning
As a branch of artificial intelligence, machine learning teaches computers to use algorithms to learn from data so they can anticipate and make decisions. It includes methods for extracting data, finding patterns, and formulating conclusions. Its primary forms include semi-supervised, supervised, unsupervised, and reinforcement learning. Computers can now do things that were previously only possible for humans thanks to deep learning, a subset of machine learning that mimics the interpretation of input from the human brain. Neural networks perform better as they get bigger and are taught with more data. Deep learning and machine learning are both essential for solving cybersecurity issues. Applications for machine learning can be found in many security activities, such as tracking botnets, anomaly detection, and spam filtering. Deep learning is useful in network systems for detecting intrusions and viruses, underscoring its significance in improving cybersecurity.
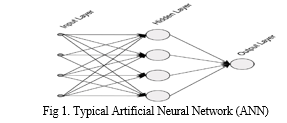
B. Artificial Neural Networks (ANN)
Frank Rosenblatt created Artificial Neural Networks (ANNs) in 1957 to mimic human brain neurons and process large amounts of data to get desired values. ANNs are excellent at comprehending complicated issues in a variety of fields, including cybersecurity. They are used to examine network traffic in intrusion detection systems (IDS) in order to detect and stop cyber threats. When new events are identified, Cascade Correlation Neural Networks (CCNN) add additional hidden units dynamically, providing flexible and scalable security solutions. With their automatic pattern recognition capabilities, ANNs improve network security by outperforming manual methods in the detection of nonlinear problems. An improved version of artificial neural networks (ANNs) called Deep Neural Networks (DNN) can anticipate potential threats in addition to defending against cyberattacks. DNNs have paved the road for cyberattacks with an 85% success rate in cyberattack detection.
C. Biological Inspired Computation
AI's "bio-inspired computing" leverages traits found in nature to solve challenging issues. In cybersecurity, methods including genetic algorithms, ant colony optimization, and evolution strategies are used, particularly for malware categorization. For example, Particle Swarm Optimization and Genetic Algorithms improve the effectiveness of malware detection systems. High accuracy rates in intrusion detection are achieved through the use of techniques like fuzzy logic and genetic algorithms. These methods demonstrate the promise of bio-inspired computing in tackling complex cybersecurity difficulties by optimizing features and parameters for classifiers, enhancing cybersecurity systems' capacity to identify and react to attacks.
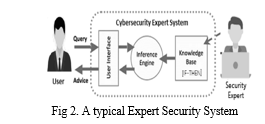
D. Security Expert Systems
An AI expert system uses an inference engine and knowledge base to create security rules, assisting human experts. In cybersecurity, it's critical to base judgments on accepted standards. Expert systems are used in many different industries, including cybersecurity, banking, and medical. They can be basic or complex. To solve issues, they use strategies like rule-based systems (RBS) and case-based reasoning (CBR). RBS classifies processes as safe or dangerous in cybersecurity by comparing them to a knowledge base. The system's ability to make decisions in intricate cybersecurity scenarios is demonstrated by notifying users according to the machine's state as defined by inference engine rules.
E. Intelligent agents (IAs)
Intelligent agents, or IAs, are self-governing, proactive systems that make decisions on their own. They evaluate dangers, take appropriate action, and adjust to environmental changes. Distributed Denial of Service (DDoS) attacks can be effectively countered by IAs, particularly when they are included into a mobile, artificial "digital police" structure. αβ-search estimation, a critical thinking technique, improves search-based security solutions in artificial intelligence (AI), which were initially created for computer chess. These tactics make it possible to make wise decisions in difficult situations, which is essential for dealing with changing cybersecurity threats.
IV. CHALLENGES AND LIMITATIONS
Proactive tactics and improved defenses are promised by the incorporation of artificial intelligence (AI) in the lightning-fast field of cybersecurity, where threats are evolving at an alarming rate. But in the midst of this technological miracle, there are many restrictions and difficulties that need to be carefully considered. These problems investigate the ethical, human, and regulatory aspects of cybersecurity in addition to testing AI systems' technological prowess.
