Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Face Detection under Hostile Circumstances using Innovative Robust Methods
Authors: Lakshmi Prasad, K Sai Teja , S Hari Haran, B Ram Nayak
DOI Link: https://doi.org/10.22214/ijraset.2024.61753
Certificate: View Certificate
Abstract
An attendance system is crucial for monitoring student presence in classes, with various methods available such as biometric, RFID card, face recognition, and traditional paper-based systems. Among these, face recognition stands out for its security and efficiency. This research focuses on enhancing the face recognition attendance system\'s accuracy by minimizing false positives through a confidence threshold based on the Euclidean distance metric. The Local Binary Pattern Histogram (LBPH) algorithm outperforms other distance-based methods like Eigenfaces and Fisherfaces due to its robustness against grayscale transformations. Face detection relies on Haar cascades for their robustness, while LBPH is employed for recognition. Leveraging LBPH for recognition tasks significantly improves the system’s ability to discern subtle variations in facial features, thereby enhancing overall accuracy. Moreover, the effectiveness of the system heavily relies on robust face detection techniques. Haar cascades are employed for this purpose, leveraging their proven reliability in detecting faces across diverse environmental conditions and camera angles. The system achieves a recognition rate of 77% for students and a false- positive rate of 28%. Notably, it effectively recognizes students even with variations like wearing glasses or facial hair. Face recognition for unknown individuals is approximately 60%, with false-positive rates of 14% and 30% with and without the threshold, respectively.
Introduction
I. INTRODUCTION
Automated attendance systems are a major technical achievement, surpassing labor-intensive approaches. Due to its accuracy, efficiency, and security, our facial recognition-based attendance system represents a quantum leap in this field.
We use cutting-edge Haar cascade and LBPH algorithms for face detection and identification. This combination is sturdy and reliable, with a low false- positive rate. Our threshold method and picture storage allow our system to accurately identify known people and catalog unidentified faces for better security.
In addition to attendance marking, our technology will revolutionize security. It collects photos of unidentified people to deter unlawful access. This multimodal strategy simplifies administrative operations and protects organizations against breaches. The switch from paper-based to automated systems is crucial. Automation reduces mistakes and administrative hassles by automating tedious tasks. Our solution excels at precise attendance monitoring in big classes with complicated and time limitations. Finally, our facial recognition-based attendance system changes how institutions handle attendance and security. Technical innovation and practical application enable attendance management where accuracy, efficiency, and security are effortlessly integrated.
II. LITERATURE SURVEY
Attendance management systems automate attendance monitoring in several fields. Due to its non- intrusiveness and precision, face recognition technology is popular [1][11]. Joseph and Zacharia (2013) offered a "Automatic Attendance Management System Using Face Recognition," whereas Samet and Tanriverdi (2017) proposed a "Face Recognition- Based Mobile Automatic Classroom Attendance Management System."
Real-time attendance tracking and access management using RFID technologies are also popular [2]. An "RFID-based Attendance System with Automatic Door Unit," by Ononiwu and Okorafor (2012), is cost- effective and scalable.
Attendance management systems use fingerprint or palm vein recognition [3]. Shoewu and Idowu (2012) created a "Attendance Management System using Biometrics," whereas Khatun et al. (2015) offered a "Iris Recognition-Based Attendance Management System," which identifies people accurately and securely.
Attendance management systems use iris recognition technology, which is reliable and secure [4][12]. Kadry and Smaili (2010) developed a "Wireless Attendance Management System based on Iris Recognition," which integrates wireless communication technology.
Local Binary Patterns (LBP) exhibit computational efficiency and robustness to illumination and facial expressions in face recognition [5][6][7]. Ahonen, Hadid, and Pietikainen (2004) introduced "Face Recognition with Local Binary Patterns," which demonstrated LBP's efficacy in facial feature extraction and description. Y.B. Sudhir Sastry et al.,[14] conducted studies on the ballistic impact of composite panels, which was published in Theoretical and Applied Fracture Mechanics in 2014. The paper delves into the behavior of composite panels when subjected to ballistic impact.
