Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Energy Efficient for Data Aggregation in Wireless Sensor Networks
Authors: Yash Verma, Inakshi Garg, Vyshnavi Mamidipelli, Nivas Kumar
DOI Link: https://doi.org/10.22214/ijraset.2024.59774
Certificate: View Certificate
Abstract
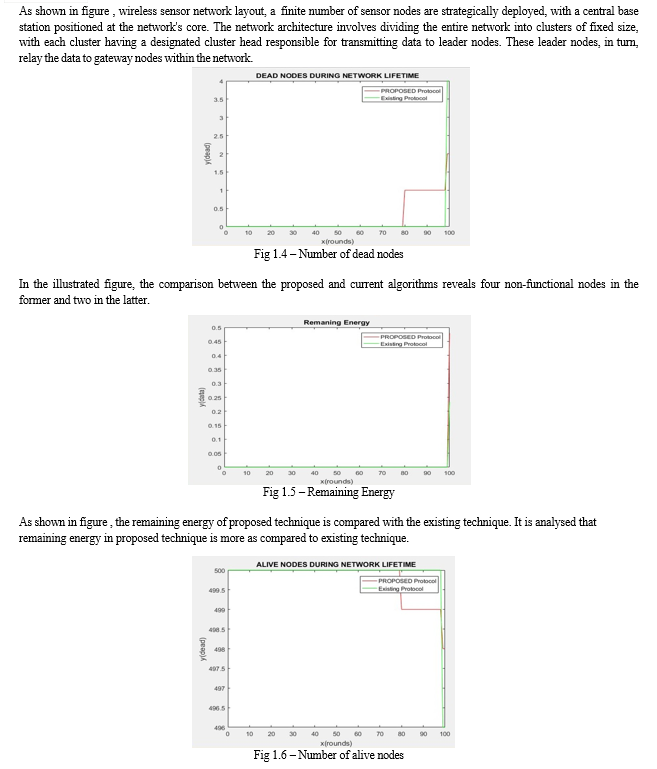
The Wireless Sensor Networks (WSNs), known for their decentralized and self-configuring properties, utilize sensor nodes to collect and transmit data to a base station. However, due to their sprawling nature and the substantial distances involved, energy management remains a critical challenge in WSNs. To mitigate this, hierarchical clustering has been identified as an effective strategy. This approach involves dividing the network into clusters of a predetermined size, each led by a cluster head selected based on their energy levels and proximity to the base station. The chosen head is typically the node with the least distance to the base station and the highest energy reserve. These heads facilitate inter-cluster communication and data transfer to the base station. This research presents the implementation and enhancement of the WEMER protocol, aimed at prolonging the lifespan of WSNs. The WEMER protocol initially segments the network into clusters with respective heads and designates leader nodes to relay data from the cluster heads to the base station. Enhancements to this protocol include the deployment of gateway nodes close to the base station. These nodes receive data from the leader nodes, which in turn acquire data from the cluster heads, thus boosting network longevity. Implemented and tested in MATLAB, the enhanced WEMER protocol demonstrates significant improvements over its predecessor. The results indicate a reduction in the number of inactive (dead) nodes, an increase in active (alive) nodes, a higher data packet transmission rate, and improved overall energy efficiency.
Introduction
I. INTRODUCTION
A. Introduction to Wireless Sensor Networks
A Wireless Sensor Network (WSN) comprises an extensive array of sensor nodes, strategically deployed to gather and process vital information from their environment. These sensor nodes are notably small, which limits their processing power and battery capacity. They adaptively collect data based on environmental changes and transmit this information through the network. Given their small size, these networks face significant computational and processing limitations.
In this context, 'motes' are introduced as compact computing devices responsible for data acquisition throughout the area. Today, motes find extensive use in various industrial settings. By employing a network of motes, specific goals within an application are achieved through the comprehensive collection of environmental data [1]. These motes are interconnected in diverse configurations to optimize performance. For inter-mote communication, transceivers are utilized. In practical applications, a WSN may encompass hundreds to thousands of these sensor nodes. This contrasts with ad hoc networks, which typically have fewer sensor nodes and lack a fixed infrastructure.
In constructing a sensor node's sensing unit, multiple sensors are integrated to gather crucial environmental data. This data, captured by the sensing unit, is relayed to the processing unit for effective utilization after being processed. The transformation of analog signals from sensors into digital format is achieved through an Analog to Digital Converter (ADC), which then sends the signal to the controller for further processing. A pivotal component of a sensor node is its processing unit, which is responsible for executing various tasks through its inbuilt processor. This unit is pre- programmed and configured via services offered by the sensor nodes. The energy consumption rate of the processor varies based on the node's functions. The processor's performance can be assessed using several metrics, including memory capacity, data rate, and processing speed. The processing unit, aided by the communication unit, facilitates seamless computations. This unit then transmits the processed results to the base station, from where they are conveyed to external users. The basic transceiver within the sensor node serves as a communication unit, handling the transmission and reception of data between the nodes and the base station. The communication unit operates through four critical stages: transmitting, receiving, idling, and sleeping. Furthermore, the efficiency of the communication unit is paramount for optimal network performance, ensuring minimal energy usage while maintaining data integrity. The sensor nodes are equipped with limited power sources, necessitating judicious energy management, especially during data transmission. Additionally, the sensor nodes are programmed to dynamically adjust their operational modes, transitioning between active and dormant states to conserve energy. This adaptability is crucial in extending the overall lifespan of the sensor network and multi-nodal systems, demonstrating its versatility in diverse environments.

