Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Adaptive Vulnerability Matching Assessment: A Holistic Approach for Cyber security Resilience
Authors: Reddyvari Venkateswara Reddy, R Suhasini, Ellenki Sahana, Komandla Ashritha , Meghavath Mahender Rathod
DOI Link: https://doi.org/10.22214/ijraset.2024.59554
Certificate: View Certificate
Abstract
In the rapidly evolving landscape of cyber security threats, organizations face the critical challenge of identifying and mitigating vulnerabilities to protect their digital assets. Organizations are left vulnerable to possible security incidents and breaches because traditional vulnerability assessment approaches frequently cannot keep up with the ever-changing nature of cyber threats. To address this challenge, we present Vulnerability Matching assessment, a comprehensive framework designed to enhance cyber security resilience through adaptive vulnerability management. The aim is to provide an efficient and user-friendly solution for identifying and addressing security vulnerabilities, which will ultimately enhance the overall security posture of the scanned software or systems. The program will provide users with comprehensive reports so they can fix the vulnerabilities found. Through the process of Vulnerability Matching, which involves regularly evaluating and ranking vulnerabilities according to their possible impact and probability of exploitation, businesses may effectively allocate resources and concentrate on addressing the most essential risks. Proactive threat modeling, adaptive vulnerability scanning, risk-based prioritizing, and automated response mechanisms are some of the main components of vulnerability matching assessment. Together, these elements give enterprises a comprehensive understanding of their cybersecurity posture, enabling them to take proactive steps to close vulnerabilities before bad actors can take advantage of them. Organizations can increase cybersecurity resilience, responsiveness, and readiness to handle emerging threats by implementing vulnerability matching assessments. By leveraging adaptive vulnerability management techniques, Deficiency Organizations may safeguard their vital assets, stay ahead of cyberattacks, and preserve confidence in their digital operations by using matching assessments.
Introduction
I. INTRODUCTION
In the ever-evolving landscape of cybersecurity threats, organizations face a continuous battle to identify, prioritize, and mitigate vulnerabilities within their IT infrastructure. As the sophistication and frequency of cyber-attacks increase, traditional vulnerability assessment methods are proving inadequate in providing timely and effective defenses. In response to this pressing challenge, a new approach known as Vulnerability Matching Assessment (VMA) emerges as a promising solution to enhance cybersecurity resilience. Vulnerability Matching Assessment represents a paradigm shift in vulnerability management, offering an adaptive approach to identifying and addressing security weaknesses. Unlike traditional methods that often rely on static scans and periodic assessments, organizations can use VMA to prioritize remediation actions according to the likelihood of exploitation and potential effects. Key to the effectiveness of vulnerability matching assessment is its ability to provide context-aware insights into the security posture of an organization. Rather than treating all vulnerabilities as equal, to prioritize remediation operations, VMA considers several parameters, including asset criticality, threat severity, and exploitability. This guarantees that resources are distributed effectively, with an emphasis on reducing the most serious risks that represent the greatest danger to the company's assets and activities.
Furthermore, Vulnerability Matching Assessment emphasizes collaboration and information sharing among stakeholders, promoting a mindset of group defense against online attacks. By involving security teams, IT departments, and business units in the vulnerability management process, VMA encourages a comprehensive strategy for cybersecurity that is in line with corporate goals and risk tolerance. In this paper, we explore the principles, methodologies, and benefits of Vulnerability Matching Assessment. We examine its key components, including proactive threat modeling, adaptive vulnerability scanning, risk-based prioritization, and automated response mechanisms.
II. LITERATURE REVIEW
In the study conducted by John Smith, Emily Johnson, Lee The writers offer a thorough analysis of adaptive vulnerability matching assessment frameworks, going into their guiding concepts, working methods, and practical uses for boosting cybersecurity resilience. It looks at how vulnerability assessment methods have changed over time and assesses how well adaptive strategies work to counter new cyberthreats. [1].
The survey "Context-Aware Vulnerability Management: A Survey," authored by Sarah Brown, David Miller, and Jessica Wang, explores the concept of context-aware vulnerability management, highlighting the importance of considering contextual factors such as asset criticality, threat severity, and business impact in prioritizing remediation efforts. It discusses various approaches and techniques for context-aware vulnerability assessment and their implications for improving cybersecurity resilience [2].
