Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Enhancement Network Security Features Through Intrusion Detection Systems
Authors: Ramgopal Kashyap, Abhipsha Sahoo
DOI Link: https://doi.org/10.22214/ijraset.2024.62248
Certificate: View Certificate
Abstract
In pursuit of its objectives, the project \"Enhancement Network Security features through Intrusion Detection Systems\" undertakes a comprehensive exploration of the intricacies surrounding network security, delving into the nuances of intrusion detection methodologies. By dissecting the mechanisms behind both anomaly- and signature-based IDS, the initiative aims not only to implement these systems but also to grasp their underlying principles deeply. Through rigorous experimentation and analysis, the project endeavours to uncover the strengths and limitations of each approach, thereby paving the way for the development of a hybrid system that leverages the best of both worlds. This meticulous approach ensures that the resulting IDS is not only robust but also finely tuned to adapt to the ever-evolving landscape of cyber threats. Furthermore, the integration of machine learning techniques represents a pivotal advancement in the realm of intrusion detection. By harnessing the power of algorithms capable of autonomously learning from data, the IDS transcends static rule-based detection methods, ushering in a new era of adaptive security measures. Through continuous training on vast datasets comprising diverse threat scenarios, the machine learning-enabled IDS hones its ability to discern subtle patterns indicative of malicious activity, thus bolstering its efficacy in safeguarding network assets. Moreover, the implementation of machine learning algorithms fosters a proactive stance against emerging threats, enabling the system to anticipate and mitigate potential breaches before they materialize into full-fledged attacks. This proactive approach not only enhances the overall security posture of organizations but also instils confidence in their ability to stay ahead of the curve in an increasingly hostile digital landscape. The project\'s goal is to provide companies with a stronger protection against cyberattacks by guaranteeing the availability, confidentiality, and integrity of their networked systems.
Introduction
I. INTRODUCTION
Today's technology world relies heavily on information, thus safeguarding computer networks has become essential. To address the mounting problems associated with cyberattacks, the project "Enhancing Network Security through Intrusion Detection Systems" suggests and puts into practice advanced intrusion detection techniques. The effort recognizes the usefulness of intrusion detection systems (IDS) as a defensive tool that is proactive in identifying and preventing potential security breaches in real time. Data availability, confidentiality, and integrity inside computer networks are seriously threatened by the growing complexity and sophistication of cyberattacks. The dynamic nature of contemporary cyber threats frequently renders traditional security solutions inadequate. As a vital tool in the cybersecurity toolbox, intrusion detection systems can monitor network activity and send out timely notifications.
As a vital tool in the cybersecurity toolbox, intrusion detection systems can monitor network activity and promptly warn users to unusual activity. This project's justification is the necessity of upgrading network security protocols to successfully counter a variety of dynamic cyberthreats. Through the improvement of Intrusion Detection System capabilities, businesses may fortify their defences against known and unexpected threats. The research offers insights into the application of cutting-edge IDS approaches to close the knowledge gap between theory and practice. The project's scope is wide, encompassing both anomaly- and signature-based intrusion detection techniques. To acknowledge the significance of adaptive systems in the face of continuously changing cyber threats, it also investigates the integration of machine learning algorithms. The creation of a strong, clever IDS architecture that can offer a flexible protection system is included in the scope. To improve network security with intrusion detection systems (IDS), it is important to recognize that these systems play a critical role in protecting networks from potential threats and illegal access. These systems work by keeping an eye on system or network activity, examining trends, and spotting any unusual activity that might point to a security breech. Organisations frequently use IDS to strengthen network security by quickly identifying and countering a variety of cyberthreats. Improving intrusion detection systems (IDS)-based network security IDS enables a proactive protection against possible intrusions by continually monitoring network traffic and identifying patterns linked to known attacks and unusual activity. By continually monitoring and examining network traffic for indications of malicious behaviour, IDS plays a crucial part in network security. Anomaly-based and signature-based detection techniques are part of conventional IDS methodologies.
A. Signature-Based Intrusion Detection
The detection method known as signature-based depends on an extensive database that has pre-established attack patterns, or signatures. This method works well for detecting known threats since it compares network data to pre-established signatures. But its potency runs out when new or tailored assault techniques that break from known patterns are encountered. To improve the capabilities of signature-based detection systems, professionals in cybersecurity and research have thus set aside a few important topics for further study. First, efforts are made to strengthen the relevance and integrity of signature databases. This entails adding to and updating the database of known attack signatures on a regular basis to include new threats and iterations of already-used attack methods. The signature-based detection technique is predicated on a large database containing pre-existing attack patterns, or signatures. This technique compares network data to pre-established signatures, which makes it effective for identifying known threats. However, its effectiveness wanes when novel or customized attack methods deviate from established patterns. To enhance the capabilities of detection systems based on signatures, experts in the fields of cybersecurity and research have so designated many crucial areas for additional investigation. Initially, efforts are undertaken to improve the integrity and usefulness of signature databases. This means that new threats and variations of previously employed attack techniques must be regularly added to and updated from the database of known attack signatures.