Following are some of the important properties of sensor nodes that help in evaluating the performance of WSN:
- Resilience to Faults: Each node in the network is susceptible to unexpected failures [2]. Fault tolerance refers to the capability of maintaining the core functions of sensor networks, even in the event of node malfunctions.
- Node Mobility: Depending on the application, sensor nodes have the flexibility to move within the deployment area, enhancing network communication efficiency.
- Dynamic network topology: A standard network topology is determined by the connections among sensor nodes in various applications. Incorporating dynamic topology can further improve the performance of WSNs.
- Heterogeneity of nodes: Given the variety of sensor nodes in WSN applications, their cooperative interaction is essential for task execution.
- Network Scalability: The network, comprising hundreds to thousands of sensor nodes, must support high scalability.
- Independency: To perform different tasks in these networks, no central authority is required here.
- Programmable Networks: To enhance adaptability to changing conditions, these networks may require reprogramming or reconfiguration. Utilization of sensors: It is important to ensure that minimum energy is consumed by sensor nodes such that highest performance results are achieved.
- Constraints on Public Key Cryptosystems: Due to limited computational and power resources, employing public key algorithms in these networks is impractical.
- Uncertain Post-Deployment Configuration: With the random distribution of sensor nodes, predicting the communication status post-deployment is challenging.
- Network Characteristics
When deploying a Wireless Sensor Network (WSN) in a targeted area, numerous sensor nodes are strategically positioned. These nodes are notable for their affordability, compactness, and multifunctional capabilities. Despite their diminutive size, they are capable of processing tasks effectively [3]. The wireless medium in these networks facilitates short- range communications, allowing nodes to collaborate closely to achieve a shared objective. WSNs possess distinct characteristics that set them apart from other network types, which are outlined below:
a. Dense Deployment: In the specified region, sensor nodes are densely deployed, outnumbering those in mobile ad hoc networks.
This high-density deployment is a common strategy in WSNs.
b. Power Source: Sensor nodes in WSNs are typically battery- operated. In many cases, these networks are situated in hostile environments where battery recharging or replacement is not feasible once the energy is depleted.
c. Self-Organizing Nature: Sensor nodes do not require predefined planning or engineering for deployment. They are often deployed randomly and can self-organize based on specific application needs [4].
d. Application-Dependent Design: WSNs are tailored according to the application, with design requirements varying significantly based on the intended use.
e. Node Reliability Issues: Deployed in various challenging environments, sensor nodes may not always be required for certain operations and are susceptible to physical damage and failures.
f. Dynamic Topology: The network topology is subject to frequent changes, often due to channel fading or node failures.
g. Lack of Universal Identification: Given the vast number of sensor nodes, it's impractical to implement a global addressing system for the network, leading to increased overhead and identity maintenance challenges.
2. Issues and Challenges in Designing WSN
In designing Wireless Sensor Networks (WSN), several challenges emerge, including:
a. Topology Flexibility: The deployment of sensor nodes involves scattering, eliminating the need for a fixed network topology.
b. Resource Constraints: These networks face limitations in various aspects, including:
- Restricted memory capacity.
- Computational limitations.
- Unreliable communication channels.
- Limited power resources.
c. Infrastructure and Maintenance Issues: The absence of a built-in infrastructure in WSNs leads to:
- Unpredictable data transmission reliability.
- Potential conflicts and latency issues.
d. Power Source Limitations: The battery power in WSNs, often in inaccessible locations, cannot be easily replaced or recharged.
e. Sensor Node Hardware Considerations [5]:
- These nodes typically operate unattended.
- Vulnerability to physical attacks.
- Remote network management is necessary.
- Lack of centralized control within the network.
f. Synchronization Requirement: Ensuring that sensor nodes are synchronized poses an additional challenge.
g. Network Topology Variability: The addition or removal of nodes, as well as potential node failures, can lead to changes in network topology.
h. Security Concerns: The unique transmission characteristics and hostile deployment environments of WSNs make security a paramount challenge.
i. Node Selection Criteria: The choice of sensor nodes depends on the type of application and computational requirements involved.
- Network Applications
Sensors within these networks enable the monitoring and detection of environmental conditions, giving Wireless Sensor Networks (WSNs) an edge over traditional wired networks. While not all costs and delays can be completely eliminated in these networks, their advantages are numerous. WSNs find diverse applications, spanning from military uses to a variety of smaller-scale deployments. The affordability and communication efficiency of sensor nodes make WSNs highly adaptable for a range of uses, including both military and civilian purposes. Here are some specific domains where these networks have been implemented:
a. Environmental Monitoring
A primary function of Wireless Sensor Networks (WSNs) is environmental monitoring, with their initial application being in military settings [6]. These networks are crucial for tracking environmental changes, providing timely data on various conditions.
- Habitat Observation: WSNs play a significant role in observing the status of flora and fauna, as well as collecting data on different habitats in specific regions.
