Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Face Recognition and Identification System for Crime Detection Using Python Programming Language
Authors: Okardi, Biobele , Udokike Daniel Ikegbunam
DOI Link: https://doi.org/10.22214/ijraset.2024.60813
Certificate: View Certificate
Abstract
Throughout the years, finding criminals has posed a challenging endeavor. In the past, the method relied on leads derived from evidence discovered at the crime scene. Genetic evidence is comparatively straightforward to trace, yet wrongdoers have grown increasingly proficient at obscuring their trail and leaving behind no discernible mark. To address this issue, a face recognition system for crime detection was developed. In this study, a qualitative method was used to collect the face images of criminals in collaboration with law enforcement agencies. An API was built using the criminals National Identification Numbers. Then, a face recognition view that returns the object of the user gotten from the National Identification Number was built. The returned user objects (including face images of the user) underwent preprocessing steps, including normalization, resizing, and noise removal, to enhance the quality and standardize the facial features. Local Binary Patterns algorithm in Python OpenCV library was applied to the preprocessed face images to extract discriminative features from the preprocessed face images. These features aimed to capture the unique characteristics of each face for subsequent recognition. The algorithm was trained on the extracted features and tested given a new input image. The interface component specification of the system was designed using HTML, CSS, and JavaScript client-side technologies. MySQL was used as a database model that stores the images of known individuals. Django web application framework for Python was used to implement the system. Finally, the result shows that the system can recognize images on a face confidence level of 90% and above with the name of the suspect being displayed.
Introduction
I. INTRODUCTION
Over the years, locating criminals has proven to be a difficult task. Previously, the approach was based on leads obtained from evidence found at the scene of the crime. Genetic evidence is relatively easy to locate, but criminals have become more adept at hiding their tracks and leaving no trace. As a result, facial recognition and surveillance technologies are now being used. Ultimately, face recognition technology has become an increasingly popular area of research due to its potential to enhance security and surveillance systems. The face is an essential element of social identity, and each face has distinctive features. Facial recognition is a unique biometric approach that is highly accurate and minimally invasive for crime detection. It involves naturally recognizing and verifying a person's identity from video sequences or photos using their face (Teoh et al 2021).
The use of face recognition technology has become increasingly common in crime detection systems, but there are several problems associated with this technology that can negatively impact its accuracy and reliability. Some of these problems include: Poor image qualities, Diversity in faces, Privacy concerns, and Biases:
This work is aimed at developing a face recognition system using Python that can accurately identify suspects and improve the efficiency of crime detection. The objectives of the study is focused:
- On developing a face recognition system using python programming language, Local Binary Patterns Histograms (LBPH) algorithm for classification and identification of potential matches.
- Developing a user interface for the system using HTML, CSS, JS, Django, framework and that can be used in law enforcement to identify criminals and prevent crime.
II. OVERVIEW
Automated facial recognition is a computerized technique that extracts significant facial features, such as the distance between the eyes, the width of the nose or jawline, and the eye color, among others. These characteristics are useful in categorization and record matching. This system involves two crucial processes: detection and recognition. The facial recognition process involves two primary phases: training and assessment.
The algorithm is fed as sample of images and trained on the training set. The facial recognition assessment phase then compares the newly obtained test image to the database. In detection we need just to determine if there is some face in the image, but in recognition we want to determine whose face it is (Zamindar et al., 2022). With the widespread adoption of face recognition in various applications, ethical considerations and privacy concerns have come to the forefront. Research and discussions around biases, transparency, and regulations in face recognition systems have gained prominence (Gebru et al., 2019).
The face plays an important role in human communication, revealing unique character traits, emotions, and age, and allowing for social interaction. In recent years, biometric-based technologies, including facial recognition, have emerged as the most effective and reliable method for recognizing faces. Although individuals can deny the truth, biometric technologies such as fingerprints, faces, and eyes are relatively more reliable and difficult to forge since "the body never lies," and altering biometric features is incredibly challenging.
Primoz et al., (2018) analyzed algorithms on many images to determine the better computer vision libraries for the face detection and recognition tasks. In the paper, computer vision libraries were first discussed. Then Face detection and Face recognition capabilities of libraries available were analyzed
III. RESEARCH METHODOLOGY
The methodology can be described as follows:
- Problem Identification: This is the initial phase that is involved with a comprehensive review of existing literature and real-world scenarios for the identification of the limitation and challenges of the current face recognition system.