In signature-based detection, handling false positives—where harmless activity is mistakenly reported as malicious—remains a recurring problem. Researchers are concentrating on improving threshold values and detecting algorithms to lessen the frequency of false alarms to address this problem. To differentiate between typical network activity and unusual activity, contextual analysis, anomaly detection, and machine learning techniques are used. This improves threat detection accuracy while reducing false positive alarms.
B. Anomaly-Based Intrusion Detection
A fundamental component of modern cybersecurity tactics is anomaly-based detection, which functions by creating a baseline of normal network activity and sounding an alarm when abnormalities or departures from this norm are discovered. This method is especially valued since it may identify dangers that were previously unidentified and provides a proactive protection mechanism independent of pre-established attack patterns or signatures. But the effectiveness of anomaly-based detection depends on the use of complex algorithms that can correctly discriminate between malicious activity and acceptable changes in network behaviour. The cybersecurity literature has focused a lot of attention on anomaly detection algorithm advancements, with researchers always pushing the envelope to improve the scalability, accuracy, and efficiency of anomaly detection systems. These initiatives cover a wide range of approaches, such as behaviour analysis, machine learning, and statistical modelling. To find anomalies, statistical techniques like distribution modelling and time-series analysis are used to look for departures from typical patterns of activity. Deep learning neural networks and ensemble techniques are two examples of machine learning algorithms that use historical data to build models that can recognize minute variations that point to unusual activity. Additionally, patterns of interactions between network elements are examined using behaviour analysis tools to find abnormal behaviours that could elude typical detection methods. The real-world implementation of anomaly detection algorithms has attracted a lot of interest, demonstrating its efficacy in a variety of contexts, such as Internet of Things (IoT) ecosystems, business networks, and critical infrastructure. An proactive protection against new cyberthreats is provided by anomaly-based detection systems, which continually monitor network traffic and adjust to changing threats. Additionally, combining anomaly detection with auxiliary security measures—like threat intelligence feeds, user behaviour analytics, and signature-based detection—improves overall threat detection capabilities and makes a more thorough security posture possible.
C. achine Learning in Intrusion Detection
To further improve the effectiveness of intrusion detection systems (IDS), researchers are looking at novel techniques for feature selection, data preprocessing, and ensemble learning in addition to experimenting with various machine learning methodologies. By identifying the most pertinent and instructive characteristics from the large amount of network data, feature selection approaches hope to decrease computing overhead and increase detection accuracy. To ensure robustness and dependability in detection results, data preparation techniques including outlier removal, dimensionality reduction, and normalization are essential when preparing input data for machine learning models.
By utilizing the diversity of individual classifiers and reducing the impact of inherent biases or weaknesses in any single model, ensemble learning techniques, which combine multiple base classifiers to form a stronger and more resilient model, offer a promising avenue for improving the overall effectiveness of IDS. Through the utilization of these supplementary tactics together with other machine learning techniques, scientists are attempting to expand the limits of intrusion detection capacities and clear the path for more resilient and flexible cybersecurity solutions.
D. Network Segmentation
Organizations are increasingly using a more dynamic and detailed strategy called micro-segmentation to solve the shortcomings of standard network segmentation. Micro-segmentation functions at a far finer level than traditional segmentation techniques, which generally divide the network into broad zones or subnets. This enables organizations to create isolated security zones around specific workloads, applications, or even down to the level of specific devices or users. Micro-segmentation greatly lowers the attack surface and decreases the lateral flow of threats within the network by implementing strict access rules and policies at this granular level. Furthermore, by utilizing technologies like virtualization and software-defined networking (SDN), micro-segmentation provides increased scalability and agility, allowing businesses to react swiftly to changing business needs and threats. Through the addition of micro-segmentation tactics to conventional network segmentation, enterprises may enhance their defenses against advanced cyber threats while preserving operational flexibility and efficiency.