- Air and Water Quality Assessment: Sensors are strategically deployed to assess the quality of air and water in specific locales. For example, they monitor water quality in hydrochemical areas and help manage air pollution by providing accurate air quality data.
- Emergency and Hazard Detection: WSNs are instrumental in identifying potential emergencies in biological or chemical environments, contributing to timely responses.
- Disaster Management: These networks are also employed to detect natural or human-made disasters. Sensors distributed across forests, for instance, can detect forest fires or flooding, while earthquake sensors help determine the direction and magnitude of quakes, aiding in the protection of people in affected buildings.
b. Military Applications
Wireless Sensor Networks (WSNs) fulfil critical roles in various domains, including military operations and telecommunications. Their ease of deployment, self- management capabilities, and fault tolerance make them integral in C3I (Command, Control, Communications, and Intelligence) systems. WSNs contribute to reducing human involvement in combat zones and have been instrumental in advancing intelligent systems.
- Battlefield Surveillance: Sensor nodes are deployed across battlefields to continuously monitor military forces and vehicles. This allows for real-time tracking of vehicle movements and the collection of strategic information.
- Asset Protection: In sensitive applications, sensor nodes are employed to safeguard important objects, ensuring constant surveillance and security.
- Intelligent Coordination: WSNs are pivotal in coordinating between robotic vehicles, military tanks, and missiles for strategic defensive actions against adversaries.
- Remote Detection: Sensors deployed in various areas play a key role in identifying chemical or nuclear threats, thus aiding in the prevention of terrorist attacks.
c. Health Care Applications
Various health departments have lack of health care personnel due to which the health of patients is at risk. Thus, the sensor networks are deployed within such hospitals so that the patients can be monitored at all times and the help required can be provided to them [7]. Thus, there is reduction in cost expenditures of these health care systems as well.
Behaviour Monitoring: The deployment of sensors is done within homes such that the behaviours of patients or normal people can be done to keep a check on their activities. The doctors are informed regarding any kind of emergency situation arising here. The sensors pass the instructions or reminders to the patients by keeping a track on their activities. Medical Monitoring: Wireless body area networks (WBANs) are deployed within the homes of old age people to keep a track on their daily activities. Within several other applications as well such as the hospital buildings, these networks are deployed so that a proper monitoring of all the patients can be done, and their medication can be given according to the requirement. The doctors are informed regarding any kind of emergency conditions and immediate actions are taken as per the need. Further, to keep a track regarding the health improvement of a patient, its tracks over certain period of time are maintained which can also be done here.
d. Industrial Process Control
With the help of deploying WSNs, it is possible to manufacture the devices or the conditions in which the industries are needed to be generated. For instance, the wireless sensors can help in monitoring and controlling the production process in the assembly and production lines.
The chemical regions or oil refiners use the sensors such that the conditions of pipelines can be monitored. It is not possible to monitor the conditions of machinery from the regions that are out of reach of humans. Thus, any kinds of failures in such regions can be identified and preventive measures can be taken accordingly. For preventing further any failures, the sensors are deployed such that the actions can be tracked. A schedule commonly is set up here as per which the machinery is checked with the time interval such that the equipment can be maintained. However, the cost of such systems is higher. The sensor networks maintain the devices on the basis of the conditions of the equipment. It is possible to minimize the cost of maintenance which can further result in increasing the lifetime of machines.
e. Security and Surveillance
The deployment of WSNs is done within several security and surveillance applications. For example, the acoustic or video sensors are deployed in the buildings, airports and underwater applications such that the important information can be gathered. In these applications it is possible to identify and track any kinds of intruders and for preventing any failures, various protection techniques are applied within these applications [8]. These applications also do not require any fixed infrastructure. Various security applications are set up in the systems such that power and communication facilities can be provided in these networks.
f. Home Intelligence
Through the deployment of WSNs in various applications, a convenient and intelligent living condition is introduced. Some of such applications include:
- Smart Home: By deploying wireless sensors in the homes and linking them with each other, an autonomous network is created at homes. For instance, using the inventory present within the refrigerators, a menu can be created by making a direct connection within the smart refrigerator and the smart stoves.
- Remote Metering: The deployment of WSNs is done such that the utility meters available within the home can be read remotely. For instance, the readings of water, gas or electricity can easily be taken remotely through the sensors and provided to user through wireless communication.
