Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Encryption and Decryption of Messages using QR and Steganography
Authors: Yash Chaudhary, Gourav Sharma, Vaibhav , Puneet , Rajdeep
DOI Link: https://doi.org/10.22214/ijraset.2024.65010
Certificate: View Certificate
Abstract
The main motive of this project is to prevent data leak in chat applications. So, to cover a protection for it we are introducing a chat application in which you can share your important details in encrypt and receive in decrypt form which are QR and Image Steganography. For preventing of data leak, we have created an application based on QR code and Image Steganography encryption and decryption where you can chat with a specified person. Whom you want to send the encrypted message through hiding the data inside a verified signature QR code created by my team so that no other QR code app can encrypt the data inside the QR code which is shared inside our app. Here, in this project we will enter confidential information inside a text box that will be visible in app. Then each character of that confidential information will be converted into ASCII equivalent, Then the RSA algorithm will be applied for each value with private key and then generate the code word for the given information by using non-binary RS code, due to this if the QR code is damaged or distorted it is retrieved. The algorithm used for Encryption and Decryption in this application provides using several layers lieu of using only LSB layer of image. Writing data starts from last layer (8st or LSB layer); because significant of this layer is least and every upper layer has doubled significant from its down layer. So, every step we go to upper layer image quality decreases and image retouching transpires. The encrypt module is used to hide information within an image so that no one can view it. This module accepts any image or message and outputs only one image file to the destination. The decrypt module is used to extract information from an image file that is hidden.
Introduction
I. INTRODUCTION
Hiding data in a QR Code or Image is a type of conveying encrypted message to another user so that it can be protected from getting leaked to some other anonymous user. And there are many apps or software which is based on chat and data transferring. But those aren’t secure anymore as it can be leaked by the organization itself or by anonymous hacker. So, to prevent this we have made a software which is externally based on chatting and internally based on transferring data in encrypted mode with two types of option which is QR Code and Image (like we can hide data inside both of the given options and encrypt it and then send it to the correct user whom we want to, as the other user should have the same features to decrypt any of the options and get their message in secure form. So that no one can see their message or the data gets leaked.). In this project we are mainly using Steganography for both QR Code and Any Random Image where two users will transfer their data in encrypted form using QR Code or Image. As we know that Steganography is an art of hiding data in digital media. So, we are using that art in QR Code and given another option of Image, as it will work as an alternative. Then there will be a feature to decryption the encrypted QR Code/Image sent by the other user. Since the advent of the Internet, one of the most essential aspects of information technology and communication has been information security. Cryptography was developed as a method of communication and information security. Cryptography was developed as a mechanism for ensuring the confidentiality of communication, and many various ways have been developed to encrypt and decrypt data in order to keep the message secret. Unfortunately, it is not always possible to encrypt and decode data in order to keep the message private. Unfortunately, keeping the contents of a message secret isn't always enough; it's also important to keep the message's existence hidden. The message was hidden in the tofu. Steganography is the technique utilized to do this. This is known as Steganography. Steganography is the art and science of communicating invisibly. This is performed using Steganography, which is the art and science of communicating invisibly. This is achieved by concealing information within other information, hence concealing the existence of the sent information. Steganography derives from the Greeks term information. Steganography is derived from the Greek terms stegos, which means "cover and cover," and grafia, which means "writing," describing it as "covered writing." In image meaning writing, it is defined as covered writing. The information is only hidden in images in image steganography. The technical challenges of data concealment are severe. Lossy signal compression is likely to remove perceptual or statistical holes in host signals that need to be filled with data. Finding flaws that are not easily exploited by compression algorithms is an important aspect in achieving successful data concealing techniques. The major challenge is to insert data in these kinds of holes in such a way that compression algorithms cannot exploit them. A more difficult problem is to fill the gaps in a way that is resistant to large-scale signal modification.
A. About Java
The Java Platform is a set of programmes that aid programmers in the development and execution of Java programming applications. It consists of an execution engine, a compiler, and a collection of libraries. Sun Micro- systems developed the Java platform, which was later acquired by Oracle Corporation.
