Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Exploring Cloud Computing Security Challenges Through an enhanced Prototype Model
Authors: Sakti Charan Panda, Dr. Bibhu Kalyan Mishra
DOI Link: https://doi.org/10.22214/ijraset.2024.65476
Certificate: View Certificate
Abstract
Cloud computing is a model that enables convenient, on-demand network access to a shared pool of configurable computing resources, such as networks, servers, storage, applications, and services.. However, cloud computing faces several challenges, particularly in the areas of traffic management, security, and resource allocation. To enhance security in the cloud, various approaches can be employed at different levels, such as securing data, networks, and storage. One promising approach is the use of homomorphic encryption, which allows operations to be performed on encrypted data without requiring decryption or access to the private key.. When the encrypted result of an operation is decrypted, it yields the same outcome as if the operation had been performed on the raw data. This method significantly improves data security as it excludes the cloud provider from key management. Additionally, We propose incorporating proxy re-encryption to further enhance security. This technique prevents ciphertext from being vulnerable to chosen ciphertext attacks, making the system more robust and secure compared to existing solutions.
Introduction
I. INTRODUCTION
Cloud Computing is an organizational technology that leverages the internet and remote servers to facilitate the sharing of computational power and resources for managing data and applications. One of its most attractive features is the "Pay-as-you-go" model, which allows users to pay only for the resources they consume. This model, combined with the ability to create and terminate virtual machines on physical hardware managed by hypervisors, makes cloud computing a cost-efficient and flexible paradigm.
- Additionally, the integration and widespread availability of large volumes of sanitized data across various domains, such as the healthcare sector, offer immense value to researchers and professionals. While cloud computing is rich in features, its core characteristics include:
- Utilizing internet-based services to support business processes.
- Renting IT services on a utility-like basis.
- Availability of diverse cloud vendors.
A. Service Models of Cloud Computing
- Cloud computing operates on three primary SPI (Software, Platform, Infrastructure) models:
- IaaS (Infrastructure as a Service): It gives virtualization content.
- PaaS (Platform as a Service): Offers a platform and environment to develop, test, and manage applications.
- Software as a Service(SAAS): It is the best cloud service model
B. Deployment Models of Cloud Computing
- Public Cloud: Services are hosted by third-party providers and available to multiple users over the internet.
- Private Cloud: Dedicated to a single organization, hosted either on-site or outsourced to a third-party provider.
- Hybrid Cloud: it is the combination of two or models as per customer needs.
- Community Cloud: Shared infrastructure tailored for a group of organizations with similar requirements, hosted on-site or by an external provider.
Depending on their needs, consumers can select and deploy the appropriate cloud service or deployment model.
II. PROBLEM STATEMENT AND OBJECTIVE
Cloud Computing represents a transformative evolution of various existing technologies and approaches to computing. At its core, it decouples data and application resources from the underlying infrastructure while leveraging a utility-based resource allocation model to enhance scalability. This paradigm enables greater collaboration, scalability, availability, agility, and the potential for significant cost reduction for both consumers and businesses. In essence, Cloud Computing refers to the utilization of a diverse range of applications, data, infrastructure, networks, storage, and distributed services. These components can be rapidly integrated, provisioned, deployed, and de-provisioned on demand, following a utility-based model for allocation and deallocation. This approach ensures efficient resource usage and supports dynamic operational needs.
A. Objectives of the Study
The study aims to achieve several objectives, which are outlined below:
- To analyze cloud network attacks and propose effective prevention or mitigation strategies for one of the identified attack types.
- To develop a taxonomy of various types of cloud attacks that have occurred in recent years, along with their associated risks. This includes analyzing categories of attacks that are particularly prevalent in cloud networks under the domain of cloud network security.
- To investigate data security breaches in cloud networks and propose suitable prevention or mitigation strategies to address these issues.
- To examine the reasons for reluctance in adopting Cloud Computing, particularly concerning security and risk perceptions.
- To identify and address the factors hindering cloud adoption in India, focusing on businesses of different sizes—small, medium, and large—to promote greater acceptance and utilization of cloud technologies.
III. METHODOLOGY
A research strategy encompasses all phases of a study that are essential for conducting effective and systematic investigation. This study employs descriptive and statistical methods to analyze the collected data. This section outlines various tasks that address key issues, hypotheses, their interpretation, data collection processes, and methodologies for designing and executing the research. It provides guidance on what, why, and how to gather and evaluate data, along with techniques for formulating results that contribute to drawing meaningful conclusions in the research.
