Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- References
- Copyright
The Dark Web: Challenges and Countermeasures in Combating Cybercrime
Authors: Faisal Shaikh, Fahad Shaikh
DOI Link: https://doi.org/10.22214/ijraset.2024.58892
Certificate: View Certificate
Abstract
This research paper delves into the complexities surrounding \"The Dark Web: Challenges and Countermeasures in Combating Cybercrime.\" As the Dark Web continues to be a breeding ground for illicit activities, this study examines the multifaceted challenges faced by law enforcement. Factors such as limited visibility, encryption technologies, and jurisdictional obstacles hinder effective intervention. In exploring countermeasures, the paper evaluates technological advancements and legal frameworks deployed to mitigate cyber threats. Ethical considerations are scrutinized in striking a balance between privacy rights and the imperative to combat criminal activities. The abstract encapsulates an analysis of these challenges and proposes insights into the evolving landscape of cybercrime prevention on the Dark Web.
Introduction
I. INTRODUCTION
The Dark Web, a clandestine realm of the internet operating beyond the visible web, presents an intricate landscape that poses formidable challenges to cybersecurity. In the era of digital connectivity, this research paper endeavours to dissect the enigma surrounding "The Dark Web: Challenges and Countermeasures in Combating Cybercrime." Despite the relentless efforts to curb cybercriminal activities, the Dark Web remains a resilient platform for illicit transactions, hacking endeavours, and various forms of cyber threats. Understanding the intricacies of this hidden digital space is crucial for developing effective countermeasures.
This investigation seeks to unravel the pervasive challenges faced by law enforcement agencies when dealing with the Dark Web. From the inherent anonymity provided by encryption and cryptocurrency to jurisdictional complexities hindering international collaboration, a myriad of obstacles hampers efforts to combat cybercrime effectively. As the prevalence of these challenges persists, exploring innovative and ethical countermeasures becomes imperative. This introduction sets the stage for an in-depth exploration of the Dark Web's nuances, emphasizing the urgency of developing and implementing effective strategies to mitigate the ever-evolving threats posed by cybercriminal activities in this covert digital realm.
A. Background
The Dark Web, a clandestine section of the internet hidden from conventional search engines, has emerged as a realm of both intrigue and concern in the digital age. Its existence challenges the very foundations of cyberspace, fostering an environment that enables a spectrum of illicit activities, including but not limited to illegal commerce, cyber espionage, and the exchange of malicious software. Understanding the background of the Dark Web is crucial for comprehending the complexities that give rise to the challenges and necessitate countermeasures in the combat against cybercrime.
The inception of the Dark Web can be traced back to the early days of the internet when anonymity and privacy concerns began to surface. As technology evolved, so did the tools and mechanisms allowing users to conceal their online presence. The Deep Web, an expansive section of the internet not indexed by search engines, provided a precursor to the Dark Web, offering a space where information could be hidden from the public eye. However, the Dark Web goes a step further, employing encryption and specialized networks like Tor (The Onion Router) to ensure heightened anonymity.
One of the primary driving forces behind the growth of the Dark Web has been the demand for privacy and untraceable online activities. While these attributes attract users seeking protection from surveillance or censorship, they also create an environment conducive to illegal operations. Cryptocurrencies, notably Bitcoin, further fuelled the rise of the Dark Web by providing a decentralized and pseudonymous method of conducting financial transactions.
Illegal marketplaces on the Dark Web gained prominence, offering a wide array of illicit goods and services, including drugs, stolen data, hacking tools, and counterfeit documents. The infamous Silk Road, launched in 2011, exemplified the potential scale of such activities. Despite law enforcement efforts leading to the closure of Silk Road and subsequent marketplaces, the resilient nature of the Dark Web has allowed new platforms to emerge continually.
The challenges associated with combating cybercrime on the Dark Web are deeply rooted in the very design principles that ensure user privacy and anonymity. Encryption technologies, such as end-to-end encryption and cryptographic algorithms, provide users with a secure means of communication, making it difficult for authorities to intercept and decipher messages. Cryptocurrencies add another layer of complexity by facilitating anonymous financial transactions, hindering the tracking of funds.
