Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Crime Predictive Model for Hotspot Mapping
Authors: Suryawanshi Sejal, Bhadane Hemangi, Patil Bhagyashri, Chaudhari Shruti
DOI Link: https://doi.org/10.22214/ijraset.2024.63305
Certificate: View Certificate
Abstract
In contemporary law enforcement, the need for proactive strategies to combat crime and ensure public safety is paramount. This paper presents the development and implementation of a predictive modeling framework aimed at identifying crime hotspots and optimizing resource allocation for law enforcement agencies. The model leverages historical crime data, geographical information, and socio- economic factors to forecast areas at elevated risk of criminal activity. Through a multi-stage process encompassing data collection, preprocessing, feature engineering, and model training, the predictive model enables law enforcement agencies to anticipate and prioritize areas with the highest likelihood of crime occurrence. By strategically deploying resources to these identified hotspots, law enforcement agencies can intervene early, deter criminal activity, and reduce overall crime rates. This research contributes to the advancement of evidence-based policing practices by offering a scalable framework for crime hotspot mapping that prioritizes efficiency, effectiveness, and community partnership.
Introduction
I. INTRODUCTION
Hotspot mapping in crime analysis refers to the process of identifying specific geographic areas where criminal activities are concentrated. By pinpointing these crime hotspots, law enforcement agencies can concentrate their resources and interventions more effectively, leading to targeted crime prevention efforts. Traditionally, hotspot mapping has been carried out through manual analysis of crime data and simple visualizations. However, this manual approach has several limitations. It is time-consuming, prone to human error, and may not capture complex patterns or relationships in the data effectively. Additionally, manual hotspot mapping may not scale well to large datasets or provide real-time insights needed for proactive policing. In recent years, there has been a growing interest among researchers and law enforcement agencies in leveraging machine learning techniques for crime prediction and hotspot mapping. Machine learning algorithms have the capability to analyze large volumes of data, including historical crime data, geographical information, socio-economic factors, and other relevant variables. By processing and learning from this data, machine learning models can identify complex patterns, trends, and relationships that may not be apparent through traditional analysis methods.[5]
II. LITERATURE SURVEY
A. Review of Existing Systems
At present, ML is being used by law enforcement and other government agencies to predict crime. Predictive policing software like Crime anticipation system, PreCobs, PredPol, and Hunchlab utilize machine learning algorithms to analyze historical crime data and make predictions about future criminal activity. These systems are designed to assist law enforcement agencies in making more informed decisions about resource allocation and crime prevention strategies. One of the main benefits of these systems is their potential to improve the efficiency of law enforcement operations. By analyzing patterns in past crime data, predictive policing software can identify high-risk areas and times, allowing law enforcement agencies to allocate their resources more effectively. For example, they can deploy patrols to areas where crime is more likely to occur, or implement targeted interventions to address specific types of crime.[3]
However, it's important to recognize that these systems are relatively new and may have limitations that can affect their effectiveness and impact on crime rates. Some of these limitations include:
- Data Bias: Predictive policing algorithms rely on historical crime data to make predictions about future crime patterns. If the historical data used to train these algorithms is biased or reflects existing disparities in policing practices, the predictions generated by the system may perpetuate or even exacerbate existing inequalities in law enforcement.
- Lack of Transparency: Many predictive policing algorithms operate as "black boxes," meaning that the inner workings of the algorithms are not fully transparent or understandable to the public, including law enforcement agencies themselves. This lack of transparency can make it difficult to assess the reliability and accuracy of the predictions generated by these systems.
- Ethical Concerns: The use of predictive policing algorithms raises ethical concerns related to privacy, civil liberties, and due process. There is potential for these systems to disproportionately target certain communities or individuals based on factors such as race, socioeconomic status, or past interactions with law enforcement.