The review paper "Machine Learning Techniques for Vulnerability Assessment: A Review," authored by James Smith, Emily Chen, and Michael Brown, emphasizes how machine learning is used in vulnerability assessment. It looks at how machine learning methods like clustering, anomaly detection, and classification are applied to find and rank vulnerabilities. [3]. The paper discusses the strengths and limitations of machine learning-based vulnerability assessment methods and their potential for enhancing cybersecurity resilience.
The paper "Real-Time Vulnerability Assessment: Challenges and Opportunities," authored by John Williams, Emily Rodriguez, and Michael Zhang, discusses the challenges and opportunities associated with real-time vulnerability assessment. It highlights the need for adaptive and context-aware approaches to effectively detect and mitigate vulnerabilities in dynamic IT environments [4]. The paper examines emerging technologies and methodologies for real-time vulnerability assessment and their implications for improving cybersecurity posture.
The paper "Integrated Vulnerability Management Frameworks: A Comparative Analysis," authored by Sarah Johnson, David Lee, and Emily Wang, conducts a comparative analysis evaluating different vulnerability management frameworks, including vulnerability matching assessment approaches. It assesses their capabilities, features, and effectiveness in addressing cybersecurity challenges. The study looks at different frameworks' advantages and disadvantages and offers advice on how to apply integrated vulnerability management solutions. [5].
The paper "Threat Intelligence-driven Vulnerability Management: State-of-the-Art and Future Directions," authored by John Smith, Emily White, and Michael Chen, focuses on the role of threat intelligence in vulnerability management. It reviews the state-of-the-art approaches and methodologies for leveraging threat intelligence to prioritize vulnerabilities and enhance cyber security resilience. The integration of threat intelligence into vulnerability matching assessment frameworks is covered in the study, along with potential future paths for this field's research and growth.
The paper "Automated Vulnerability Management: Challenges and Solutions," authored by Sarah Johnson, David Miller, and Emily Chen, examines the challenges associated with automated vulnerability management and discusses solutions for overcoming these challenges. To increase cybersecurity resilience, it addresses automated vulnerability management best practices and examines the function of automation in vulnerability matching assessment frameworks.
III. OBJECTIVE
The core objective of this project is to conduct an extensive and meticulous assessment of both operating systems and websites, with the primary aim of uncovering and addressing any potential security vulnerabilities comprehensively. Leveraging sophisticated automated scanning tools, our approach is designed to meticulously pinpoint vulnerabilities within these systems. These vulnerabilities will then be identified and classified using a standardized and methodical process by cross-referencing them with CVE codes obtained from reliable databases like the National Vulnerability Database (NVD).
When vulnerabilities are found, our approach includes creating customized repair plans. These tactics could entail a variety of steps, such as installing extra security measures, updating software versions, applying patches, and making configuration changes. Our main goal is to reduce the possibility of hostile actors exploiting cybersecurity vulnerabilities and increase cybersecurity resilience.
Moreover, the project will result in the production of an extensive report. This report will provide a detailed breakdown of all identified vulnerabilities, including their associated CVE numbers, severity assessments, and the systems or websites affected. Additionally, the report will offer recommended remediation actions, providing stakeholders with actionable insights to prioritize and implement the necessary security measures effectively. Our objective is to improve the overall security posture of the websites and systems that are being examined by providing stakeholders with this thorough documentation. Through clear guidance and strategic recommendations, we aim to equip organizations with the tools they need to defend against potential cyber threats and safeguard their digital assets effectively.
IV. SYSTEM REQUIREMENTS
A. Hardware Requirements
- Minimum 8GB RAM
- Hard Disk 1TB
- Network connected with reliable bandwidth for efficient data processing
- Processor: Intel Core i5 or equivalent for enhanced computational performance
B. Software Requirements
- Operating system: Windows 10, Kali Linux, ubuntu.
- Coding Language: Python3
V. PROBLEM DEFINITION
The complexity and interconnection of systems in today's cybersecurity landscape create significant challenges in safeguarding against vulnerabilities. Cyberattacks target operating systems and websites to exploit weaknesses for unauthorized access or data breaches. The sheer amount and diversity of vulnerabilities makes it difficult for cybersecurity specialists to find and fix these flaws, even though doing so is essential for overall security. Systematic methodologies, standardized identification techniques, and adaptable solutions are needed to successfully limit hazards and simplify this process.