B. About Android Studio
The official Integrated Development Environment (IDE) for Android application development is Android Studio. Android Studio adds new capabilities to help us be more productive while developing Android apps. Android Studio was announced as an official IDE for Android app development on the 16th of May 2013 at the Google I/O conference. It began its early access preview in May 2013 with version 0.1. The first stable constructed version, starting with version 1.0, was released in December 2014. Kotlin has been Google's preferred language for Android application development from May 7, 2019. Aside from that, Android Studio supports a variety of programming languages.
C. Why are we using Java?
Using Java in this project because it is acceptable while making an app in android studio. As we know that, Java is used as a backend in android app. So, using tool java is easy for implementing new and optional features and it can also be easy later on for editing and making new changes in any of the screen or make a change in android app. Because of its amazing features and performance, Java is a very popular language. There is a sizable community of Developers who are proficient. Thus, android developers should choose java since there is already a large community of java programmers who can assist in the creation and improvement of android applications, as well as numerous libraries and tools that make developers' lives easier. Because of the large number of java developers, it is possible to construct a large number of Android apps quickly. Dvelopers that do not use Java face major issues such as memory leaks and incorrect pointer usage. These issues can sometimes have far-reaching consequences, such as application or OS crashes.
II. METHODS
A. Tester
The tester of the following android app was the developers who made it and it was also introduced to other team members of our project team. So that we can also get feedback from others like how the app is improving their daily secured way of sending information to others and yes, we received a good feedback from them. Also made some more improvements in app while it was in development phase, which was necessary so that it cannot be an issue later on while it will be launched on platforms which are introduced to us like Google Play store.
B. Test Protocols
There were many test protocols which was used while testing an android app like firstly, as a developer we checked the android app from each possible way in the first phase so, that it looks more attractive and innovative to the users who will use it later. Secondly, we were working on the QR code encryption and decryption app, so there were many test cases like testing the backend of encryption a message into QR code using matrix
III. DISCUSSION & RESULTS
A. Discussion
1) Image Encryption and Decryption
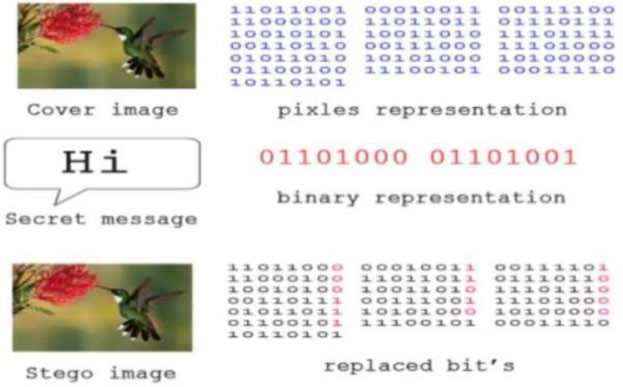
Fig 3.1.1(a) Process of Image Steganography
The steganography technique used is LSB coding which is performed in Encoding.java file. The offset of the image is retrieved from its header. That offset is left as it is to preserve the integrity of the header, and from the next byte, we start our encoding process. For encoding, we fist take the input carrier file i.e., an image file and then direct the user to the selection of the text file.
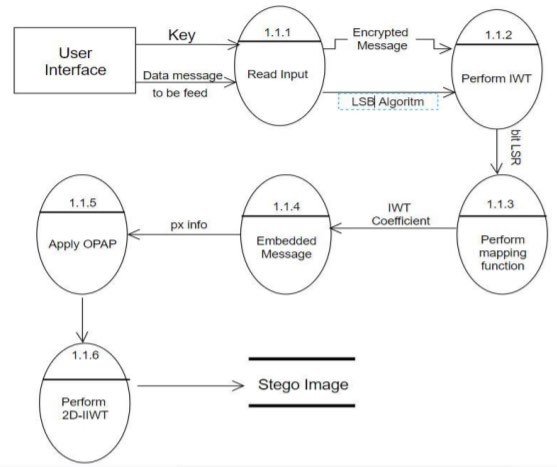
Fig 3.1.1(b) Level-2 DFD of Image Steganography
To keep the header's integrity, that offset is left alone, and we begin the encoding procedure with the following byte. We start with the input carrier file, which is an image file, and then send the user to the text file selection.