- Evaluation Challenges: Assessing the impact of predictive policing on crime rates can be challenging due to the complex nature of crime causation and the multitude of factors that influence crime trends. It can be difficult to isolate the effects of predictive policing from other concurrent interventions or external factors that may also be affecting crime rates.[7]
III. PROPOSED SYSTEM
The proposed system involves harnessing machine learning algorithms like Random Forest, K-means, and Support Vector Machine to analyze a dataset containing details about crime incidents in India, including location, date, type of crime, latitude, and longitude. These algorithms are trained on historical crime data to recognize patterns and associations within the dataset, enabling them to predict crime hotspots based on various input features. Once trained, the models can generate hotspot maps highlighting areas with a higher likelihood of criminal activity, thereby aiding law enforcement agencies in allocating resources more effectively and implementing targeted crime prevention strategies. Evaluation of the models' performance ensures their accuracy in predicting crime hotspots, thus facilitating proactive measures to enhance public safety and security.[8]
It is important to ensure that the collected data is reliable, accurate, and representative of the target region or jurisdiction. Data preprocessing steps may be required to clean, transform, and normalize the data before using it for model training and prediction. Additionally, privacy and security considerations should be addressed to protect sensitive information within the data. Furthermore, privacy and security considerations are paramount to protect sensitive information contained within the dataset, such as personal details of victims or suspects. Implementing robust data security measures, such as encryption and access controls, helps safeguard confidentiality and prevent unauthorized access or misuse of the data. Compliance with data protection regulations and ethical guidelines is essential to ensure that individuals' privacy rights are respected throughout the data collection, storage, and analysis processes.[1]
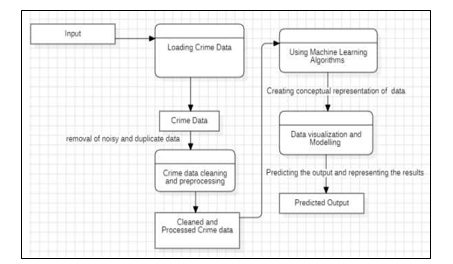
IV. REQUIREMENT ANALYSIS
Requirement analysis for crime predictive models for hotspot mapping using machine learning typically involves several methods and techniques to gather, analyze, and define system requirements. Here are some commonly used methods in requirement analysis:
- Stakeholder Interviews: Conducting interviews with various stakeholders, such as law enforcement officials, crime analysts, and end users, to understand their needs, expectations, and domain-specific knowledge related to crime prediction and hotspot mapping.
- Surveys and Questionnaires: Distributing surveys or questionnaires to stakeholders to collect quantitative and qualitative data about their requirements, preferences, and priorities regarding the crime predictive model.
- Observation and Ethnography: Observing and studying the work environment, processes, and interactions of stakeholders involved in crime analysis and prediction. This method provides insights into existing practices, challenges, and opportunities for improvement.
- Document Analysis: Analyzing existing documentation, such as crime reports, data specifications, or policy documents, to extract relevant information about data sources, data formats, system interfaces, and regulatory requirements.
- Use Case Analysis: Identifying and analyzing typical use cases or scenarios where the crime predictive model would be utilized. This helpsin understanding the context of system usage, user interactions, and desired outcomes.
- Data Analysis: Analyzing available crime data, including historical crime records, spatial data, weather data, and demographic data, to identify patterns, correlations, and factors that influence crime occurrences and hotspot formation.
- Prototype Development: Creating prototypes or mock-ups of the crime predictive model to gather feedback from stakeholders and validate requirements. This iterative process helps refine and validate the system’s functionality and user interface.
- Brainstorming and Workshops: Facilitating group discussions, brainstorming sessions, and workshops with stakeholders to generate ideas, identify system requirements, and clarify expectations. This collaborative approach fosters knowledge sharing and consensus building.
- Requirement Prioritization: Prioritizing requirements based on their importance, feasibility, and impact on the overall system. Techniques like MoSCoW (Must-have, Should-have, Could-have, Won’t have) or Analytic Hierarchy Process (AHP) can be used for prioritization.
It’s important to employ a combination of these methods to gain a comprehensive understanding of stakeholders’ needs, system constraints, and the operational context for the crime predictive model. The iterative and collaborative nature of requirement analysis helps ensure that the developed system meets the expectations and requirements of its intended users.[6]
V. RISK ASSESSMENT
Risk assessment is an important step in the development and implementation of a crime predictive model for hotspot mapping. It helps identify potential risks and vulnerabilities that may affect the project’s success and allows for the implementation of risk mitigation strategies. Here are some common risks to consider in the context of a crime predictive model for hotspot mapping.
A. Data Quality and Availability
Risk: Insufficient or poor-quality crime data may lead to inaccurate predictions.
