Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
The Future of Cybersecurity and Its Potential Threats
Authors: R Ramakrishnan, M Leethial, S Monisha
DOI Link: https://doi.org/10.22214/ijraset.2023.54603
Certificate: View Certificate
Abstract
The future of cybersecurity brings forth a range of advancements and threats in the ever-evolving digital landscape. This article provides an overview of the potential threats that individuals and organizations may face in the coming years. It explores vulnerabilities in the Internet of Things (IoT), the exploitation of artificial intelligence (AI) and machine learning (ML), the risks posed by quantum computing, supply chain attacks, cloud security challenges, and social engineering and phishing attacks. By understanding these threats, individuals and organizations can develop proactive strategies to enhance cybersecurity measures and protect their digital assets. Collaboration, technological innovation, and user awareness are key to navigating the future of cybersecurity successfully and ensuring the integrity of our digital infrastructure.
Introduction
I. INTRODUCTION
In the rapidly evolving digital landscape, the future of cybersecurity presents both exciting advancements and emerging threats. As technology continues to advance, the interconnectedness of our digital infrastructure increases, bringing convenience and efficiency, but also exposing vulnerabilities. This article explores the future of cybersecurity, examining the potential threats that organizations and individuals may face. By understanding these threats, we can better prepare and develop effective strategies to safeguard our digital assets. In recent years, the world has witnessed a rapid proliferation of digital technologies that have revolutionized how we live, work, and interact. From smart homes and connected devices to cloud computing and artificial intelligence, our reliance on digital systems has become ubiquitous. While these advancements have brought numerous benefits, they have also opened the door to new cybersecurity challenges.
The future of cybersecurity is shaped by the continued evolution and adoption of technology. As we move towards a more interconnected world, the attack surface for potential threats expands, presenting a complex and ever-changing landscape. It is essential to anticipate and understand these threats to effectively protect our digital infrastructure and sensitive information.
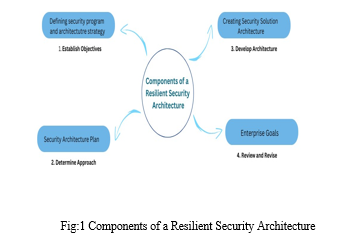
One of the key areas of concern is the Internet of Things (IoT). The IoT encompasses a vast network of interconnected devices, from smart appliances and wearable devices to industrial systems and infrastructure. While IoT offers unprecedented convenience and automation, it also introduces vulnerabilities that can be exploited by malicious actors. Inadequate security measures, weak authentication mechanisms, and lack of proper device management can leave IoT systems susceptible to attacks. Future cybersecurity strategies must address these challenges by implementing robust encryption protocols, regular software updates, and enhanced security measures for IoT devices.
Artificial intelligence (AI) and machine learning (ML) technologies are transforming various industries and revolutionizing how we process and analyze data. However, they also present new avenues for cyber threats. Malicious actors can leverage AI and ML algorithms to automate attacks, conduct targeted phishing campaigns, and bypass traditional security measures. As AI becomes more advanced, it is crucial to develop AI-powered defense mechanisms that can detect and respond to evolving threats in real-time. Additionally, ensuring ethical use of AI in cybersecurity practices is essential to prevent misuse and potential harm.
The advent of quantum computing poses both opportunities and challenges for cybersecurity. Quantum computers have the potential to break current encryption algorithms, jeopardizing the security of sensitive information. To address this threat, researchers are actively working on developing quantum-resistant encryption algorithms and post-quantum cryptography. These advancements will be critical in safeguarding data against future quantum computing-based attacks.
Another significant concern in the future of cybersecurity is the rise of supply chain attacks. Organizations increasingly rely on third-party vendors and suppliers for various components and services. However, this dependency introduces vulnerabilities in the supply chain ecosystem. Cybercriminals can exploit weak links in the supply chain to gain unauthorized access to critical systems or inject malicious code into software or hardware components. Establishing robust vetting processes, implementing continuous monitoring, and fostering collaboration among all stakeholders are crucial to strengthening supply chain security.