G. Kalyani, et al.,[15] worked on detecting and classifying diabetic retinopathy using capsule networks, published in Complex & Intelligent Systems in 2023. Their work focuses on using advanced neural network architectures for medical image analysis. Spandana, K et al.,[ [16] presented an Internet of Things (IoT)-based smart water quality monitoring system, published in the International Journal of Engineering & Technology in 2018. The system aims to monitor water quality parameters in real-time using IoT technologies. Telagam, N et al.,[ [17] developed a smart sensor network-based high-quality air pollution monitoring system using LabVIEW, published in the International Journal of Online and Biomedical Engineering (iJOE) in 2017. The system focuses on monitoring and analyzing air pollution levels using sensor networks. L. Lakshmi et al.,[ 18] proposed a smart phishing detection system in web pages using supervised deep learning classification and the optimization technique ADAM, published in Wireless Personal Communications in 2021. The system aims to detect phishing attempts in web pages using deep learning algorithms.
Malliga Subramanian et al.,19] optimized hyperparameters for transfer learning of VGG16 for disease identification in corn leaves, published in Big Data in 2022. The work focuses on using deep learning and transfer learning for plant disease identification.
R. R. Vallabhuni et al.,[20]developed a smart cart shopping system with an RFID interface for human assistance, presented at the 2020 3rd International Conference on Intelligent Sustainable Systems (ICISS). The system aims to improve shopping experiences using smart cart technology. Rao et al., [21] discussed the use of ensemble deep learning techniques for forecasting crypto currency trends, focusing on time-series analysis.
Prasad et al. ,[22] explored advancements in machine learning algorithms for improving hand- written digit recognition. Baskar et al.,[23] presented a deep learning approach for accurately predicting and diagnosing Alzheimer's disease. Sampath et al., [24] introduced an ensemble nonlinear machine learning model for predicting chronic kidney diseases. Kumar et al. [25] proposed a deep neural learning-based approach for early prediction of cancer. Joshi et al. [26] presented an accurate prediction model for coronary heart disease using ensemble algorithms.
Sudhakar et al [27] discusses the use of CNN-based deep learning networks for predicting brain tumor images from MR images.D, B., K, C et al. [28] presented machine learning techniques for predicting the risk of chronic kidney disease.
Narasimha Prasad L V et al [29] introduced a novel decision tree approach for predicting precipitation, leveraging entropy in the SLIQ algorithm. This work likely focuses on improving the accuracy and efficiency of precipitation prediction models, which is crucial for various applications such as agriculture, water resource management, and weather forecasting. Madhuri Avula et al.[30] discussed a method for detecting bone cancer from MRI scan imagery, specifically using mean pixel intensity. The research likely involves developing a computer-aided diagnosis (CAD) system to assist radiologists in detecting bone cancer earlier and more accurately, potentially leading to better patient outcomes.
Lakshmi Prasad et al.,[31] introduced a novel method for generating t-way test cases using an improved particle swarm optimization strategy. This work is valuable in software testing, where generating effective test cases is crucial for ensuring software quality and reliability. M. Lakshmiprasad et al.,[32][33][34]presented an adaptive framework for detecting accident black spots using IoT and machine learning techniques. The research likely aims to improve road safety by identifying high-risk areas for accidents and implementing preventive measures and discussed an IoT-based agriculture monitoring system for improving agricultural practices. The system likely involves sensors and data analytics to monitor and optimize various aspects of farming, such as irrigation and fertilization, leading to increased crop yield and efficiency. They presented a reactive approach for predicting accident black spots using IoT and machine knowledge. The research may focus on using real-time data and machine learning algorithms to predict and prevent accidents, enhancing road safety.
M. Lakshmi Prasad and Dr. JKR Sastry [35] to [41] provided a comprehensive survey of combinatorial testing techniques, discussing their applications and advantages in software testing. They also presented a graph-based strategy, PSO, Neural networks strategies for generating test cases for testing embedded systems using combinatorial approaches, likely focusing on improving test coverage and efficiency and also explored the testing of embedded systems using test cases generated through combinatorial methods, focusing on improving test coverage and effectiveness.
