Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Human Eye Ball Gazing and Face Based Ultra Digital Security System using AI
Authors: Dr. R. Divya, Priyadharshini T, Abarnaa T, Susmitha S
DOI Link: https://doi.org/10.22214/ijraset.2024.61295
Certificate: View Certificate
Abstract
The \"Eye Ball Gazing and Face-Based Ultra Digital Security System\" invents a remarkable surveillance mechanism by fusing recognition of faces with eye ball movement monitoring. It gathers and safely retains people\'s unique visages and eyeball peering patterns upon participation. It sets up an authentication system with multiple factors that bolsters security and cuts the chance of unlicensed entry if access is requested. This novel solution to the continually evolving requirements of technological safety distinguishes real-time eye-ball peering information with recorded sequences, besides ensuring human facial features. Sophisticated facial identification and eye motion monitoring techniques are put together in the \"Eye Ball Gazing and Face-Based Ultra Digital Security System\" to produce an effective validation structure in the realm of digital safety. When a person signs up, the tool confidentially saves distinct facial traits and eyeball staring movements. Upon access request, the documented data is cross-referenced with actual time eyeball gazing sequences, and recognition of facial features is utilized to confirm ID in addition. The simultaneous use of both of these methods of login minimizes the possibility of inappropriate entry and improves confidentiality, which requires a multi-step verification procedure. In the current age of technology, this ground-breaking solution guarantees top-notch security and accessibility control.
Introduction
I. INTRODUCTION
Our dependence on virtual platforms is now pervasive in an era where advancement in technology is moving at an unstoppable pace, influencing every aspect of our everyday lives. The need to safeguard our electronically stored resources from cunning attacks is more crucial than ever before when we cross this technological terrain. Under these circumstances, the "Eye Ball Gazing and Face-Based Ultra Digital Security System" stands out as a trailblazing option that combines cutting-edge profile detection and optic tracking technology into a potent barrier for assaults and illegal access. With the intent of transforming the field of cyber privacy, this thorough analysis sets out on a journey through the complexities of this novel protection model. This cutting-edge technique's actual time verification processes, the complexities of recognizing facial features, the procedure for registering, and the operation of retinal movement monitoring will all be evaluated in detail as we take a detailed look at the digital terrain in eight distinct sections. The expedition begins with a proactive investigation of its potential effects, especially regarding its amalgamation with the Internet of Things (IoT) and its worldwide effect on safety protocols and statutory frameworks.
II. LITERATURE SURVEY
A. A Generic Algorithm for Controlling an Eyeball-based Cursor System
In this study, a particular framework for communicating between humans and computers is put forward. A platform requires a few types of input sources to collect data from users. However, a few individuals cannot use computers because they suffer from certain illnesses or conditions. People with sight challenges or limitations will greatly benefit from being able to use computers with their eyes. Furthermore, this kind of management will lessen the necessity for outside help when using the system. This is going to be particularly beneficial for the person who does not have hands and is able to function only by moving their gaze. The motion of the pointer is closely associated with the nucleus of the pupil. The machine's pointer is moved by means of a digital gadget. The Haar cascade procedure and OpenCV modules are applied in this suggested approach to recognize gaze activities.
B. Eye-Controlled Wheelchair
A motorized wheelchair is a type of transportation aid for people with chronic illnesses or mild to serious impairments. Many quadriplegic and amyotrophic lateral sclerosis sufferers rely on others to push their mobility devices for them. While wheelchairs that are driven by power or by hand are examples of helpful locomotion tools, these are not the best choices for everyone with physical constraints.
With the goal of helping individuals who have impairments live lives of fulfillment and completely engage in their surrounding societies, this initiative will use technological innovations to let them use their mobility devices autonomously. The hands-free wheelchair that is being developed operates through a gaze control mechanism. Rather than using hands to operate the wheeled device, ocular gestures are utilized instead. For a number of reasons, this study used an IR visual tracking device. A device that consists of an impediment scanner, a motorized wheelchair, and a head-mounted eye tracker has been put together and evaluated in order to accomplish this objective.