- System Requirements Gathering: This phase carries out an extensive consultation with domain experts, law enforcement agencies, and stakeholders in order to gather the necessary requirements for the proposed system.
- Data Collection: Collection of a diverse dataset of face images comprising both criminal and non-criminal individuals, with variations in lighting conditions, pose, and expressions. The dataset was carefully screen to ensure accurate representativeness and minimize biases.
- Preprocessing: The data (face images) collected undergo face images preprocessing steps, including normalization, resizing, and noise removal, to enhance the quality and standardize the facial features. This step aimed at improving the system's performance in different environmental conditions.
- Feature Extraction: Various feature extraction techniques, such as Local Binary Patterns (LBP), Eigenfaces, and deep learning-based methods, were explored and implemented to extract discriminative features from the preprocessed face images. These features aimed to capture the unique characteristics of each face for subsequent recognition.
- Algorithm Selection and Implementation: Different face recognition algorithms, including support vector machines (SVM), k-nearest neighbors (KNN), and convolutional neural networks (CNN), were evaluated and implemented using Python and OpenCV libraries. The algorithms were trained on the extracted features using appropriate training and testing methodologies.
- Performance Evaluation: The developed system underwent rigorous testing and evaluation using various performance metrics such as accuracy, precision, recall, and F1 score. The system's performance was assessed on different subsets of the dataset, considering factors like occlusion, pose variations, and lighting conditions to gauge its robustness and generalizability.
- System Validation: The developed system was validated through comparative analysis with existing face recognition systems and benchmark datasets. The validation aimed to establish the effectiveness and superiority of the proposed system in terms of accuracy, speed, and crime detection capabilities.
By following this research methodology, the development of the face recognition system for crime detection ensured a robust, systematic, and evidence-based approach, leading to the creation of an advanced system capable of accurate and efficient crime detection based on facial recognition technology.
IV. ALGORITHM OF THE PROPOSED SYSTEM
The algorithm used to get this face recognition system for crime detection is the Local Binary Patterns Histograms (LBPH) algorithm. It is a widely used method for face recognition. Here's a step-by-step explanation of the algorithm:
A. Algorithm
- Preprocessing
a. Convert the input image to grayscale
b. Optionally, apply image normalization techniques to enhance contrast and reduce illumination variations.
2. Local Binary Patterns (LBP) Calculation
a. Divide the image into overlapping cells or regions.
b. For each pixel in the cell, compare its intensity value with its neighboring pixels (usually using an 8-pixel neighborhood).
c. Assign a binary value of 1 if the neighboring pixel is greater than or equal to the center pixel; otherwise, assign a value of 0.
d. Concatenate the binary values of all pixels to form a binary pattern for that cell.
3. Histogram Calculation
a. Calculate a histogram for each cell by counting the occurrences of different binary patterns.
b. Optionally, apply histogram equalization or other normalization techniques to enhance the discriminative power of the histograms.
4. Feature Extraction
a. Concatenate the histograms from all cells to form a feature vector for the entire image.
b. Optionally, perform dimensionality reduction techniques, such as Principal Component Analysis (PCA) or Linear Discriminant Analysis (LDA), to reduce the feature vector size and improve computational efficiency.
5. Training
a. Collect a set of labeled face images for training.
b. Extract LBPH features from each training image using the aforementioned steps.
c. Train a classifier, such as Support Vector Machines (SVM) or k-Nearest Neighbors (k-NN), using the extracted features and their corresponding labels.
6. Testing
a. Given a new input image, extract LBPH features using the same steps as in training.
b. Feed the extracted features to the trained classifier to predict the identity of the face.
c. Optionally, apply post-processing techniques, such as majority voting or confidence thresholding, to improve the accuracy of the predictions.
The LBPH algorithm provides a robust representation of local texture patterns in the face images, making it effective for face recognition tasks. It can handle variations in illumination, pose, and facial expressions to some extent. However, it may not perform well in scenarios with severe occlusions or large variations in scale
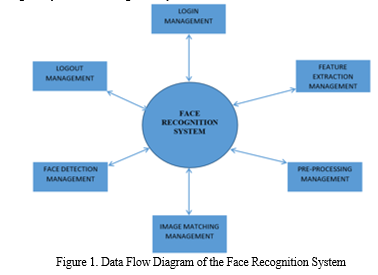
B. Level 0 Data Flow Diagram of the Face Recognition System
From the screenshot above, we can see the different columns of the table and their associated datatypes and constraints which include: id (INT datatype), username (VARCHAR datatype), password (VARCHAR datatype), first_name (VARCHAR datatype), last_name (VARCHAR datatype), date_joined (DATE datatype), is_admin (TINYINTY datatype), last_login (DATE datatype), and Userscol (VARCHAR datatype).