As input, a text file is read and divided into a stream of bytes. Each of these bytes' bits is now encoded in the LSB of the following pixel. Finally, using the ImagelO. Write method, we obtain the final image containing the encoded message, which is saved in PNG format at the user-specified destination. The encoding process is now complete. Create the user space using the same process as in the Encoding. Using getRaster() and get DataBuffer() methods of Writable Raster and DataBufferByte classes. The data of image is taken into byte array. Using above byte array, the bit stream of original text file is retrieved into another byte array And above byte array is written into the decoded text file, which leads to the original message.
2) QR Code Encryption and Decryption
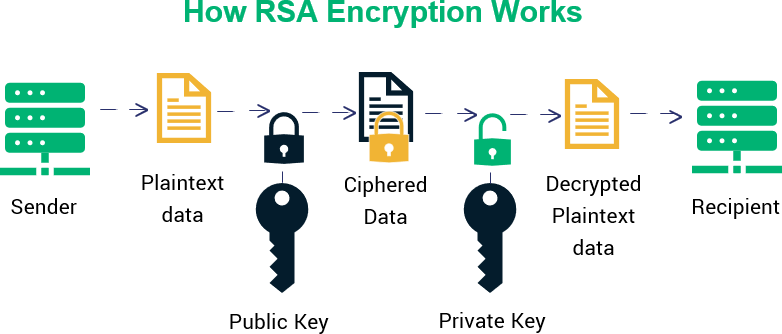
Fig 3.1.2(a) Process of QR Code
The QR technique used is RSA coding which is performed in GenrateQR.kt file. First, we take the text as input and convert it into array and using the characters of text we generate the QR from the inbuilt function. Along with that we pass a secret code in QR generation which can only be read by the scanner code we provided.
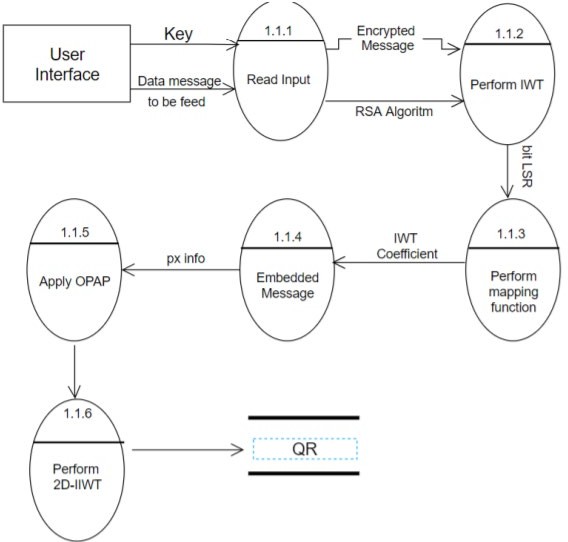
Fig 3.1.2(b) Level-2 DFD of QR Code
The offset of the image is retrieved from its header. Firstly, we ask the user for permission on Request Permissionresult() method and then when the user gives the permission we open the scanner by InitiateScan() method to scan the QR and check whether the key matches with it , if it matches then extract the hidden text and display it as a message.
3) Errors While Scanning QR and Image
This error mainly appears before the splash screen when the user/tester doesn’t give access to camera in the starting of opening/running android app. And then when the user or tester starts scanning or uploading an Image or QR code, this app crashes and for fixing it we need to go in the app info from settings of mobile device and then go to permission folder and select camera and files access to allow every time. So, that there won’t be any delays while launching android app.
4) App crash while Implementing of Encryption and Decryption Feature
While implementing the feature of encryption and decryption in QR code app, there were some errors which was causing to store the encoded files (like when we are encoding message inside an QR code or image the final compilation of the file is been shown as file encoded and saved). But when we locate the file manager or storage where the encoded file should be saved by default (in Internal Storage-> Downloads), there we couldn’t find the required file. This same Erro was occurring in case of steganography also, as it contains the same procedure. There was one more error which is delay in saving the encoded file. As the image should be save while clicking the file save button which will take 4 seconds maximum. But before it was taking more than 1 minute. So, we fixed the errors which appeared during the testing phase of an android app.