II. LITERATURE REVIEW
This literature study is predicated on a grasp of the core ideas behind intrusion detection systems (IDS). IDS actively monitor and analyse network traffic for indications of hostile behaviour, which is a crucial part of their function in network security. The detection techniques used in traditional IDS systems are anomaly- and signature-based. A database of recognized attack patterns or signatures is necessary for signature-based detection. This method works well for spotting known risks, but it might not be sufficient against new or tailored assaults. Improved signature databases, faster signature matching, and overcoming false positive issues have been the main topics of research. Establishing a baseline of typical network activity and sending out notifications when deviations happen are key components of anomaly-based detection. Though complex algorithms are needed to differentiate between harmful and lawful variants, this strategy is useful for identifying risks that were not previously identified. Advances in anomaly detection algorithms and their practical applications are highlighted in literature.
The literature acknowledges a number of difficulties in implementing IDS. Among these difficulties include the necessity of updating signature databases on a regular basis, the problem of creating precise baselines for anomaly detection, and the possibility of false positives and negatives. It is imperative that these issues be resolved to create intrusion detection systems that are dependable and efficient. The use of hybrid approaches—which incorporate anomaly- and signature-based detection mechanisms—has grown in popularity. Studies investigate how different approaches might work in concert to maximize strengths and minimize limitations. The goal of hybrid models is to offer a more thorough and flexible defense against various cyberthreats. The review of the literature includes case studies and real-world IDS deployments in various organizational contexts. The efficiency of intrusion detection systems in identifying and reducing cyber threats is demonstrated by these real-world instances. Case studies also highlight the difficulties encountered in implementation and offer solutions. An examination of upcoming developments and new technology in intrusion detection is included in the review's conclusion. This covers the possible effects of AI, how blockchain can enhance IDS security, and how integrating threat intelligence feeds can strengthen preventative defense systems.
III. IMPLEMENTATION STUDY
Conventional security methods, including firewalls and antivirus software, are frequently used in the current network security system to ward against recognized threats. Although these solutions offer a basic degree of protection, they might not be sufficient to counter the complex and ever-changing nature of contemporary cyber threats. To improve the capabilities of the current security architecture, intrusion detection systems (IDS) are frequently incorporated.
A. Firewalls and Antivirus Software
By enforcing pre-established security rules, traditional firewalls serve as a barrier between a private internal network and external networks, permitting or prohibiting traffic. The purpose of antivirus software is to find and eliminate known viruses. Although these solutions work well against typical threats, they might not be as successful in identifying and thwarting unique or tailored assaults.
B. Intrusion Detection Systems (IDS):
The notable advancement is the incorporation of IDS into the current system. To identify known threats, signature-based intrusion detection systems use a database of established patterns or signatures. Anomaly-based intrusion detection systems create a baseline of typical network activity and sound an alarm when deviations happen. However, issues like false positives and the requirement for regular signature database changes might arise with these systems.
C. Network Segmentation
In the present framework, network segmentation is the process of breaking a network into smaller, more isolated portions in order to prevent attacker lateral movement and contain any breaches. Although somewhat successful, it could not be enough to stop sophisticated attacks that take advantage of weaknesses in several areas.
D. Security Policies and User Training
Employee security is encouraged by the current system, which frequently includes user training and security standards. Even with their importance, human mistake and constantly changing attack methods can still be dangerous, which is why automated and intelligent security solutions are necessary.
E. Incident Response Plans
As a way to quickly handle security breaches, most organizations have incident response procedures in place. The pace and complexity of sophisticated cyberattacks, however, may be beyond the capabilities of these systems, which frequently rely on human interaction.
F. Security Information and Event Management (SIEM)
Some organizations use security intelligence and event management to collect and analyze data from various network devices. While SIEM provides visibility into potential security threats, it may lack the real-time capabilities provided by traditional IDS solutions.
G. Vendor-Specific Security Solutions
Depending on the organization, specific or vendor-specific security solutions can be integrated into existing systems. These solutions often focus on specific security functions, and their effectiveness depends on the balance between their functionality and the ability to deal with perceived threats.
IV. PROPOSED METHODOLOGY
The goal of the proposed system is to adopt sophisticated Intrusion Detection Systems (IDS) to solve the shortcomings of the current security architecture and therefore dramatically improve network security. The following are the main elements and attributes of the suggested system: The suggested system combines intrusion detection methods based on anomaly and signature detection to offer a complete defense against a variety of cyberthreats. Signature-oriented. While anomaly-based detection creates a baseline of typical behavior and finds variations suggestive of possible intrusions, detection aids in the identification of established attack patterns.
A. Machine learning Integration
It allows the IDS architecture to adapt to new and emerging threats, the proposed system incorporates machine learning techniques. Thanks to machine learning, the system may eventually learn from novel patterns and behaviors, enhancing its ability to recognize hazards that weren't previously noticed. This adaptive approach reduces false positives while improving overall detection accuracy.
