Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Biometric for Data Protection
Authors: R. K. Poongodi , S. Sudharsan, C. Vinoth
DOI Link: https://doi.org/10.22214/ijraset.2025.66818
Certificate: View Certificate
Abstract
Biometric data, including fingerprints, facial recognition, iris scans, and voice patterns, has become a vital tool in various industries, offering enhanced security and streamlined user experiences. However, the use of biometric data raises significant concerns regarding privacy and data protection due to its sensitive nature and potential for misuse. This abstract discusses the importance of protecting biometric data, examining the risks associated with its collection, storage, and processing, as well as the legal frameworks that govern its use. Key regulations such as the General Data Protection Regulation (GDPR) and the Biometric Information Privacy Act (BIPA) set stringent guidelines for organizations to ensure biometric data is collected with explicit consent, securely stored, and properly managed. The abstract also explores the role of encryption, access controls, and privacy policies in mitigating risks and safeguarding individuals\' rights. As biometric technologies continue to advance, it is essential that organizations implement comprehensive data protection strategies to prevent unauthorized access, breaches, and misuse while maintaining the trust of individuals. The abstract concludes with an emphasis on the need for continued innovation in both biometric technologies and data protection practices to address emerging challenges and ensure compliance with evolving privacy standards.
Introduction
I. INTRODUCTION
Biometric technology refers to the use of unique biological characteristics, such as fingerprints, facial recognition, iris scans, voice patterns, and even behavioral traits, to identify and authenticate individuals.
This technology has become an integral part of modern security systems, replacing traditional authentication methods like passwords and PINs with more secure and convenient solutions. Biometric systems are widely used in various industries, including finance, healthcare, law enforcement, and travel, enhancing security and streamlining access control. As advancements continue, biometric technology is evolving to offer faster, more accurate, and more secure identification methods while raising important ethical and privacy considerations.
II. USES OF BIOMETRICS
Biometric technology is used for several reasons, primarily for security, convenience, and accuracy in identity verification. Here are some key reasons why biometrics are widely adopted:
A. Enhanced Security
Biometric traits, such as fingerprints, iris scans, and facial recognition, are unique to each individual, making it difficult for unauthorized users to gain access. This provides stronger security than traditional passwords or PINs, which can be stolen or shared.
B. Convenience and Speed
Unlike passwords, which users may forget or need to reset, biometric authentication is quick and effortless. Scanning a fingerprint or face takes only a few seconds, making it ideal for fast identity verification in banking, airports, and smartphones.
C. Accuracy and Reliability
Biometric authentication reduces errors and fraud by ensuring that only the rightful owner gains access. Advanced biometric systems combine multiple recognition methods (e.g., face and fingerprint) to improve accuracy.
D. Reducing Identity Theft and Fraud
Biometrics help prevent identity fraud in banking, government services, and e-commerce by ensuring that only authorized individuals can access accounts or complete transactions.
III. FUTURE OF BIOMETRIC
The future of biometrics includes advancements in contactless authentication, behavioral biometrics (e.g., typing patterns and gait recognition), and the integration of quantum computing and blockchain for enhanced security. Ethical and privacy concerns will also shape the evolution of biometric technologies.
IV. RECENT ADVANCE IN BIOMETICS
Biometric technology has evolved rapidly with advancements in artificial intelligence (AI), machine learning, and sensor technology. Below are some of the most recent and emerging trends in biometrics:
A. Contactless Biometrics
- Touchless Fingerprint Recognition: New imaging techniques capture fingerprints from a short distance, enhancing hygiene and convenience in public places.
- 3D Facial Recognition: Unlike traditional 2D methods, 3D facial recognition uses depth-sensing cameras to improve accuracy and security, making it resistant to spoofing.
- Iris Recognition at a Distance: AI-powered iris scanning can now authenticate users without requiring close proximity to a scanner.
B. Behavioral Biometrics
- Gait Recognition: AI can analyze walking patterns for identification, useful in security and healthcare applications.
- Keystroke Dynamics: Typing rhythm and pressure patterns are being used for continuous authentication in cybersecurity.
- Voice Biometrics: Enhanced voice authentication with deep learning models improves security in banking and virtual assistants.
C. Multimodal Biometrics
- Fusion of Multiple Biometric Traits: Combining fingerprint, face, and voice recognition enhances security and reduces false positives.