Mitigation: Implement data validation and cleaning processes. Establish data partnerships with reliable sources. Have backup plans in case of data unavailability.
B. Model Accuracy and Performance
Risk: The predictive model may not achieve the desired accuracy or performance
Metrics. Mitigation: Use appropriate evaluation metrics and validation techniques during model development. Continuously monitor and refine the model based on feedback and performance analysis.
C. Bias and Fairness
Risk: The model may exhibit bias or unfairness, resulting in discriminatory or unjust outcomes. Mitigation: Carefully select training data to ensure representation and fairness. Regularly assess and address bias issues. Conduct fairness audits and implement corrective measures.
D. Ethical Considerations
Risk: Unintended ethical implications may arise from the use of the predictive model, such as privacy concerns or misuse of sensitive information.
Mitigation: Adhere to ethical guidelines and legal regulations. Implement privacy protection measures. Conduct regular ethical reviews and engage with relevant stakeholders.
E. Scalability and Performance
Risk: The system may encounter performance issues or fail to scale effectively when dealing with large datasets or high-demand scenarios.
Mitigation: Optimize algorithms and system architecture for scalability. Conduct stress testing to identify potential bottlenecks. Plan for infrastructure scalability as the project grows.
F. User Acceptance and Adoption:
Risk: Users may have difficulty understanding or accepting the predictive model’s outputs, leading to low adoption rates or resistance to change.
Mitigation: Involve end-users in the design and development process.
G. Security and Privacy:
Risk: The system may be vulnerable to security breaches or unauthorized access, potentially compromising sensitive crime data. Mitigation: Implement robust security measures, including data encryption, access controls, and regular security audits. Comply with relevant data protection regulations. It’s crucial to conduct a thorough risk assessment specific to your project, considering its unique context and requirements. Regularly monitor and reassess risks throughout the project’s lifecycle, implementing mitigation strategies and adapting as needed.[4]
VI. APPLICATIONS
Applications for crime predictive models for hotspot mapping are diverse and can benefit various stakeholders involved in crime prevention, law enforcement, urban planning, and public safety. Here are some applications:
- Law Enforcement: Police departments can utilize predictive models to optimize resource deployment by identifying areas with a higher likelihood of criminal activity. This allows for strategic placement of patrol officers and proactive measures to deter crime.
- Community Safety Initiatives: Community organizations and local authorities can use hotspot mapping to target crime prevention efforts in areas identified as high-risk. These efforts may include neighborhood watch programs, community policing initiatives, or interventions to address environmental factors contributing to crime.
- Urban Planning: Predictive models can inform urban development strategies by highlighting areas with recurring patterns of criminal activity. This information assists city planners in making informed decisions regarding infrastructure development, zoning regulations, and the creation of safer public spaces.
- Resource Allocation: Efficient allocation of resources for crime prevention and public safety initiatives is facilitated through hotspot mapping. This includes budget allocation for law enforcement agencies, funding for community programs aimed at reducing crime, and prioritization of areas for infrastructure improvements.
- Emergency Response Planning: Emergency services can benefit from predictive models by anticipating areas with higher emergency call volumes due to criminal incidents. This enables emergency responders to prepare for potential incidents and allocate resources effectively to ensure timely and efficient response.
- Business and Tourism: Businesses can use hotspot mapping data to assess the safety of potential locations for new ventures or expansions. Similarly, tourism agencies can provide safety recommendations to visitors based on crime prediction insights, enhancing their experience and safety.
- Public Awareness Campaigns: Sharing hotspot mapping results with the public fosters awareness about crime patterns and encourages community involvement in crime prevention efforts. This transparency facilitates collaboration between residents, law enforcement, and local authorities to address safety concerns collectively.
- Research and Policy Development: Researchers and policymakers can analyze historical crime data alongside predictive modeling results to evaluate past interventions' effectiveness and develop evidence-based policies for crime prevention and public safety in the future.[1]
The crime predictive models for hotspot mapping offers valuable insights that can be applied across various domains to enhance safety, resource allocation, and community well-being.
VII. SYSTEM SPECIFICATION
System Specification for crime predictive models for hotspot mapping using machine learning typically includes the following components:
- System Overview: This outlines the purpose of the crime predictive model system, who will use it, and why.
