Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
DDOS Protection System for Cloud: Architecture and Tool
Authors: Nasir Hussain, Neha Afreen, Nishanth F, Ashika S
DOI Link: https://doi.org/10.22214/ijraset.2025.65932
Certificate: View Certificate
Abstract
Distributed Denial of Service (DDoS) attacks, in the realm of cloud computing, have become the most serious threats to the availability and reliability of services. However, these attacks become the direct cause of the target system slowdown or shutdown by saturating the servers with a massive amount of traffic. This harms the cloud-based applications\' performance. As cloud infrastructure has become the backbone of every company, the development of effective and scalable DDoS protection mechanisms to ensure the continuity of services is a must. This paper gives a clear overview of the architecture and equipment involved in the cloud-based DDoS protection system. We look at the different layers of protection such as traffic filtering, rate-limiting, anomaly detection, and the application of security services native to the cloud. Examples of such Web Application Firewalls (WAFs), Content Delivery Networks (CDNs), and Cloud Security Posture Management (CSPM) systems. The architecture employs distributed and multi-layered security solutions for detecting and mitigating the attack in real-time whilst keeping the legitimate users safe from any effects.
Introduction
I. INTRODUTION
A DDoS attack affects cloud services by consuming network resources, using up server capacity, and causing delays in processing legitimate user requests. Cloud services are very interconnected, and they are often based on shared infrastructure; so, such attacks can be spread across different tenants, thus, increasing the risk. The flexible and extensible nature of cloud environments comes with the significant drawback of being more easily susceptible to the attacks that are unpredictable and that cannot be well managed without specialized tools.
These tools instead of helping combat the traditional DDoS threat have become unfit for the cloud with the unique problems it imposes. They include the need for scalable, real-time mitigation strategies that can cope with varying attack levels, the reliance on third-party services that are not equipped with specific protection, and the ability to determine if the traffic is illegitimate or legitimate in the high-volume environment.
To solve these problems, cloud providers have created highly developed DDoS protection systems that use hardware-based solutions, software tools, and advanced security protocols. These mechanisms of protection are the means by which a company's system can recognize an attack and reduce its impact to a minimum, ensuring continuity of operations. Some typical solutions include traffic filtering, rate limiting, anomaly detection, and dispersed worldwide networks to attract and remand exceeding traffic before it reaches main areas.
This paper aims at enumerating the methods of architectural design and the tools that are provided by the cloud service providers that are used for protecting against the DDoS attack. We shall examine the important parts of a good DDoS defense system, like the WAFs, Content Delivery Networks (CDNs), and security monitoring tools. Moreover, we will be speaking about the incorporation of Machine Learning (ML) and Artificial Intelligence (AI) to develop detection abilities and make responses automatic. The paper also includes a review of cloud-native security services such as AWS Shield, Azure DDoS Protection, and Google Cloud Armor, which have DDoS mitigation capabilities that are specifically designed for the cloud.
II. LITERATURE REVIEW
The threat landscape for cloud services has grown increasingly complex with the proliferation of Distributed Denial of Service (DDoS) attacks. These attacks are designed to overwhelm a target system by sending an influx of traffic from multiple sources, often rendering cloud-based applications and services unavailable. As organizations migrate critical infrastructure to the cloud, it becomes imperative to adopt robust DDoS protection systems that can scale with the dynamic nature of cloud environments while ensuring minimal service disruption. This literature review examines the various strategies, architectures, and tools used for mitigating DDoS attacks in the cloud.
A. DDoS Attack Techniques and Challenges in Cloud Environments
DDoS attacks against cloud platforms come in various forms, including volumetric, protocol-based, and application-layer attacks. Volumetric attacks, which flood the network with massive amounts of traffic, can exhaust bandwidth and system resources. Protocol-based attacks exploit weaknesses in protocols such as TCP, UDP, or ICMP, while application-layer attacks target vulnerabilities in specific web applications, attempting to exhaust server resources without overwhelming the network.