B. Energy Consumption in WSN
The WSNs consist of un-attended and un-tethered sensor nodes within them which help in monitoring the surroundings. Within the area of interest, the distribution of these sensor nodes is done, and multi-hops are used to transfer such information further [9]. With the help of such deployments, an ad hoc network is created in this manner. The sensor nodes include within them the battery powers which are small in size and irreplaceable or rechargeable. The nodes collect important information which is processed and stored within the sink node or the gateway node which is usually one within the region. An important component of sensor nodes is battery which helps in performing data acquisition. It is, however, not possible to recharge these batteries. The batteries include few energy generating units which are known as photo-voltaic cells within them. Due to the node acquisition the energy of order 1 to 2 J is provided as there are very small sized sensor nodes present in the networks. Thus, there is limited lifetime of a sensor and because of this, the overall performance of network also gets affected. The energy of nodes of WSN is the most important factor to be considered. For increasing the lifetime of networks, it is important that the energy can be saved from hardware and software solutions provided in the network. As per the various research made on this network, it is seen that data communication consumes higher amount of energy in researchers have introduced various routing protocols which have been categorized into various categories. All such categories have been presented below:
- Location-based Protocols
The location-based protocols focus on the information related to the location of sensor nodes. The location of sensor nodes is important to be known by most of the routing protocols such that the distance amongst two particular nodes can be calculated. This mechanism also helps in calculating an estimate of amount of energy that is being consumed by the networks. The researchers have proposed several such protocols amongst which few have been described below:
Geographic Adaptive Fidelity (GAF): The Mobile ad hoc networks initially proposed this protocol. Due to the benefit of providing energy conservation, this type of protocol is used by WSNs as well. The GAF protocol is introduced on the basis of energy model through which energy consumption is known [11].
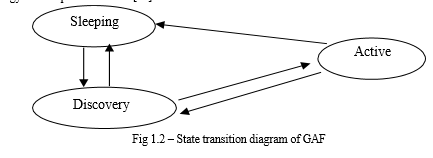
Along with recognition of availability of incoming packets when radio sensor is working, it is possible to transmit comparison to other activities being performed in the network [10]. Thus, there is a need of only short-range communications in these networks such that less transmission power is being consumed. The long-range communications are avoided in these networks. The sensing of events by WSNs near to the region of interest and far from the sink nodes is also possible. therefore, for forwarding data packets over larger distances, multi-path communication is required with the help of intermediate nodes.
C. Routing Protocols in WSN
It is very different to perform routing within WSNs as compared to the conventional routing that is performed in fixed networks. As the network does not include any infrastructure, the wireless links provided are unreliable. The routing protocols provide node failures here due to which it is important to save energy in the networks. Several and receive the packets in these networks. GAF turns off any kinds of unnecessary sensors available in the network. This also ensures the maintenance of constant level of routing fidelity. The GAF helps in dividing complete sensor field into grid squares and each sensor provides the information that is relevant to the location of the node. The above figure 1.2 shows the three different stages of GAF which are discovery, active and sleeping. When a sensor is in a sleeping stage, the radio is turned off such that the energy can be saved. For identifying the sensors present in similar grid in the discovery stage, the sensors exchange the discovery messages amongst each other. There is a periodic broadcasting of the discovery message even in the active state, when a sensor node is informed related to its state. The amount of time that is consumed by all of the states is tuned by the application. However, it is important to consider few of the important factors such as requirement and sensor mobility. The major objective here is to increase the lifetime of network [12].
Trajectory-Based Forwarding (TBF): This protocol is used such that a dense network can be deployed, and a coordinate system can be generated in the application. The system can be self-localized, and it is also possible to estimate the distance of neighbours here. The source mentions the trajectory within the packet. Although, it is not possible to identify the path depending on the hop-by hop communication. With the help of location information about the neighbours, a greedy decision is made here. This helps in knowing the next hop that is closes to the trajectory. The route maintenance amongst TBF is not affected by the mobility of sensors when a trajectory node is involved such that no forwarding nodes are provided.
Bounded Voronoi Greedy Forwarding [BVGF]: This is a type of protocol in which similar to the Voronoi diagrams, the geographical positions of sensors are considered to be very important. With the help of sites given in the diagram, the locations of sensors are represented in this protocol. The neighbour that has minimum distance towards the destination is forwarded the packet here. The greedy geographic routing approach is used to do so [14]. For the sensors that can easily act as next hops, the Voronoi areas are traversed by the segment line from which the source and destination are joined. BVGF selects the neighbour that has the shortest Euclidean distance towards the destination from all the neighbours that are eligible to be selected as next hop.
Geographic Random Forwarding (GeRaF): A routing protocol in which a prior to the sensor that acts as relay is not known by the sender is known as GeRaF routing protocol. During all the time intervals, the forwarding of message to the sink is not ensured here. Therefore, best effort forwarding protocol is another name for this type of protocol. Depending on the assumption of this protocol, the physical locations of all sensors available and sink are known in this routing protocol.
- Data Centric Protocols
These types of routing protocols are very different from others as from source to the sink the data is transmitted here. Each source sends the data to the sink in an independent form such that these address-centric protocols can process it. The data that originates from multiple source sensors is aggregated using the data-centric protocols when the transmission is to be performed amongst the source and sink of the network. The amount of energy being saved here is higher as very less amount of transmission from source to sink is needed here. Following are few of these types of protocols:
Sensor Protocols for Information via Negotiation (SPIN): In order to improve the classic flooding protocols and solve several issues related to routing, SPIN protocol has been introduced [15]. The two categories of this protocol are resource aware and resource adaptive. With the help of sensors that are available within these protocols, the energy that is required to compute, transmit and receive the data from network is consumed. The decisions are made here therefore, by using the own resources in an efficient way. The two approaches in which these protocols are used are the negotiation and resource adaptation.
Directed Diffusion: The introduction of directed diffusion protocol is done such that sensor query dissemination and processing can be provided to the networks. This protocol helps in fulfilling several requirements of WSN. This approach utilizes data naming, data propagation, and interests etc. as elements within them [16].