C. An IOT Driven Eyeball and Gesture-Controlled Smart Wheelchair System for Disabled Person
By providing enough assistance through modern technological advances, the field of automated houses has developed with the aim of regaining the ability of elderly individuals, physically impaired persons, and those with restricted access to do important daily tasks. Making sure a smart wheelchair works correctly and properly is one of the harder parts of its development. People with disabilities can move around indoors and carry out routine duties effortlessly with the help of smart mobility devices. With this technology, patients may feel more liberated and have little or no difficulty driving their wheelchairs because autonomous wheelchair control—which can be accessed by ocular movement—replaces manual wheelchair operation. A continuous image is captured with the use of an imaging device in order to establish the position of the pupil in the retina. This image goes through additional processing using several image approaches.
D. Voice Controlled and Eye Ball Movement Operated Wheelchair
Remedial assistive devices for mobility are essential for people with impairments in their bodies. Significant endeavors are being made to build human-interfacing machines (HMIs) that can communicate with biofeedback in order to control digital motion-assisting devices. The fundamental problem for people with severe disabilities is that bio-signals are transmitted to an HMI by the action of components of the body and exact commands. In order to achieve the goal of implementing a staircase climbing mechanism in a mobility device for a physically impaired population, this study presents a signal-driven mechanism that uses retinal motion as well as voice detection. There are three components to the system: Optical motility is first detected using optical data. Recognition of voices by RF is the second. Third, the wheelchair incorporates all three processes through the use of the rocker-bogie technique.
E. Intelligent Eye Ball Movement Controlled Wheelchair
The wheelchairs are very important for individuals who are physically challenged. Mobility devices that are presently supplied are operated by a joystick-type system for control. These powered wheelchairs only allow the user to go in a particular direction. For those who are entirely paralyzed—those who are unable to raise their hands—using this kind of equipment is quite challenging. Under these conditions, their gaze movements can help them stride in the right direction. The goal of this project is to construct a smart mobility device that the user can operate with just their vision. Eye tracking is possible by utilizing MATLAB to process a picture of an eye. Using a camera, the individual's visage is constantly captured. MATLAB is utilized for the image processing procedure on the acquired photos. The microcontroller will get the following commands based on the direction of the lens in the selected pattern: Consequently, the directions in which the wheels start to move are controlled by the retina's gestures.
III. PROBLEM STATEMENT
The world of technology presents endless potential yet additionally brings lots of difficulties. Formerly the cornerstones of privacy, typical methods for authentication are becoming ever more susceptible to the resourcefulness of cybercriminals. The mainstay of previous encryption technologies, secure passwords, have recently become prone to hacking, and fingerprinting methods have downsides in addition. The methods by which we protect confidential data must change substantially as our cyber network evolves and the channels of susceptibility do the same. The "Eye Ball Gazing and Face-Based Ultra Digital Security System" is an attempt to tackle this compelling demand for an increasingly efficient and robust protection framework.
A. Necessity
The rising complexity of cyber assaults demands that our privacy protocols also expand in parallel. Classic approaches, which commonly depend on only one validation element, are vulnerable to diligent opponents. By integrating the individuality of eye ball staring behaviours with the characteristics of the face, the "Eye Ball Gazing and Face-Based Ultra Digital Security System" employs a dual-factor validation technique to mitigate the problem.
In a time when the importance of digital safety is now even greater, this multilevel protection considerably increases the obstacles to unwanted access and offers an effective way.