III. METHODOLOGY
A. Proposed Work
The proposed automated attendance management system integrates Haar cascade for face detection and the LBPH algorithm for face recognition. It includes a Graphical User Interface (GUI) developed using the Python module Tkinter for user interaction. Functionalities encompass capturing student images and details for database storage, training images from both the database and live camera feed, and real-time tracking of individuals entering the classroom. As students enter, the system detects faces from the camera feed, preprocesses images, and tracks attendance automatically. With Tkinter providing a user-friendly interface, the system ensures efficient and accurate attendance management, optimizing classroom management for educational institutions.
The sequence diagram starts with the system obtaining input data from hostile surroundings, such pictures or video feeds. Preprocessing modules are triggered to improve image quality and minimise noise after obtaining this data. The appropriate face characteristics are then extracted from the preprocessed data by feature extraction components. The recognition system then receives these features and uses stored templates of well-known faces to compare them. The recognition procedure is then finished when the system outputs the identified face or informs if no match is detected.
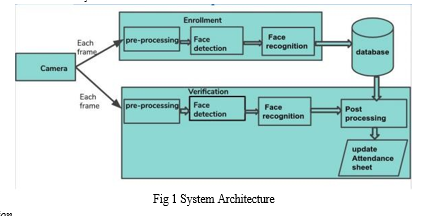
B. System Architecture
The automated attendance management system consists of face detection using Haar cascade, face recognition via the LBPH algorithm, and a Tkinter- based user interface. Detected faces are recognized against pre-trained images in the database, updating attendance records. The GUI allows user interaction, including image capture, database storage, and real- time tracking. Modules for image preprocessing and database management ensure smooth operation. This modular design ensures efficient and accurate attendance tracking with a user-friendly interface.
C. Dataset Collection
For our automated attendance management system, we constructed a bespoke dataset due to the absence of suitable datasets online. Our dataset comprises 1,080 images, with 60 images per each of the 18 individuals involved in the project. These images were captured under varied conditions to enhance robustness in face recognition. Additionally, we included 10 individuals not part of the training set to test the system's ability to recognize unknown faces. Images were captured uniformly using a high-resolution camera, ensuring consistency across the dataset. This exhaustive dataset facilitated comprehensive training of the face recognition algorithm and rigorous testing, including live real-time video attendance tracking, to evaluate the system's performance in diverse real-world scenarios.
1) Image Capturing
By acquiring 50 diverse images of the individual, encompassing various expressions and environmental conditions, the system ensures adaptability and resilience. This extensive dataset enables the algorithm to effectively discern facial features amidst challenging scenarios, such as low lighting, obscured visibility, or dynamic facial expressions. Through meticulous image acquisition, the system fosters heightened accuracy and reliability in identifying individuals, even amidst the most adverse conditions.
D. Image Processing
Our automated attendance management system extracts and preprocesses facial photos before sending them to the face recognition module. Initial face extraction uses the Haar cascade technique to localize faces in collected pictures. After extraction, the faces are cropped and isolated from the backdrop to keep just important facial parts for processing. Faces are scaled to a uniform size after extraction. Uniformity improves feature extraction and comparison during recognition and reduces computing complexity. Normalization and histogram equalization may improve picture quality and contrast. Normalization uniformly scales pixel intensities, whereas histogram equalization enhances contrast by redistributing values.
E. Training & Testing
Training and testing are crucial to face recognition algorithm development and evaluation in our automated attendance management system. The system uses 60 photos for each of the 18 people during training. The program learns from these photographs to extract face attributes and encode them into feature vectors for IDs. Supervised learning improves the algorithm's face classification and recognition. Different pictures are used to assess the system's performance. This involves testing its ability to recognize unfamiliar and known people from the training dataset. Live video feeds and other testing scenarios verify the system's reliability and efficacy. The facial recognition system is constantly refined and improved, improving attendance tracking reliability.