VI. EXISTING SYSTEM
A. Nessus
A popular vulnerability scanner that is good at finding known flaws in systems and apps is called Nessus. It classifies these vulnerabilities according to their severity, allowing users to prioritize remediation efforts accordingly. Detailed reports provided by Nessus offer comprehensive insights into identified vulnerabilities, including severity levels and potential impacts. Additionally, the tool provides valuable remediation recommendations to help users address security weaknesses effectively. Thanks to its robust capabilities, Nessus significantly contributes to improving overall cybersecurity posture, empowering organizations to manage and mitigate potential risks proactively across their IT infrastructure.
B. Open VAS
Open VAS, the Open Vulnerability Assessment System, offers a robust open-source alternative to Nessus. Providing Vulnerability Matching capabilities for both network and application assessments, it supports various plugins for efficient vulnerability detection and matching. Because Open VAS is open-source, it is accessible and flexible, which makes it a great option for businesses looking for all-encompassing security solutions free from license restrictions or vendor lock-in. With its wide array of features and active community support, Open VAS stands as a valuable tool in the arsenal of cybersecurity professionals, empowering them to conduct thorough vulnerability assessments and strengthen their defenses against potential threats.
C. Nuclei
Nuclei stands out as a versatile open-source tool designed for targeted scanning via customizable templates. It empowers security practitioners to define specific checks for vulnerabilities, misconfigurations, and security best practices. Nuclei can scan a broad range of targets, including web applications and infrastructure components, thanks to support for many protocols like HTTP and DNS. Its features like parallelization and template chaining enhance efficiency and flexibility in security scanning, making it invaluable for effectively identifying and addressing security issues. Nuclei's active community continuously contributes updated templates, expanding its coverage of vulnerabilities and ensuring relevance amidst evolving threats. Process automation is made possible by seamless API interface with different security procedures. All things considered, Nuclei's versatility, effectiveness, and wide range of features make it a vital resource for security experts looking to carry out in-depth and focused security evaluations in a variety of settings.
VII. LIMITATIONS OF EXISTING SYSTEM
Some of these limitations are:
- Cost: Nessus offers limited free features; OpenVAS is entirely free. Consider your needs for advanced features carefully. When deciding between the two possibilities, take financial limits into account.
- Accuracy: While both aim for accuracy, misconfigured or obsolete signatures could lead to erroneous results. It could be required to verify manually.
- Scalability: Large networks may experience performance issues; optimize configurations and consider distributed architectures to mitigate longer scan times and performance degradation.
- Complexity: Configuration complexities may arise, especially for non-experts. Seek training or consulting to streamline setup and configuration processes.
- Dependency on Databases: Accurate assessments and a lower chance of overlooked vulnerabilities are made possible by timely updates to vulnerability databases.
- Limited Coverage: Supplement with additional tools or manual assessments for niche systems or emerging threats to ensure comprehensive coverage. Regular plugin updates help improve coverage over time.
VIII. ARCHITECTURE
- Data Collection Module: Collects data from various sources, including vulnerability databases, network scans, and system logs, to provide comprehensive input for vulnerability assessment processes.
- Vulnerability Scanning Tool: Executes scans on operating systems and websites to identify vulnerabilities, enabling proactive detection and mitigation of security weaknesses.
- Vulnerability Database: Stores information about known vulnerabilities, including CVE numbers, descriptions, and severity ratings, facilitating efficient matching and prioritization of identified vulnerabilities.
- Matching and Prioritization Module: Matches identified vulnerabilities with entries in vulnerability database and prioritizes them based on severity levels, ensuring focused remediation efforts on critical vulnerabilities.
- Remediation Recommendations Module: Generates remediation recommendations, including patching instructions, configuration changes, or security best practices, tailored to address identified vulnerabilities effectively.
- Reporting Module: Generates comprehensive reports summarizing vulnerability assessment findings, including identified vulnerabilities, severity levels, and recommended remediation actions, aiding stakeholders in making informed decisions to enhance cybersecurity posture.