- Functional Requirements: This section details what the system needs to do, including how it collects and processes data, develops models, makes real-time predictions, visualizes results, and interacts with users. It also covers scalability, integration with other systems, security measures, and documentation.
- Non-Functional Requirements: These are qualities the system must have, like reliability, ease of maintenance, usability, compatibility with other systems, and adherence to regulations or standards.
- Data Requirements: Describes the types of data needed for the model, including crime, geographic, temporal, environmental, and demographic data.
- System Architecture: This section explains how the system is structured, including its components, how they work together, and any external systems or databases it interacts with.
- Algorithm Selection: Specifies which machine learning algorithms will be used for building the model and why they're suitable for hotspot mapping and crime prediction.
- Performance Metrics: Defines how the model's performance will be measured, including metrics like accuracy, precision, recall, and the desired thresholds for these metrics.
- User Interface Design: Provides guidelines for designing the system's interface, focusing on usability, interactivity, and clear visualization of predicted crime hotspots.
By addressing each of these components, the system specification ensures that the crime predictive model meets the needs of its users and performs effectively and reliably.[2]
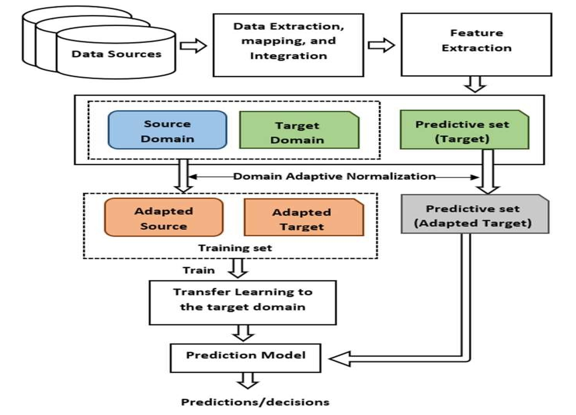
Conclusion
Many law enforcement agencies and crime reduction agencies use heat maps to identify crime patterns. Using previous data, the heat map can determine where the most crime is occurring and begin the decision-making process on what is the best safety bridge and protection program. There are many mapping techniques that can be used to create hotspot maps, but to date there is no research to determine whether they can accurately predict future terrorist attacks. This project introduces the accuracy index as a measure of the predictive power of crime-fighting technology and determines whether there is a difference between the relevant hotspot methods that medical professionals often use in their ability to predict crime patterns. The project also determined whether the predictive power of hotspot maps differs for different types of crime.
References
[1] Mohler, G. O., Short, M. B., Brantingham, P. J., Schoenberg, F. P., & Tita, G. E. (2011). Self-exciting point process modeling of crime. Journal of the American Statistical Association, 106(493), 100-108. [2] Chainey, S., & Ratcliffe, J. (2005). GIS and crime mapping. John Wiley & Sons. [3] Gerber, M. S., & Johnson, B. D. (2010). Rigor and relevance: A research agenda for the field of crime forecasting. Crime Prevention and Community Safety, 12(3), 165-187. [4] Mohler, G., Raje, R., Carter, J., & Valasik, M. (2019). Crime analytics: Identifying, predicting, and preventing crime. Routledge. [5] Braga, A. A., Papachristos, A. V., & Hureau, D. M. (2010). The concentration and stability of gun violence at micro places in Boston, 1980– 2008. Journal of Quantitative Criminology, 26(1), 33-53. [6] Mohler, G. O., Raje, R., Carter, J., Valasik, M., & Brantingham, P. J. (2016). A penalized likelihood method for estimating parameters of a self-exciting point process model for crime data. Journal of the Royal Statistical Society: Series A (Statistics in Society), 179(3), 831-852. [7] Ratcliffe, J. H., Taniguchi, T., & Taylor, R. B. (2009). The crime reduction effects of public CCTV cameras: A multi?method spatial approach. Justice Quarterly, 26(4), 746-770. [8] Johnson, S. D., Bowers, K. J., & Hirschfield, A. F. (1997). New insights into the spatial and temporal distribution of repeat victimization. British Journal of Criminology, 37(2), 224-241.
Copyright
Copyright © 2024 Suryawanshi Sejal, Bhadane Hemangi, Patil Bhagyashri, Chaudhari Shruti. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET63305
Publish Date : 2024-06-15
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