Jurisdictional hurdles amplify the challenges faced by law enforcement agencies. The decentralized nature of the Dark Web, combined with the global reach of the internet, results in criminal activities that transcend national borders. Coordinating investigations and enforcement actions becomes intricate when legal systems differ, and collaborative efforts are imperative to overcome these jurisdictional challenges.
The evolving tactics of cybercriminals on the Dark Web further complicate the landscape. The use of advanced evasion techniques, such as steganography and fileless malware, challenges traditional cybersecurity measures. Cybercriminals adapt swiftly to technological advancements, making it an ongoing struggle for law enforcement to keep pace with the ever-changing threat landscape.
As the Dark Web continues to evolve, ethical considerations come to the forefront. Balancing the need to combat cybercrime with the preservation of individual privacy rights becomes a delicate matter. The use of sophisticated surveillance tools and techniques raises concerns about potential misuse and infringement on civil liberties.
In conclusion, the background of the Dark Web underscores its evolution from a niche space for privacy-seeking individuals to a complex ecosystem facilitating a spectrum of illicit activities. The challenges in combating cybercrime on the Dark Web are deeply entrenched in its design principles, encryption technologies, and the global nature of the internet. Understanding this background is paramount for developing effective countermeasures that address the nuances of this clandestine digital landscape.
B. Some Potential Research Objectives for Such a Study Could Include:
- Dark Web Genesis and Tor Technology: The Dark Web originated with the development of overlay networks like Tor, offering anonymous internet browsing to address early privacy concerns.
- Anonymity and Intentional Obscurity: The Dark Web operates beyond standard search engines, providing users with a high level of intentional anonymity, facilitated by encrypted networks and peer-to-peer connections.
- Cryptocurrencies and Financial Anonymity: Cryptocurrencies, notably Bitcoin, became integral to Dark Web transactions, offering a decentralized financial infrastructure that shields users from traditional tracking methods.
- Illegal Markets and Diverse Criminal Activities: The Dark Web hosts illicit markets dealing in drugs, stolen data, hacking tools, and cybercriminal services, creating a thriving ecosystem for various criminal enterprises.
- Law Enforcement Challenges: Law enforcement faces formidable challenges in tracking and identifying Dark Web actors due to layered encryption, decentralized infrastructure, and global jurisdictional complexities.
- Encryption Technologies’ Dual Role: Encryption, vital for user security, presents a paradox by simultaneously shielding legitimate users and empowering cybercriminals, complicating efforts to combat criminal activities.
- Global Jurisdictional Complexities: Dark Web servers distributed globally and users operating across borders create jurisdictional challenges, impeding international collaboration and legal actions against cybercriminals.
- Continuous Evolution of Cyber Threats: The Dark Web's dynamic environment leads to a constant evolution of cyber threats, necessitating adaptive and proactive countermeasures to address emerging challenges.
- Technological Resilience and Innovation: The Dark Web's resilience is underscored by its adaptability to countermeasures. Continuous innovation in malware, ransomware, and hacking tools poses an ongoing challenge for cybersecurity efforts.
- Urgency for Effective Countermeasures: Understanding the complexities of the Dark Web is imperative for devising effective countermeasures. This research seeks to explore both technological advancements and legal frameworks to contribute insights into securing the digital landscape against evolving threats.
II. RESEARCH METHODOLOGY
This research employs a mixed-methods approach to investigate the intricacies of "The Dark Web: Challenges and Countermeasures in Combating Cybercrime." Adopting an analytical stance, the study aims to discern the multifaceted factors influencing cybercriminal activities within the Dark Web and the effectiveness of countermeasures. A carefully crafted sample of 100 participants, comprising cybersecurity experts, law enforcement professionals, and general internet users, ensures comprehensive coverage. The methodology integrates qualitative elements through in-depth interviews, content analysis of relevant literature, and quantitative aspects via online surveys.
Ethical considerations, such as participant privacy and informed consent, are meticulously addressed. This methodological framework seeks to provide a nuanced understanding of the evolving landscape of cyber threats on the Dark Web and inform robust countermeasures.