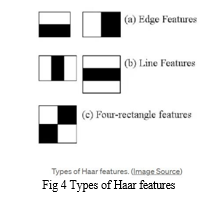
F. Haar Cascade
Haar cascade detects objects in photos regardless of size or position. This simple algorithm runs in real time. We can train a haar-cascade detector to identify automobiles, motorcycles, buildings, fruits, etc.
Haar cascade classifies. The system identifies positive data points as part of the identified item and negative data points as not containing it. Haar cascades function quickly and in real time. Haar cascade is less precise than current object detection.

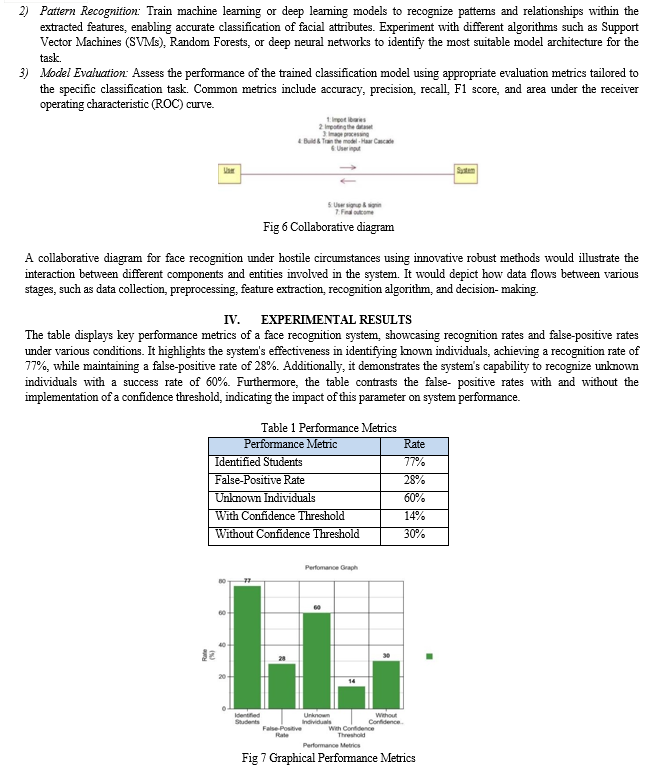

V. FUTURE SCOPE
The dataset should be expanded to increase recognition accuracy. Security might be improved by improving Haar cascade classifiers and adding intruder alerts. Further study is needed to improve the system's accuracy, dependability, and security in real- world applications.
There are a lot of interesting prospects for innovation and progress in the field of face recognition in hazardous environments. Research may focus on creating innovative algorithms that can manage progressively more complicated situations, such as faces that are partially or completely hidden and varied ambient circumstances. Incorporating state-of-the-art technology like infrared photography and augmented reality might improve recognition accuracy in difficult circumstances. Moreover, investigating the combination of several biometric modalities—such as voice, iris, and facial recognition—holds potential for enhancing the resilience and robustness of systems. To propel these developments and promote the creation of practical and morally good face recognition solutions in hostile environments, cooperation between government, business, and academia will be essential.
Conclusion
In conclusion, the utilization of LBPH for face recognition in our system has proven effective in accurately identifying students, even amidst unintentional changes such as wearing glasses or growing a beard. However, a notable limitation is the relatively small dataset, which could potentially impact the accuracy of recognition results. To address this, future efforts could focus on expanding and enhancing the dataset to improve the system\'s overall performance and reliability. Furthermore, enhancing the system\'s capabilities in identifying individuals entering the class. Additionally, incorporating a system alert mechanism, comprising both voice and visual alerts, in the event of an intruder detection, would further bolster the security measures of the attendance management system. Synthesizing fresh training examples for Haar cascade classifiers may improve their identification rate of unfamiliar people, allowing the algorithm to identify class members. Adding a system alert mechanism with audio and visual notifications for intruder detection will better secure the attendance management system.