B. Real-time Monitoring and Alerts
Real-time monitoring of system activity and network traffic is ensured by the suggested IDS. Alerts are sent out immediately in the event of any suspicious activity or possible security breach, facilitating prompt action and mitigation strategies. In order to reduce the effect of security events and stop illegal access, real-time warnings are essential.
C. Behavioural Analysis and Profiling
The system has the ability to profile and comprehend typical network and user activity thanks to its behavioral analysis features. This lessens false positives by aiding in the distinction between potentially harmful activity and valid changes. An intrusion detection system that is more precise and context-aware benefits from behavioral profiling.
D. Continuous Updates and Threat Intelligence Integration
The significance of regular updates to threat intelligence feeds and signature databases is emphasized by the suggested system. By doing this, you can be confident that the IDS is up to date and ready to detect even the newest known threats. Integrating with threat intelligence sources makes use of outside knowledge about new cyberthreats to improve the system's proactive protection.
E. User-Friendly Dashboard and Reporting
Within the proposed system, an intuitive dashboard gives managers a clear visual representation of network activity, alarms, and possible risks. Comprehensive analysis of security events is made possible by detailed reporting features, which support well-informed decision-making and ongoing security posture development.
F. Automated Response Mechanisms:
Regarding the suggested system's reaction to security issues, automation is essential. Isolating compromised systems, obstructing hostile communications, and starting predetermined security routines are a few examples of automated reactions. This lessens the effect of security breaches while also speeding up reaction times.
V. MODULES & ALGORITHM
A. Signature- Based Detection
Description: Signature-based detection is based on known harmful activity signatures or established patterns. These signs stand for certain traits or patterns connected to recognized dangers. Algorithm Justification The system correlates patterns found in network traffic analysis with the signature database. An alert is sent out if a match is activated, signifying the existence of a recognized danger.
B. Anomaly- Based Detection
The goal of anomaly-based detection is to spot departures from the usual. With this method, a baseline of what is deemed normal is established, and when actions considerably depart from this baseline, an alarm is raised. Algorithm Justification The typical behavior baseline is established through the use of statistical models, rule-based systems, or machine learning techniques. When a network actions depart from this standard, a warning is sent.
C. Machine Learning Algorithms
Description: Machine learning techniques improve intrusion detection systems (IDS) by facilitating intelligent and adaptive threat identification. =These algorithms constantly enhance their capacity to recognize novel patterns by learning from past data.
D. Algorithm Explanation: Common machine learning algorithms include
- Neural Networks: Learn intricate patterns by imitating the structure of the human brain.
- Decision Trees: Hierarchical structures that make judgments depending on input features Data points are grouped using clustering algorithms, which are helpful in detecting anomalies.
E. Statistical Analysis
- Description: Network data is analyzed statistically to find abnormalities or trends that point to malicious behavior. The mean, median, standard deviation, and other statistical metrics are examples of these techniques.
