Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
FPGA Implementation of 256-Bit Key AES Algorithm
Authors: Dr. P. Ravikiran, M. Gnaneshwar, Enje Hepsibha, Sudhesh Srivastav
DOI Link: https://doi.org/10.22214/ijraset.2024.63028
Certificate: View Certificate
Abstract
The most popular network security technique for secure data transmission between two end users, particularly over a public network, is the AES algorithm, also known as the Rijndael algorithm. It may be found in all kinds of wired and wireless digital communication networks AES, a network security technique, uses 256 bits on an FPGA. An authorized cryptographic technique that can be used to secure electronic data is the Advanced Encryption Standard technique (AES), which is specified by the National Institute of Standards and Technology. Because they provide faster and more flexible solutions, reprogrammable devices like Field Programmable Arrays (FPGA) are a very appealing alternative for hardware implementation of the encryption algorithm AES. The effective FPGA implementation of advanced encryption standards (AES) is proposed in this research. The encryption code is written in the Verilog programming language. The AES Rijndael algorithm performs better than any other when implemented on FPGA. Other works are covered by this implementation to demonstrate its effectiveness. The block and key sizes in the design are 256, and an iterative looping technique is used. Bits, S-box implementation using lookup tables. This results in a low-complexity design that can readily achieve high throughput and low latency
Introduction
I. INTRODUCTION
A key component of data security is cryptography. We can store confidential data on it or send it over unsecured networks, keeping it safe from prying eyes. The need for safe digital data exchange prompted the development of numerous encryption techniques in enormous volumes. Algorithms that fall into two categories: symmetric algorithms using private key algorithms and asymmetric algorithms using public key algorithms. Electronically, symmetric key algorithms typically run far more quickly than asymmetric key algorithms. The US Government organized a contest in 1997 and the Advanced Encryption Standard (AES) emerged as the victor. The Data Encryption Standard was deemed inadequate due to its tiny key size and the increasing processing capacity of devices. In 1998, fifteen candidates were approved; in 1999, the pool was narrowed to five finalists in response to public feedback. One of these five algorithms—a slightly altered Rijndael algorithm—was chosen as the future standard in October 2000.For the Advanced Encryption Standard (AES), the National Institute of Standards and Technology (NIST) issued a call for suggestions. An encryption technique called the AES is a Federal Information Processing Standard (FIPS) that is used to safeguard electronic data. An example of a symmetric block cipher that can both encrypt and decode data is the AES algorithm. Data is transformed into cipher-text, an incomprehensible format, using encryption. The data is returned to plaintext, or its original form, upon decryption of cipher-text.
The AES algorithm may encrypt and decrypt data in blocks of bits using cryptographic keys with 128-, 192-, and 256-bit lengths. In order to obtain more security and enhance confidentiality, we are using the AES-256 algorithm with a 256-bit key length. This is in contrast to AES-128 and AES-192, which have smaller keys than AES-256. Governments and individuals seeking security from data and signal interception now place a high premium on privacy. The desire for a higher level of security on previously unsafe communications has only increased due to the widespread use of personal communications devices. The primary distinction between symmetric key block ciphers like AES and DES (Data Encryption Standard) is the bit length of the key (56 bits for DES). Since both the sender and the recipient utilize the same key in these symmetric key encryption techniques, public keying does not require a verification server. Symmetric keying promotes greater system interoperability by enabling operation without the need for an open network.
II. LITERATURE SURVEY
- AES-128 cipher. high-speed, low-cost fpga implementation
The Rijndael Algorithm, which replaced DES in October 2000, is known for its fast throughput, low latency, and area optimization for parallel encryption. These goals balance area and speed. AES, integral to the 802.11 standard, is robust but demands additional processing power, often unsupported by older hardware. A high-speed, small-area FPGA implementation can offload processing from the main processor. Implemented on a Xilinx FPGA, the 10-round AES architecture aims for a high-speed, low-area core cipher. This design optimizes hardware and reduces clock cycles compared to the original. Functions related to AES transformations were developed independently and integrated. The 128-bit block encryption takes 200 nanoseconds, utilizing 50% of the FPGA device.
2. Implementation of AES algorithm using VHDL
Cryptography, the science of converting messages into an unrecognizable form using a secret key, protects information from theft. This critical data security measure, in use since 1976, ensures secure information transfer. Changing secret keys enhances security and complexity but increases memory usage and execution time. In November 2001, NIST selected the Advanced Encryption Standard (AES), a symmetric key cipher that uses the same key for both encryption and decryption of 128-bit data blocks. Encryption transforms plain text into cipher text, while decryption reverses this process. Field Programmable Gate Arrays (FPGAs), known for their reconfigurability, affordability, and speed, are ideal for implementing the 128-bit AES algorithm. This paper proposes an FPGA implementation of AES, requiring an understanding of the AES algorithm and coding it in VHDL.
