Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Fake Product Identification System for E-Commerce Applications
Authors: Sireesha Keesara, Tanmayee Veerabhadra, Sai Sriya Tiruveedhula, Uma Varshitha Reddy Vajrala, Venkata Lakshmi Vemula
DOI Link: https://doi.org/10.22214/ijraset.2024.59338
Certificate: View Certificate
Abstract
The use of blockchain technology, combined with QR codes, presents a promising solution for identifying and combating counterfeit products efficiently and securely. By integrating a blockchain-based system with QR code scanning, stakeholders can establish a reliable mechanism to verify product authenticity. This system involves storing product details and generating unique QR codes for each product as blocks in the blockchain database. When a QR code is uploaded, the system compares the code against entries in the blockchain database. If a match is found, the customer receives a notification confirming the product\'s authenticity; otherwise, they are alerted that the product is fake. Blockchain technology\'s ability to eliminate the need for trusted intermediaries, facilitate faster transactions, and provide transparency makes it particularly intriguing for addressing counterfeit issues. However, reducing counterfeits requires a comprehensive approach, including increasing awareness, legal action against counterfeiters, implementing a robust alert system, and ensuring secure packaging. These factors, combined with blockchain technology and digital signature verification, can lead to a more efficient and thorough strategy for combating counterfeiting in the marketplace.
Introduction
I. INTRODUCTION
Counterfeiting poses an incredible risk across industries, causing significant economic loss and endangering consumer welfare. The staggering annual costs of counterfeiting in the US alone, estimated at $600 billion, and projected global impacts of $4.2 trillion by 2022 highlight the urgency of addressing this issue. The counterfeit medicine market, valued at $75 billion annually, further underscores the severity of the problem, contributing to approximately 1 million deaths each year.
In transactions, trust is essential, but intermediaries such as banks often complicate matters, increasing costs and reducing transparency. However, blockchain technology, as demonstrated by Bitcoin, offers a promising solution by enabling decentralized transactions, thus bypassing intermediaries and enhancing security. This paper investigates the potential of blockchain technology in combating counterfeiting. It proposes a decentralized inventory management system involving blockchain and its related features to detect counterfeit attacks, aiming to replace centralized supply chain models and improve security and efficiency. Subsequent sections explore traditional anti-counterfeiting methods, the design of the blockchain-based inventory management system, its performance, and concluding remarks on its potential to revolutionize efforts against counterfeiting
II. LITERATURE REVIEW
The literature review underscores the significance of combatting counterfeiting to protect financial interests, reputation, and consumer safety. It highlights key features of effective anti-counterfeiting measures, including difficulty of duplication, ease of identification, prevention of re-use, and indicators of tampering. Strategies explored encompass incorporating visible and covert elements into product design, utilizing track-and-trace technologies like RFID and barcodes, and enhancing vigilance against counterfeit suppliers.
- Satoshi Nakamoto introduced blockchain as a core component of Bitcoin in 2008. Various blockchains serve different purposes, with Bitcoin having its own blockchain, known as the Bitcoin blockchain.
- Christophe Zimmermann, from the World Customs Organization, notes the alarming prevalence of counterfeit drugs, stating, "We already have more fakes than genuine drugs in the market".
- The citation "Blockchain Past Bitcoin" by S. Underwood underscores that blockchain technology, the backbone of Bitcoin, operates without reliance on a central authority, as transaction validity is determined by algorithms. This eliminates the need for third-party trust. Additionally, it highlights the broader applicability of blockchain beyond financial transactions, suggesting its potential to revolutionize the digital economy.
- L. Li fights that extraordinary adversary of fashioning strategies should all around be not difficult to apply, yet difficult to duplicate and have four chief features: They should be trying to duplicate, it should be plausible to recognize them without uncommon stuff, it should be hard to re-use them, and it should be evident expecting they were adjusted. As indicated by a thing perspective, there are three general developments to diminish fakes -Unquestionable (Recognizable) Components expected to assist the clients with insisting the legitimacy of a pack. Such features will be essentially perceptible, and convoluted or expensive to reproduce.
- Berman Associations need to ensure that they have the genuine confirmation and enlistments set up to be defended against fakes, this consolidates brand names, copyrights, plan licenses, etc. With this set up, it can anyway be excessive to actually fight against fakes. Especially luxury stock associations consume millions to fight fakes and work alongside confidential specialists really. Having a spending plan for circling back to fakes is thusly huge Controlling reexamine suppliers - Numerous associations use re-appropriated suppliers.
