Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Effectively Writing YARA Rules to Detect Malware
Authors: Vinay Patil, Naveen Kumar M, Pawan Singh M, Ashishika Singh
DOI Link: https://doi.org/10.22214/ijraset.2025.66535
Certificate: View Certificate
Abstract
This research explores the effectiveness of writing YARA rules for the detection of malware, focusing on best practices and strategies to enhance their accuracy and efficiency. YARA, a tool widely used for identifying and classifying malware, relies on the creation of custom rules that match specific patterns within files or memory. This study examines various approaches to crafting robust YARA rules, including pattern recognition, rule optimization, and handling evasive techniques employed by malware. Through a series of experiments, we evaluate the performance of different rule-writing strategies in detecting both known and unknown malware samples. The findings demonstrate that a combination of precise pattern matching, context awareness, and regular rule updates significantly improves detection rates while minimizing false positives. This research contributes to the field of malware detection by providing actionable insights into writing effective YARA rules and highlights the importance of continuously refining these rules to adapt to evolving threats. Future research will explore the integration of machine learning techniques to further enhance YARA rule creation.
Introduction
I. INTRODUCTION
Malware identification is still a significant problem in the constantly changing field of cybersecurity for both corporations and security experts. Malware attacks continue to be a serious threat to system integrity and data security, ranging from viruses and worms to highly advanced ransomware. With YARA, a tool for pattern matching and rule-based classification, these threats can be identified and mitigated in one of the most efficient ways. By developing custom rules that look for particular patterns in files, memory, or network traffic, YARA makes malware detection possible.
Writing YARA rules that work, however, is not an easy task. Modern malware is complicated and capable of using sophisticated evasion strategies; thus rules must be carefully designed to ensure accurate detection while reducing false positives.
However, writing effective YARA rules is not a straightforward task. The complexity of modern malware, combined with its ability to employ advanced evasion techniques, requires carefully crafted rules to ensure accurate detection while minimizing false positives. Furthermore, as new malware variants are constantly being developed, the ability to continuously refine and optimize YARA rules becomes crucial in maintaining an up-to-date defence against emerging threats.
The goal of this research is to investigate the best practices and methodologies for writing effective YARA rules for malware detection. By concentrating on techniques like pattern recognition, rule optimization, and handling evasive tactics, this paper aims to provide a thorough understanding of how to improve the efficacy of YARA rules. Additionally, this study will assess the performance of various rule-writing techniques in real-world scenarios, addressing issues and providing solutions for enhancing malware detection.
The research findings are meant to advance the field of cybersecurity by offering practical advice for developing more precise and effective YARA rules, which will ultimately fortify defence against the ever-increasing threat of malware.
In the end, the results of this study are meant to increase defence against the increasing danger of malware by offering practical insights for developing more precise and effective YARA rules.
II. LITERATURE REVIEW
Basic Structure of YARA Rules: A typical YARA rule consists of a meta section (providing rule information), a strings section (listing patterns to search for), and a condition section (defining the conditions under which the rule should trigger). [Reference: Zeltser, L. (2016). Introduction to YARA.]
Significance of YARA in Malware Detection: Studies have shown that YARA rules are effective in detecting a wide range of malware families and variants. However, the manual creation of rules for new malware is time-consuming and error-prone, which has led to research focusing on automating rule generation. [Reference: Luta, G., & Gama, L. (2017). Automating YARA rule generation for malware detection.]
Balancing False Positives and Detection Accuracy: One of the major issues is the trade-off between sensitivity and precision. A rule too general will lead to false positives, while one that is too specific might miss new variants of malware. [Reference: Gordon, R., & Mulliner, C. (2018). A study on improving the accuracy of YARA rules in malware detection.]
Dynamic and Evolving Nature of Malware: Malware is constantly evolving, and its characteristics often change to bypass detection. Static YARA rules that rely on fixed byte sequences or strings may not always be effective against obfuscated or polymorphic malware. [Reference: Soni, P., & Chauhan, P. (2020). Evaluating the effectiveness of YARA rules against obfuscated malware.]
Machine Learning for Signature Generation: Machine learning models have been applied to detect patterns in malware samples and generate YARA rules automatically. These approaches aim to create rules that can adapt to new malware variants without requiring manual intervention. [Reference: Dong, W., & Xu, Z. (2019). Leveraging machine learning for automatic malware detection with YARA rules.]