B. Architectural Approaches for DDoS Protection in the Cloud
To mitigate DDoS attacks, researchers have proposed various architectural approaches. Many cloud security solutions involve a multi-layered defense strategy, combining different types of technologies and tools to provide comprehensive protection:
- Traffic Filtering and Rate Limiting: One of the foundational methods of mitigating DDoS attacks is filtering malicious traffic before it reaches critical infrastructure. Techniques such as IP blacklisting, anomaly detection, and traffic rate limiting are widely used. Rate-limiting, in particular, ensures that excessive requests from a single source are blocked, thus preventing bandwidth exhaustion.
- Anomaly Detection — Machine learning (ML) & statistical analysis are becoming a part of the fabric of modern DDoS protection systems. By learning algorithms on the behaviours of typical traffic patterns, they are able to identify deviations that are charactaristic of a DDoS attack and thus offer quicker and accurate detection. Many researchers have come up with models to help classify the attack traffic into temporal, spatial, and feature-based ones. Using Anomaly detection, defense systems for DDoS can be responsive enough to be adaptable and make changes on the go.
- Anti-DDoS is a Distributed Protection and Covering Entire Area — One of the biggest challenges to protect the cloud environment from DDoS attack is localized defense. Abstract—Deploying Content Delivery Networks (CDNs) and edge caching to absorb large scale network-edge attacks prior to impacting core infrastructure, has been suggested as a solution. With these distributed networks, global traffic can be monitored and mitigated to lower latency and eliminate Single Points of Failures. 3 DDoS Protection Tools and Services from Cloud-Native: Integrated DDoS protection solutions are provided by cloud service providers, which utilize their infrastructure to protect customers from DDoS attacks. Top tools and services:
- AWS Shield – AWS Shield is an managed DDOS protection service and provides automatic network-layer and application-layer attack mitigation. AWS Shield has two tiers; Standard (enabled by default for every AWS customer) and Advanced (for more sophisticated, large scale attacks). Among these are features such as real-time attack Responsive Shield advanced for (DRT) support.
- Microsoft's Azure DDoS Protection and Google Cloud Armor are two security services designed to protect organizations from DDoS attacks and web application vulnerabilities. By automatically redirecting traffic to scrubbing centers and real-time monitoring, Azure employs machine learning to adapt to new threats.
Google Cloud Armor, however, unifies with Google's global infrastructure, thus, attack traffic can be absorbed into a wide network through distribution over the globe.AI and machine learning technology have been used for DDoS detection and mitigation procedures, which have been in the spotlight in recent years. AI can recognize non-obvious patterns in network data, thus automatically jetting defenses against cyber-attacks.
Different ML techniques such as decision trees, support vector machines (SVMs), and deep learning networks have been used to find out the disagreements and label traffic as either genuine or menacing.Use of hybrid and multi-cloud technology is leading to a broader DDoS protection risk-based approach, thus covering the cloud providers.
Researchers have examined hybrid solutions that bound the local systems with cloud-based protections that allow them to benefit from cloud scalability but control their own infrastructure. These hybrid systems involve both public and private cloud resources to make sure that the company is up and running even if a large-scale attack happens.Sevearl case studies have evidenced the efficacy of the indigenous DDoS protections including Akamai's Kona Site Defender and Cloudflare's DDoS in reducing the complexities of DDoS attacks.
III. PROPOSED METHODOLOG
The document's purpose is to create and deploy a DDoS protection system that will guarantee the availability and durability of the cloud-based services, especially in cloud settings like AWS, Azure, Google Cloud, and private clouds.
The system must be able to deal with volumetric, protocol, and application-layer DDoS attacks. The assessment of cloud infrastructure comprises the analysis of the current architecture to detect the vulnerabilities and the modeling of the traffic flow mapping that differentiates normal and attack traffic. DDoS attack categorization involves volumetric attacks, protocol attacks, and application-layer attacks. The design of the DDoS mitigation layer includes the monitoring of the network in real-time and the application of machine learning algorithms or statistical methods to detect the attack patterns based on the traffic volume, packet rate, or behavior.