A. Ethical Considerations of AI in Cybersecurity
Concerns about privacy, autonomy, and accountability are among the ethical issues that are brought up by the use of AI in cybersecurity. AI systems need a lot of data, which increases the possibility of abuse and privacy violations. The necessity for strong ethical frameworks to strike a balance between security and individual freedoms is highlighted by the opaque nature of AI decision-making, which undermines accountability and transparency.
B. Technical Challenges and Limitations of AI-Powered Defences
Even with AI's potential, cybersecurity still faces several obstacles. AI flaws can be exploited by adversaries using strategies like deceptive defenses and hostile examples. The dynamic nature of cyber threats necessitates AI's real-time adaptation, which presents technical challenges for accuracy maintenance. Reliance on AI also creates new potential areas of vulnerability for abuse.
C. Human Factors in AI-Based Cybersecurity Systems
Human considerations are critical to AI-based cybersecurity. AI outputs must be appropriately interpreted by operators; nevertheless, human-machine interaction might result in misunderstandings or overconfidence, which can produce false positives or negatives. Furthermore, a lack of awareness of AI among cybersecurity professionals creates obstacles to utilizing AI technologies to their full potential.
D. Regulatory and Compliance Issues
Regulation and compliance present difficulties for AI in cybersecurity because particular frameworks are still developing. Complying with industry standards and data protection rules increases complexity. International cooperation and cross-border data transfers give rise to jurisdictional concerns. To guarantee that AI systems are morally, legally, and successfully safeguarding digital assets, these issues must be resolved.
V. BENEFITS OF AI IN CYBERSECURITY
Since automated algorithm mitigation is replacing old, manual procedures in the cybersecurity system, artificial intelligence (AI) can offer significant answers to many cybersecurity issues today. Artificial intelligence (AI) has the ability to detect novel and intricate changes in the extensibility of attacks, in contrast to traditional technology, which mostly depends on previously discovered attackers and incursions, leaving a blind spot during atypical intrusion activities. AI technology has now solved these shortcomings of traditional security technology. For instance, it is now possible to monitor privileged internet activity, and any modification to privileged access procedures may be cause for concern.
AI prediction techniques give security teams a competitive advantage, which is critical to thwarting assaults before they can do any damage. A UK startup called Dark Trace employed machine learning (ML) to identify trends and potential dangers in a variety of industries, including manufacturing, retail, energy, and transportation. AI-based methods can be used to manage large amounts of data and enhance network security systems. For security specialists, the sheer volume of active security issues is staggering. Security groups are dealing with less work because to AI's autonomous attack detection and response. Managing huge amounts of security data that are produced and sent on a regular basis presents a difficult problem for security experts.
As a result, AI can aid in accelerating the examination of dubious actions and procedures. Additionally, by substituting the labor-intensive manual techniques with automated ones, security staff may profit and respond to new situations more quickly. AI-based systems are more capable of defending against threats and attacks and are prepared to adapt over time. AI assists in identifying threats by taking into account the features of the application and the general activity on the network. As time went on, AI learned the regular and typical traffic state and established a restriction for the routine activities. Therefore, whenever there is an abnormal departure, attacked is noted.
VI. FUTURE DIRECTIONS AND RECOMMENDATIONS
A. Potential Advancements in AI for Cybersecurity:
Innovations in artificial intelligence (AI) for cybersecurity are critical to staying ahead of cyber threats as technology develops quickly. AI algorithms with improved detection and prediction capabilities can analyze large amounts of data in real-time using sophisticated machine learning techniques like deep learning to identify patterns indicative of malicious activities. AI integration with emerging technologies like blockchain and quantum computing promises stronger cybersecurity defenses. Blockchain-powered systems can improve data integrity and authentication, and quantum AI algorithms can improve encryption methods. Professionals need to understand explainable AI decisions in order to be transparent and trustworthy.
B. Strategies for Integrating AI into Existing Cybersecurity Frameworks:
Investing in workforce training guarantees cybersecurity professionals are equipped with AI skills. This includes training on AI tools and techniques, fostering a culture of continuous learning to adapt to evolving cyber threats. By starting small, collaborating effectively, and investing in training, organizations can seamlessly integrate AI into cybersecurity practices, enhancing their ability to detect, respond to, and mitigate cyber threats across various industries and sectors. To effectively integrate AI into cybersecurity frameworks, a strategic approach is needed, starting with small-scale implementations for specific tasks like threat detection. Collaboration among AI developers, cybersecurity vendors, and organizations is essential for tailored solutions.