References
[1] Jomon Joseph1, K. P. Zacharia, “Automatic Attendance Management System Using Face Recognition”, International Journal of Science and Research (IJSR), 2013. [2] Ononiwu G. Chiagozie, Okorafor G. Nwaji, “Radio-frequency identification (RFID)based Attendance System with Automatic Door Unit”, Academic Research International(2012). [3] O. Shoewu, PhD, O.A. Idowu, B.Sc., “Development of Attendance Management System using Biometrics.”, The Pacific Journal of Science and Technology(2012). [4] A. Khatun, A. K. M. F. Haque, S. Ahmed and M. M. Rahman, ”Design and implementation of iris recognition based attendance management system”, 2015 International Conference on Electrical Engineering and Information Communication Technology (ICEEICT), Dhaka, 2015, pp. 1-6. [5] Ahonen, T.; Hadid, A.; Pietikainen, M. Face Recognition with Local ¨ Binary Patterns. InProceedings of theAdvances in Visual Computing; Springer Science and Business Media LLC: Berlin, Germany, 2004; Volume3021, pp. 469–481. [6] A. Ozdil and M. M. ¨ Ozbilen, ”A survey on comparison of face¨ recognition algorithms,” 2014 IEEE 8th International Conference on Application of Information and Communication Technologies (AICT), Astana, 2014, pp. 1-3. [7] Ahonen, Timo, Abdenour Hadid, and Matti Pietikainen. “Face description with local binary patterns: Application to face recognition.” IEEE transactions on pattern analysis and machine intelligence 28.12 (2006): 2037–2041. [8] P. Viola and M. Jones, ”Rapid object detection using a boosted cascade of simple features,” Proceedings of the 2001 IEEE Computer Society Conference on Computer Vision and Pattern Recognition. CVPR 2001, Kauai, HI, USA, 2001, pp. I-I. [9] Will Berger, Deep Learning Haar Cascade Explained, WILL BERGER,< http://www.willberger.org/cascade-haar-explained>. [10] Kelvin Salton do Prado, Face Recognition: Understanding LBPH Algorithm, towards data science,. [11] R. Samet and M. Tanriverdi, ”Face Recognition-Based Mobile Automatic Classroom Attendance Management System,” 2017 International Conference on Cyberworlds (CW), Chester, 2017, pp. 253-256. [12] Kadry, Seifedine Smaili, Mohamad. (2010). ”Wireless attendance management system based on iris recognition”. Scientific Research and Essays. 5. 1428-1435. [13] A. Ahmed, J. Guo, F. Ali, F. Deeba, and A. Ahmed, ”LBPH based improved face recognition at low resolution,” in 2018 International Conference on Artificial Intelligence and Big Data (ICAIBD), 2018: IEEE, pp. 144-147. [14] Y.B. Sudhir Sastry, Pattabhi R. Budarapu, Y. Krishna, S. Devaraj, “Studies on ballistic impact of the composite panels”, Theoretical and Applied Fracture Mechanics, Volume 72, 2014, Pages 2-12, https://doi.org/10.1016/j.tafmec.2014.07.010. [15] G. Kalyani, B. Janakiramaiah, A. Karuna, and L. V. N. Prasad, \"Diabetic retinopathy detection and classification using capsule networks,\" Complex & Intelligent Systems, vol. 9, no. 3, pp. 2651- 2664, 2023/06/01 2023, doi: 10.1007/s40747-021-00318-9. [16] Spandana, K., & R. Seshagiri Rao, V. (2018). “Internet of Things (IoT) Based Smart Water Quality Monitoring System”. International Journal of Engineering & Technology, 7(3.6), 259-262. [17] Telagam, N., Kandasamy, N., Prasad G, N., & Nanjundan, M. (2017). “Smart Sensor Network Based High Quality Air Pollution Monitoring System Using Labview”. International Journal of Online and Biomedical Engineering (iJOE), 13(08), pp. 79–87. https://doi.org/10.3991/ijoe.v13i08.7161 [18] L. Lakshmi, M. P. Reddy, C. Santhaiah, and