A. Research Methods
The strategy for research utilized in this investigation contains subjective method that include the utilization of electronic mail polls (email), distributed survey over subsequent meet-ups, mobile phone, skype, WhatsApp and one on one meeting communications. Associations and client were chosen dependent on their particular involvement in cloud computing, security and protection angle in cloud, cloud administration, organization just as innovations to follow the fundamental point of the exploration concentrate in discovering an answer for the security issues related to cloud computing.In first phase survey is sent to clients. The polls were thoroughly examined to empower respondents to concur whether to be conveyed, at whatever point needed for whichever extra information. PDA/skype/WhatsApp and one on one meeting cooperation’s directed with many cloud clients too. The meeting connections are semi-organized towards permitting the interviewee respondents free communication of their perspectives.
Watchfulness is continued in data examination, while suitable semi-organized meetings and questions are intended to discover extra theoretical issues and to help with getting free missteps, question in various responses to review questions and meeting. Respondents are given affirmation by the scientist on classification of all that they contributed in the exploration study.
B. Research Approach
As previously said, subjective approach may be the most effective way to conduct an examination study in the exploration sector of computing and information technology. It is anticipated that a portion of the exploration research issues will be addressed by the fundamental investigation of relevant examination, precise meeting, and utilization of records, as a result of the investigation's concept that reports the recent problems that were perceived by specialists. This method helps both type of questions to be used in study. The researcher then applies some of the strategies mentioned to fully achieve the study's objectives by providing appropriate recommendations to conclude and a variety of methods for addressing cloud security and risk challenges.
C. Research Design
Exploration configuration considered being approaches, systems just as strategies utilized while directing a specific report, distinct ideas are created, inspect in an unmistakable methodology. Illustrative methodology which is now and again examines as explorative examination are utilized in this investigation for investigating beneficial thoughts and purposeful entirely on the need to sort various techniques; cloud computing security issues will be radically diminished and annihilated to foster associations execution with suggestions of expected various methodologies and model improvement toward the finish of exploration study discoveries.
D. Research Process
Even if there are various methods in place to guide investigation, each strategy contributes to a series of successes that result in research measurements that are incredibly dependent on one another. Similar guidelines are not always screened in research techniques. As a result, the examination adhered to specific protocols in order to produce an excellent report. The interaction in research includes: presenting the problem as it is presented in the presentation section; refining the exploration plan and inspection through evaluation; collecting and compiling the essential data for the investigation (meetings and overviews); handling and examining the data collected from both mandatory and optional sources of data assortment methodology; and finally, expressing conclusions and revelations that are essential to concluding the study. Eventually,
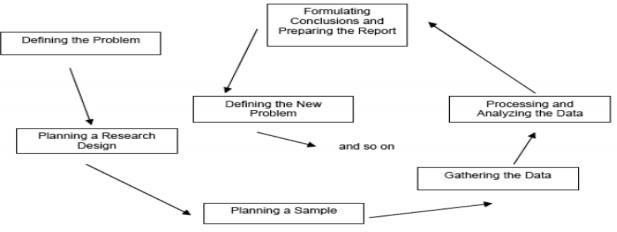
Fig.1: Research Process. [Source: Adopted in Ahmad Sobhani, 2008]
IV. CLASSIFICATION AND METHOD OF DATA COLLECTION
A good report is thought to be distinct, trustworthy, analytical, useful, and heavily supported by sufficient evidence. The data must be derived from bases that are typically arranged in secret using important and optional information [39]. This analysis makes use of both data, although the focus is mostly on the data that has been gathered. Because it enables researchers to make strong, trustworthy, and appropriate decisions that may be used to work on the examination's findings regarding security flaws in SPI administration models, sending models, advancements, and cloud computing in general.
A. Primary Data
Review techniques are the method the researcher uses to get data. Questions are prepared and distributed to a large number of respondents who are chosen from among different cloud technology clients and experts. Approximately 200 questionnaires were taken, however only 178 responses were received. Unfortunately, some were returned as invalid because they were not filled out correctly, and some were filled out incorrectly. Therefore, 100 accurately completed questionnaires were randomly selected and used in the exploration cycles to find the answers to the examination questions and accomplish the research goal.
B. Secondary Data
In order to get knowledge as a matter-of-fact researcher in cloud computing and security, the secondary types of data used in this examination were unquestionably library resources such as diaries, the web, course readings, publications, meetings, and understudy papers. As a result, the material greatly enhanced the examination study's plausibility and the researcher's capacity to fully consider the exploration study region. The papers, distributed diaries, and course and meeting papers are being carefully examined. They contain large and overwhelming articles about information security and information framework technology. To obtain the relevant data required for the inquiry, papers from various regions were used, including those with quantifiable data.