IV. PROPOSED SYSTEM
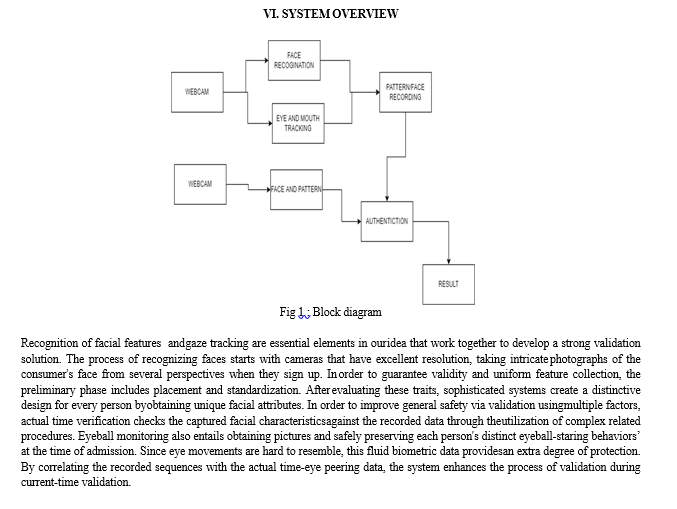
Modern visage recognition and gaze ball tracking systems are implemented in the submitted "Eye Ball Gazing and Face-Based Ultra Digital Security System" in order to offer a strong foundation for secure digital identification. The tool precisely collects and records distinctive features of the face and eyeball staring behaviours at the time the user logs in. A multi-factor identification system is implemented when permission is requested. Actual-time eye movement info is checked with recorded patterns, and recognition of facial features is applied to validate an ID. By combining image detection and technology for tracking gazes in an intuitive way, this novel solution promises to greatly reduce the likelihood of uninvited entry while providing sophisticated accessibility and safety management in the cybersphere. The "Eye Ball Gazing and Face-Based Ultra Digital Security System" gives a unique resolution by effortlessly blending detection of faces and eye ball mobility observing systems in an effort to tackle the downsides of existing protection frameworks. The method generates a multiple-factor security process during registration by effectively and securely retaining each person's distinct eyeball peering movements and facial attributes. In addition to improving protection by limiting the possibility of illicit access, the unique mix of biometric elements additionally delivers an easy-to-use registration system that uses cutting-edge technology to guarantee the precise collection and safe preservation of fingerprint information. By overcoming the shortcomings of current approaches while providing enhanced levels of safety from constantly changing security threats, the suggested fix is an important step forward in online privacy.
A. Advantages of Proposed System
This privacy concept is based on the combination of two advanced techniques: recognition of visages and eye ball mobility observation. The precise profile detection strategies and the accuracy of eyeball movement monitoring methods work together, resulting in a potent combination that exceeds the bounds of typical methods. By providing rapid and exact validation as well as decreasing the possibility of unwelcome entry, the real-time time verification procedure successfully brings together the above techniques. The technology builds an effective barrier by having multiple forms of verification, residing on top of the latest developments in a continually shifting cyber field. The "Eye Ball Gazing and Face-Based Ultra Digital Security System" is a prime example of the inventive spirit advancing online safety and durability rather than simply a means of protection.
V. METHODOLOGY
The "Eye Ball Gazing and Face-Based Ultra Digital Security System" is being carried out via an elaborate procedure that includes multiple critical phases, all of which are vital to the program's emergence, implementation, and perpetual enhancement.
A. Requirement Analysis
To comprehend the precise requirements and problems that the framework seeks to resolve, do a thorough investigation of the current condition of digital safety. Determine customer demands, structure features, and efficacy by communicating with all parties involved, including safety professionals as well as potential users of the system.
B. System Design
Create an elaborate framework that describes how facial identification and eye movement monitoring will be combined. To assure an uninterrupted and customer-friendly registration and validation process, specify the data flow, front-ends, and database processes.
C. Data Collection and Preprocessing
When acquiring biometric details during the process of registration, provide an arrangement that is both reliable and legal. Both the reliability and precision of the personally identifiable information that is obtained can be improved by deploying prepping procedures.
D. Feature Extraction and Representation
To properly record unique sequences, use sophisticated strategies to derive pertinent elements from the visage and ocular motion information. Provide techniques for describing these attributes in an arrangement that can be assessed in real time during verification.
E. Algorithm Development
Assure precision and efficacy by employing cutting-edge techniques for identifying faces and eyeball movement monitoring. Strengthen protection and system functionality by tweaking the parameters involved.