Cloud computing has transformed the way we store, process, and access data. However, it also brings unique security challenges. Data breaches, misconfigurations, and unauthorized access to cloud resources can have severe consequences. Future cybersecurity efforts should focus on enhancing cloud security through robust access controls, encryption, and continuous monitoring to protect sensitive data stored in the cloud.
Lastly, social engineering and phishing attacks remain persistent and continue to evolve. Cybercriminals exploit human vulnerabilities, manipulating individuals through psychological tactics to gain unauthorized access to systems or extract sensitive information. Combating social engineering attacks requires a multi-faceted approach, including user awareness training, strong authentication mechanisms, and effective incident response strategies.
II. AN OVERVIEW OF ENTERPRISE CYBERSECURITY ARCHITECTURE
"Enterprise Cybersecurity" offers organizations a comprehensive framework to bolster their defenses against the evolving threat landscape of targeted cyberattacks. This book provides valuable insights and guidance for managing all aspects of an enterprise cybersecurity program. It empowers organizations to architect, design, implement, and operate a cohesive cybersecurity program that aligns seamlessly with policy, technology, IT life cycle, and assessment. Accompanied by a Study Guide featuring helpful slides, this resource equips organizations to navigate the complex cybersecurity landscape effectively.
The core of "Enterprise Cybersecurity" lies in its unified framework, encompassing the key elements of a robust cybersecurity program: policy, personnel, budget, technology, strategy, engineering, operations, and assessment. This comprehensive framework, documented and publicly disclosed for the first time, has been successfully utilized by Fortune 500 companies in defending against nation-state attackers, cyber criminals, and other advanced adversaries. It emphasizes the integration of cyberdefenses with an organization's IT infrastructure, establishing layered protections that offer redundancy and resilience.
Rather than striving for unattainable perfection, the book advocates for organizations to define their cybersecurity goals as "good enough" and focus on achieving visibility, employing metrics and indicators, and adopting an active defense approach. It emphasizes the importance of continuous evaluation and adaptation based on real-time insights into the effectiveness of cybersecurity measures. Blindly attempting to protect all assets without visibility into their security posture is no longer sufficient in the face of sophisticated threats.
By embracing the principles and strategies outlined in "Enterprise Cybersecurity," organizations can strengthen their cyber defenses, mitigate risks, and proactively respond to emerging threats. This comprehensive approach enables organizations of all sizes to establish a robust cybersecurity program that safeguards their critical assets and supports their overall business objectives.
Enterprise Cybersecurity Architecture encompasses various components and considerations related to system administration, network security, application security, programming, people, budget, technology, and the IT life cycle. Let's discuss each of these aspects in the context of cybersecurity architecture:
- System Administration: System administration involves managing and maintaining the organization's information systems, including servers, databases, and operating systems. In the context of cybersecurity architecture, system administrators play a crucial role in ensuring the security and proper configuration of these systems. They implement security patches, updates, and access controls, and monitor system logs for potential security incidents.
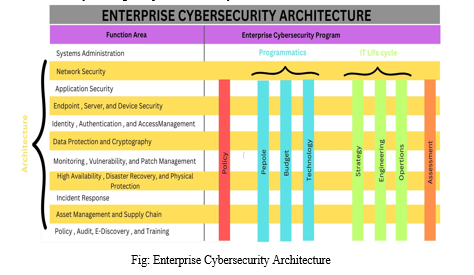
2. Network Security: Network security focuses on protecting the organization's network infrastructure from unauthorized access and malicious activities. This includes the implementation of firewalls, intrusion detection and prevention systems, secure network segmentation, and secure Wi-Fi protocols. Network security aims to safeguard the confidentiality, integrity, and availability of network resources and data.
