Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
E-Auction for Courier Service
Authors: Rohan Kiran, Dr. Mohammed Tajammul
DOI Link: https://doi.org/10.22214/ijraset.2022.40332
Certificate: View Certificate
Abstract
Auctions have been there since a long time, with advancement in technology everything from food to clothes can be bought and sold at the comfort of your home; similarly auctions have shifted to electronic medium as well. We have sites like eBay where e-auctions are done. Since auctions are usually of commodity/goods this project aims to do it for services that courier companies are offering. The problem that we’re trying to solve is to make a hassle-free system for the customers as well as the service provider where both are authentic, and the privacy of the customer is maintained which is lacking in the present system and a chance for new and individual courier service an equal opportunity to compete.
Introduction
I. INTRODUCTION
E-Auction and online courier services have been there for a long time, what we’re trying to do is combine both and come up with a solution that might change how we send courier and how we’re currently being charged for it.
As customer we must do lot of research to find out the best reliable and cheap courier service to transport our goods. During this process we might encounter a lot of fake websites, where we must share our personal information and numbers available online for courier might be fake, we do have some application where we can transport our goods but usually those apps are functional in major cities. So, what the application will do is let the customer post ad in the web app and the ad will contain all the information about the package and pick up and drop location, later the service provider i.e., the courier company can place their bids on the ad and customer can choose and share further contact details with the courier service.
We are going to develop the system in web application format using .NET framework and MySQL as a backend and host this web application in cloud.
II. LITERATURE REVIEW
In [1] the author aims to highlight the growth of courier companies in Philippines during the pandemic. This growth of courier service will grow even more, since majority of the people are still not vaccinated and even after that the growth won’t stop as people are becoming more habituated to use these services. To conduct this research an online survey was conducted where there was a total of 120 participants the assessment was done based on respondents preferred courier services, frequency of delivery on different age group.it also evaluated the number of times users used the courier services before and during pandemic and preferred payment options. In [2] the author wants to identify and classify the key factors which determine the perception of courier service quality by customer shopping online, growing competition on courier market and meet client’s expectations, one of the goals of courier services is to provide high quality service though there were some limitations to this research, the study was aiming to develop scale of courier service quality to verify the scale in future the author will use CFA
In [3] the author wants to highlight and improve upon the existing courier system. This way they system provides the service which is less efficient in terms of comfort, cost estimation from consumers’ point of view, tracking dispatch and cost estimation. Authors projects aims to develop a mobile application which a user can use to avail the services from comfort of home and have all the features that current/existing system lacks. This application is developed specifically for Nigeria, it provides an easier way to send packages with less delay and stress.
In [4] the author wants to investigate how the biding behavior changes when new auction format gets introduced into marketplace. The author analyzes the data set on internet display ad auctions that exploits a staggered adoption by different sellers (publishers) of first auction price (FPAs) in place for traditional second price auction. The average price jumps up immediately after the format changing to SPAs to FPAs.
In [5] the author wants to evaluate and discover patterns and behavior of online auction due to lack of real and extensive transaction data for this author used eBay as a subject and find out how eBay auction works and its various factor like consumer surplus, biding strategy etc. the key issue here is the wrong assumption that bidders’ quotations are independent from each other which leads to inefficient auction, in order to over come the inefficiencies of the current online format the author introduced a declining price auction model customized for online transaction.
In [6] author sees the growing demand of cloud service, as these cloud services allows users to remotely store data that is maintained by the cloud service provider it raises a huge concern based on data privacy and security. The author compares the security and privacy pf amazon AWS S3 and Microsoft azure Blob. The comparison focuses on their security and compliance program and how access control behaves on securing the user’s data. Both services used string encryption techniques for data and network connection and tremendous effort in compiling most common standard regulation.
In [7] the author does a comparative study on on-premises databases and cloud databases regarding the response time of the databases. This study focused on presenting the advantage of storing data and application in the cloud and have a comparison between when it’s stored on-prem. As a result, it highlighted the many advantages of cloud data storage in relation to data accessibility, speed, security, automation and disaster recovery. But there were some case where on-prem databases performed slightly better.