III. THE AES ALGORITHM
The AES algorithm belongs to the iterative, symmetric block cipher class. Given that the same key is used for both the encryption and decryption procedures, it is symmetric. Because each data block has a fixed length of 128 bits and the encryption key has changeable key lengths that can be independently chosen as 128, 192, or 256 bits, it is a block cipher. This means that three alternative key lengths can be employed with this technique, producing three separate forms called AES-128, AES-192, and AES-256. Because this algorithm's steps are repeated multiple times, it is iterative. Another name for these iterations is rounds. The size of the key determines how many rounds or iterations are used in the encryption and decryption operations overall utilized. The link between the key length and the total number of rounds is shown in Table I. The 128-bit data block is divided into 16 bytes, which are then mapped into the State, a size 4 X 4 array.
A 4x4 matrix with 8 bits for each element is created using the 128-bit data. The four operations are carried out on a column basis; therefore, we turn the 128-bit data into a 4x4 matrix with 8 bits for each member.
Tabel 1: Data Structure of 128-bit Message
|
A0 |
A1 |
A2 |
A3 |
|
A4 |
A5 |
A6 |
A7 |
|
A8 |
A9 |
A10 |
A11 |
|
A12 |
A13 |
A14 |
A15 |
Tabel 2:RELATIONSHIP BETWEEN KEY LENGTH AND TOTAL NUMBER OF ROUNDS
|
AES |
Key Length (Nka Words) |
Block Size (Nba Words) |
Number of Rounds (Nr) |
|
AES-128 |
4 |
4 |
10 |
|
AES-192 |
6 |
4 |
12 |
|
AES-256 |
8 |
4 |
14 |
AES ENCRYPTION AND DECRYPTION ALGORITHM
The three primary components of the AES-256 algorithm are the Key Expansion, Inverse Cipher, and Cipher.
An inverse cipher returns data to its original form, known as plaintext, whereas a cipher transforms it into an unintelligible form known as cipher text. A Key Schedule is produced by Key Expansion and is utilized in the Cipher and Inverse Cipher procedures. The Cipher and Inverse Cipher consist of a predetermined quantity of rounds. The AES method employs a round function for its Cipher and Inverse Cipher that is made up of four distinct byte-oriented transformations:
- Using a substitution table (S-box) for byte replacement
- Modifying the State array's rows by various offsets
- Combining the information in every State array column.
- Including the State in a Round Key
To create a simple Inverse Cipher for the AES algorithm, the Cipher modifications can be inverted and then applied in reverse order. The specific modifications applied in the Inverse Cipher.
- Inverse Shift Rows
- Inverse Sub Bytes
- Inverse Mix Columns
- Add Round Key
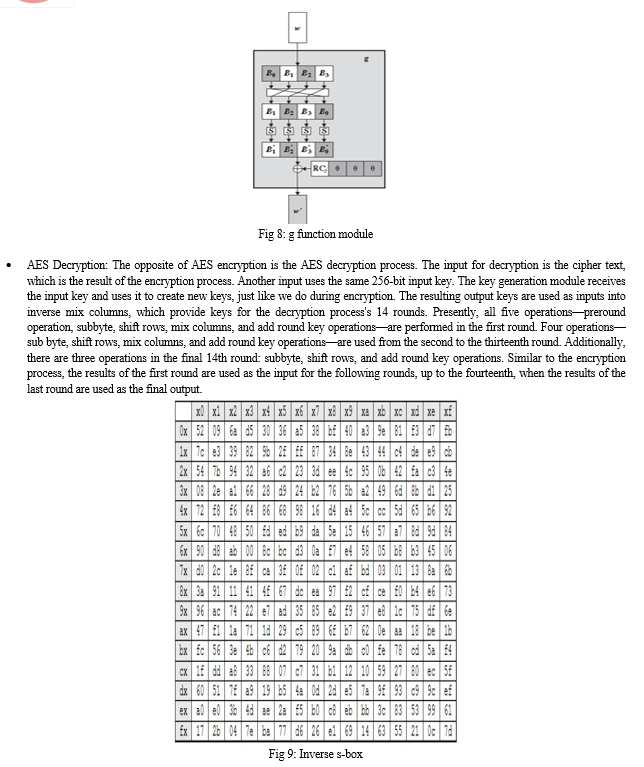
The key expansion module, key reversal buffer, start permutation module, round permutation module, and final permutation module make up the core of the AES inverse encryption. The keys for every round are first stored in the key reversal buffer, which then presents them to the rounds in reverse order. For 256-bit keys, the round permutation module will execute 14 iterations in a continuous loop.