2. Hierarchical Protocols
Different researchers have proposed several viewpoints on the basis of which hierarchical clustering in WSN has been evaluated and developed. Clustering is the effective communication protocol used to transmit the sensed data towards sink. This study presents a view over the sample of layered protocols involved within various clusters of sensors. Each cluster includes within it a special node known as cluster head. There are few special activities performed by this cluster head for other nodes of the cluster. The hierarchical approach introduced here generates various clustered layers. When the nodes are grouped to create clusters, a cluster head is chosen amongst them. Towards other base stations or cluster head routing from one cluster is performed. The data is forwarded to higher layer from lower clustered layer [17]. Following are few of these types of routing protocols:
Low-energy adaptive clustering hierarchy (LEACH): When the energy efficient clustering algorithm called LEACH is applied within the network, there is reduction in the overall energy being consumed by it. The clustering task is rotated amongst the nodes on the basis of time duration left or energy remaining for a sensor node. Direct communication is provided for each cluster head such that the data can be forwarded to the base station. The clusters are used to increase the lifetime of WSNs. Aggregation is known as the mechanism through which the original data is combined from small grid sized data that is forwarded to the individual sensors. The LEACH protocol uses this aggregated data [18].
Power-Efficient Gathering in Sensor Information Systems (PEGASIS): By creating chains of sensor nodes in this manner that the neighbours can transmit and receive the data from neighbours, the LEACH protocol is enhanced. It is named as PEGASIS. From the created chain, only one node is selected such that the data can be transmitted towards the base station. The data is forwarded from one node to the next and then the base station receives this protocol at the end. For constructing the chains such that one sensor dies, similar greedy mechanism is used only with the exclusion of failure sensor. This is done because of the depletion of power of batteries present in the nodes. After each round, the aggregated data is transmitted to the base station through the random selection of sensor node from the chain generated [19]. Therefore, there is less amount of energy consumption as per each round in comparison to LEACH protocol.
Hybrid, Energy-Efficient Distributed Clustering (HEED): Within cluster selection process of HEED, the residual energy and node degree are used as metrics such that a power balance condition can be achieved. This protocol is basically an enhanced version of LEACH. For providing an inter-cluster communication and also providing multi-hop networking operations, the adaptive transmission power is used.
Threshold Sensitive Energy Efficient Sensor Network Protocol (TEEN): TEEN is known as the grouping of sensors into clusters in which individual cluster heads are present. With the help of sensors available in the cluster, the information that is sensed is aggregated to the CHs. The CH of higher level is then forwarded this information and the process keeps continuing in this manner till the base station receives this data. TEEN is introduced depending upon the hierarchical grouping that creates the clusters using nodes that are near to each other. TEEN is only applied within the applications that have a proper maintenance of the energy efficiency, accuracy and response time.
Adaptive Periodic Threshold Sensitive Energy Efficient Sensor Network Protocol (APTEEN): APTEEN is introduced by integrating LEACH and TEEN. This protocol helps in solving issues that arise using TEEN protocol. In this protocol, there is periodic transmission of sensed data and information related to any kinds of modifications within the value of sensed attribute is provided to the CHs. The architectural designs of TEEN and APTEEN are however much alike [20].
D. Review of Literature
Ramin Yarinezhada, et.al (2018)presented the relationship shared between the sensor nodes and sink node as it forwarded the more traffic loads in the wireless sensor network. This huge traffic leads to depletion of large amount of energy. Therefore, in the network, there is partition between the nodes and the sink isolation. In order to solve the above-mentioned issue, they utilized the mobile sink in this network. The appropriate use of the mobile sinks within the network creates the balance in the consumption of energy. Sensor nodes must know the position of the mobile sink in advance which is required to transfer the data to the network [21]. In case, the sensor nodes know the position of the sink in the network, there is more consumption of energy and delay in the network. On the basis of virtual grid infrastructure and mobile sink, they proposed a routing algorithm in this paper. The nodes are selected from the network using, proposed method and with the use of virtual infrastructure, which help in maintaining the position of the sink. They performed experiments and concluded results shows the effectiveness of the proposed method in terms of performance, energy efficient and compared delay as compared to the other methods.
Ram Murthy Garimella, et.al (2018)presented the wireless sensor network in this paper, in which essential role is played by the energy efficiency.
This issue is considered as the major in this network due to which various methods has been proposed by the researchers so far. Clustering the widely utilized technique was used in these algorithms but it does not show the mathematically validation. Hence, in order to fill the research gap, they proposed a system and method in this paper. For the process of data gathering and routing in the wireless sensor network, the concept of the Hessian matrix was used for the utilization of efficient energy techniques in this paper [22].This concept was utilized for the validation of the proposed method having the multi variable calculus. On the basis of assumption, in the multidimensional space, these wirelesses sensor nodes are distributed. The performed experiments evaluated the proposed method and illustrated that it can be utilized in any clustering approach using its mathematical design and provide the low-energy communication structure.