In [8] the authors compare on-demand EC2 instance and reserved instance for cost optimization. In this paper they devised heuristic based on EDF where decision on number of instances required a pricing plan and task scheduling considered to make decision on number of instances required. Existing workflows and their characteristics mentioned in previous literature are used for experimentation. The result shows that our proposed heuristic minimizes total number of instances required for execution and maximizes utilization of each instance. It gives us the opportunity to use plans such as reserved pricing, which is cheaper compared to on demand, thereby giving us better cost performance
In [9] the authors compare the performance of REST APIs implemented with java technologies and Microsoft .NET. it could be deduced that APIs implemented using the Java framework would be suitable for business-to-business such as Online Transaction Processing (OLTP) applications that periodically transfer data across data stores. Conversely, APIs developed using the .Net Framework would be a better choice for applications that has many users concurrently inserting data through input forms on client applications as well as making regular updates.
In [10] the authors did a study on bid arrivals on e-auction and noticed a pattern which is indicator of bidding strategies and behavior of bidders in online auction the sellers decide a time frame for the thing they’re selling, and the bidders do the bidding as late as possible this study was done for understanding bidders’ behavior and on a C2C (customer to customer) base websites data i.e., eBays.
In [11] the authors did a comparative study between encryption algorithm with context to cloud and states that there’re two different type of algorithms one is heterogenous and other homogenous. The homogenous algorithm of encryption is used for when encryptors and decryptors are same and heterogenous algorithm when encryptors and decrytors are different. This research paper also presents their comparative analysis.
In [14] the authors are trying to tell us about Cloud computing, is the delivery of different services on the Internet. Those services are offers to the user on a pay as go basis. These services include computation, storage, and various types of applications. Cloud computing also means storing and accessing data and programs over the internet instead of your computer's hard drive. As it has been found from past few years of study that cloud storage is not fully secured so this paper focuses on storage security of cloud computing. Various algorithms have been designed and implemented but in all of them the user must create and enter key to encrypt data rather than generate the key by themselves. This research paper proposed an algorithm which will produce key itself on the basis of data input and subsequently encrypt data on the basis of key produced where the encrypted data will upload on the cloud storage while key is kept secure at local server for future use.
The following figure shows the conceptual architecture of cloud computing.
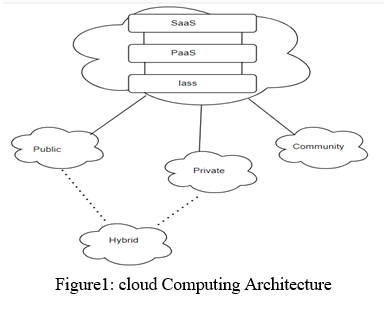
In [16] A lot of companies which required cloud services are still in confusion whether to used it or not as they are not completely secured. This research paper focus on security of storage as a service which is a part of infrastructure as a service. Whenever a company rent the storage from the cloud service provider, chances of hacking take place. To avoid this, it is necessary to encrypt the data before uploading to the cloud and it will be more convenient if we will divide the data into fragments and encrypt these small data pieces also know as fragments separately and then upload on cloud. There are many algorithms like DES, AES, RSA, Ellamae and Blow Fish but they are static in nature and the size of encrypted file increased rapidly. To resolve the above problem this paper will propose Two Pass Multidimensional Key Generation and Encryption Algorithm, a data sensitive algorithm which could sense data and produce different key for different data automatically and it will also check the integrity of the documents while decrypting.
In [17] Cloud computing is a very trustful and useful technology which offers different services to user on pay per use basis. Many companies offer cloud services for computation or storing data but while transferring the data on cloud many middlemen like Cloud Service Provider (CSP) and internal employees of CSP are come to know about the data which will increase the chances of cyber-attack. A lot of companies out there like Amazon Web Services (AWS) provide us with computation and storage, but slight fear hacking remains in the mind of data proprietor. To solve this problem lot of algorithms are designed but all of them are used to ask the user to enter the key. This research paper proposes an algorithm for key generation which uses Data Encryption Standard (DES) which helps it in generating a unique key by itself and subsequently encrypts data based on key produced. This algorithm will not only used to develop an automatic system which itself produce key for encryption but also making this complete process user independent where the user need to upload the text data only and the key produced will be sent to user related to that particular data and encrypted data will be uploaded on cloud storage.