U. J. Reddy, \"Smart Phishing Detection in Web Pages using Supervised Deep Learning Classification and Optimization Technique ADAM,\" Wireless Personal Communications, vol. 118, no. 4, pp. 3549-3564, 2021/06/01 2021, doi: 10.1007/s11277-021-08196-7. [19] Malliga Subramanian, Narasimha Prasad L.V., Janakiramaiah B., Mohan Babu A., and Sathishkumar VE, \"Hyperparameter Optimization for Transfer Learning of VGG16 for Disease Identification in Corn Leaves Using Bayesian Optimization,\" Big Data, vol. 10, no. 3, pp. 215-229, 2022, doi: 10.1089/big.2021.0218. [20] R. R. Vallabhuni, S. Lakshmanachari, G. Avanthi and V. Vijay, \"Smart Cart Shopping System with an RFID Interface for Human Assistance,\" 2020 3rd International Conference on Intelligent Sustainable Systems (ICISS), Thoothukudi, India, 2020, pp. 165-169, doi: 10.1109/ICISS49785.2020.9316102. [21] Rao, K.R., Prasad, M.L., Kumar, G.R., ...Hussain, M.M., Reddy, P.C.S.“Time-Series Cryptocurrency Forecasting Using Ensemble Deep Learning”, Proceedings of the International Conference on Circuit Power and Computing Technologies, ICCPCT 2023, 2023, pp. 1446–1451 [22] Prasad, M.L., Srinivasulu, C., Yashaswini, G., Rakshitha, K., “Decoding Digits: Advancements in hand written Digit Recognition with Machine Learning Algorithms”, International Conference on Recent Advances in Science and Engineering Technology, ICRASET 2023, 2023. [23] Baskar, S., Nandhini, I., Prasad, M.L., ...Sharma, N., Reddy, P.C.S. “An Accurate Prediction and Diagnosis of Alzheimer\'s Disease using Deep Learning”, Proceedings of NKCon 2023 - 2nd IEEE North Karnataka Subsection Flagship International Conference, 2023. [24] Sampath, S., Parameswari, R., Prasad, M.L., ...Hussain, M.M., “Ensemble Nonlinear Machine Learning Model for Chronic Kidney Diseases Prediction”, 2023 IEEE 3rd Mysore Sub Section International Conference, MysuruCon 2023, 2023 [25] G. R. Kumar, M. L. Prasad, G. Yedukondalu, S. T. Bhanu, S. B. Latha and P. C. S. Reddy, \"An Early Cancer Prediction Based On Deep Neural Learning,\" 2023 International Conference on Research Methodologies in Knowledge Management, Artificial Intelligence and Telecommunication Engineering (RMKMATE), Chennai, India, 2023, pp. 1-7 [26] K. P. Joshi, M. L. Prasad, R. Natchadalingam, P. C. S. Reddy, S. Mukherjee and G. C. Babu, \"An Accurate Prediction of Coronary Heart Disease Using Ensemble Algorithms,\" 2023 International Conference on Ambient Intelligence, Knowledge Informatics and Industrial Electronics (AIKIIE), Ballari, India, 2023, pp. 1-5 [27] Sudhakar, B., Sikrant, P. A., Prasad, M. L., Latha, S. B., Kumar, G. R., Sarika, S., & Shaker Reddy, P. C. (2024). Brain Tumor Image Prediction from MR Images Using CNN Based Deep Learning Networks. Journal of Information Technology Management, 16(1), 44-60. doi: 10.22059/jitm.2024.96374 [28] D, B., K, C., Prasad, M. L., N, P., Kiran, A., N, P., & Shaker Reddy, P. C. (2024). Chronic Kidney Disease Risk Prediction Using Machine Learning Techniques. Journal of Information Technology Management, 16(1), 118-134. doi: 10.22059/jitm.2024.96378 [29] Narasimha Prasad L V, Prudhvi Kumar Reddy K, Naidu M M, \"A Novel Decision Tree Approach for the Prediction of Precipitation Using Entropy in SLIQ,\" IEEE International Conference on Modelling and Simulation, Apr. 10-12, 2013, Cambridge, UK, pp. 209-217. [30] MadhuriAvula, Narasimha Prasad L V, Murali Prasad Raja, “Bone Cancer Detection from MRI Scan Imagery Using Mean Pixel Intensity,” IEEE