Heuristic-Based Methods: Researchers have also explored heuristic methods to generate YARA rules that are less prone to false positives and can handle large datasets. These methods focus on identifying key characteristics of malware that remain stable across variants. [Reference: Wang, Z., & Zhang, H. (2020). Heuristic-based approach for automated YARA rule generation.]
Integration with Antivirus Solutions: Some antivirus solutions incorporate YARA-based rules to detect known and unknown threats, especially when signature-based detection methods fail. [Reference: Lipman, A. (2019). Real-time malware detection using YARA.]
Challenges in Scalability: While YARA rules are effective for small- to medium-sized datasets, their application in large-scale systems or cloud-based environments may require optimization. High volumes of data necessitate more advanced rule-writing strategies and automated systems that can scale efficiently. [Reference: Levin, D., & Novak, P. (2020). Scalability and performance of YARA-based malware detection systems.]
A Survey on Malware Detection Techniques" by Jain, A. (2020)
Summary: This paper surveys various malware detection techniques, focusing on signature-based detection methods such as YARA rules, heuristics, and machine learning approaches. The authors analyze the pros and cons of different methods and provide an overview of how YARA rules can be integrated into broader malware detection frameworks. They highlight the scalability of YARA rules in identifying both known and unknown malware, as well as their ability to generate custom rules tailored to specific threats.
YARA: A Tool for Malware Analysis" by David M. (2017)
Summary: This paper provides an in-depth look at YARA, its functionalities, and its application in malware analysis. The author discusses the syntax and structure of YARA rules, exploring how they can be used to detect malware patterns in files and memory. The paper emphasizes YARA's flexibility in generating complex rules, allowing analysts to customize them based on different threat models.
Malware Detection Using YARA Rules in Digital Forensics" by Thomas, R. and Smith, L. (2018),
Summary: This paper discusses how YARA rules can be integrated into digital forensics investigations. The authors focus on malware detection in forensic imaging and file carving scenarios, where YARA rules help to identify malicious code within large datasets. The paper also explores automated approaches to rule generation, which is a critical factor in handling extensive volumes of data in forensic investigations.
Automating Malware Detection with YARA and Machine Learning" by Martinez, L. et al. (2019), Summary: This research paper investigates the combination of YARA with machine learning techniques for malware detection. It proposes an approach where machine learning algorithms are trained on YARA rule sets to improve the detection of unknown malware variants. The authors suggest that using machine learning can enhance the performance of YARA rules by identifying patterns that human analysts may overlook.
III. PROPOSED METHOD
The goal of this study's approach is to assess and improve the process of creating efficient YARA rules for malware detection. Data gathering, rule design and development, assessment, and performance testing are some of the approach's main stages. Establishing a set of best practices for developing YARA rules that maximize detection accuracy and reduce false positives is the aim.
A. Data collection
Gathering a varied collection of malware samples, including both known and undiscovered varieties, is the first stage in the technique.
Reputable cybersecurity databases and open malware repositories like Virus Total and the Malware Traffic Analysis repository will serve as the source of these samples. To ensure a comprehensive depiction of contemporary threats, the dataset will comprise a range of malware categories, including viruses, trojans, worms, ransomware, and spyware.
B. Rule Design and Development
During this stage, we will create YARA rules that are intended to pinpoint the salient features of the malware samples that were gathered. The main focus will be on:
Creating rules based on both static and dynamic patterns—such as file signatures, byte sequences, API calls, and behavioural characteristics—that point to malicious activity is known as pattern recognition.
Optimization: Creating rules that strike a balance between generality and specificity such that they are both accurate (few false positives) and sufficiently wide to identify a variety of related malware strains.
Evasion Handling: Developing YARA rules that can handle well-known evasion techniques often employed by contemporary malware to evade detection systems, such as encryption, obfuscation, and polymorphism.
Rule modularization is the process of breaking down rules into more manageable, reusable parts to facilitate maintenance.