From the schema defined above, the users table will look like this below, due to the fact that we’re using a relational database with table consisting of rows and column structurally.
V. RESULTS
The programming language used for the implementation, system requirements to run the system, and the result of the implementation is addressed here. The Modules of the System include the following: Face Detection, Face Confidence and Face Recognition
- Face Detection: This module is responsible for detecting face objects from images. What this module does is that it turns on the camera, then detect any object or any face that is Infront of the camera and label the assumed name.
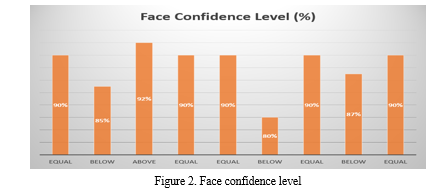
- Face Confidence: This module returns the actual number of percentages that is shown on the person’s face that is being identified. The system rejects any face confidence that is below 90%, and this always occurs when it found a resemblance in two faces.
- Face Recognition: This module does database comparison. The extracted facial features are compared against a database of known individuals. This involves matching the feature vectors of the captured face with the feature vectors stored in the database. After recognizing the face we want, we press letter Q on the keyboard to end the face recognition, and then it takes us to the criminal’s profile page which has all the information about the criminal it recognized his face.
To save more of our time in taking pictures of criminals every time, we leverage on their national identification number by building an API (Application Programming Interface) of the national identification number. We also built different views where we handle our logics. The first view is the face recognition view, which returns the object of the user gotten from the national identification number API. It is now that we run our face confidence module discussed above. Once the face confidence level is below 90%, the face is rejected.
For motion detector, we have two object frames. We compare the difference between these two frames. If there’s any difference, that means there’s a motion, but if there’s no difference, then there’s no motion in the object. We have other views (a view in Django is like a business logic) such as the about view which shows us the about page on request, the home view which displays the home page on request, the detail view which shows us the picture and information of the suspect on request after identifying the suspect.
Views
- Face recognition API view
- National Identification Number API view
- Home view
- Detail view
- About view
We tested the models developed to check for any errors. To finally run the developed system, created template directories, connect the template with the views, and connect the views with the URL endpoints, and run the engine to start it running.
Endpoints are functions bounded to URL which performs the task of the function whenever a user hits the URL bounded to the function on the web.
Finally, the result of the implementation is shown here. Below are the screenshots of the working system:
A. The Home Page
The Home page displays the basic functionalities of the system which are face detection, face recognition, and motion detection.


VI. RECOMMENDATIONS
To optimize the effectiveness of the system, we propose the following key recommendations:
- Algorithm Enhancement: Continuously explore and optimize state-of-the-art face recognition algorithms, such as the Local Binary Patterns Histograms (LBPH) algorithm.
- Dataset Diversity: Enrich the training dataset with diverse facial attributes, including varying age groups, ethnicities, and facial expressions.
- Real-time Processing: Investigate hardware acceleration and parallel processing techniques, such as GPU utilization, to ensure real-time face recognition for swift analysis of video streams from surveillance cameras.
- Motion Detection Refinement: Refine the motion detection module by exploring advanced motion analysis techniques, such as optical flow or background subtraction, to identify and flag suspicious activities promptly.
- Real-world Testing: Conduct extensive real-world testing and validation with law enforcement agencies to assess the system's accuracy and reliability in actual crime detection scenarios.
- Security and Privacy: Implement robust security measures, including data encryption and access controls, to safeguard sensitive information and ensure privacy compliance.
- User Interface Optimization: Create an intuitive and user-friendly interface, incorporating feedback from potential end-users, to enhance ease of adoption and efficient interaction with the system.
Conclusion
In conclusion, the project holds significant potential in enhancing crime detection and prevention efforts. By harnessing the power of advanced face recognition algorithms and motion detection, the system provides law enforcement agencies with a powerful tool to combat crime and ensure public safety. As a computer science final year project, this research contributes valuable insights to the field of face recognition technology and serves as a foundation for further advancements in crime detection systems. The successful implementation of this system can positively impact law enforcement operations, leading to more effective crime detection, faster response times, and ultimately, safer communities.