If a product is suspected to be counterfeit, immediate action should be taken, starting with visual inspection of its packaging and contents. If confirmed as fake, patients should be notified, and authorities must investigate its origin to combat counterfeiters and increase awareness. This approach aims to combat counterfeiting by enhancing vigilance and disrupting criminal networks.
III. METHODOLOGY
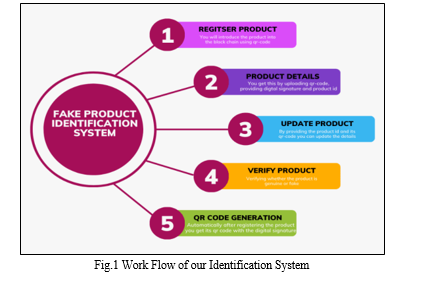
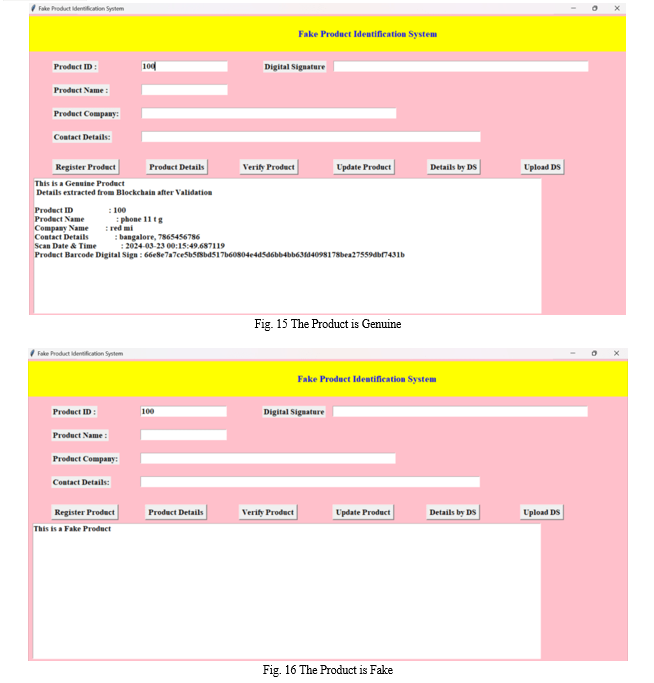
The research methodology involves the implementation of a blockchain-based system with four main functionalities as mentioned in the Fig 1: product registration, product retrieval, product updating, and product verification. Initially, products are registered on the blockchain, and a QR code is generated for each registered product uniquely. Users can then retrieve product information using the QR code. Furthermore, the system allows for updating product details on the blockchain. Finally, the blockchain is utilized to verify the authenticity of registered products. This methodology ensures secure and transparent tracking of product information throughout its lifecycle using blockchain technology.
A. Blockchain
Essentially, blockchain is a distributed organization where the interconnected frameworks are completely open and straightforward to each other. It comprises of N number of blocks which are binded together to frame a Blockchain. Every single block comprises of the exchanges which have been endorsed by the companions. Block chain usage ensures traceability, decentralization, authentication.
Overall, blockchain technology has the capability for the detection and prevention of counterfeit products by providing an authenticated, transparent, and tamper-proof application for tracking goods throughout the supply chain. However, widespread adoption and collaboration among stakeholders will be crucial for its success in combating counterfeit products effectively.
B. QR Code
QR codes are commonly used in conjunction with blockchain technology for fake product detection for several reasons like there will be Easy Access to Information, Secure Verification, User understandability, uniqueness.
Overall, QR codes serve as a practical and efficient means of linking physical products to their corresponding blockchain records, enabling transparent and secure product authentication and traceability in the fight against counterfeit goods.
C. SHA-256
It is a cryptographic hash function that gives unique hash values from input data, ensuring data and its security. In digital signature, SHA-256 hashes the document, then senders data is encrypted by using a private key and a signature is created. Upon receiving the signature, the decryption is done by using the sender’s public key in the receiver side and verifies the integrity by comparing the computed hash value with the decrypted hash. This process ensures secure communication and authentication of digital documents.
D. Pickle
It is a Python module, plays a crucial role in fake product detection by facilitating data preprocessing and serialization of Python objects. In the context of detecting counterfeit products, Pickle is utilized to preprocess data by cleaning, transforming, and organizing it for analysis. Moreover, Pickle enables the serialization and deserialization of Python objects representing product characteristics, facilitating efficient communication and exchange of data within the detection system. By leveraging Pickle, the system can effectively handle serialized data representations, enabling seamless processing and analysis of large datasets involved in identifying counterfeit products.