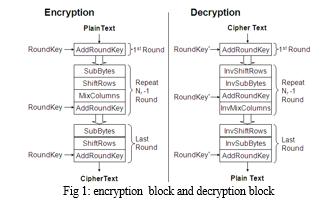
IMPLEMENTATION OF AES 256
A 256-bit key and 128-bit plaintext are used in the encryption procedure. There are fourteen cycles in AES 256. All five operations—preround, sub byte, shift rows, mix columns, and add round key operations—are included in the first round. Four operations—sub byte, shift rows, mix columns, and add round key operations—are included in the rounds two through thirteen. Additionally, there are three operations in the fourteenth and last round: subbyte, shift rows, and add round key operations.
- Key Expansion round keys are derived from the cipher key using Rijndael's key schedule.
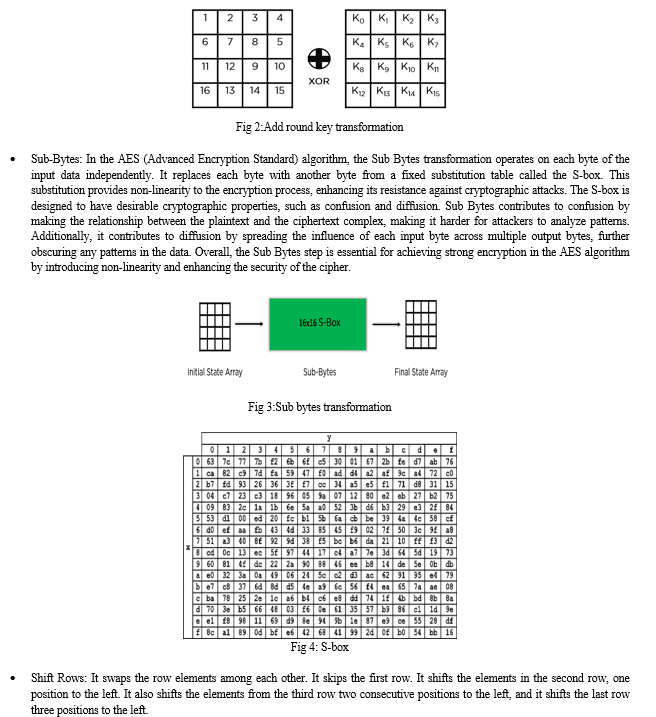
- Add Round Key each byte of the state is combined with the round key using bitwise xor.
- Sub Byte a non-linear substitution step where each byte is replaced with another according to a lookup table.
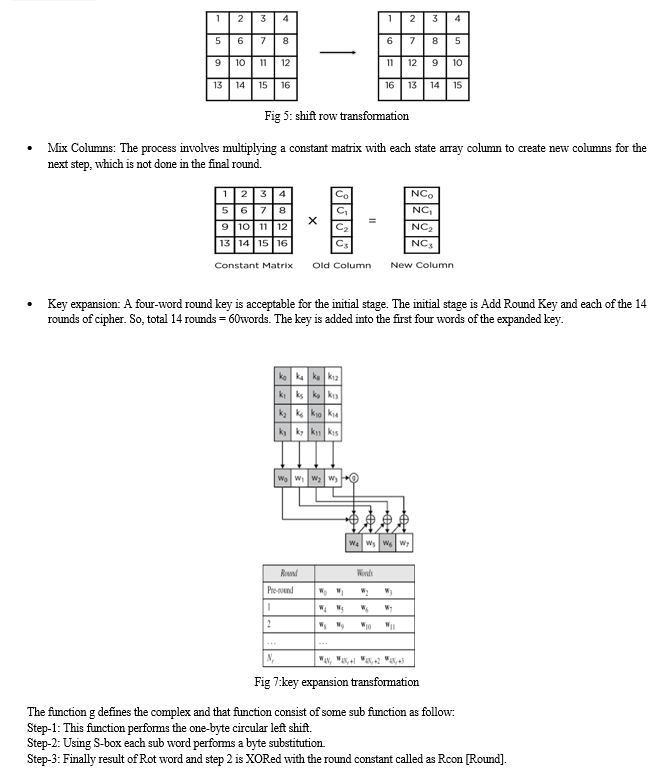
- Shift Rows a transposition step where each row of the state is shifted cyclically a certain number of steps.