Asia International Conference on Mathematical Modelling and Computer Simulation, 2014. [31] M. Lakshmi Prasad ; J.Kodanda Rama Sastry ; Basetty Mallikarjuna, “Development of a Programmed Generation of t-way Test cases Using an Improved Particle Swarm Optimization Strategy”,2022 2nd International Conference on Advance Computing and Innovative Technologies in Engineering (ICACITE) , 28-29 April 2022 . [32] Dr. M. Lakshmiprasad, Dr. G. V. Shrichandran, A. Chandrashekhar, Dr. Revathi R., Venkata Harshavardhan Reddy Dornadula, Maddukuri Supriya. (2021). “Adaptive framework for detecting Accident black spots using IoT and Machine Learning”. Design Engineering, 5422 - 5428. [33] Dr. M. Lakshmiprasad, Dr. Ashok Kumar Koshariya, Sumedh V. Dhole, Prashant Ashok Chougule, Vikas P. Kaduskar, Nayani Sateesh. (2021). “An Internet of Things based Agriculture Monitoring System”. Design Engineering, 3637- 3642.. [34] Lakshmiprasad, M.; Sreenivasulu, Ch.; Bojja, Polaiah; Kodanda Rama Sastry, J.; Alekhay, V., “A Reactive Approach for Predicting Accident Black Spots Using IOT and Machine Knowledge.”, International Journal of Early Childhood Special Education . 2022, Vol. 14 Issue 8, p235-244. 10p. M. Lakshmi Prasad and Dr.JKR Sastry, “A Comprehensive Survey on Combinatorial Testing,” PONTE Journal, Vol.73 Issue No.2, pp.no.187-261, Oct 2017-1 (Science Citation Index, Thomson Reuters). [35] M. Lakshmi Prasad and Dr. JKR Sastry, “A Graph Based Strategy (GBS) For Generating Test Cases Meant for Testing Embedded Systems Using Combinatorial Approaches,” Journal of Advanced Research in Dynamical and Control Systems, Vol. 10, 01- Special Issue, pp.no.314-324, Jan 2018 (Scopus). [36] M. Lakshmi Prasad and Dr. JKR Sastry, “A Neural Network Based Strategy (NNBS) For Automated Construction of Test Cases for Testing an Embedded System Using Combinatorial Techniques,” International Journal of Engineering Technology Vol. No.7 Issue No.1, pp.no.74-81, Jan 2018 (Scopus). [37] M. Lakshmi Prasad and Dr. JKR Sastry, “Building Test Cases by Particle Swarm Optimization (PSO) For Multi Output Domain Embedded Systems Using Combinatorial Techniques,” Journal of Advanced Research in Dynamical and Control Systems, Vol. 06- Special Issue, pp.no.1221-1229, May 2018 (Scopus). [38] M. Lakshmi Prasad and Dr. JKR Sastry, “Testing Embedded Systems using test cases generated through Combinatorial Methods,” International Journal of Engineering Technology Vol. No.7 Issue No.1, pp.no.146-158, March 2018 (Scopus). [39] Dr.M. Lakshmi Prasad, Dr.A.Rajasekhar Reddy and Dr. JKR Sastry, \"GAPSO: Optimal Test Set Generator for Pair wise Testing\", International Journal of Engineering and Advanced Technology, Vol-8 Issue-6, Aug-19. [40] Dr. JKR Sastry and M. Lakshmi Prasad, “Testing Embedded System through Optimal Mining Technique (OMT) Based on Multi- Input Domain,” International Journal of Electrical and Computer Engineering Vol. No.9 Issue No.3, pp.no.2141-2150, 2019 (Scopus). [41] M. Lakshmi Prasad and Dr. JKR Sastry, “Generation of Test Cases Using Combinatorial Methods Based Multi-Output Domain of an Embedded System through the Process of Optimal Selection,” International Journal of Pure and Applied Mathematics, Volume 118 No. 20, pp.no.181-189, March 2018 (Scopus)
Copyright
Copyright © 2024 Lakshmi Prasad, K Sai Teja , S Hari Haran, B Ram Nayak. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET61753
Publish Date : 2024-05-07
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