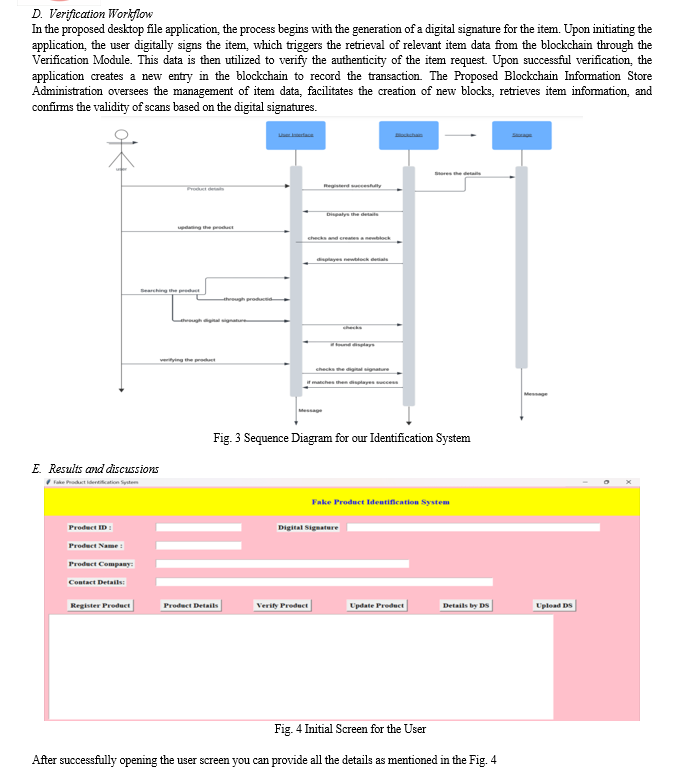



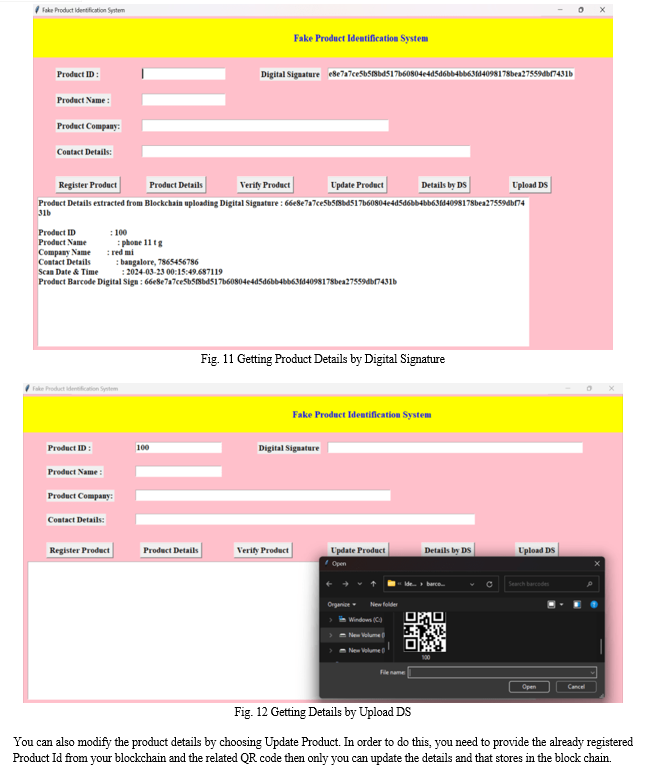
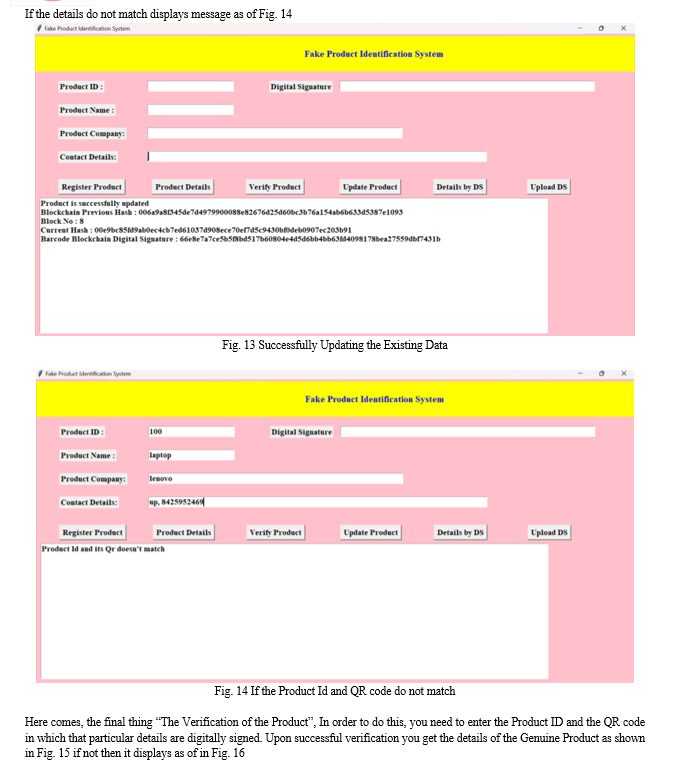
V. LIMITATIONS AND FUTURE WORK
A. Limitations
- Reliability on the Data: The data that is entered into the blockchain is heavily accurate. If incorrect data is given then it can lead to the increase of propagation of the network without proper identification.