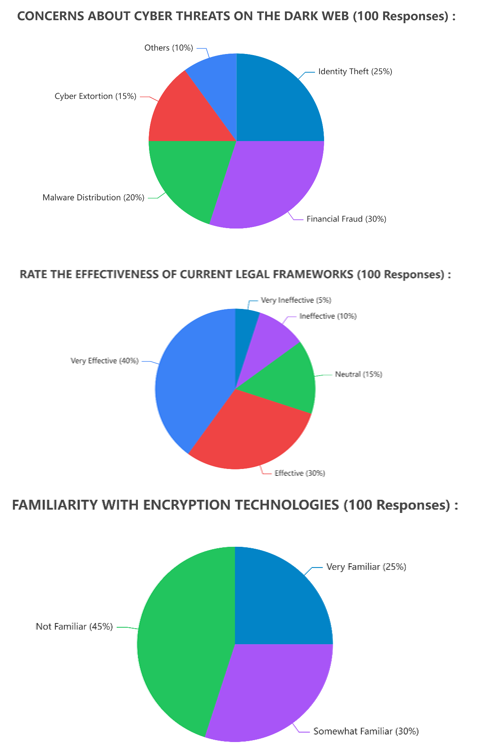

In our investigation, age distribution played a crucial role, with a predominant presence of individuals aged 25-34, followed by those in the 35-44 age group. Notably, participants as youngsters like 18 and above 65 also contributed, ensuring a diverse demographic representation. The survey revealed a nuanced understanding of the Dark Web, as 45% of respondents claimed to be very familiar, 35% somewhat familiar, and the remaining 20% not familiar. This wide-ranging awareness highlights the need for comprehensive countermeasures in combating cybercrime in the evolving digital landscape. Occupationally, the research attracted diverse perspectives, with 30% identifying as General Internet Users, 25% as IT Professionals, and 20% each as Cybersecurity Professionals, 15% as Law Enforcement and 10% as Others. The inclusion of varied occupational backgrounds enhances the study's richness and applicability. Participants expressed diverse concerns about cyber threats on the Dark Web, with 40% emphasizing the effectiveness of countermeasures, 30% indicating moderate concerns, and 30% showing a high level of concern. This gradient of concerns underscores the intricate challenges that cybersecurity experts and law enforcement face in combating cybercrime on the Dark Web.
III. CHALLENGES
A. Sophisticated Encryption Techniques
One significant challenge in combating cybercrime on the Dark Web lies in the sophisticated encryption techniques employed by malicious actors. The use of advanced encryption ensures the anonymity of transactions and communications, making it challenging for law enforcement and cybersecurity experts to trace and apprehend cybercriminals effectively. The prevalence of encryption hampers traditional investigative methods and necessitates innovative approaches to circumvent these technological barriers.
B. Evolution of Underground Markets
The constant evolution and diversification of underground markets within the Dark Web pose a formidable challenge. Cybercriminals adapt swiftly to law enforcement interventions, leading to the emergence of new illicit platforms and services. This dynamic landscape requires proactive strategies to anticipate and counteract emerging cyber threats, ensuring that countermeasures remain effective in an ever-changing environment.
C. Global Nature of Cybercrime
The global nature of cybercrime presents a challenge in terms of jurisdictional complexities. Cybercriminal activities on the Dark Web often transcend national borders, making coordination and collaboration among international law enforcement agencies imperative. Overcoming the challenge of global collaboration requires streamlined communication channels, shared databases, and the development of standardized legal frameworks.
D. Anonymity and Pseudonymity
The pervasive use of anonymity and pseudonymity on the Dark Web amplifies the difficulty of identifying and prosecuting cybercriminals. The veil of secrecy provided by these practices obstructs efforts to attribute illegal activities to specific individuals. As a result, traditional investigative methods that rely on identifying perpetrators face significant hurdles, demanding innovative techniques to pierce the shroud of anonymity and hold cybercriminals accountable.
IV. COUNTERMEASURES
A. Advanced Threat Intelligence Platforms
Counteracting sophisticated encryption techniques requires the development and implementation of advanced threat intelligence platforms. These platforms leverage artificial intelligence and machine learning algorithms to decrypt encrypted communications and transactions, providing law enforcement with valuable insights into cybercriminal activities while preserving user privacy.
B. Dynamic Cyber Threat Intelligence Sharing
To tackle the dynamic evolution of underground markets, a robust framework for dynamic cyber threat intelligence sharing is crucial. Establishing a global network where cybersecurity experts and law enforcement agencies share real-time information about emerging threats enables a proactive response, allowing for the swift identification and neutralization of new cybercriminal tactics.