Deepa PUNEETH, et.al (2018)presented the study related to some parameters that plays an essential role in the functionality of the wireless sensor network such as energy efficiency, data reliability, and security. The combination of the cryptographic secret sharing technique and the disjoint multipath routing scheme must be used to make a effective and efficient approach that address all the these requirements. The Shamir’s secret sharing (SSS) provided the reliability and information-theoretic security but not able to provide the energy efficiency and optimal results linked to it. In order to obtain the energy efficiency and data reliability, they provided the Shamir’s ramp secret sharing (SRSS) in this paper [23]. The compromised node (CN) attack is the limitations of these approaches which occur when there are minimum numbers of nodes are compromised. Therefore, to overcome all the above-mentioned issues, they proposed another method in this paper using which security against CN attacks is provided. It also provided the data reliability, efficient energy in the network. The split hop AES (SHAES) defined the integration of SRSS and a round-reduced AES cipher which was their main objective. They performed various analysis and simulation, for the validation of the method near-sink CN attack. The obtained results concluded the superiority of the proposed methods as compared to other methods.
Peijun Zhong, et.al, (2018)presented the extensive application of wireless sensor networks is due to the vast development and emerging technology, it has been utilized it various different fields. The sensor nodes are deployed in this network which gathered all the data, further send to base station for the communication. Various methods have been proposed so far in order to mitigate the effects of major issues faced in the network. They discussed the hot spot problem as the base station is closer to nodes of the network which tend to die earlier than other sensors. Therefore, they introduced the concept of mobile sink node, in order to remove this issue effectively [24]. The nodes of hot spot can be distributed evenly in all direction as the sink node can move along certain trajectories. In detailed, they studied the energy efficient routing method in which multiple mobile sinks was used. In the several clusters the whole network was divided in order to perform various experiments to show the effects of mobile sink on the network lifetime.
Hassan Oudani, et.al (2017)presented the study related to the wireless sensor network and faced issues in this paper in which consumption of more energy leads to decease in the network lifetime. Therefore, consumption of power by the sensor nodes in transmitting and receiving data must be minimized for which a strategy is required. There are various algorithms and methods have been proposed so far by the researchers in order to increase the network lifetime of sensor. They also developed some hierarchical protocols that lead to reduce in the network traffic toward the sink and also enhance the working capability of network. They utilized the hierarchical cluster-based approach named as LEACHES in order to perform the survey on the energy efficient [25]. In order to minimize the issue of energy consumption and maximize the lifetime of network sensor, they proposed a new method in this paper. Therefore, they performed the simulation for the evaluation of proposed method and the performance of the LEACH protocol. MATLAB Simulink was used a simulator.
Nukhet Sazak, et.al (2017)presented the network in which sensor nodes are deployed randomly within the network where they can join and leave the network any time due to which significant design issues faced. There are some additional limitations faced by this network such as resource constraints, remote location, limited energy are the reasons due to which functionality of the network is degraded [26]. They proposed an active node determination method (ANDM) in this paper for WSN MAC design with the help of which, there is improvement in the energy efficiency. The integrated the ANDM with ETDMA and compared this combination with E-TDMA. The obtained results concluded the effectiveness of the proposed method which provides the usage up to 31 % approx. for the optimal energy.
Harshita Jain, et.al (2017)studied an important concern of wireless sensor networks of the limited lifetime of the battery and maintaining the energy efficiency of the network. The several sensing nodes are deployed randomly in the hostile environment in order to sense the physical conditions such as temperature, pressure and so on.
These sensor networks faced the issue of limited battery which is not possible for a human being to replace it as they are installed in the geographical region of hostile area. Therefore, once the battery exhausted, replacement process of battery causes major issues due to which this network is breakdown sometimes [27].
Therefore, due to these reasons, they discussed some energy efficient routing protocols for this network. There is reduction in the packet overhead, if there is updation in the routing tables frequently, which also minimizes the energy consumption rate of the network. The used the system named as power efficient gathering in sensor information system (PEGASIS) in which combine the dynamic source routing (DSR) which helps in determining the best path, similar to the GA and BFO.
Vivek Kumar Singh, et.al (2017) presented the set of independent transducers used as the communication infrastructure and installed at different locations for the purpose of monitoring and recording the data. In the wireless sensor network, sensor nodes are deployed by which the physical conditions are sensed. The parameters sensed by these nodes are energy, temperature, humidity, pressure, direction and speed of the node [28]. There are some major challenges that has been faced by this network such as efficiency, reliability, heterogeneity, scalability, robustness, privacy and security which hampered the network working. Therefore, in order to enhance the lifetime of the sensor network, they proposed a method in this paper. This method utilized the new cluster-based approach due to which reliable and energy efficient results provided by this method. The energy efficiency within the new cluster technique takes care the cluster head of the network, it is also helpful in preventing the crashes of cluster ead node provide the network reliability.