3. Application Security: Application security refers to the measures taken to protect software applications from potential vulnerabilities and attacks. This includes secure coding practices, input validation, access controls, and regular application testing and scanning for vulnerabilities. Application security ensures that software applications are developed and deployed with security in mind, minimizing the risk of exploitation.
4. Programming: Programming in the context of cybersecurity architecture involves ensuring secure coding practices. Programmers and developers should follow established coding standards, use secure programming languages, and implement security controls to prevent common vulnerabilities such as SQL injection, cross-site scripting, and buffer overflow attacks. Secure programming practices contribute to the overall security of applications and systems.
5. People: The human element is a critical aspect of cybersecurity architecture. It involves creating a security-aware culture within the organization and providing ongoing training and awareness programs to employees. People need to understand their roles and responsibilities in maintaining a secure environment and be aware of potential security threats, such as social engineering attacks. Regular security training helps foster a security-conscious workforce.
6. Budget: Budget considerations are essential in cybersecurity architecture. Organizations need to allocate sufficient resources to implement and maintain effective security controls and technologies. This includes investing in security hardware and software, security training programs, and engaging third-party security services, if necessary. Adequate budget allocation ensures that cybersecurity remains a priority within the organization.
7. Technology: Technology forms the foundation of cybersecurity architecture. It includes the selection and implementation of security tools, such as firewalls, intrusion detection systems, encryption technologies, and security information and event management (SIEM) solutions. The choice of technology should align with the organization's security objectives, risk appetite, and budget constraints.
8. IT Life Cycle: The IT life cycle refers to the various stages of IT operations, from strategy and planning to engineering, operations, and assessment. In the context of cybersecurity architecture, it involves developing a security strategy that aligns with the organization's overall objectives, designing and engineering secure systems and networks, implementing security controls, monitoring and managing security operations, and regularly assessing and testing the effectiveness of security measures.
A. Internet of Things (IoT) Vulnerabilities
The proliferation of IoT devices presents significant cybersecurity challenges. With billions of interconnected devices, ranging from smart homes to industrial systems, the attack surface for potential cyber threats expands exponentially. As more devices become interconnected, the vulnerabilities within these systems, such as weak authentication mechanisms and unpatched software, pose serious risks. Future cybersecurity measures must focus on securing IoT devices, implementing robust encryption protocols, and improving device management practices.
III. ARTIFICIAL INTELLIGENCE (AI) AND MACHINE LEARNING (ML) EXPLOITATION
The integration of AI and ML technologies brings tremendous benefits across various sectors. However, these technologies can also be exploited by malicious actors. The potential misuse of AI for automated cyberattacks, such as spear-phishing and social engineering, raises concerns about the future of cybersecurity. It is crucial to develop advanced AI-powered defense mechanisms that can detect and counteract evolving threats in real-time, while also ensuring the ethical use of AI in cybersecurity practices.
A. Quantum Computing Threats
Quantum computing holds the promise of solving complex computational problems at an unprecedented speed. However, this advancement also poses a significant threat to traditional encryption algorithms used to secure sensitive data. Quantum computers have the potential to decrypt encrypted information, rendering current cryptographic protocols obsolete. To mitigate this threat, the development of quantum-resistant encryption algorithms and post-quantum cryptography is imperative to maintain data security in the future.
IV. SUPPLY CHAIN ATTACKS
As organizations increasingly rely on third-party vendors and suppliers, the risk of supply chain attacks grows. Cybercriminals exploit vulnerabilities in the supply chain ecosystem to gain unauthorized access to critical systems or inject malicious code into software or hardware components. Strengthening supply chain security requires robust vetting processes, continuous monitoring, and collaboration among stakeholders to ensure the integrity and security of the entire supply chain.
V. UNDERSTANDING THE MECHANICS OF A SUPPLY CHAIN ATTACK
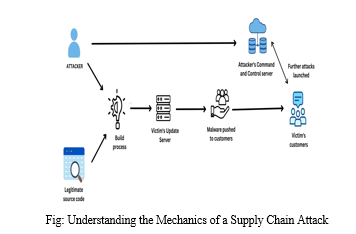
A supply chain attack exploits the trusted processes and relationships within a business ecosystem to gain unauthorized access. This type of attack begins by infiltrating the security defenses of a vendor, often taking advantage of the lax cybersecurity practices commonly found among suppliers.