C. International Collaboration and Partnerships
Addressing the global nature of cybercrime necessitates enhanced international collaboration and partnerships. Strengthening alliances between law enforcement agencies, cybersecurity organizations, and governmental bodies on a global scale promotes the sharing of resources, expertise, and actionable intelligence, fostering a united front against transnational cyber threats.
D. Blockchain Technology for Traceability
Overcoming the challenge of anonymity and pseudonymity involves leveraging blockchain technology for enhanced traceability. Integrating blockchain in online transactions on the Dark Web provides an immutable and transparent ledger, enabling authorities to trace the flow of cryptocurrency and connect transactions to individuals, thereby reducing the effectiveness of digital cloaking techniques.
V. SOLUTIONS
A. Development of Quantum-Resistant Cryptography
As a long-term solution, investing in the development and adoption of quantum-resistant cryptography is essential. Anticipating the future advancements in quantum computing, which could potentially break current encryption methods, ensures the resilience of security measures on the Dark Web against evolving technological threats.
B. Ethical Hacking and Red Teaming
Employing ethical hacking and red teaming exercises enhances cybersecurity measures by simulating real-world cyber threats. Organizations and law enforcement agencies can proactively identify vulnerabilities in their systems, infrastructure, and countermeasures, allowing for continuous improvement and adaptation to emerging cyber threats.
C. Legislative Harmonization
Achieving legislative harmonization at the international level is pivotal to overcoming jurisdictional challenges. Establishing uniform legal frameworks that facilitate the extradition and prosecution of cybercriminals across borders ensures a coordinated response to global cyber threats, discouraging criminals from exploiting jurisdictional gaps.
D. Public-Private Partnerships in Cybersecurity
Enhancing public-private partnerships in cybersecurity is instrumental in fortifying defence mechanisms against Dark Web cybercrime. Collaboration between governmental bodies, law enforcement agencies, and private-sector entities fosters a collective approach, combining resources, expertise, and technological capabilities to effectively combat cyber threats in a rapidly evolving digital landscape.
Table shows data regarding India reported cybercrimes during 2017-2020 Year
|
Year |
Reported cybercrime cases in India |
|
1) 2017 |
21,796 reported cybercrimes |
|
2) 2018 |
27,248 reported cybercrimes |
|
3) 2019 |
44,735 reported cybercrimes |
|
4) 2020 |
50,035 reported cybercrimes |
From 2017 to 2020, reported cybercrime cases in India exhibited a notable increase, escalating from 21,796 cases in 2017 to 50,035 cases in 2020. The surge reflects the dynamic and evolving nature of cyber threats, demanding heightened vigilance.
It's essential to recognize that these statistics are based on reported cases, potentially indicating both an actual rise in incidents and an increased awareness or reporting of cybercrimes.
As the cyber landscape continually transforms, proactive measures and ongoing vigilance are imperative for effectively addressing the challenges posed by cybercrime in India.
References
Internet and Conference Sources [1] https://pib.gov.in/PressReleseDetailm.aspx?PRID=1883066 [2] https://www.business-standard.com/article/current-affairs/11-jump-in-cyber-crime-in-2020-ncrb-data-in-home-panel-report-122021100189_1.html [3] https://www.statista.com/topics/5054/cyber-crime-in-india/ Book Sources [1] \"Cybercrime and Espionage : An Analysis of Subversive Multi-Vector Threats\" by Will Gragido and John Pirc (2011). [2] \"Cybersecurity and Cyberwar : What Everyone Needs to Know\" by P.W. Singer and Allan Friedman (2014). [3] \"Dark Territory : The Secret History of Cyber War\" by Fred Kaplan (2016). [4] \"The Darkening Web : The War for Cyberspace\" by Alexander Klimburg (2017). [5] \"Cybersecurity : What You Need to Know About Computer and Cyber Security, Social Engineering, the Internet of Things + An Essential Guide to Ethical Hacking for Beginners\" by Lester Evans (2020).
Copyright
Copyright © 2024 Faisal Shaikh, Fahad Shaikh. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET58892
Publish Date : 2024-03-09
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