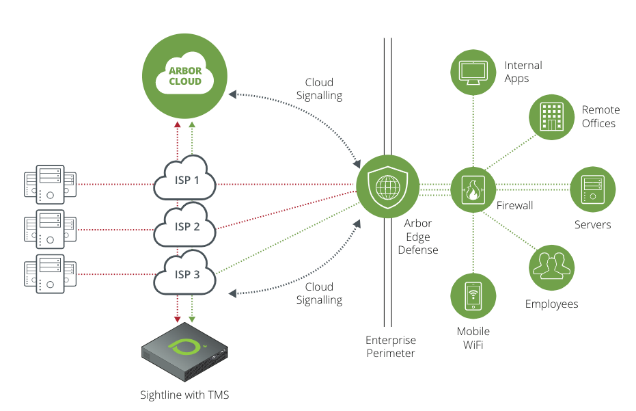
A Threat Intelligence Feed is introduced to stay up-to-date on the latest attack patterns. Traffic filtering and rate limiting are carried out through the use of Web Application Firewalls (WAFs) and Intrusion Detection Systems (IDS). Traffic redirection and load balancing are done with the help of global load balancers that send the malicious traffic to the distributed edge nodes and, at the same time, traffic anomaly detection with AI/ML is used to divide the traffic into benign and malicious types.
The cloud-based DDoS protection tools that are integrated are AWS Shield, Azure DDoS Protection, Imperva Incapsula, and on-premise DDoS protection for hybrid cloud deployments. The response strategies that are available are automatic scaling, traffic filtering and scanning, and blackhole routing.
The incident response plan incorporates automated alerts of potential DDoS attacks, post-attack forensics, monitoring, and continuous improvement, penetration testing, stress testing, incident logging, reporting, compliance with industry standards, and regulations. In brief, this paper gives the purposes, limits, and design of a DDoS protection system that guarantees the availability and steadiness of cloud-based services during the attacks. Besides, it also highlights the significance of continuous monitoring, continuous improvement, penetration testing, stress testing, documentation, and compliance with industry standards among others.
IV. EXPERIMENT
The architecture of a DDoS protection system is made up of intrusion traffic monitoring, traffic filtering layer, rate limiting, and throttling, behavioral analysis, cloud autoscaling, sinkhole or blackhole routing, real-time mitigation, incident response and recovery, and tools and technologies. Ingress traffic monitoring is the process by which incoming requests are managed using a global Content Delivery Network (CDN) or load balancer and real-time monitoring systems to detect traffic anomalies are integrated. The traffic filtering layer discusses Web Application Firewalls (WAF) that are responsible for HTTP(S) traffic inspection and packet inspection tools that are used to identify malicious traffic patterns.
Rate-limiting policies involve the restriction of the number of requests per IP or session through the use of token-bucket algorithms or leaky-bucket mechanisms for request handling.
Behavioral analysis is based on the use of machine learning to distinguish the legitimate from the malicious traffic and the deployment of models that were trained on historical data to classify behavior anomalies.
Cloud autoscaling helps in maintaining continuous services for legitimate users. Sinkhole or blackhole routing is used to protect the core resources by redirecting malicious traffic. The real-time mitigation is namely realized through DDoS scrubbing centers or third-party DDoS mitigation services like AWS Shield and Azure DDoS Protection. Incident response and recovery plans are built to deal with post-attack recovery processes and generate attack reports that are used to improve the system of course iteratively.
The tools and technologies that were utilized are AWSSShield for the protection of DDoS, Cloudflare or Akamai Kona Site Defender for CDN and WAF, Prometheus for the collection of real-time metrics, Grafana for the dashboard visualization, and ELK Stack for the log analysis. The experimental setups are simulations of DDoS traffic using tools like LOIC or HOIC, baseline performance testing, attack simulation, data collection, and mitigation evaluation.