The initial breach can occur through various attack vectors. Once inside the vendor's environment, the malicious code seeks to embed itself within the legitimate flow of data destined for the vendor's customers. This is achieved by leveraging digital signatures, which verify the authenticity of software and enable its distribution to all connected parties.
By leveraging the digital signature, the malicious code disguises itself within the stream of software updates exchanged between the compromised vendor and its customers. For instance, the infamous SolarWinds attack involved injecting a malicious payload into a digitally signed SolarWinds Orion software library file. This file, carrying the masked intentions of nation-state hackers, provided access to SolarWinds' extensive customer base.
Compromised vendors inadvertently propagate malware to their entire customer network. The software patches intended to address vulnerabilities actually contain a backdoor that establishes communication with external servers, serving as the point of distribution for the malware.
Through a single update, a prominent service provider can unwittingly infect thousands of organizations, enabling malicious actors to achieve a broad reach with minimal effort. This technique allows for a higher magnitude of impact, as threat actors exploit the inherent trust placed in reputable vendors and exploit the interconnected nature of supply chains.
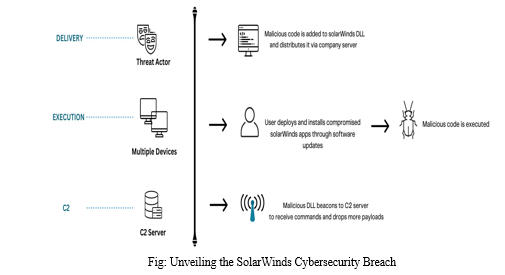
A. Unveiling the Solar Winds Cybersecurity Breach
The SolarWinds cyberattack, attributed to Russia, has revealed a larger scope of impact than initially thought. Instead of a few dozen organizations, the attack targeted approximately 250 entities, including government and enterprise organizations. The attackers exploited multiple layers of the supply chain to carry out their operation, infiltrating the systems of networking devices vendor SolarWinds.
The consequences of the attack are far-reaching, with cybersecurity insurance companies estimated to face potential losses of up to $90 million. This substantial cost is due to the lack of confidence in the digital security measures of government agencies. The attackers deliberately maintained a low profile to stealthily steal information, opting not to cause visible damage to systems.
The SolarWinds cyberattack serves as a stark reminder of the vulnerability of supply chains and the potential for sophisticated cyberattacks to breach even well-established security defenses. Organizations and governments must remain vigilant and implement robust cybersecurity measures to protect their networks from such threats.
VI. CLOUD SECURITY CHALLENGES
The adoption of cloud computing has transformed how organizations store, process, and access data. However, this shift to the cloud introduces new security challenges. Data breaches, misconfigurations, and unauthorized access to cloud resources can have severe consequences. Future cybersecurity efforts should focus on enhancing cloud security through rigorous access controls, encryption, and continuous monitoring to protect sensitive data stored in cloud environments.
VII. SOCIAL ENGINEERING AND PHISHING ATTACKS
Despite advancements in technology, social engineering and phishing attacks remain significant threats. Cybercriminals exploit human vulnerabilities through sophisticated social engineering techniques to deceive individuals into disclosing sensitive information or performing malicious actions. Addressing these threats requires a multi-layered approach that combines user awareness training, robust authentication mechanisms, and effective incident response strategies.
Conclusion
The future of cybersecurity presents a dynamic landscape with both promising advancements and evolving threats. Organizations and individuals must remain vigilant and proactive in their cybersecurity practices. By understanding the potential threats discussed in this article, we can prepare for the challenges ahead and invest in robust security measures. Through collaboration, technological innovation, and continuous learning, we can navigate the future of cybersecurity with resilience and confidence, safeguarding our digital assets and preserving the integrity of our digital infrastructure.
