Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
High Accuracy Bank Locker Security System using GSM and GPS
Authors: Md. Abdul Naqi, Vura Bhanu, Surakanti Nikitha, Tupakula Shravani
DOI Link: https://doi.org/10.22214/ijraset.2024.60132
Certificate: View Certificate
Abstract
In this world, there is a need of security in pretty much every area for example structures, banks, homes, and so on the grounds that robbery and burglaries are expanded by step by step .to conquer this danger a security framework has been proposed utilizing Arduino and IOT innovation. In this innovation, the secret phrase for security is at first put away in the Electrically Erasable Programmable Read Only Memory [EEPROM]. At the point when the client enters the right secret phrase then the two-way confirmation a haphazardly produced OTP is shipped off the client gadget. On the off chance that the OTP is coordinated, the framework will be opened and required capacity can be started. On the off chance that the OTP isn\'t right, the client will be furnished with just the set number of possibilities (for example three possibilities in the proposed framework). So, what we need computerized innovation to build a very much incorporated and altered security framework at a sensible cost.
Introduction
I. INTRODUCTION
In this project, we are going to make a smart OTP-based locking system. This smart lock can generate a new password every time you unlock it, which further enhances your security level. This new device is much safer than the traditional key-based system and electronic wireless lock system. If you are still using the key-based system, you are likely to land in a big problem if your key gets lost or stolen. The electronic wireless lock system is not safe either. You might forget the password and there is also a high risk being hacked. For your safety and security, we bring to you a DIY smart lock that has the capability to remove all these security threats and problems.
In an era marked by increasing reliance on technology, the need for robust security measures has never been more critical, particularly in safeguarding high-value assets such as those stored in bank lockers. Conventional security systems, while effective to a certain extent, often fall short in providing the level of protection demanded by today's sophisticated threats. Recognizing this imperative, this proposal presents a comprehensive solution: a cutting-edge bank locker security system leveraging the combined capabilities of GSM (Global System for Mobile Communications) and GPS (Global Positioning System) technologies.
The traditional reliance on physical keys or passcodes for bank locker access is being progressively replaced by advanced technological solutions that offer unparalleled accuracy, reliability, and convenience. The integration of GSM and GPS technologies into the security framework of bank lockers represents a significant advancement in this regard. By harnessing the power of these two technologies, our system not only fortifies the security measures but also introduces innovative features such as real-time tracking and remote monitoring, thereby mitigating the risks associated with unauthorized access and theft.
GSM technology, ubiquitous in today's communication infrastructure, serves as the backbone of our security system, enabling seamless connectivity and communication between the bank's central monitoring station and individual lockers. Through GSM modules installed within each locker unit, encrypted data transmission ensures secure communication channels, enhancing the system's resilience against potential breaches or tampering attempts.
Complementing the robust communication capabilities facilitated by GSM, GPS technology empowers the system with precise location tracking functionalities. Each bank locker equipped with GPS modules allows for accurate geolocation monitoring, enabling instantaneous identification of any unauthorized movement or tampering with the lockers' physical location. This real-time tracking feature not only serves as a deterrent to potential intruders but also enables swift response measures to be deployed in the event of a security breach, thereby minimizing potential losses or damages.
Furthermore, our bank locker security system incorporates intelligent algorithms and predictive analytics to proactively identify suspicious patterns or anomalies in user behavior, thereby enhancing the system's adaptability and responsiveness to emerging threats. By leveraging the vast amount of data generated by the system, our predictive analytics engine continuously refines its threat detection capabilities, ensuring proactive mitigation measures are implemented to safeguard the integrity of the bank's assets and maintain customer trust and satisfaction.
In summary, the proposed bank locker security system represents a paradigm shift in the realm of asset protection, offering unparalleled accuracy, reliability, and peace of mind to both financial institutions and their clientele. By harnessing the synergistic potential of GSM and GPS technologies, coupled with advanced data analytics, our system sets a new standard for bank locker security, reinforcing the foundation of trust and integrity upon which the financial industry thrives.
II. RELATED WORKS
A. Locker Security System Using Keypad and RFID
The fundamental reason for this paper is to plan and execute framework dependent on a Password and a Radio-Frequency Identification RFID. This framework is essentially a secret word and the RFID based admittance control framework which allows just a credible individual to open. The framework will initiate and verify the client. We have applied a security framework through an uninvolved sort of RFID and PASSWORD dependent on at mega16 microcontroller. The RFID per user peruses the ID number structure RFID tag. At that point enter the secret phrase from a Keypad, in the event that the ID number of the tag and the secret word are right, they will open. The point of building this framework is to set up an imposing storage security framework with minimal effort and liberated from blunders.