C. Prototype Model
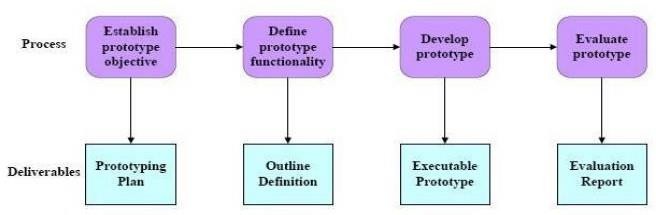
Fig.2 : Stages in Prototype Model. Adapted from [41] Sommerville (2007).
After the results have been analysed, a prototype model will also be employed as part of the procedures and techniques previously mentioned as part of the research plan to create a security model that will help lower the degree of security threats related to cloud computing. To illustrate the value of the created framework or model, a single emphasis from the prototyping model will be used. The model considers making changes and corrections to a framework, then unloading the entire framework and developing a new one that is consistent with the exploratory study's findings. The capabilities of the model will also be demonstrated using a UML Use Case Diagram. The accepted prototyping model includes the four-phase measurements model.
D. Prototype Development
Three technologies that can be used for user interface prototype were identified by an investigation: content-driven prototyping, web-based prototyping, and visual programming languages. In order to create visual rudiments that clients could interact with as the framework performed its tasks or features, content-driven prototyping was used. Therefore, the following tools and languages must be used to create the model for the test: WordPress, Adobe Fireworks, CSS, Ajax, PHP, and MySQL.
UML: Use Case, Sequence and Class Diagrams
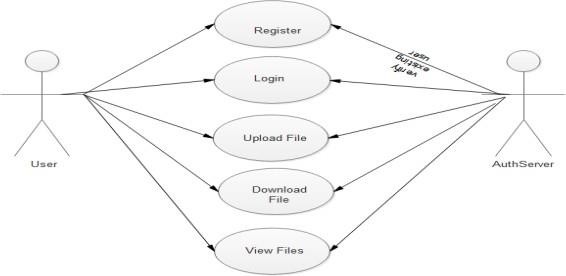
Fig.3 Use Case Diagram for Prototype [Source: Adopted in survey 2018]
Linked together UML is a modelling language that has the ability to display use case charts. Use case outlines are typically used to organise framework features during the inquiry phase of a particular examination focus. As a result, the expert isolates the framework that interests entertainers and the use case using the utilisation case. Characters portrayed by clients of a framework are implied by the entertainers. Furthermore, the utilisation case chart is a simple process for addressing the client's relationship with the framework that illustrates the client's link to the many use cases that include the client.
V. DATA ANALYSIS OUTCOME
Data are gathered to enable the researcher to formulate logical analysis and responses to the study questions. The overview is accompanied with the survey instrument guide that has been distributed for revelations to a small number of respondents who are familiar with cloud computing. Concerns typically centre on security and protection difficulties pertaining to cloud computing innovations, administrations, arrangements, and choosing. A simple illustrative investigation using a variety of questions was used to analyse the study's findings..
Fig.4 Usefulness of Cloud Computing
Question 4 of the overview survey discussed various sorts of cloud computing in which clients can have one of admittance to cloud computing technology through any of the models.
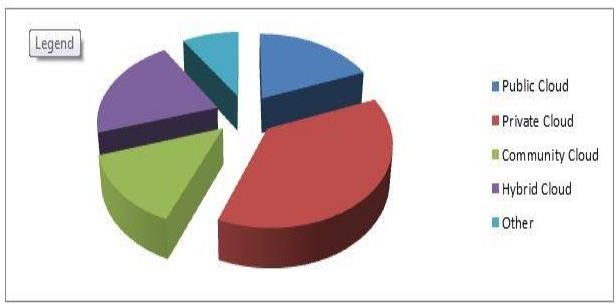
Fig.5 Cloud Deployment Models (Q4)
Result in the underneath figure showed that 43% concurred Cloud Computing further develop execution in business, unequivocally concurred had 21% as those with the assertion as per result, Neutral had 31%, emphatically differ had 2%, though differ had 3%.