- Verification through Physical attributes: It is not possible for the blockchain to detect the internal physical features of the product by the observation in order to distinguish between real and fake.
- Integration difficulty: Implementation of blockchain for product verification requires integration with existing supply chain systems and technologies. This integration process can be complex and costly, and it may not be feasible for all companies, particularly smaller ones with limited resources.
- Scalability: As the number of blocks and data grows sometimes it may become difficult for the blockchain to process.
B. Future Work
- Advanced Authentication: Some of the advanced authentication mechanisms like QRCODE linked to block chain plays an important level of security and becomes more difficult for the counterfeiters to replicate the data
- Integration with various Technologies: Blockchain can be integrated with various technologies like AI, ML, IOT to enhance fake product detection capabilities. AI, ML are used to detect through patterns whereas IOT provides real time data for the product.
- Instant Verification: Future projects which can be developed through blockchain need not be dependent on any 3rd party apps which leads to the faster processing of verification or authentication.
- Optimization of Performance: Addressing scalability and performance challenges is crucial for the widespread adoption of blockchain-based solutions for fake product detection. Future projects could focus on developing scalable blockchain platforms with improved consensus mechanisms and transaction processing speeds to support the high-volume transactions required for real-time product authentication in large-scale supply chains.
Conclusion
In conclusion, with this the users can finally know which product is fake or real through the QR code with the help of blockchain. Through the interconnection between unique nature of the QR code assigned to every product and the details that are stored in the blockchain we can easily verify the product and its details. With the help of the blockchain we can create a trustworthy website for any fields where users can confidently verify the authentication of products. Due to the transparency which is unparallel, immutable nature, decentralization block chain plays an important role in identifying the fake products.
References
[1] Satoshi Nakamoto, ?Bitcoin: A Shared Electronic Money System?, 2008 [2] OECD (2016), Illegal Exchange: Combining Criminal Organizations, OECD Audits of Chance Administration Strategies, OECD Distributing, Paris, https://doi.org/10.1787/9789264251847-en. [3] S. Underwood, ?Blockchain Past Bitcoin?, in Correspondences of the ACM, vol. 59, no. 11, p. 15-17, 2016. [4] L. Li, ?Technology intended to battle fakes in the worldwide stock chain?, in Business Skylines, vol. 56, no. 2, p. 167-177, 2013. [5] Berman, ?Strategies to identify and lessen duplicating activity?, in Business Skylines, vol. 51, no. 3, p. 191-199, 2008. [6] K. D\'egardin, Y. Roggo and P. Margot. ?Understanding and battling the medication fake market?, in Diary of Drug and Biomedical Examination, vol. 87, p. 167-175, 2013 [7] R. C. Merkle, ??A computerized signature in light of a traditional encryption capability,\'\' in Proc. Conf. Hypothesis Appl. Cryptogr. Techn., 1987, pp. 369-37 [8] Fake meds. QA fake. World Wellbeing Association (WHO) 2009. Accessible from: http://www.who.int/medications/administrations/fake/faqs/QACounterfeit-october2009.pdf [last refered to on 2010 Jun 12]. [9] R.C. Merkle, \"Conventions for public key cryptosystems,\" In Proc. 1980 Conference on Security and Protection, IEEE PC Society, pages 122-133, April 1980.
Copyright
Copyright © 2024 Sireesha Keesara, Tanmayee Veerabhadra, Sai Sriya Tiruveedhula, Uma Varshitha Reddy Vajrala, Venkata Lakshmi Vemula. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET59338
Publish Date : 2024-03-23
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