B. Results
So, this was the brief process about the function of Steganography application. Let’s see the results after installing the application in our device. The first thing we see is:
- Splash Screen: This screen is the logo screen which is available for 2 seconds and then it gets disappeared.
- Home Screen: This is the main screen where we choose our choice whether to encrypt or decrypt. Based on the choice we can select the option and then we can move ahead.
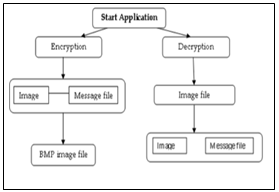
- Encrypt: If we choose encrypt option, we get to the encrypt screen where we have to first, upload an image and then type our private key and secret message. After that we use the Encrypt button to encrypt the secret message to the image and then save button to save it in our device.
- Decrypt: If we choose Decrypt option then we must upload the encoded image from our storage options and then enter the private key. If the private key is incorrect, it will display a toast of incorrect else the decrypt key will show the encrypted message on the Hidden text field.
We know about the function of QR application. Let’s see the results after installing the application in our device. The first thing we see is:
- Splash Screen: This screen is the logo screen which is available for 2 seconds and then it gets disappeared.
- Home Screen: This is the main screen where we choose our choice whether to generate or scan. Based on the choice we can select the option and then we can move ahead.
- GenerateQR: If we choose Generate option, we get to enter the text and click the generate button. Then we get to see the QR code that is encrypted and we can save it.
- ScanQR: If we choose Scan option then the rear camera with flash light option gets turned on. We can then Scan the QR code and get our encrypted message.
Conclusion
As steganography has become more widely employed in computing, and there are issues that required to be resolved. There is a good form of different techniques with their own advantages and drawbacks. Many currently used techniques don\'t seem to be robust enough to forestall detection and removal of embedded data. the utilization of benchmarking to judge techniques should become more common and a more standard definition of robustness is required to assist overcome this. For a system to be considered robust it should have the subsequent properties: 1) The standard of the media shouldn\'t noticeably degrade upon addition of a secret data. 2) Secret data will be undetectable without secret knowledge, typically the key. 3) If multiple data are present, they must not interfere with one another. 4) The key data should survive attacks that do not degrade the perceived quality of the work. This work presents a scheme that may transmit large quantities of secret information and supply secure communication between two communication parties. Both the concept of steganography and cryptography will be woven into this scheme to form the detection more complicated. Any kind of text data will be employed as secret message. the key message employing the concept of steganography is shipped over the network. additionally, proposed procedure is straightforward and straightforward to implement. Also, there are many developed systems which has many practical, personal and militaristic applications for both point- to-point and point-to multi- point communications. After Steganography based encryption, we will further convert the encrypted image into QR codes. this may lead to more encrypted data. Our QR encryption method allows us to handle the method. We use our own technique so other apps cannot decrypt it Its benefits, application areas, and its impact on marketing and technological world. Originally designed and used for inventory tracking, QR codes have since found uses in a variety of different fields such as marketing, advertising, secure payment systems, education, and so on. Due to advantages such as large data store capacity, fast scanning, error correction, and direct scanning, QR code adoption has accelerated in recent years, and the number of users has increased significantly marking and simple use.
References
[1] R.M. Redlich, M.A. Nemzow, Digital information infrastructure and method for security designated data and with granular data stores: US, US9734169 [P] (2017). [2] Z. Han, S. Huang, H. Li, et al., Risk assessment of digital library information security: A case study [J]. Electron. Libr. 34(3), 471–487 (2016) [3] https://www.scribd.com/document/86328469 [4] http://programmer2programmer.net/live_pr [5] https://www.engpaper.com/cryptography-20 [6] https://www.nap.edu/read/15269/chapter/5 [7] https://www.quora.com/How-do-I-build-a-s [8] https://people.cs.rutgers.edu/~pxk/419/e [9] https://www.researchgate.net/publication [10] https://www.researchgate.net/publication [11] https://quizlet.com/238052166/religion-s [12] https://www.academia.edu/6827897/Key_Bas
Copyright
Copyright © 2024 Yash Chaudhary, Gourav Sharma, Vaibhav , Puneet , Rajdeep . This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET65010
Publish Date : 2024-11-05
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