- Mix Columns is a mixing operation which operates on the columns of the state, combining the four bytes in each column. 6. Add Round Key
- Add Round Key: In AES encryption, the AddRoundKey step is pivotal, serving as a crucial link between the plaintext and the encryption key. During this stage, each byte of the current block undergoes a bitwise XOR operation with a corresponding byte from the round key. This process ensures that the input data is mixed with the encryption key, introducing a key-dependent transformation that enhances the security of the algorithm. By incorporating the key at each round, AES achieves confusion and diffusion, crucial properties for robust encryption.
Through successive rounds of AddRoundKey, the original plaintext is obfuscated, making it increasingly resistant to cryptographic attacks. Ultimately, the AddRoundKey operation fortifies AES by integrating key material into the encryption process, contributing significantly to its strength and resilience against adversarial threats.
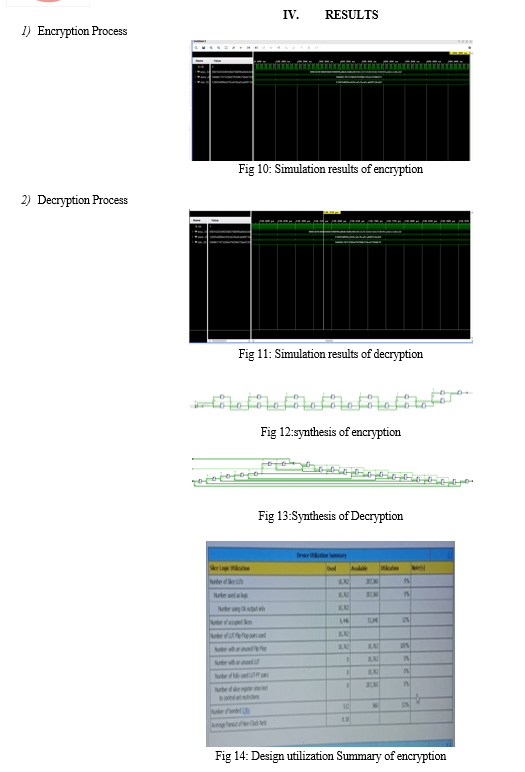
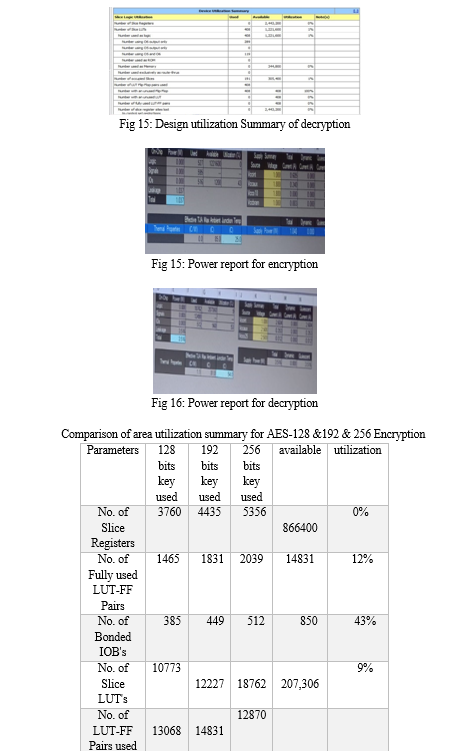
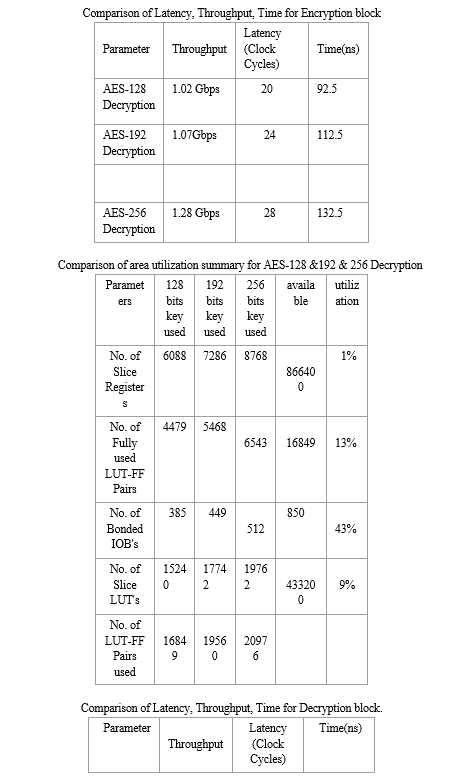
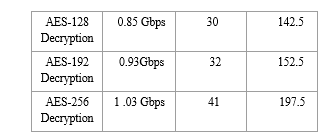
V. ACKNOWLEDGMENT
We are very grateful to Dr.P. Ravikiran, Associate Professor in the ECE Department of CMR College of Engineering and Technology for his valuable suggestions and help throughout our project and paper work completion.