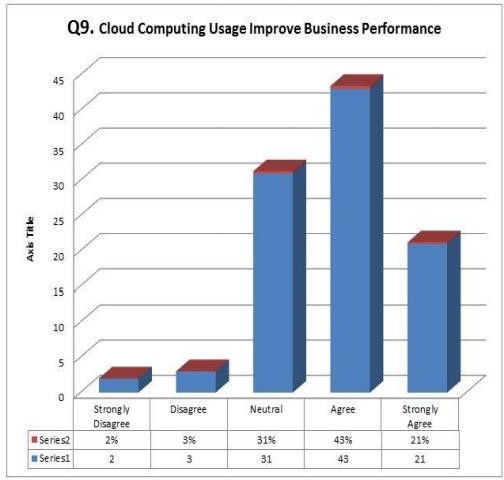
Fig.6 Cloud Computing Usage Improves Business Performance
A. The Issue of Adherence to Data Security Control
On the Issue of Adherence to Data Security Control as concurred in Services Level Agreements (SLA) the reactions from respondents is that 16% said Yes, 49% said No and 35% of the respondent addressed Maybe, that is to say they don't know on whether the Cloud Service Provider comply to such understanding rigorously or not.
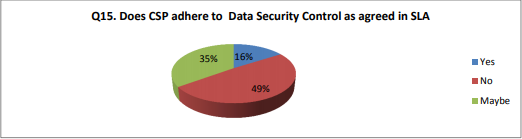
Fig.7 CSP adherence to Data Security Control as agreed in SLA
B. Cloud Service Providers (CSP) Perspective and Users Perspective
On the security worries with respect to relationship from Cloud Service Providers (CSP) Perspective and Users Perspective, both the suppliers and clients are having both data & relation Storage. Most particular the protection and security issues, so reactions are introduced after investigation of the Question from the Survey structure which shows 62% of the reacted consider there is solid direct relationship from the two players and 38% are of the assessment of in a roundabout way related as displayed in the figure beneath
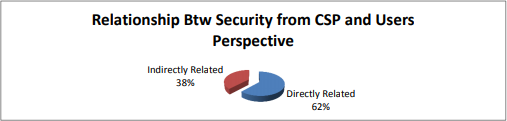
Fig.8 Relationship between security from CSP and User Perspective
C. Statistical Result of the Hypothesis and Correlation Analysis
Question 7, 9 and 10 were used in describing the hypotheses 1, 2 and 3 respectively.
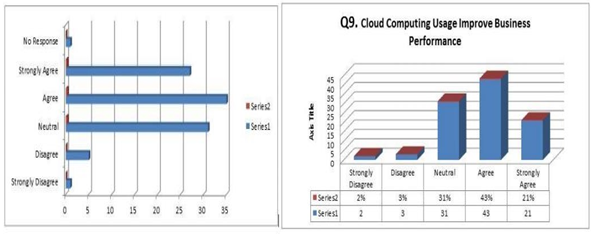
Fig.9 Question 7 for Hypothesis 1 Fig.10 Question 9 for Hypothesis 2
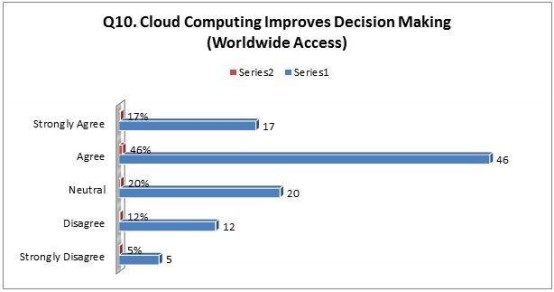
Fig.11 Question 10 for Hypothesis 3
Conclusion
Although cloud computing offers many advantages to users, many clients are hesitant to adopt it due to security concerns. Additionally, the specialized co-op may experience problems with unapproved admission. Accordingly, we developed a different structure by suggesting a combination of encryption and jumbling method in order to resolve the issues that were recognized with both the client and the expert co-op. Data that is on change in the network is secured before being sent via cloud encryption, allowing the client to ensure the privacy of his data. We have suggested a secure storage cutoff that keeps track of client keys and the hash of the archive that is transmitted to the employee productive obscurity technique is suggested for cloud providers, which ensures that the client\'s privileged information, such as contact details and secret keys, is not compromised by third parties. Calculation tools are also organized to ensure that actions are carried out efficiently. Additionally, we have provided a detailed analysis of the outcome produced by the implemented model while taking important constraints like time and security into account. According to the comparison of the models with and without confusion, even though obscurity may increase over time, it becomes irrelevant to the cloud provider when considering client data protection. instead of using the encryption measure on the worker that some models suggest. A. Future Work The ends of the finished exploration have been revealed in the preceding section. The specialist was able to identify the potential future scope of the investigation based on the knowledge gained during the assessment. Bearings are comparable to the following. 1) The benefits of the proposed lightweight encryption plot are evaluated in relation to large amounts of data. Additional research is necessary with Map Reduce the worldview of programming with massive amounts of data. 2) It is intriguing to approve the suggested instruments in the IoT-incorporated use cases like smart home, smart city, and smart transportation, given that the Internet of Things (IoT) is one of the sources of massive data with asset-obligated linked devices..