Sheikh Tahir Bakhsh, et.al, (2017)proposed a new algorithm in this paper named as adaptive sleep efficient hybrid medium access control (AEH-MAC), for the wireless sensor network. This method has been widely utilized for the improvement of scheduling. The sleep times of the nodes has been adjusted by this method which also minimizes the scheduling time. The major design issue faced in scheduling the algorithm in the wireless sensor network was the allocation of the resources to different attributes. It is required to develop more mechanism, as there is wastage of more power when the listening in WSN is in the inactive state, also that method which saves the energy of the network. The major issues faced by this network are limited energy and the lesser number of renewable resources. There is creation of delay in the network due to the utilization of fixed duty cycling that also helps in saving the energy of nodes [29]. Therefore, it is required to use the MAC protocol in the efficient manner which leads to increase ion the network lifetime further and efficiency in energy effectively. With the help of this proposed method, the sleep time is adjusted dynamically in accordance with the traffic load and wake up time of the neighbour nodes. It is required to do further improvement, for which they generate ACK packets transferred those to receiver as they take short packets for improving the waiting time of the source code. Each node in this proposed method took the conflict-free time slot for itself up to two-hop neighbouring nodes. On the basis of proposed method, it is illustrated that proposed method has better performance in terms of runtime, number or rounds energy consumption, and slot reservation.
Fawaz Lamasery, et.al (2017)presented there are various major fields in which the extensive application of wireless sensor networks has been utilized as there are large amount of sensor nodes are deployed for sensing the physical conditions of environment. The limited resources in the sensor nodes and the additional issues such as energy source, computational ability and communication bandwidth have been faced while designing the reliable smart WSN. The connectivity is guaranteed by this developed network using which lifetime of sensors batteries enhanced. They utilized the technology of virtual multiple input multiple output (V- MIMO) as a solution for the sensor nodes. This method helps in gaining the energy efficiency of smart WSNs. in this paper, they proposed a high energy efficiency smart WSN in which the advantages given by virtual MIMO technique was used [30]. The network transmission is based on the two circumstances such as first, implementation of one rechargeable relay node in the centre of the sensing field using which data packets are received from the source node. After receiving all the packets, they are decoded and forwarded to destination node. Second, in the number of clusters, the sensing field is divided contain a rechargeable relay node in each cluster. This is used to transfer the packets to the destination node in the same cluster or any other cluster. They also studied the effects of Rayleigh flat fading channels as there is enhancement in the re-transmission error of data packets. The advantages of virtual MIMOand one central/rechargeable relay node were used in order to achieve the low energy efficiency for Signal to Noise Ratio (SNR). The range of this ratio is between –20 to 20dB over Rayleigh flat fading channel. The performed experiments concluded that high energy efficiency is achieved by the second scenario as compared to first as there is direct transmission in each cluster due to clustering technique and the central relay nodes.
E. Objectives of the Study
Following are the various research objectives :-
- Implement WEMER energy efficient routing protocol to increase lifetime and reduce routing overhead in wireless sensor networks.
- To improve WEMER energy efficient routing protocol to increase lifetime and reduce routing overhead in wireless sensor networks.
- Implement proposed protocol and compare with existing in terms of various parameters.
F. Outline of the project
In this report first chapter is introduction of wireless sensor networks. 1.1 overview of the topic, 1.2 specific study of the work, 1.3 literature review of research, 1.4 objectives and scope of the study. In chapter 2 theory and concepts are introduced related to research work. In this chapter problem formulation and definition of problem is described. In chapter 3 research methodology is defined, how to solve the problem. Chapter 4 includes the experiments, results of the solved problem. In chapter 5 conclusion and future work is described. At the end of the report references are included.
II. THEORY AND CONCEPT
A. Problem Formulation
The wireless sensor networks are the decentralized type of network in which sensor nodes sense information and pass it to base station. The energy consumption is the major issues of the sensor network due to far deployment and small size of the sensor nodes. The WEMER is the energy efficient structure free data aggregation protocol which works in the structural manner. The WEMER protocol works in the three phases, in the first phase base station send the hello message to each node in the network. The node reverts back to base station with their location and other information. In the second phase, whole network is divided into hierarchal structure based on the network density. In the third phase, the next hop node is selected based on the next node buffer size, residual energy and link strength. In this research work, WEMER protocol will be improved to reduce routing overhead in the network.
- Problem Definition
Following are the various problem definitions which can be resolved in this research work :-
a. The WEMER is the protocol which work in the three phases, due to which energy hole problem can be raised. In this research work, technique will be proposed which resolve the energy hole problem.
b. When the energy hole problem raised, the network throughput is reduced which can increased in this research work .
III. RESEARCH METHODOLOGY
The wireless sensor networks are the self-configuring type of network and size of the sensor nodes are very small. Due to which energy consumption is the major issue of wireless sensor networks. The LEACH is the energy efficient protocol which is used to reduce energy consumption of the network. The various improvements in the LEACH protocol are done in the recent times to reduce energy consumption of the network. In the proposed improvement three level of architecture is proposed in which leader nodes, cluster heads and gateway nodes are involved in the data communication The proposed technique involved two phases.
The cluster head is the first phase of the network. The network is deployed with the finite number of sensor nodes. The base station is deployed at the centre of the network. The base station floods the message in the network. The base station calculates the signal strength and nodes which have signal strength above threshold value will be eligible to be selected as the cluster head. The threshold value will be defined by the equation. In the given equation ???????????????? is the
radius of the cluster, ???????????? is the node distance from the base station, ???????????????????????? is the minimum distance from the base station, ???????????????????????? is the maximum distance from the base station.