- Brainwave Authentication: Electroencephalogram (EEG) signals are being explored as unique biometric identifiers for high-security applications.
D. AI-Driven Biometrics
- Deepfake Detection in Facial Recognition: AI models are improving the ability to detect deepfake images and videos, preventing fraud.
- Self-Learning Biometric Systems: AI-powered biometric systems continuously learn user patterns for adaptive authentication.
E. Biometric Cryptography & Blockchain Integration
- Biometric Encryption: Protects biometric data by converting it into cryptographic keys rather than storing raw biometric templates.
V. DATA PROTECTION IN BIOMETRICS
As biometric systems increasingly become a core component of identity verification and security, ensuring the protection of biometric data is crucial to maintaining privacy and preventing misuse. Biometric data is highly sensitive because it is unique to each individual and cannot be changed if compromised (e.g., unlike passwords). Below are key aspects of biometric data protection:
A. Encryption of Biometric Data
- Data Encryption: Biometric data should be encrypted both during transmission (when being sent over a network) and at rest (when stored in databases). This ensures that even if the data is intercepted or accessed without authorization, it cannot be read or misused.
- Biometric Template Encryption: Instead of storing raw biometric data (such as a fingerprint image), biometric systems typically store a "template" (a mathematical representation of the biometric data). Encrypting these templates further protects sensitive information.
B. Decentralized Data Storage (Distributed Systems)
- Local Storage vs. Centralized Databases: Instead of storing biometric data in a central database, decentralized or distributed storage solutions can be used, reducing the risk of mass data breaches. This approach ensures that biometric data is stored locally (e.g., on a device) rather than on a central server, allowing for greater control and privacy.
- Blockchain for Biometric Security: Blockchain technology can be used to store biometric data in a decentralized and immutable ledger. This ensures that biometric records are not altered and can only be accessed by authorized parties, providing an additional layer of security and accountability.
C. Secure Transmission Protocols
- SSL/TLS Protocols: Secure protocols like SSL/TLS should be used for transmitting biometric data between devices and servers. These protocols prevent data from being intercepted by unauthorized parties during transmission.
- Biometric Authentication without Raw Data Transmission: Some systems use methods such as one-way encryption or hashing, where the biometric data is not transmitted in raw form. Instead, only a unique identifier or a hashed value of the biometric data is shared for authentication purposes.
D. Privacy-Enhancing Technologies
- Differential Privacy: Differential privacy techniques can be applied to biometric systems to ensure that individual biometric data cannot be extracted from aggregate data sets. This is especially useful when large volumes of biometric data are being processed.
- Homomorphic Encryption: This allows computations to be performed on encrypted data without decrypting it. In the context of biometrics, it can help process and match biometric templates without exposing the underlying sensitive data.
VI. PERFOMANCE OF BIOMETRIC SYSTEM
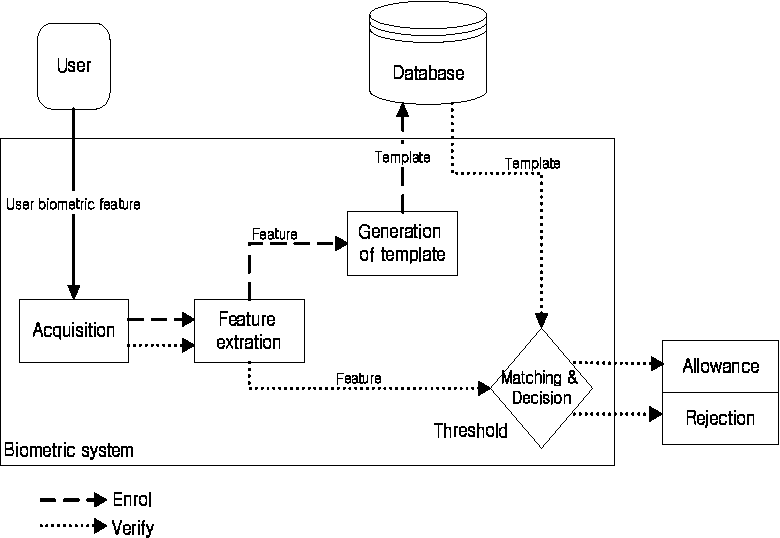
The performance of biometric systems is crucial for their effectiveness and reliability. A well-performing biometric system should have high accuracy, speed, and reliability while maintaining privacy and security. Below are key performance metrics used to evaluate biometric systems:
A. Accuracy Metrics
1) False Acceptance Rate (FAR)
- Definition: FAR measures the likelihood that the biometric system incorrectly accepts an unauthorized individual. It is the probability that the system mistakenly matches a non-matching biometric sample to a valid user’s template.