III. PROPOSED SYSTEM
The system helps local transporters / courier services to compete with others and present equal opportunity to all and a better customer stratification with following implementation.
- Both transporters and customers need to upload some kind of Government document as address proof and identity
- Contact details will be not enclosed with any of the transporters maintaining privacy
- Customer can post their ads. That contains detailed information about the goods they want to transport and the destination and pickup location
- Transporter can make their bids and the user can decide which offer he/she has to select.
IV. SYSTEM DESGIN
In the above proposed system, the clients i.e. both the customer and the transport service provider has to register on our website, after that they can post Ads and place bids. The fig 3 show how our processed system will work there are four parts [3]
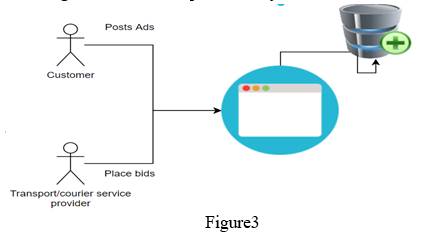
A. Database Creation
The system we have requires the following data from both users’ 1. Name 2. Username 3. Email 4. Password 5. Identify proof the database tables will be separate for the customers and the service providers. Then the database will also contain users’ information such as Ads posted and bids for the transporters. All this information will be store in SQL database that will be hosted in cloud platform. In [6] we compared two of the most popular cloud service providers on their security and privacy related to the storage services they offer they show almost the same kind of features like encryption and securing network then in [7] we got to understand the difference in performance of on-prem databases to the databases on cloud and which outperformed the on-prem on certain scenarios which we might face hence decide to go forward with cloud storage.
B. Login & Signup
The user will be presented with the login and signup page where they must provide their personal information like email id, id proof, username and password to register at the time of registration you’ll also get option to choose form that is whether you are a customer or a service provider and using the username and password they can login.
C. Posting Ads
This is for the customer where they can post Ads which will be displayed to the bidders and the ad will contain details like no. of package the pickup and drop location and weight and size and date till which this ad is valid. In [5] we have seen that how bidders wait till the last moment to place their bids in order to make more profits so to overcome that I have removed the automation instead user can choose the price on his own regardless of what these bids have been placed.
D. Bidding on Ads
This is for the service providers where they will have option to bid on the ads posted by the customer and they can interest specified amount that will be visible to the customer as well as other bidders so they can do a comparative bidding this will help the customer to get a better deal since everyone will be offering their lowest price to win the bid. In [4] we saw how the FPA, and SPA affect the bidding so we have decided to go with the concept of SPA but with a bit of twist since users will pay the service provider they would be billed as the amount which they opted for plus the 2% of second lowest bid.
V. ACKNOWLEDGMENT
I do acknowledge the support and encouragement of all people who helped me throughout the completion of this project.
I would wish to give thanks Dr. Dinesh Nilkhant, Director – JGI, Knowledge Campus, Bangalore, Karnataka for proving the facilities to try to analysis work. His leadership and management skills are continuously a supply of inspiration.
I conjointly wish to give thanks Dr. M. N Nachappa, Head of School of Computer Science & IT, Jain deemed to be university, Knowledge campus, Bangalore, Karnataka for his support and cordial cooperation.
I give thanks the project Committee Members, Prof. Bhuvana J, Mentor and Program coordinator, Department of Master of Computer Application for providing for providing the support and steerage to try to analysis work. Her timely direction and motivation helped me to stay my patience throughout this journey.
Moving further, I would like to give my sincere gratitude to Project Centric Learning Coordinator, Dr. Manju Bargavi S.K., Professor, Department of Master of Computer Application for helping me in completing my project work as per the university requirements.