Conclusion
A. Conclusion The wireless sensor network is self-configuring type of network which is deployed on far places to sense environmental conditions. Due to far deployment of the network energy consumption is the major issue which reduces network performance. The WEMER is the protocol in which cluster heads and leader nodes are formed in the network. The cluster head send information to leader which forward it to base station. In this research work, the WEMER protocol is improved using the gateway nodes. The cluster head send information to leader node which forward information to leader node. The leader node then forward information to gateway node. The proposed protocol is implemented in MATLAB and simulations shows up to 20 percent improvement in the results. B. Future Work Following are the various future prospective of this research work:- 1) The proposed algorithm can be further improved compared with the other algorithms to increase lifetime of WSN. 2) The proposed algorithm can be further improved to increase security of wireless sensor networks.
References
[1] Bharathidasan, A., & Ponduru, V. A. S. (2002). Sensor networks: An overview. Department of Computer Science, University of California, Davis, CA, 95616. [2] Somani, A. K., Kher, S., Speck, P., & Chen, J. (2006). Distributed dynamic clustering algorithm in uneven distributed wireless sensor network. Technical Reports [DCNL-ON-2006-005], Iowa State University [3] Mamalis, B., Gavalas, D., Konstantopoulos, C., & Pantziou, [4] G. (2009). Clustering in wireless sensor networks. RFID and Sensor Networks: Architectures, Protocols, Security and Integrations, Y. Zhang, LT Yang, J. Chen, eds, 324-353 [5] Bakr, B. A., & Lilien, L. (2011, June). A quantitative comparison of energy consumption and WSN lifetime for LEACH and LEACH-SM. In Distributed Computing Systems Workshops (ICDCSW), 2011 31st International Conference on (pp. 182-191). IEEE [6] Puccinelli, D & Haenggi.M.(2005).Sensor Networks: applications and challenges of ubiquitous sensing.IEEE circuits and systems magazine.5(3).(pp.19-31,2005).IEEE. [7] Dahnil, D. P., Singh, Y. P., & Ho, C. K. (2011, February). Energy-efficient cluster formation in heterogeneous Wireless Sensor Networks: A comparative study. In Advanced Communication Technology (ICACT), 2011 13th International Conference on (pp. 746-751). IEEE. [8] Raj, E. D. (2012). An Efficient Cluster Head Selection Algorithm for Wireless Sensor Networks–Edrleach. IOSR Journal of Computer Engineering (IOSRJCE), 2(2), 39-44. [9] Hansen, E., Neander, J., Nolin, M., & Björkman, M. (2006). Efficient cluster formation for sensor networks. The Online Publication Documentation System (OPUS), Mälardalen [10] University. [11] Xiangning, F & Yulin, S.(2007).Improvement on LEACH Protocol of Wireless Sensor [12] Network.International Conference on Sensor Technologies and Applications.(pp. 260 -264). IEEE [13] Atero.F,Vinagre.J, Morgado.E &M.R. Wilby.(2011).A Low Energy and Adaptive Architecture for Efficient Routing and Robust Mobility Management in Wireless Sensor Networks.(pp. 172 -181)IEEE. [14] Akyildiz, I. F., Su, W., Sankarasubramaniam, Y., & Cayirci, E. (2002). Wireless sensor networks: a survey. Computer networks, 38(4), 393-422. [15] Mendes, L. D., Rodrigues, J. J., Vasilakos, A. V., & Zhou, L. (2011, June). Lifetime analysis of a slotted ALOHA-based wireless sensor network using a cross- layer frame rate adaptation scheme. In Communications (ICC), 2011 IEEE International Conference on (pp. 1-5). IEEE [16] Rai, M., K., D., (2013) “Dynamic Clustering in Wireless Sensor Network using Neural Network”, International Journal for Advance Research in Engineering and Technology Vol. 1, Issue II , ISSN 2320-6802. [17] Nikodem, M., & Wojciechowski, B. (2011, February). Upper Bounds on Network Lifetime for Clustered Wireless Sensor Networks. In New Technologies, Mobility and Security (NTMS), 2011 4th IFIP International Conference on (pp. 1-6). IEEE. [18] Ying Miao (2005).Seminar Wireless Self-Organization Networks Application of sensor network. [19] Pant, S., Chauhan, N., & Kumar, P. (2010). Effective cache based policies in wireless sensor networks: A survey. International Journal of Computer Applications (0975–8887) Volume, 11, 1721. [20] Anand, D., G., Chandrakanth, H., G., and Giriprasad, M., N., D., [21] (2012) “An Energy Efficient Distributed Protocol For Ensuring Coverage And Connectivity (E3c2) Of Wireless Sensor Networks”, International Journal of Ad hoc, Sensor & Ubiquitous Computing (IJASUC) Vol. 3, No.1. [22] Soltan, M., and Hwang, I., (2007) “Modulation- Aware Energy Balancing in Hierarchical Wireless Sensor Networks”, EURASIP Journal on Wireless Communications and Networking, pp. 355359.
Copyright
Copyright © 2024 Yash Verma, Inakshi Garg, Vyshnavi Mamidipelli, Nivas Kumar. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET59774
Publish Date : 2024-04-03
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