- Impact: A low FAR is crucial for security, as high FAR can allow unauthorized users to gain access.
2) False Rejection Rate (FRR)
- Definition: FRR measures the probability that the system incorrectly rejects a valid user. This happens when the system fails to match the user's biometric sample with their stored template.
- Impact: A low FRR is important for user convenience, as high FRR can cause legitimate users to be denied access, leading to frustration.
B. Security and Privacy
1) Liveness Detection
- Definition: Liveness detection ensures that the biometric sample comes from a live person and not from an artificial replica, such as a photograph, video, or molded fingerprint.
- Impact: Effective liveness detection is essential for preventing spoofing and fraud in systems like facial recognition and fingerprint scanning.
2) Anti-Spoofing Measures
- Definition: Anti-spoofing measures are techniques designed to prevent the use of fake or altered biometric samples (e.g., using photos or 3D models in facial recognition systems).
- Impact: The performance of a biometric system can be significantly improved if it has strong anti-spoofing mechanisms, which can protect against identity theft and unauthorized access.
C. User Acceptance and Experience
1) Ease of Use
- Definition: The ease with which users can interact with the biometric system for enrollment, authentication, and verification. A user-friendly interface contributes to overall user satisfaction.
- Impact: If a biometric system is intuitive and easy to use, it is more likely to be accepted by users in everyday applications.
2) User Satisfaction
- Definition: The overall level of user satisfaction with the biometric system, which includes factors like convenience, speed, and reliability of the system.
- Impact: High user satisfaction is key for the widespread adoption of biometric systems in areas such as mobile security, customer service, and healthcare.
VII. ACKNOWLEDEGEMENT
We acknowledge that biometric data, such as fingerprints, facial recognition, iris scans, and voiceprints, is sensitive personal information that requires robust protection under data protection laws, including the General Data Protection Regulation (GDPR) and other relevant national regulations. As an organization, we are committed to:
By using biometric data, we acknowledge the trust placed in us by individuals and commit to respecting their privacy rights and ensuring the secure and responsible handling of their biometric information.
This acknowledgement ensures that all stakeholders understand the importance of biometric data protection and demonstrates the organization’s commitment to maintaining high standards of data privacy and security.
Conclusion
The performance of biometric systems is multifaceted, involving accuracy, speed, robustness, security, user experience, and cost-effectiveness. Achieving a balance across these factors is key for the successful deployment of biometric systems, whether in security, consumer electronics, healthcare, or large-scale government applications.
References
[1] M. M. Al-Mousa, M. A. Mahfouz, & A. S. M. Hassan, \"Biometric-Based Healthcare Authentication Systems,\" IEEE Transactions on Biomedical Engineering, 2020 [2] K. A. MacDorman & J. R. Reichenbach, \"Biometric Borders: The Role of Biometric Technology in International Immigration and Border Control,\" Immigration Review, 2020. [3] C. D. Lee, \"Biometric Access Control in the Workplace,\" Security Systems Journal, 2020 [4] M. M. N. Suraiya & A. A. A. Bakar, \"Biometric Authentication Systems in the Banking Sector,\" International Journal of Computer Applications, 2019. [5] J. P. C. van der Veen, \"Biometrics in Criminal Justice,\" The Journal of Forensic Sciences, 2017. [6] K. B. Raja, \"Biometric Authentication in Financial Institutions,\" Journal of Financial Security, 2018 [7] M. S. Hossain, M. A. A. Bhuiyan, & M. A. R. Ahad, \"Biometric Authentication: A Review,\" International Journal of Computer Science and Network Security, 2017. [8] Jain, A. K., Ross, A., & Nandakumar, K., \"Introduction to Biometrics,\" Springer, 2011.
Copyright
Copyright © 2025 R. K. Poongodi , S. Sudharsan, C. Vinoth. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET66818
Publish Date : 2025-02-03
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