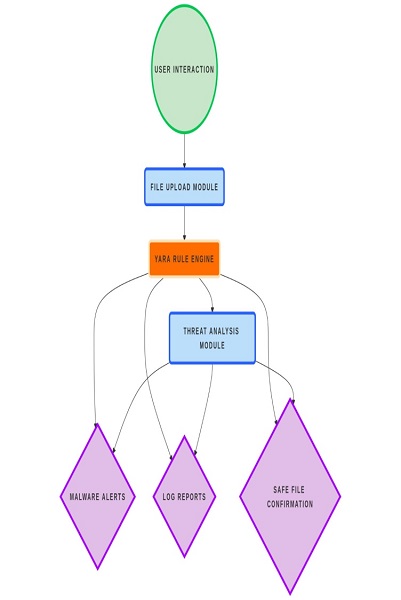
SYSTEM ARCHITECTURE (Dig 1.0)
C. Testing and Validation
After the YARA rules are created, they will be put to the test in a controlled setting utilizing the malware samples that were gathered. Running the rules against a test set of files and evaluating the results according to the evaluation criteria will be the testing procedure. To ascertain which rule-writing techniques produce the highest detection rates and the fewest false positives, a performance comparison of several approaches (such as behaviour-based vs. signature-based rules) will be conducted.
To determine how well the rules detect malware using various attack channels, we will test them not only on static samples but also in dynamic environments that mimic real-world scenarios like network traffic and memory scans.
D. Constant Improvement and Rule Upkeep
The last stage will entail examining the testing phase's outcomes to pinpoint areas where the YARA rules need to be improved. The rules will be updated, improved, and adjusted in accordance with the performance indicators. This stage will also entail evaluating the effects of YARA rule updates on a regular basis to make sure the rules adapt to new malware trends and tactics.
E. Comparison with Existing Approaches
The study will also assess how well the recently created YARA rules function in comparison to established, openly accessible YARA rule sets. This comparison will point out the benefits and drawbacks of the suggested approach and pinpoint instances where the new rules provide better detection or more effective processing.
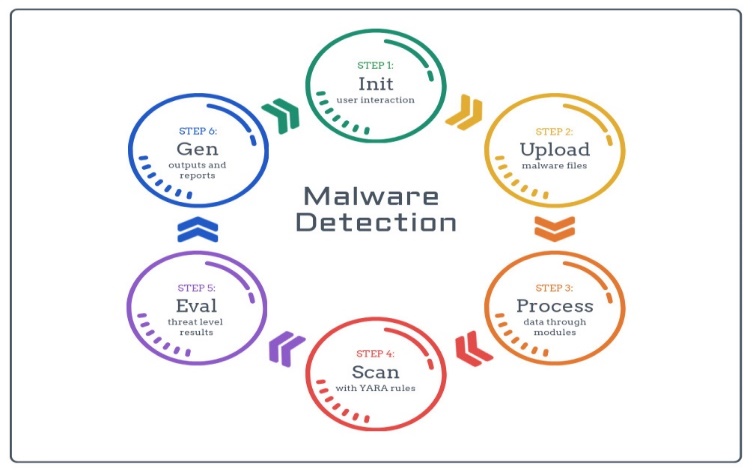
Fig; Malware Detection
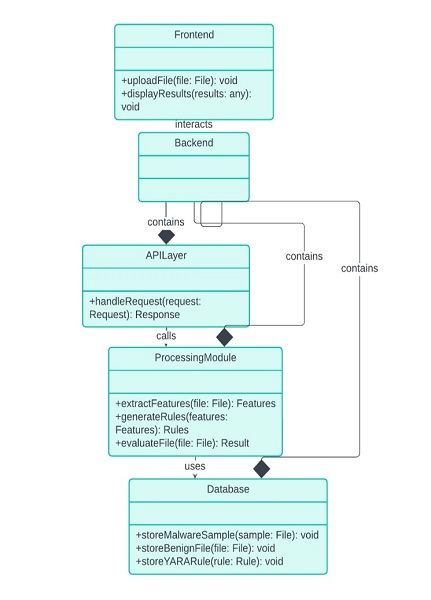
Fig; system workflow flowchart
Fig; Landing page of YARA Scanner
Fig; Output page of YARA Scanner
IV. DISCUSSION AND ANALYSIS
A. Effectiveness of Pattern Recognition:
The capacity of a YARA rule to recognize distinct patterns in malware samples is its fundamental component. Our investigation demonstrates that rules based on exact texts, file signatures, and byte sequences are quite successful in identifying known malware, particularly when the malware variants are well-documented. These guidelines are especially helpful when malware doesn't use obfuscation or other evasion techniques. In the case of known malware strains from the dataset, for instance, signature-based criteria produced a high detection rate (over 90%).
