Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Hybrid Encryption using LSB steganography and RSA
Authors: Vineela Reddy M, Anudeep Reddy G
DOI Link: https://doi.org/10.22214/ijraset.2023.55617
Certificate: View Certificate
Abstract
In the present world of communication, computers and the internet are the major media that connects different parts of the world as one global virtual world. So we can easily exchange lots of information within seconds of time, but the confidential data that needs to be transferred should be kept confidential. Thus, in order to aid this, we have proposed a new encryption technique by combining Image steganography (LSB) with the cryptographic RSA algorithm for providing more security to our data as well as imperceptibility. The expected outcome would be a properly secure combination of encryption models that uses steganography to hide the message content in a cover image, and also encrypts the message using the cryptographic algorithm, as an additional security layer, in case the content was retrieved from the cover image.
Introduction
I. INTRODUCTION
The basic need of every growing area in today’s world is communication. This exchange of information must be secure and safe. In order to transport and share information in our daily lives, we use a variety of unsafe channels, including the telephone and the internet. Two techniques that are used to share information covertly are steganography and cryptography. A communication can be modified using cryptography such that it is protected by an encryption key that is only known to the sender and recipient. In contrast, steganography conceals the secret message in a cover image so that no intermediary can tell whether a message is hidden in the information being transferred. In cryptography, it is always obvious to an intermediary that the communication is in an encrypted form. The recipient is then given the cover image with the hidden message. The recipient uses the steganography algorithm to decode the message. It is a difficult technique that will require us to integrate two technologies: the RSA cryptographic method on the one hand, and the LSB steganography algorithm on the other. Our research has been concentrated on developing a method for securely transferring and sharing critical data. To prevent competitors or bogus parties from learning information about their company, all reputable businesses always encrypt data before transferring it over the internet. We have developed a secure steganography technique using LSB and RSA that is much more secure than many other systems used to covertly convey data.
II. LITERATURE REVIEW
Applications requiring high-volume embedding with robustness against certain statistical attacks have used the proposed approach. The current approach makes an effort to pinpoint what makes an effective data hiding algorithm. Additionally, it is meant to support cryptography and steganography rather than to replace them [1]. The embedding capacity grows when a message is encrypted and concealed using an LSB steganographic approach, allowing us to conceal vast amounts of data. Additionally, the technique fits the criteria for data concealment, including those for capacity, security, and robustness. The generated stego-image can be transferred covertly while yet maintaining confidentiality. Furthermore, even if an attacker were to defeat the steganographic technique to detect the message from the stego- object, Applications requiring high-volume embedding with robustness against certain statistical attacks have used the proposed approach. The current approach makes an effort to pinpoint what makes an effective data hiding algorithm. Additionally, it is meant to support cryptography and steganography rather than to replace them [1]. The embedding capacity grows when a message is encrypted and concealed using an LSB steganographic approach, allowing us to conceal vast amounts of data. Additionally, the technique fits the criteria for data concealment, including those for capacity, security, and robustness. The generated stego-image can be transferred covertly while yet maintaining confidentiality.
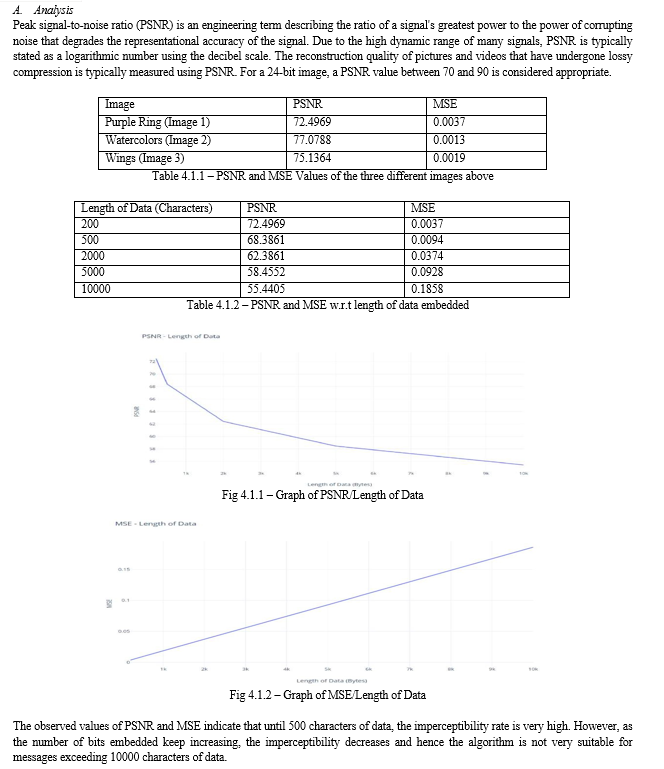
LSB based steganography embed the text message in LSB of cover image. The text message is hidden via DCT- based steganography in the LSB of the DC coefficients. This study applies LSB- and DCT-based steganography and computes the PSNR ratio. The peak signal to noise ratio (PSNR), expressed in decibels, compares two pictures. This ratio is used to compare the two photos' quality. Images are of higher quality if the PSNR ratio is high.
The PSNR ratio used to compare LSB-based and DCT-based stego photos reveals that the DCT-based steganography scheme has a higher PSNR ratio than the LSB-based steganography scheme for all types of images (Grayscale as well as Colour). DCT based steganography scheme works perfectly with minimal distortion of the image quality as compared to LSB based steganography scheme.[2] Despite the fact that less secret data may be concealed with this method than with an LSB-based steganography scheme, DCT-based steganography is still advised since it causes the least amount of image quality distortion.