C. Recommendations for Policymakers, Organizations, and Cybersecurity Professionals:
Regulators that govern cybersecurity and AI place a strong emphasis on preventing prejudice and promoting ethical use. Businesses place a high priority on cybersecurity, investing in AI technologies, and encouraging teamwork. Professionals in cybersecurity keep up with developments in AI, adjusting protections against new threats. Transparency and fairness in AI systems are ensured by explicit guidelines. Funds are set aside to support cybersecurity, encouraging information exchange for group resilience. Professionals that receive ongoing training are better able to use AI to their advantage and outwit adversaries.Policymakers,organizations, and cybersecurity specialists must work together to navigate the changing scenario responsibly.
Conclusion
This study explores the critical role that artificial intelligence (AI) plays in solving cybersecurity issues. Given that humans are insufficient to protect enterprise-level attack surfaces, the study emphasizes how AI has become essential to enhancing the efficacy of information security teams. With AI becoming more and more integrated into daily life, its impact is expected to grow despite differing views on its ramifications. Its advantages in quickly identifying and addressing security risks, especially in the context of cloud computing, cannot be disputed, nevertheless. Notwithstanding problems like adversarial machine learning, AI helps with risk discovery, incident response guidance, and proactive malware identification. Notwithstanding reservations, considering the increasing complexity of cyberattacks, AI integration is considered necessary for cybersecurity progress.
References
[1] Zeadally, S., Adi, E., Baig, Z., & Khan, I. A. (2020). Harnessing artificial intelligence capabilities to improve cybersecurity. Ieee Access, 8, 23817-23837. [2] Calderon, R. (2019). The benefits of artificial intelligence in cybersecurity. [3] Shah, V. (2021). Machine Learning Algorithms for Cybersecurity: Detecting and Preventing Threats. Revista Espanola de Documentacion Cientifica, 15(4), 42-66. [4] Hussain, A., Mohamed, A., & Razali, S. (2020, March). A review on cybersecurity: Challenges & emerging threats. In Proceedings of the 3rd International Conference on Networking, Information Systems & Security (pp. 1-7). [5] Lidestri, N., Maher, Stephen J., & Zunic, Nev.,” The Impact of Artificial Intelligence in Cybersecurity,”. ProQuest Dissertations and Theses, 2018. [6] anjeet Rege, Raymond Blanch K. Mbah, “Machine Learning for Cyber Defense and Attacks,”. The seventh international conference on data analytics, 2018, ISBN: 978-1-61208-681-1. [7] K. Rieck, P. Trinius, C. Willems, and T. Holz, “Automated analysis of malware behavior using machine learning,”. Journal of Computer Security, 19(4), 639 668, 2011. [8] Benoit Morel, “Artificial Intelligence a Key to the Future of Cybersecurity,”. In Proceeding of Conference AISec’11, October 2011, Chicago, Illinois, USA. [9] Y. Ye, L. Chen, S. Hou, W. Hardy, X. Li, “DeepAM: A heterogenous deep learning framework for intelligent malware detection,”. Knowledge Information System. 2018, 54, 265-285. [10] Kabbas, A., Alharthi, A., & Munshi, A. (2020). Artificial intelligence applications in cybersecurity. IJCSNS International Journal of Computer Science and Network Security, 20(2), 120-124. [11] Shamiulla, A.M. (2019). Role of Artificial Intelligence in Cyber Security. International Journal of Innovative Technology and Exploring Engineering, 9(1), 4628 4630. [12] Srivastava, S., Benny, B., Ma’am, M. P. G., & Ma’am, N. B. (2021). Artificial Intelligence (AI) and It’s Application in Cyber Security (No. 5791). EasyChair. [13] Tyugu, E. (2011, June). Artificial intelligence in cyber defense. In 2011 3rd International Conference on Cyber Conflict (pp. 1-11). IEEE. [14] Wirkuttis, N., & Klein, H. (2017). Artificial intelligence in cybersecurity. Cyber, Intelligence, and Security, 1(1), 103-119.
Copyright
Copyright © 2024 Abhishek Khot, Omkar Potadar, Prof. Pavan Mitragotri. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET63434
Publish Date : 2024-06-24
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