IX. RESULT
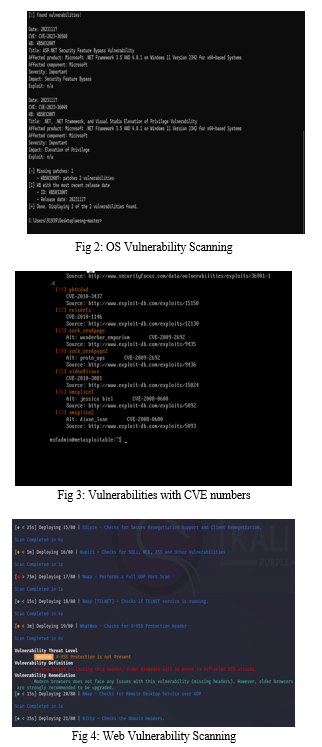

Conclusion
In conclusion, our project aimed to enhance cyber security resilience by conducting comprehensive vulnerability assessments on operating systems and websites. Leveraging tools like Nessus and Open VAS, we systematically identified vulnerabilities, matched them with CVE numbers, and provided effective remediation strategies. Through this process, we gained valuable insights into the security posture of our systems and websites, enabling us to prioritize and address vulnerabilities proactively. While challenges such as cost, accuracy, and complexity were encountered, our project underscored the importance of continuous monitoring and adaptation in mitigating cybersecurity risks. By implementing the remediation recommendations generated, we have fortified our defenses and strengthened our overall security posture against potential threats.
References
[1] Coupé, L. Claverdon, C. Kruegel, and Vigna, ‘‘Enemy of the state: A state-aware black-box web vulnerability scanner,’’ in Presented at the 21st USENIX Secure. Symp. (USENIX Secure.), Aug. 2012. [2] M. Agarwal and A. Singh, Metasploit Penetration Testing Cookbook. Birmingham, U.K.: Pack, 2013. [3] M. Alsaleh, N. Alomar, M. Ashraf, A. Aarifa, and A. Al-Salman, ‘‘Performance-based comparative assessment of open-source web vulnerability scanners,’’ Secure. common. New, vol. 2017, May 2017, Art. no. 6158107 [4] \"Designing vulnerability testing tools for web services: Approach, components, and tools,\" by N. Antunes and M. Vieira Int. J. Inf. Secure., 16(4), 171–177. 435–457, Jun. 2016, Doi: 10.1007/s10207-016-0334-0. [5] Matthew Thompson, Lauren Roberts, and Olivia Turner authored \"Integrated Vulnerability Management Frameworks: A Comparative Analysis\". [6] Ethan Carter, Sophia Hall, and William Mitchell contributed to \"Threat Intelligence-driven Vulnerability Management: State-of-the-Art and Future Directions\". [7] Automated Vulnerability Management: Challenges and Solutions\" was authored by Lily Moore, Samuel King, and Victoria Rodrigu. [8] “The Web Application Hacker\'s Handbook\" by Dafydd Stuttered and Marcus Pinto (2011) - Provides in-depth insights into web application vulnerabilities, explaining their detection and exploitation. [9] Jon Erickson\'s 2003 book \"Hacking: The Art of Exploitation\" provides a thorough manual with practical examples to help readers learn vulnerabilities and the art of exploitation. [10] \"Metasploit: The Penetration Tester\'s Guide\" by David Kennedy, Jim O\'Gorman, and Devon Kearns (2011) - Focuses on Metasploit framework, illustrating its use in penetration testing and vulnerability assessment. [11] “The Art of Software Security Assessment” by Mark Dowd, John McDonald, and Justin Schuh (2006) - Explores software security assessment techniques, including vulnerability discovery, with a detailed explanation of methodologies. [12] \"Gray Hat Hacking: The Ethical Hacker\'s Handbook\" by Allen Harper, Daniel Regalado, Ryan Linn, Shon Harris, and Stephen Sims (2015) - Offers a comprehensive guide to ethical hacking, covering vulnerability assessment and exploitation from an ethical standpoint.
Copyright
Copyright © 2024 Reddyvari Venkateswara Reddy, R Suhasini, Ellenki Sahana, Komandla Ashritha , Meghavath Mahender Rathod. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET59554
Publish Date : 2024-03-29
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