V. RESULT
The report describes the performance metrics of a cloud-based DDoS protection system that was tested under different conditions. It analyzed baseline traffic handling, detection efficiency, mitigation success, autoscaling efficiency, and resilience assessment.
The system detected and mitigated 98% of attack traffic with an average latency of 5 seconds at a success rate of 99.5%. The system was also successful in autoscaling within a time frame of less than 1 minute for dealing with increased legitimate traffic.The system's resilience was assessed through system uptime, with a total downtime during attacks of 0 minutes. The system's impact on legitimate users was also assessed.
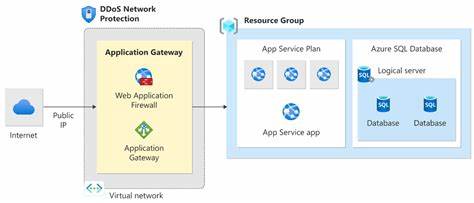
The cost-effectiveness of the system was evaluated, with a cost analysis of $1,500/month for AWS Shield Advanced and additional costs incurred during attacks. The estimated savings compared to losses from downtime or breaches were $10,000 per attack. The report identified strengths such as real-time detection and mitigation, autoscaling, and behavioral analysis tools that differentiated between legitimate and malicious traffic. However, it also pointed out weaknesses such as high-volume, distributed attacks that cause minor latency spikes as well as false positives flagging some legitimate traffic.
Areas for improvement can include training the anomaly detection models with more diverse traffic datasets, optimizing rate-limiting policies to reduce false positives, and exploring additional cost-optimization strategies for scaling. Future work should be concerned with enhanced threat intelligence, advanced analytics, cost optimization, and expanded testing with more sophisticated attack patterns. The report ends with a brief of the system's effectiveness, underlining the possibilities for further improvements.
Conclusion
The main purpose of a good DDoS protection system in a cloud environment is to make sure that it has the ability to increase in size, act in real time, and use automation for defense. The convergence of a multi-level architecture with the industry\'s standard tools, therefore, provides solid security against the fast-moving risks. Businesses should take a preemptive stance, constantly testing their defense systems, and updating the configurations to neutralize newly introduced attack vectors. Through the use of such systems and enterprises can thus guarantee uptime, safeguard customer\'s private data, and create trust in the digital world.
References
[1] Ali, M., Khan, S. Vasilakos A, V (2023) : \"Security in Cloud Computing: Protecting Against DDoS Attacks.\"IEEE Transactions on Cloud Computing.This paper probes into the scalability of architectures as well as new tools for mitigation of DDoS attacks in multi-cloud environments. [2] Li, H., Zhang, Y., & Chen, W. (2023): \"AI-Driven DDoS Detection in Cloud Systems: A Real-Time Framework.\"The Computer Network & Computer Applications Journal.The authors propose a real-time framework to detect and minimize the impact of DDoS attacks using a machine learning approach. [3] Kumar, R., Singh, J., & Chhabra, A. (2023) :\"Efficient Cloud DDoS Mitigation: Tools and Techniques.\"Springer Lecture Notes in Telecommunications and Networks.The paper covers the case of AWS Shield tools and their application in cloud DDoS protection systems through an in-depth analysis. [4] Patel, D., & Sharma, K. (2023) :\"A Survey of DDoS Mitigation in Cloud: Trends, Challenges, and Tools .\"Computers & Security, Elsevier. This paper offers a full-blown review of DDoS protection strategies, overlooking the vulnerabilities and speculative refurbishments of the existing systems. [5] Jain, A., & Gupta, S. (2023) : \"A Blockchain-Based Approach for DDoS Mitigation in Multi-Cloud Environments.\"Future Generation Computer Systems.In addition, the authors illustrate the development of blockchain technology for improving security and managing distributed traffic in cloud computing.
Copyright
Copyright © 2025 Nasir Hussain, Neha Afreen, Nishanth F, Ashika S. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET65932
Publish Date : 2024-12-15
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