- Algorithm Explanation: The system can identify departures from typical behavior by setting statistical criteria. unusual designs that go beyond what is Alerts are triggered by thresholds.
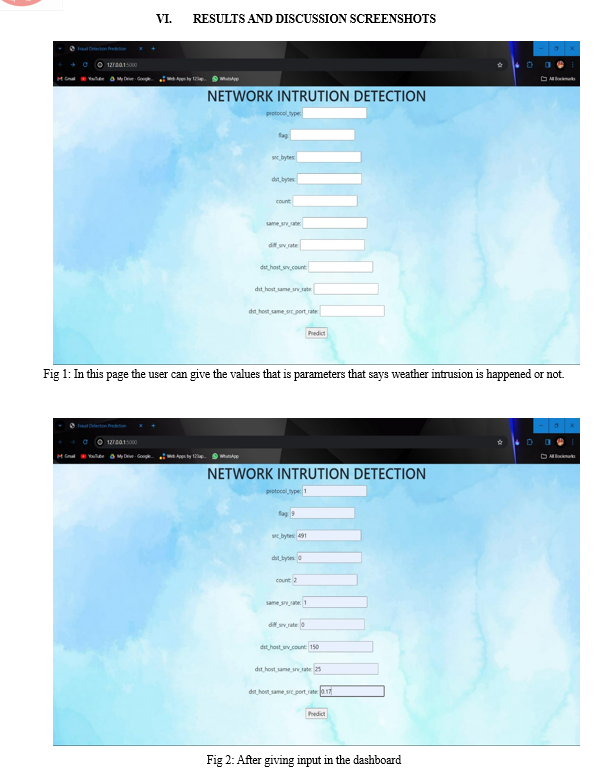
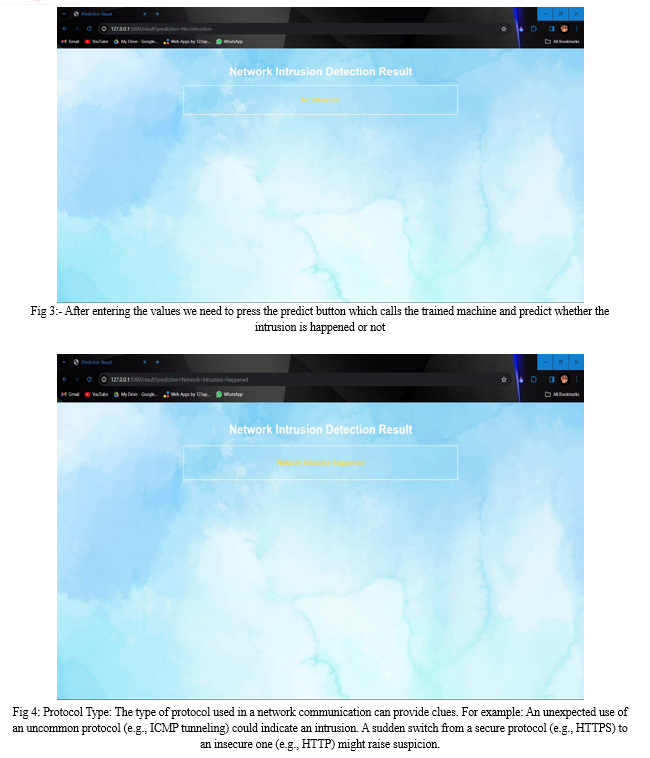
Conclusion
The research effort effectively tackles the vital requirement for cutting-edge security measures against growing cyberthreats. It offers a thorough analysis of intrusion detection techniques, making a significant contribution to the cybersecurity community. Through the application of anomaly-based, machine learning, and signature-based methodologies, the project has created a proactive, flexible, and strong network security defensive system. With this initiative, networks\' ability to withstand changing cyberthreats will be strengthened significantly. In order to accomplish the project, cutting-edge intrusion detection technology, processes, and best practices have to be integrated. This project represents a thorough and proactive strategy to protect networks from various cyberthreats. Whilst the present system provides a strong basis, the project\'s flexible and adaptable architecture allows it to grow with the constantly evolving field of network security. Maintaining system efficacy in the face of changing cybersecurity issues will need ongoing cooperation, keeping an eye on new threats, and system changes. A. Future Enhancements Although there are many opportunities for future improvements and extensions, this project establishes the groundwork for strong network security. Here are a few possible directions this project might go in the future: Form partnerships with external threat intelligence groups in order to exchange knowledge and research results and to work together to counteract cyber threats. This might make it easier for the project to keep ahead of new dangers. These future scopes are in line with the rapidly changing cybersecurity and technological landscape, guaranteeing the intrusion detection system\'s continued efficacy and adaptability in the face of new threats. The project\'s ongoing success will depend on regular updates, cooperation with the cybersecurity community, and a dedication to being up to speed on the most recent threats.
References
[1] Stallings, W. (2017). \"Network Security Essentials: Applications and Standards.\" Pearson. [2]Northcutt, S., Novak, J., & Winters, S. (2014). \"Network Intrusion Detection.\" New Riders. Research Papers: [2] Dhanalakshmi, R., & Sharmila, T. (2018). \"An Overview of Intrusion Detection System.\" International Journal of Computer Applications, 181(45), 1-5 [3] Sperotto, A., Schaffrath, G., Sadre, R., & Pras, A. (2010). \"Overview of IP Flow-Based Intrusion Detection.\" IEEE Communications Surveys & Tutorials, 12(3), 343-356. [4] Forrest, S., Hofmeyr, S. A., Somayaji, A., & Longstaff, T. A. (1996). \"A Sense of Self for Unix Processes.\" IEEE Transactions on Software Engineering, 22(11), 718-731. [5] Mukkamala, S., Sung, A. H., & Abraham, A. (2005). \"Intrusion Detection Using an Ensemble of Intelligent Paradigms.\" Journal of Network and Computer Applications, 28(2-3), 167-182. Online Resources: [1] CERT Coordination Center. (2019). \"Intrusion Detection Systems (IDS).\" Retrieved from https://www.cert.org/ [2] Cisco. (2021). \"Intrusion Prevention System (IPS).\" Retrieved from https://www.cisco.com/
Copyright
Copyright © 2024 Ramgopal Kashyap, Abhipsha Sahoo. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET62248
Publish Date : 2024-05-17
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