References
[1] NIST National Institute of Standard and Technology, U.S Department of Commerce. Guidelines on Security and Privacy in Public Cloud Computing. Special Publication [Home Page on the Internet] 2011. [Cited on 15th December, 2016] Available from http://csrc.nist/specialpublication/nistpubs/800-144.pdf [2] Bharat Bhargava (2012), Security and Privacy Issues in Distributed System and Cloud Computing. Seminar Lecturer, Computer Science Department, Purdue University, West Lafayette, Indiana, USA. 2012, [Cited on 15th December, 2016] Available from www.cs.purdue.edu/homes/bb [3] Rabi P. P, Manas R P, Suresh Chandra S. Cloud Computing: Security Issues and Resaerch Challenges, 2011. Published in IRACST-International Journal of Computer Science and Information Technology & Security (IJCSITS) Vol.1, No.2, December 2011. [4] Usman Ahmad U., Shah Shoib F. and Mavera U. Security and Privacy issues in Cloud Computing and Providing Platform for E-learning, 2014 Published in International Jounal of Information and Computation Technology. ISSN 0974-2239 Volume 4, Number 5 [5] Shilpashree S., David Q. L., Athanasios V. et al. Security and Privacy in Cloud Computing: A Survey. Parallel & Cloud Computing, 2013. 2 (4), 126-149. New York, NY: American V-King Scientific Publishing, LTD. [Cited on 2nd January, 2017] Available from http://opus.ipfw.edu/compsci_facpubs/44 [6] Sapna M., MM Chaturvedi. Privacy and Security in Mobile Cloud Computing: Review, 2013. Published by International Journal of Computer Applications (0975-8887) Volume 80-No11, October 2013. [7] Ms. Rupali R. K., Ms Rinkle C. P. Data Security and Privacy Protection Issues in Cloud Computing, 2015. Published in International Journal of Computer Science and Information Technology Research ISSN 2348-120X (online) Vol. 3, Issue 2, pp:(1130-1134), Month: April-June 2015, [Cited on 23rd January 2017] Available from www.researchpublish.com [8] Shufen Z., Hongcan Y., Xuebin C. Research on Key Technologies of Cloud Computing. 2012 International Conference on Medical Physics and Biomedical Engineering. Physics Procedia 33 (2012) pp:1791 - 1797. [Cited on 1st February, 2017] Available from www.sciencedirect.com [9] Sean C., Kevin C. Cloud Computing Technologies, 2012. Published in International Journal of Cloud Computing and Services Science (IJ-CLOSER) Vol.1, No2, June 2012, pp. 59-65 ISSN: 2089-3337. [10] Shrinivas A. An Overview of Cloud Deployment Models and Security Issues in Cloud, 2016. Published in International Journal of Computer Application (2250- 1797) Volume Six (6), No. Four (4), July – August 2016. [Cited on 8th February, 2017] [11] Nikita G. and Toshi S. Cloud Computing – SPI Framework, Deployment Models and Challenges, 2014. Published by International Journal of Emerging Technology and Advanced Engineering, Volume 4, Special Issue 1, February 2014, International Conference on Advanced Development in Engineering and Technology (ICADET-14), India. [Cited on 28th February] Available from www.ijetae.com [12] Al-Muslim W. and Li C. User Privacy and Security issues in Cloud computing, 2016. Published by Internation Journal of Security and Applications Vol. 10, No 2, (2016) pp 341-352. [13] Awodele O. et al. Big Data and Cloud Computing Issues, 2016. Published in International Journal of Computer applications (0975-8887) volume 133 – No. 12, January 2016. [Cited on 3rd March, 2017] [14] Nancy J., and Sakshi C. Overview of Virtualization in Cloud Computing, 2016. Published by IEEE, in Colossal Data Analysis and Networking (CDAN), Symposium on 18-19 March 2016. [Cited 2nd May, 2017] [15] Chakradhara R., Mogasala L., and Ramesh K.Cloud: Computing Services and Deployment Models, 2013. Published in International Journal of Engineering and Computer Science ISSN: 2319-7242 Volume 2 Issue 12, Dec. 2013 Page No.3389-3392 [Cited 2nd May, 2017] Available online from www.ijecs.in [16] Shrinivas A. An Overview on Cloud Deployment Models and Security issues in Cloud, 2016. Published by International Journal of Computer Application (2250-1797) Volume 6 – No. 4 July – August 2016. [Cited 7th May, 2017]
Copyright
Copyright © 2024 Sakti Charan Panda, Dr. Bibhu Kalyan Mishra. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET65476
Publish Date : 2024-11-23
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