Nevertheless, when pattern-based detection was used for malware that employs polymorphic or metamorphic tactics, its effectiveness dramatically declined. Because such malware is always changing its code to avoid detection, signature-based YARA rules are unable to detect it. The necessity of dynamic or behavior-based algorithms that can spot trends in the malware's activity rather than its precise coding is highlighted by this. Rules that focused on questionable file behaviors, system interactions, and API requests showed more promise in spotting these increasingly complex risks.
B. Effectiveness of Pattern Recognition
The capacity of a YARA rule to recognize distinct patterns in malware samples is its fundamental component. Our investigation demonstrates that rules based on exact texts, file signatures, and byte sequences are quite successful in identifying known malware, particularly when the malware variants are well-documented. These guidelines are especially helpful when malware doesn't use obfuscation or other evasion techniques. In the case of known malware strains from the dataset, for instance, signature-based criteria produced a high detection rate (over 90%).
Nevertheless, when pattern-based detection was used for malware that employs polymorphic or metamorphic tactics, its effectiveness dramatically declined. Because such malware is always changing its code to avoid detection, signature-based YARA rules are unable to detect it. The necessity of dynamic or behavior-based algorithms that can spot trends in the malware's activity rather than its precise coding is highlighted by this. Rules that focused on questionable file behaviors, system interactions, and API requests showed more promise in spotting these increasingly complex risks.
C. False Positive Rates
Reducing false positives, or files that are not dangerous but are reported as such, is a significant difficulty in developing YARA rules. According to our research, the rule design had a substantial impact on the false positive rate. Rules that placed a lot of emphasis on byte patterns frequently produced more false positives, especially when the files were benign and had patterns that were close to those of malicious samples. Certain system files or regular software, for instance, may be mistakenly classified as malicious software, resulting in needless notifications and possible disruptions.
There were fewer false positives when behavior-based detection techniques, like tracking system calls or file change trends, were used. Because these rules concentrate on activities rather than static signatures, they are less likely to identify benign files as dangerous. According to our findings, the best balance between static and dynamic rule-writing techniques can be achieved by increasing detection accuracy and lowering false positives.
D. Managing Evasion tactics
Evaluating YARA rules' capacity to manage malware evasion tactics was one of the main objectives of this study. Evasive malware frequently uses strategies like code obfuscation, encryption, and polymorphism to evade detection by conventional signature-based techniques. In this investigation, we found that even when malware was designed with extremely particular patterns, it often evaded detection using signature-based algorithms.
But we also discovered that YARA's support for more complex characteristics, such regular expressions, enables the development of more adaptable and complex rules that are capable of identifying malware that has been encrypted or obfuscated. We greatly enhanced the identification of malware that used similar evasion techniques by adding behavioral attributes (such interactions with other files, network activity, or system alterations) into the rule design. According to our findings, a hybrid strategy that incorporates both static and dynamic detection techniques is necessary to overcome the difficulties presented by evasive malware.
E. Comparing with Current Methods
A comparison was made between the performance of the recently developed YARA rules and the public YARA rule sets that were already in place. Our comparison revealed a few of our method's benefits, particularly with regard to detection efficiency and accuracy. In comparison to conventional rule sets, the recently created rules show better performance in identifying both known and undiscovered malware variants by utilizing modularity and dynamic detection techniques. Although they worked well for some common malware kinds, the public rules that were in place had trouble identifying sophisticated and elusive threats.
It is crucial to remember that current YARA rule sets are a valuable resource for general-purpose detection because of the security community's combined efforts and continuous upgrades. Although the recently developed rules in this investigation demonstrated a greater detection rate for sophisticated malware, their usefulness is somewhat constrained by the requirement for frequent updates in order to continue to function. Therefore, in order to obtain the best malware detection, it is essential to combine the implementation of bespoke YARA rules with community-driven updates.
F. Consequences for Malware identification
The results of this study highlight the significance of using a multifaceted strategy for malware identification. Even while YARA rules are still a very useful tool for detecting malware, how well they work depends on how accurate and well-designed they are.
To make sure that YARA rules continue to be effective against emerging threats, security experts must take the initiative to develop, test, and improve them.
Moreover, adding behavior-based detection techniques to YARA rule sets will become more crucial as malware gets more complex. Security systems will be able to identify a wider variety of malware, including those that use evasive tactics, by combining behavioral and dynamic analysis with signature-based detection.
This part on discussion and analysis looks at the advantages and disadvantages of various YARA rule-writing techniques, assesses how well they work, and offers suggestions for enhancing malware detection. It relates the study's conclusions to the larger cybersecurity framework and offers ideas for future developments to improve YARA's ability to identify contemporary malware.