B. Design and Fabrication of Remote-Controlled Sewage Cleaning Machine
In everyday life, security of an article or property assumes a significant part. These days, security is the significant danger looked by a large portion of the associations; thus, security is acquiring significance in nowadays. This paper gives a study on different programmed distinguishing proof and access control components that have been utilize the years to forestall unapproved access. In times past, for high security zones like storage spaces for banks, military locales and so on, customary lock frameworks or passwords were utilized. However, this arrangement was not secure. Because of the headways in innovation RFID cards were utilized, yet this was not helpful for the client because of the possibility of getting lost, failed to remember or taken. Later different entryway lock security frameworks dependent on biometrics, GSM, OTP, cryptography and so forth were created. A ton of exploration is going on different programmed entryway lock frameworks and can anticipate safer frameworks in the impending years.
C. Door Lock System Using Cryptographic Algorithm Based
On IOT The Door lock framework discovers its applications in spots like workplaces structures, banks, malls, worker rooms, labs and homes. There are additionally numerous different uses of an entryway lock framework. In the new advancement in innovation, Internet of Things (IOT) has experienced numerous progressive changes nearby businesses, brilliant home application, farming, wellbeing offices, PDA and so on Nearby systems administration IOT discover applications identified with information classification, power over unapproved access of secret information and furthermore far-off access of data. The task points in planning a Door Lock System dependent on IOT utilizing cryptographic calculations. The framework planned based on IOT accomplishes uses of secrecy, security and furthermore faroff access of information. Here and there, the information shared over an organization probably won't be gotten. Thusly numerous specialists are looking into growing such a framework got from programmers. The cryptographic calculations which are utilized in this entryway lock framework will shield the information being conveyed from programmers, in light of the fact that the information is significant as the resources behind the entryway.
D. IoT Based Door Lock Surveillance System Using Cryptographic Algorithm
IOT is reforming the world. One of its famous applications is a savvy entryway lock framework to ensure the resources and insider facts behind the entryway.
In IOT based framework the client is sending his classified information over the organization which may contain passwords and other data, which are just about as vital as the privileged insights or resources behind the entryway. To determine the assets security and data security issues, the client will particularly propose a secret key based and cryptographically protected profoundly secure entryway lock framework. The planned and built up a total framework including an Android advanced cell application, utilizing cryptographic calculations for secure correspondence and programmable equipment with sensors and actuators to control unapproved access. This crypto Lock ensures our assets behind the entryway as well as it secures our information which is being communicated over the organization. It gives simple far-off access, controls unapproved access and gives a total feeling that all is well with the world.
E. Insecurity Solution of RFID Card Through Cryptography
In this venture, the framework has been proposed where the data must be more gotten than existing framework. We have utilized an encode decode instrument which is utilized for encryption and unscrambling of the data by an unscrambling watchword. The scrambled data can be saved to the neighbour data set or online distributed storage. Yet, the primary bit of leeway of our proposed framework is that the entire activity has worked with windows OS. Other than we likewise break down the run time for our framework for specific information and improve devouring run time. Wellbeing prerequisite is basic this bundle. Our system can be utilized to limit the unapproved use of RFID Card data and spotlight on the run time.
III. METHODS
- Dual Authentication: Implement a system that requires dual authentication, such as a combination of a unique PIN or biometric authentication along with location verification using GPS coordinates.
- Geofencing: Set up geofences around the bank locker locations, ensuring that access is only granted when the user's device is within a predefined boundary. This can be achieved by comparing the GPS coordinates of the user's device with the coordinates of the bank locker.
- Secure Communication: Utilize encrypted communication protocols over the GSM network to transmit authentication and access data between the user's device and the bank's server. This prevents unauthorized interception and ensures data integrity.
- Remote Locking and Unlocking: Allow authorized personnel, such as bank staff or the locker owner, to remotely lock or unlock the bank locker using secure commands sent over the GSM network. GPS coordinates can be used to verify the legitimacy of the request.
- Tamper Detection: Incorporate tamper detection mechanisms into the bank locker system to alert authorities in case of unauthorized attempts to access or tamper with the locker. This could include sensors to detect physical tampering or attempts to bypass the security mechanisms.
- Real-Time Monitoring: Implement real-time monitoring of the bank locker system, including GPS tracking of authorized personnel who access the lockers. Any suspicious activity or deviations from predefined procedures can trigger alerts for further investigation.