References
[1] AlBdairi, A. J. A., Xiao, Z., Alkhayyat, A., Humaidi, A. J., Fadhel, M. A., Taher, B. H., & Al-Shamma, O. (2022). Face Recognition Based on Deep Learning and FPGA for Ethnicity Identification. Retrieved from Researchgate: Applied Sciences, 12(5), 2605 [2] Almeida, D., Shmarko, K., & Lomas, E. (2022). What is Literature Review in research works. Retrieved from Scribbr: https://www.scribbr.com/methodology/literature-review/ [3] Andrew H. (2019). How does facial recognition work?. Retrieved from howtogeek: https://www.howtogeek.com/427897/how-does-facial-recognition-work/ [4] Apoorva, P., Impana, H. C., Siri, S.L., Varshitha, M.R. & Ramesh, B. (2019). Automated criminal identification by face recognition using open computer vision classifiers. 3rd International Conference on Computing Methodologies and Communication (ICCMC) 2019 Mar 27 (pp. 775-778). IEEE. [5] Arjun M., Kumari S. S., Raushan K., Ritvik S., & Abha K. R. (2023). Leveraging Facial Recognition Technology in Criminal Identification. Retrieved from Researchgate: https://www.researchgate.net/publication/369961780_Security_Technologies_Using_Facial_Recognition. [6] Asif, A., Radhika, M., Shraddha, B., Ujwwal, M., & Vipul, J. (2021). Automatic Face Recognition Attendance System using Python and OpenCv. GRD Journals- Global Research and Development Journal for Engineering, 2455-5073. [7] Minal, T., Rupesh, C. J., Girish, P. P., & Manish, R. K. (2023). Face, Expression And Gesture Recognition & Compilation In Database. International Journal of Creative Research Thoughts, 2320-2882. [8] Ms. Jaishree T., Ms. Rashmi S., Ms. Neha S., & Mr. Jitendra P. (2018). Image–Based Face Detection and Recognition using MATLAB. Retrieved from ijcemjournal: https://issuu.com/ijcemjournal/docs/image___based-face-detection-and-re [9] Nick Barney (2023). What is face detection?. Retrieved from techtarget: https://www.techtarget.com/searchenterpriseai/definition/face-detection [10] Nurul, A. A., Md. J. Saidi, N. H. A. Rahman, C. C. Wen, & I. R. A. Hamid (2018). Face recognition for criminal Identification: An implementation of principal component analysis for face recognition. AIP Conference Proceedings 1891:1 [11] Primoz, P. & Boris, K. (2019). Face Detection and Face Recognition in Python Programming Language. Proceedings of The Seventh International Conference on Informatics and Applications, 978-1-941968-53-6. [12] Ramiz S., & Mohamed N. (2022). Security Technologies Using Facial Recognition: https://www.researchgate.net/publication/369961780_Security_Technologies_Using_Facial_Recognition. [13] Rupali, S. S. & Pawar, K. N. (2019). Face Recognition using Fisherfaces. International Journal for Research in Applied Science and Engineering Technology, 2321-9653. [14] Shona, (2023). How to write a literature review | guide, examples, & templates. Retrieved from Scribbr: https://www.scribbr.com/methodology/literature-review/ [15] Soppari K., & Ramesh A. (2022). Criminal Identification using Face and Gesture Recognition by Image. Retrieved from researchgate: https://www.researchgate.net/publication/369742206 [16] Tayyaba Z., Shradhatai G., Shital K., & Yogita K. (2022). Real-Time Face Recognition and Detection Using Python. Retrieved from Ijraset: https://www.ijraset.com/research-paper/real-time-face-recognition-and-detection-using-python [17] Teoh, K. H., Ismail R. C., Naziri S., Hussin, R., Isa M. & Basir. M. (2021) Face Recognition and Identification using Deep Learning Approach KH Teoh et al 2021 J 5th International Conference on Electronic Design (ICED) 2020 Journal of Physics: Conference Series 1755 (2021) 012006, IOP Publishing doi:10.1088/1742-6596/1755/1/012006
Copyright
Copyright © 2024 Okardi, Biobele , Udokike Daniel Ikegbunam. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET60813
Publish Date : 2024-04-23
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