Conclusion
Using cipher keys of lengths of 128, 192, and 256 bits, the Advanced Encryption Standard algorithm is an iterative private key symmetric block cipher that can handle data blocks of 128 bits. This study presents an effective FPGA implementation of the 128 bit block and 256 bit key AES cryptosystem. For the purpose of implementing 128 bit data encryption and decryption, optimized and synthesizable Verilog ode is produced. The description is confirmed through the use of Xilinx\'s ISE 9.2i functional simulator. To reduce hardware consumption, an iterative design approach is used to simulate all algorithm modifications.
References
[1] M.Rajeswara Rao and R.K. Sharma, \"FPGA implementation of combined s box and inv s box of AES\", 2017 4th international conference on signal processing and integrated networks (spin). [2] M. Liberatori, f. Otero, j. C. Bonadero and j. Castineira, \"aes-128 cipher. High-speed, low-cost fpga implementation,\" 2007 3rd southern conference on programmable logic, mar del plata, argentina, 2007. [3] Amit Kumar Manoj Kumar P. Balramudu,” implementation of AES algorithm using VHDL”, proceedings of the IEEE 2017 international conference on computing methodologies and communication (iccmc). [4] Atul M. Borkar, R. V. Kshirsagar and M. V. Vyawahare, FPGA implementation of AES algorithm. [5] Xinmiao Zhang and Keshab K. Parhi, \"high speed vlsi architectures for the aes algorithm\", IEEE, vol. 12, no. 9, september 2004. [6] Yulin Zhang and Xinggang Wang, \"pipelined implementation of AES encryption based on FPGA\", IEEE international conference on information theory and information security, 2010. [7] Vatchara Saicheur and Krerk Piromsopa, \"an implementation of aes-128 and aes-512 on apple mobile processor\", 14th international conference on electrical engineering/electronics computer telecommunications and information technology (ecti-con), 2017. [8] \"advanced encryption standard (aes)\", fips 197, November 2001. [9] Marko mali, Franc novak and Anton Biasizzo, \"hardware implementation of aes algorithm\", journal of electrical engineering, vol. 56, no. 9–10, pp. 265-269, 2005. [10] N. S. Sai srinivas and MD. Akramuddin, \"FPGA based hardware implementation of AES rijndael algorithm for encryption and decryption\", international conference on electrical electronics and optimization techniques (iceeot), 2016. [11] Ashwini M. Deshpande, Mangesh S. Deshpande and Devendra N. Kayatanavar, \"FPGA implementation of aes encryption and decryption\", international conference on control automation communication and energy conservation, 2009. [12] J. Nechvatal et al., \"Report on the development of Advanced Encryption Standard\", NIST publication, Oct 2000 [13] K. Gaj and P. Chodowiec, \"Comparison of the hardware performance of the AES candidates using reconfigurable hardware\", The Third AES Candidates Conference printed by the National Institute of Standards and Technology. [14] Behrouz A. Forouzan and Debdeep Mukhopadhyay, \"Cryptography and Network Security\". [15] F.X. Standaert, G. Rouvroy and J.D. Legat, \"Efficient Implementation of Rijndael Encryption in Reconfigurable Hardware\", Improvements and Design Tradeoffs, pp. 334-350, 2003. [16] Shanxin qu, Guochu Shou and Vihong hu, \"high throughput pipelined implementation of aes on fpga\" in information engineering and electronic commerce(ieec), ieee press, pp. 542-545, 2009. [17] Fx. Standaert, G. Rouvoy, JJ. Quisquater, JD. Legat, \"efficient implementation of rijndael encryption in reconfigurable hardware: improvements and design tradeoffs\". in the proceedings of ches 2003, lecture notes in computer science, vol 2779, pp. 334-350, springer verlag. [18] M6nica Liberatori, Fernando 0tero, J. C. Bonadero, Jorge castifieira, \"aes-128 cipher. high speed, low cost fpga implementation\". programmable logic, 2007. spl07. 2007 3rd southern conference on mar. del plata pp. 195-198 feb. 2007.
Copyright
Copyright © 2024 Dr. P. Ravikiran, M. Gnaneshwar, Enje Hepsibha, Sudhesh Srivastav. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET63028
Publish Date : 2024-05-31
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