- Backup Power Supply: Ensure continuous operation of the security system by incorporating backup power supplies, such as batteries or generators, to prevent disruptions due to power outages or tampering attempts.
- Regular System Audits: Conduct regular audits of the security system to identify and address any potential vulnerabilities or weaknesses. This includes reviewing access logs, testing system components, and updating software to patch any security flaws.
By integrating these methods, you can create a robust bank locker security system that leverages GSM and GPS technologies to ensure high accuracy and reliability.
IV. IMPLEMENTATION AND RESULTS
A. Implementation
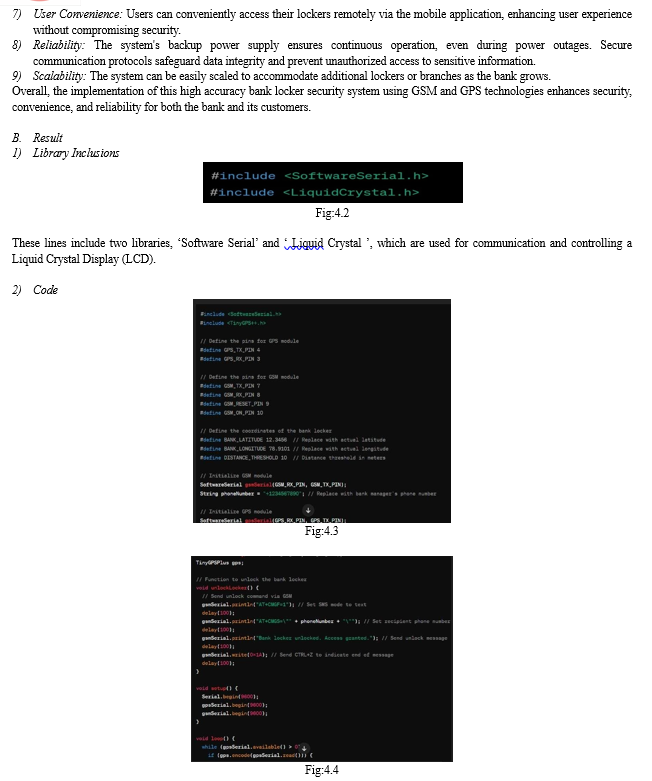
1) GSM Module: Integrate a GSM module into the system to send real-time alerts to the bank's security team and authorized users in case of unauthorized access attempts or suspicious activities.
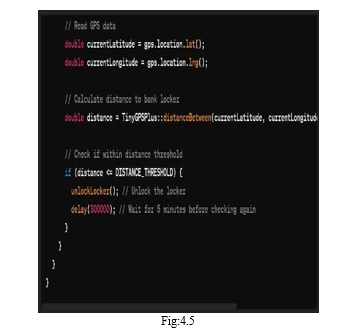
2) GPS Tracking: Incorporate GPS tracking technology into the lockers to monitor their location in real-time. This can help in case of theft or misplacement of the lockers.
3) Remote Locking/Unlocking: Allow authorized users to remotely lock or unlock their lockers using a secure mobile application. This provides convenience while maintaining security.
4) Backup Power Supply: Ensure that the system has a backup power supply to prevent disruption in case of power outages.
5) Secure Communication: Use encrypted communication protocols to ensure the security and integrity of data transmitted between the lockers, GSM module, and authorized users.
6) Real-Time Monitoring: The GSM module sends instant alerts to the bank's security team and authorized users in case of unauthorized access attempts or suspicious activities. GPS tracking enables real-time monitoring of locker locations, aiding in theft prevention and recovery. By integrating these features, you can create a highly secure bank locker system with high accuracy using GSM and GPS technologies.
In order to open the bank locker the gam based security system have been used. The gsm helps to send and receive the signals immediately within no time. First the locker system should registered the bank authorised phone number and also the respective user phone number. The lcd scans and release an OTP number to the users phone number and followed by the authorized phone no., the obtained OTP should be enter on the lcd display... If the person entered the correct OTP the locker will be open, otherwise the bank locker will not open by turning the buzzer on and sending the message 'wrong OTP' to the registered persons which includes the exact location.
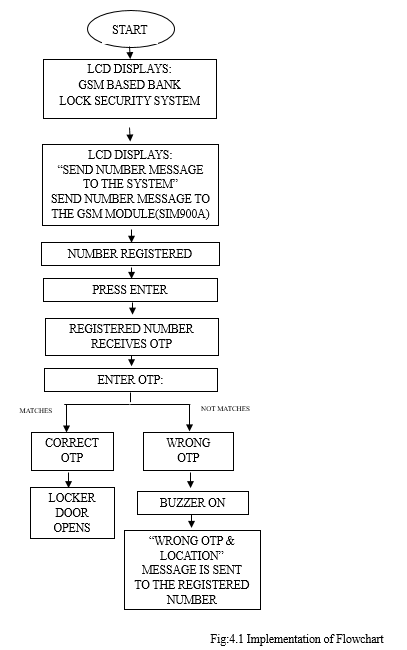
V. FUTURE SCOPE
The above proposed system can have a large number of applications due to its practicality and its security aspect.