F. Integration and Testing
Construct a single framework that combines the recognition of facial features with eyeball movement surveillance in an intuitive way by using the existing computational methods. To verify its precision, dependability, and resilience against various threats—such as faking attempts—it is carried out via analysis.
G. User Enrollment Process
Develop and set up an intuitive signup procedure that walks clients through the process of obtaining and safely saving their face characteristics and eyeball staring trends. Also, include methods for user input to assure a satisfying experience.
H. Real-Time Authentication Mechanism
Provide an on-demand identification system that validates identity through matching facial traits and eyeball-staring information with pre-stored sequences. Use dynamic methods that take client actions and external factors into consideration.

Conclusion
To sum up, the \"Eye Ball Gazing and Face-Based Ultra Digital Security System\" is a revolutionary approach to cybersecurity. The intricate operation of the ocular tracking and facial identification components highlights the intricacy and cooperation inherent in our approach. In order to guarantee accurate customer verification at real-time validation, visage recognition, with its tedious recording and subsequent evaluation of important visual traits, is a component of multiple-factor security systems. The method for verification is further strengthened by the inclusion of an extra level of intricacy brought about by eye ball monitoring, which records and safely retains changing gaze movements. The combined use of these methods overcomes the drawbacks of conventional methods of login, offering enhanced security along with a smooth and convenient registration and entry application process. Because the system is flexible and takes user choices and shifts in the environment into account, it is more effective in a variety of instances. The intricate operation of these elements indicates the groundbreaking capabilities of the \"Eye Ball Gazing and Face-Based Ultra Digital Security System,\" given that we are at the junction of both safety and technology. With its versatility and multi-factor strategy, this distinctive solution not only establishes fresh norms for verification but also predicts possible future problems.
References
[1] Dhanasekar J,Guru Aravindh K B,Kiren A S,Faizal Ahamath A,\"System Cursor Control Using Human Eyeball Movement\",2023 3rd International Conference on Advance Computing and Innovative Technologies in Engineering (ICACITE) [2] Praveena Narayanan,Sri Harsha. N,Sai Rupesh. G,Sunil Kumar Redy,Rupesh. S,Yeswanth. M,\"A Generic Algorithm for Controlling an Eyeball-based Cursor System\",2022 International Conference on Automation Computing and Renewable Systems (ICACRS) [3] Marwa Tharwat,Ghada Shalabi,Leena Saleh,Nora Badawoud,Raghad Alfalati,\"Eye-Controlled Wheelchair\",2022 5th International Conference on Computing and Informatics (ICCI) [4] Rani.V Udaya,S Poojasree,\"An IOT Driven Eyeball And Gesture-Controlled Smart Wheelchair System for Disabled Person\",2022 8th International Conference on Advanced Computing and Communication Systems (ICACCS) [5] Maheswari R.,Vignesh S.,Rakesh Kumar M.,Venkatesh T.M.,Sundar R.,Jose Anand A.,\"Voice Control and Eyeball Movement Operated Wheelchair\",2022 International Conference on Edge Computing and Applications (ICECAA) [6] Suma T,Divyaraj G N,Archana M,Veda N,Rakshitha K S,\"Women safety by real-time eye tracking for password testimony\",2022 International Interdisciplinary Humanitarian Conference for Sustainability (IIHC). [7] \"Intelligent Eyeball Movement Controlled Wheelchair\",2021 International Conference on Advancements in Electrical Electronics Communication Computing and Automation (ICAECA) [8] Shalini Shinde,Sandeep Kumar,Prashant Johri,\"A Review: Eye Tracking Interface with Embedded System & IOT\",2018 International Conference on Computing Power and Communication Technologies (GUCON) [9] Bharat Thakur,Kush Kulshrestha,\"Eye controlled electric wheelchair\",2014 IEEE International Conference on Computational Intelligence and Computing Research
Copyright
Copyright © 2024 Dr. R. Divya, Priyadharshini T, Abarnaa T, Susmitha S. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET61295
Publish Date : 2024-04-29
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online