References
[1] “A Study of Cyber Security Threats, Challenges in Different Fields and its Prospective Solutions: A Review”, Chinyere Nneoma Ugwu, Ifeanyi Cornelius Ugwuanyi, Val Hyginus U. Eze, 2021 International Network Organization for Scientific Research, INOSR Scientific Research 9(1):13-24, 2023, ISSN: 2705-1706. [2] Abel Yeboah-Ofori, Shareeful Islam, Sin Wee Lee, Zia Ush Shamszaman, Khan Muhammad, Meteb Altaf, Mabrook S.Al-Rakhami at June 2021 “Cyber Threat Predictive Analytics for Improving Cyber Supply Chain Security”in Volume 9. [3] Qi Li, Weishi Li, Junfeng Wang, Mingyu Cheng at October 2019 “A SQL Injection Detection Method Based on Adaptive Deep Forest” in Volume 7. [4] Yaoqi Yang, Xianglin WeiRenhui Xu, Laixian Peng,Lei Zhang ,Lin Ge at June 2020 “Man-in-the-Middle Attack Detection and Localization Based on Cross-Layer Location Consistency” in Volume 8. [5] Alireza Esfahani, Georgios Mantas, Jose Ribeiro, Joaquim Bastos, Shahid Mumtaz, Manuel A.Violas, A.Manuel De Oliveira Duarte, Jonathan Rodriguez at April 2019 “ An Efficient Web Authentication Mechanism Preventing Man-In-The-Middle Attacks in Industry 4.0 Supply Chain” in Volume 7. [6] Keren L.G. Snider, Ryan Shandler, Shay Zandani and Daphna Canetti at August 2021 “Cyberattacks, cyber threats, and attitudes toward cybersecurity policies”. [7] Sultan Asiri, Yang Xiao, Saleh Alzahrani, Shuhui Li, Tieshan Li at January 2023 “A Survey of Intelligent Detection Designs of HTML URL Phishing Attacks” in Volume 11. [8] Innocent Mbona, Jan H.P. Eloff at October 2022 “Classifying social media bots as malicious or benign using semi-supervised machine learning”. [9] Md.Sakir Hossain, Naim Hasan, Md.Abdus Samad, Hossain Md.Shakhawat, Joydeep Karmoker, K.F.M.Nafiz Fuad, Kwonhue Choi at December 2022 ” Android Ransomware Detection From Traffic Analysis Using Metaheuristic Feature Selection” in Volume 10. [10] Keren L.G. Snider , Ryan Shandler , Shay Zandani and Daphna Canetti at August 2021 “Cyberattacks, cyber threats, and attitudes toward cybersecurity policies”. [11] Anderson, R. (2008). Security Engineering: A Guide to Building Dependable Distributed Systems. Wiley. [12] Cavusoglu, H., Mishra, B., & Raghunathan, S. (2004). The Effect of Internet Security Breach Announcements on Market Value: Capital Market Reactions for Breached Firms and Internet Security Developers. International Journal of Electronic Commerce, 9(1), 69-104. [13] Herley, C. (2009). So Long, and No Thanks for the Externalities: The Rational Rejection of Security Advice by Users. Proceedings of the 2009 Workshop on New Security Paradigms, 133-144. [14] Lipinski, M., & Lipinski, P. (2015). Social Engineering in the Cyberspace: Psychological Perspective of Manipulation Techniques Used in Cyber Crimes. Journal of Applied Security Research, 10(3), 373-395. [15] McQueen, R. J., & Mahmoud, Q. H. (2009). Cyber Security and Information Assurance Challenges in Smart Grids. Proceedings of the 42nd Hawaii International Conference on System Sciences, 1-10.
Copyright
Copyright © 2023 R Ramakrishnan, M Leethial, S Monisha. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET54603
Publish Date : 2023-07-04
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