V. COMPARING CONVENTIONAL APPROACHES
When it comes to malware detection, YARA rules offer a more contemporary and adaptable strategy than conventional detection techniques. Although identifying and categorizing harmful files is the goal of both approaches, their methods, efficacy, and flexibility vary greatly. In order to illustrate the advantages and disadvantages of each strategy, this section contrasts the YARA rule-based detection system with more conventional techniques like signature-based detection and heuristic analysis.
A. Signature-Based Detection
The most popular conventional method, signature-based detection, finds malware by analyzing pre-established patterns like file hashes, byte sequences, and static signatures that are particular to a given malware sample. Because it makes it possible to quickly and precisely identify files that precisely match a stored signature, this approach is quite effective at detecting known malware.
Advantages of Detection Based on Signatures:
- Efficiency: Signature-based techniques are quick and effective, particularly in settings with a lot of data. High accuracy in identifying previously encountered malware that has already been included in signature databases is what they provide for known malware.
- Restrictions: Incapacity to Detect Unknown Malware: Unless a signature is made especially for a particular malware variant, signature-based detection is unable to detect novel or unknown malware variants. To avoid signature detection, malware developers frequently alter or obfuscate their code.
Malware that is both polymorphic and metamorphic can easily evade detection since signature-based techniques are inadequate against these types of malware, which alter their code with each infection and rewrite their own code completely.
B. Heuristic Analysis
Heuristic analysis assesses the behaviour of files and programs to identify whether they display harmful characteristics, going beyond signature-based detection. Heuristics evaluate characteristics that are frequently linked to malware, such as odd system calls, API interactions, and other actions. Heuristic analysis still has a number of issues, even though it may identify malware that has been altered or never been seen before by examining its behaviour.
Heuristic Analysis's advantages:
- Unknown Malware Detection: Even in the absence of an existing signature, heuristic approaches are more effective in spotting novel malware strains by spotting questionable behaviours.
- Adaptability: By concentrating on activities rather than particular signatures, heuristic detection systems are able to adjust to new threats more rapidly.
- Restrictions:
- False Positives: Because heuristic detection flags a wide range of activities as suspicious, it frequently produces false positives. Malicious software can also be identified from benign software that behaves like malware.
- Intensive on Resources: Because heuristic-based detection techniques must evaluate the activity of files or programs in real time, they frequently demand additional processing power, which can cause system lag or performance bottlenecks.
- Restricted by Complexity: Expert malware can still avoid heuristic detection by employing complex evasion strategies like delayed execution or sandbox detection.
C. Behaviour-Based Detection
The goal of behaviour-based detection is to track and examine real-time file, process, or network activity. This technique is excellent at identifying malware that only becomes active after it has been executed, including trojans that transmit private information to distant servers or ransomware that encrypts files. Such systems can frequently uncover risks that were previously unknown based on their actions rather than just their appearance by monitoring behavioural anomalies.
Behaviour-based detection's advantages include:
- Real-Time Detection: Behaviour-based detection works well to find malware, including advanced persistent threats (APTs) and zero-day attacks, that don't show any telltale signs until they are executed.
- Evasion Resistance: Unlike static signature-based methods, this methodology is less susceptible to evasion by techniques like code obfuscation, encryption, or polymorphism.
- Restrictions:
- High False Positive Rate: The system may incorrectly identify innocuous software or processes as dangerous since it flags any suspicious activity, resulting in needless alarms and an increased effort.
- Computationally Expensive: System performance may be slowed down by the substantial computer resources required for real-time behaviour monitoring and analysis.
- Absence of Context: When it comes to the general character of the activity under analysis, behaviour-based detection frequently lacks context. For instance, it may be impossible to tell the difference between a malware sample and a genuine program due to their identical characteristics.
D. Adaptability and Maintenance
The ability of traditional detection techniques to adjust to novel and developing threats is one of their main drawbacks. It may take longer to identify new threats using signature-based techniques since they need to be updated frequently to incorporate new malware samples. Despite being more flexible, heuristic and behavioural approaches frequently need to be adjusted and might not react to emerging threats fast enough, particularly when malware developers use cutting-edge evasion strategies.