Some of them are:
- It can be used for doors at Home and Offices.
- It can be used for Industrial doors.
- It can be used for high security Bank vault doors.
Practically any place where remote controlling is required. For future scope, the device can be paired with a CCTV.
VI. ACKNOWLEDGEMENT
Sincere thanks of gratitude are extended to the Guide and coordinator “Dr. Sudha Arvind”, Professor, Department of Electronics & Communication Engineering, for their guidance and support in completing the project and also to “Mr. G. Srikanth”, Professor and Head, of the Department of Electronics & Communication Engineering, and “Dr. A. Raji Reddy” Director of CMR Technical Campus for providing all the facility that was required.
Conclusion
The proposed framework improved the ease of use and high unwavering quality of the advanced lock framework utilizing IOT. The computerized lock framework assumes a critical part, to give the security and decrease the HR in the shrewd home and building robotization situation. The proposed technique is executed the advanced the proposed framework upgraded the convenience and high unwavering quality of the computerized lock framework, to guarantee the wellbeing, for an approved and the visitor client. The tried security viewpoints are in various climate. It is diminished the human labour, and furthermore it is given greater security, for the savvy home and building robotization applications. The proposed framework improved the convenience and high unwavering quality of the computerized lock framework utilizing IOT. The computerized lock framework assumes a huge part, to give the security and decrease the HR in the brilliant home and building computerization situation. The proposed strategy is executed the computerized lock framework, to guarantee the security, for an approved and the visitor client. We tried the security angles in the diverse climate. It is decreased the human labour, and furthermore it is given greater security, for the shrewd home and building robotization applications.
References
[1] A.Aditya Shankar, P.R.K.Sastry, A.L.Vishnu ram.A.Vamsidhar Fingerprint Based Door Locking System International Journal of Engineering and Computer Sciences ISSN:2319-7242, Volume 4 Issue 3 March 2015. [2] Kanak Chopra, garvit Jain Door Opening System Based On Fingerprint Scanning International Journal of Engineering Research Management Technology, March 2015, Volume 2, Issue-2. [3] Pavithra.B.C, Myna.B.C, Kavyashree.M Fingerprint Based Bank Locker System Using Microcontroller Proceedings of IRF International Conference, 5 April-2014, Pondicherry, India, ISBN: 978-93-82702-71-9. [4] M.Gayathri, P.Selvakumari, R.Brindha Fingerprint and GSM based Security System International Journal of Engineering Sciences Research Technology, ISSN: 2277- 9655, Gayathri et al.3(4): April, 2014. [5] Sagar S. Palsodkar, Prof S.B Patil Biometric and GSM Based Security for lockers International Journal of Engineering Research and Application ISSN: 2248-9622, Vol.4, December 2014. [6] Raghu Ram.Gangi, Subhramanya Sarma.Gollapudi Locker Opening And Closing Sys-tem Using RFID, Fingerprint, Password And GSM International Journal of Emerging Trends Technology in Computer Science (IJETTCS), Volume 2, Issue 2, March April 2013. [7] R.Ramani,S.Valarmathy, S. Selvaraju, P.Niranjan Bank Locker Security System based on RFID and GSM Technology International Journal of Computer Applications (09758887) Volume 57 No.18, November 2012 . [8] Pramila D Kamble and Dr. Bharti W. Gawali Fingerprint Verification of ATM Security System by Using Biometric and Hybridization International Journal of Science and Research Publications, Volume 2, Issue 11, November 2012. [9] Gyanendra K Verma, Pawan Tripathi, A Digital Security System with Door Lock System Using RFID Technology, International Journal of Computer Applications (IJCA) (0975 8887), Volume 5 No.11, August 2010. [10] Mary Lourde R and Dushyant Khosla Fingerprint Identi cation in Biometric Security Systems International Journal of Computer and Electrical Engineering, Vol. 2, No. 5, October,2010.
Copyright
Copyright © 2024 Md. Abdul Naqi, Vura Bhanu, Surakanti Nikitha, Tupakula Shravani. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET60132
Publish Date : 2024-04-10
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