I am highly indebted to my guide Project Guide Dr. Mohammed Tajammul, Assistant professor Department of MCA - School of Computer Science & IT for providing a valuable guidance throughout the course of the project to submit successfully
Conclusion
Through this research we could come up with a web-based solution for our problem that was lack of privacy and a platform for upcoming business an equal opportunity to compete. The system will allow the users (customer) to post ads for their requirements and other users (service providers) to bid on those ads.
References
[1] Reginald Lance E. Dones;Michael N. Young, “Demand on the of courier services during COVID-19 pandemic in the philippines,” 2020 7th International Conference on Frontiers of Industrial Engineering (ICFIE). Year: 2020 | | Publisher: IEEE [2] Aleksandra Gulc,“Determinants of courier service quality in e-commerce from customers’ perspective”. Year: 2020 | | Publisher: Research gate [3] Chinedu Nwoye, Monica Agu, Blessing Ogechi Ogbuokiri, “Enhancing courier service with the development of an interactive mobile app in android platform” Year: 2015 | | Publisher: Research gate [4] Shumpei Goke, Gabriel Y. Weintraub, Ralph Mastromonaco, and Sam Seljan, “Learning new auction format by bidders in internet display ad auctions” Year: 2021 . [5] Hu Wenyan,Alvaro Bolivar, “Online auctions efficiency: a survey of ebay auctions,” Year: 2008 . [6] Iman Saeed, Sarah Baras and Hassan Hajjdiab, “Security and privacy of aws s3 and azure blob storage services,” Year:2019 [7] Robert Gy?rödi, Marius Iulian Pavel, Cornelia Gy?rödi And Doina Zmaranda “Performance of OnPrem Versus Azure SQL Server: A Case Study” Published:2019. [8] Ms. Vidya K. Bhise, Mr. Ajit S. Mali “EC2 instance provisioning for cost optimization”Year:2013 [9] Munonye K, Martinek P “Performance Analysis of the Microsoft .Net- and Java-Based Implementation of REST Web Services” Year: 2018 Publisher:IEEE [10] Zhang Jie and Zhang Yaping ,“Research on duration and bid arrivals in eBay online auctions in the internet” year:2011 [11] Tajammul, M., Parveen, R., & Tayubi, I. A. (2021, March). Comparative Analysis of Security Algorithms used in Cloud Computing. In 2021 8th International Conference on Computing for Sustainable Global Development (INDIACom) (pp. 875-880). IEEE. [12] Tajammul, M., Shaw, R. N., Ghosh, A., & Parveen, R. (2021). Error Detection Algorithm for Cloud Outsourced Big Data. In Advances in Applications of Data-Driven Computing (pp. 105-116). Springer, Singapore. [13] Tajammul, M., & Parveen, R. (2020, December). To Carve out Private Cloud with Total Functionality. In 2020 2nd International Conference on Advances in Computing, Communication Control and Networking (ICACCCN) (pp. 831-835). IEEE. [14] Tajammul, M., & Parveen, R. (2020). Auto encryption algorithm for uploading data on cloud storage. International Journal of Information Technology, 12(3), 831-837. [15] Tajammul, M., & Parveen, R. (2019). Algorithm for Document Integrity Testing Pre Upload and Post Download from Cloud Storage. International Journal of Recent Technology in Engineering, 973-979. [16] Tajammul, M., & Parveen, R. (2019). Two pass multidimensional key generation and encryption algorithm for data storage security in cloud computing. International Journal of Recent Technology in Engineering. [17] Tajammul, M., & Parveen, R. (2019). Key generation algorithm coupled with DES for securing cloud storage. International Journal of Recent Technology in Engineering. [18] Tajammul, M., & Parveen, R. (2017, October). Comparative analysis of big ten ISMS standards and their effect on cloud computing. In 2017 International Conference on Computing and Communication Technologies for Smart Nation (IC3TSN) (pp. 362-367). IEEE.
Copyright
Copyright © 2022 Rohan Kiran, Dr. Mohammed Tajammul. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET40332
Publish Date : 2022-02-13
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