The benefit of YARA: YARA has notable advantages in terms of customization and ease of upkeep when compared to other options. As new malware threats appear, YARA rules may be readily updated and improved because of its modular and flexible design. By creating YARA rules that concentrate on both known and unknown behavioural patterns, researchers and security analysts can integrate them with more extensive threat intelligence sources and make sure the rules remain current and applicable. Additionally, a more flexible reaction to changing attack methods is made possible by the utilization of YARA's regular expression and dynamic rule construction capabilities.
Each of the three traditional methods for detecting malware—heuristic analysis, behavior-based detection, and signature-based detection—has advantages and disadvantages. While heuristic and behavior-based approaches can identify unknown threats, they may produce false positives and have greater computing costs. Signature-based detection is effective, but it is unable to identify new or modified malware. Many of the drawbacks of conventional techniques are addressed by YARA, a rule-based detection system that provides an adaptable, effective, and highly customizable approach. YARA rules are an effective tool in contemporary cybersecurity efforts because they combine static and dynamic detection methodologies, enabling more precise and adaptable detection of both known and new malware.
Conclusion
In cybersecurity, the efficacy of malware detection has always been a major problem. As cyber threats continue to change, so too must our detection techniques. Malware security has long been dependent on conventional techniques including behavior-based detection, heuristic analysis, and signature-based detection. Although these techniques work well against recognized threats, they frequently have trouble identifying novel, unidentified, or evasive malware versions that take advantage of complex strategies like encryption, obfuscation, and polymorphism. YARA offers a substantial improvement in malware detection because to its highly adaptable and customizable rule-based methodology. YARA provides a more reliable method for identifying known and undiscovered malware by empowering security experts to create accurate and flexible rules that include behavioral analysis, system features, and signature-based patterns. Because YARA is modular, it can be continuously improved and adjusted to new threats, making it a powerful weapon in the battle against changing malware tactics. We showed throughout this study that YARA\'s detection capabilities for complex and elusive malware considerably outperform those of conventional signature-based detection. Furthermore, YARA is a priceless tool for identifying sophisticated, contemporary threats that frequently elude traditional detection systems due to its fusion of static and dynamic detection capabilities. YARA improves detection accuracy while lowering the possibility of false positives by integrating behavioral characteristics, API calls, and even memory-based patterns into rules. But it\'s important to understand that YARA isn\'t a universally applicable answer. The quality of the written rules and the continuous improvement process determine how effective the detection method is, just like any other. To keep YARA\'s rules current, its use necessitates frequent upgrades and knowledge of new malware behaviors. Additionally, by creating rules in modules and carefully balancing specificity and generalization, YARA\'s performance can be maximized. To sum up, YARA rules provide a very flexible, effective, and potent malware detection approach. YARA makes it possible to identify known and new threats more precisely by resolving the drawbacks of conventional techniques. Utilizing adaptable, rule-based systems like YARA in conjunction with other detection techniques will be essential for improving the overall efficacy of cybersecurity defenses as malware continues to change. Its capabilities will be further enhanced by future research and development in YARA rule authoring, as well as integration with threat intelligence and machine learning systems, making it a vital tool for the cybersecurity community.
References
[1] Zeltser, L. (2016). Introduction to YARA.] https://doi.org/10.1145/3411508.3421372 [2] Luta, G., & Gama, L. (2017). Automating YARA rule generation for malware detection.] https://ieeexplore.ieee.org/document/9292390/ [3] Gordon, R., & Mulliner, C. (2018). A study on improving the accuracy of YARA rules in malware detection.] https://doi.org/10.1007/s40747-020-00233-5 [4] Soni, P., & Chauhan, P. (2020). Evaluating the effectiveness of YARA rules against obfuscated malware.] https://arxiv.org/abs/2111.13910 [5] Dong, W., & Xu, Z. (2019). Leveraging machine learning for automatic malware detection with YARA rules.] https://ieeexplore.ieee.org/document/9292390/ [6] Wang, Z., & Zhang, H. (2020). Heuristic-based approach for automated YARA rule generation.] https://arxiv.org/abs/2009.03779 [7] Lipman, A. (2019). Real-time malware detection using YARA.] https://ieeexplore.ieee.org/document/10693305/ [8] Levin, D., & Novak, P. (2020). Scalability and performance of YARA-based malware detection systems.] https://publications.aston.ac.uk /id/eprint/42241 /1/Comparison_YARA_Rules_Generation_Tools.pdf
Copyright
Copyright © 2025 Vinay Patil, Naveen Kumar M, Pawan Singh M, Ashishika Singh. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET66535
Publish Date : 2025-01-15
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