The purpose of this work is to evaluate RSA, analyse its advantages and disadvantages, and suggest fresh remedies to address the disadvantage [3]. One of the most effective cryptographic methods now in use for ensuring secure network communication is RSA (Rivest, Shamir, and Adleman). Even though RSA is now the most popular cryptographic method, it has some drawbacks that must be taken into account if RSA is to remain the best, and work must be done to make RSA quantum resistant. Studies on quantum encryption techniques that are resistant to quantum computers are more important than ever because they will soon replace the existing encryption systems. Comparisons between the RSA and ECC ciphers show that the ECC has significantly lower overheads than RSA [4]. Due to its capacity to offer the same level of security as RSA while utilizing smaller keys, the ECC has been demonstrated to have numerous advantages. Its lack of maturity, however, may even mask its beauty because mathematicians felt that not enough research had been done on ECDLP. Additionally, we thought that even if both systems are legitimate, RSA is now superior to ECC because it is more dependable and its security can be trusted more. However, ECC's future appears more promising than RSA's because modern applications (such as smart cards, pagers, and mobile phones) cannot support the overheads that RSA introduces.
III. METHODOLOGY
A. Overall Architecture
The algorithm's fundamental structure is relatively straightforward. A text is entered by the user and transmitted to the recipient. The text is then encrypted and embedded in an image using LSB steganography. The image is transferred to the recipient, who decrypts the embedded bits to read the original message.
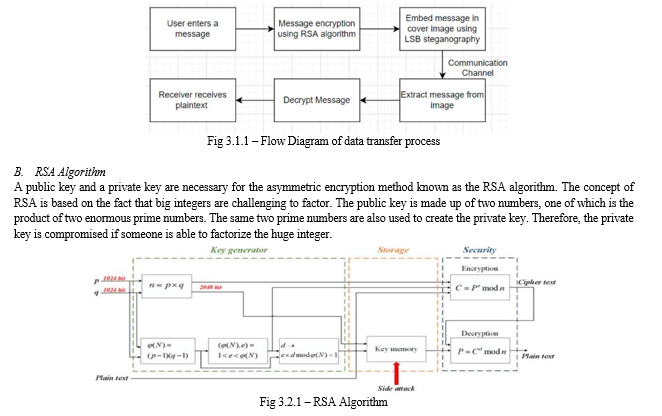
- Select two large prime numbers, p and q.
- Multiply these numbers to find n = p x q, where n is called the modulus for encryption and decryption.
- Choose a number e less than n, such that n is relatively prime to (p - 1) x (q -1). It means that e and (p -1) x (q - 1) have no common factor except 1. Choose "e" such that 1<e < φ (n), e is prime to φ (n), gcd(e,d(n)) =1
- If n = p x q, then the public key is <e, n>. A plaintext message m is encrypted using public key <e, n>. To find ciphertext from the plain text following formula is used to get ciphertext C. C = me mod n, Here, m must be less than n. A larger message (>n) is treated as a concatenation of messages, each of which is encrypted separately.
- To determine the private key, we use the following formula to calculate the d such that: De mod {(p - 1) x (q - 1)} = 1 or De mod φ (n) = 1
- The private key is <d, n>. A ciphertext message c is decrypted using private key <d, n>. To calculate plain text m from the ciphertext c following formula is used to get plain text m. m = cd mod n .
C. LSB Steganography
At its foundation, the idea that underlies image-based steganography is extremely straightforward yet incredibly adaptable. The discovery that an image's content, primarily the colours and visual features that humans see, is fundamentally defined by the digital data that makes up the image is at the core of this technique. In its purest form, an image is a mosaic of pixels, each of which contributes significantly to the final image. These pixels typically have three different values, which correspond to the red, green, and blue colours. The numerous hues and tints that give an image life are created when these RGB values are mixed in different ratios. The essence of image-based steganography lies in the recognition of this fundamental truth: that images are, at their core, composed of pixels. This realization opens up a world of possibilities for concealing and retrieving information within images. By subtly manipulating the RGB values of individual pixels, one can embed hidden messages, data, or even entire files within the seemingly innocuous facade of an image.
- Encode the Data: Through the use of ASCII values, every byte of data is transformed into its 8-bit binary equivalent. Now a set of three pixels with a total of 9 values are read from left to right. Binary data is stored in the first 8 values. If 1 happens, the value becomes odd; if 0 occurs, it becomes even.
- Decode the Data: Three pixels are read at a time during decoding, and when the last value is odd, the message is finished. The same encoding technique can be used to retrieve the binary data that each set of three pixels contains. The binary bit is 1 if the value is odd and 0 otherwise


Conclusion
The study that has been provided thus far highlights the efficiency and synergy attained by combining cryptography with steganography. In particular, data protection and covert communication are greatly improved by this potent combination of security approaches. One of the main benefits is the retention of imperceptibility, which ensures that the concealed data stays essentially invisible to the human eye and concealed inside the host data. In addition, because of the encryption used, even if this composite data were to get up in the wrong hands, it would still provide a double layer of security. The RSA method was selected as the encryption technique for this particular project, demonstrating its dependability and durability in securing sensitive information. However, there are many exciting possibilities for investigation and improvement on the horizon for future study in this field. Comparing the implemented RSA algorithm against other cryptographic methods is one approach. This comparative analysis can be used to determine which algorithm is best for a certain application. Choosing the best algorithm can greatly improve the system\'s overall security and performance because each algorithm has specific strengths and drawbacks. For instance, when comparing several cryptographic methods, one may look at the speed, key length, and attack resistance. The creation of a user-friendly interface is another intriguing possibility for future effort. This could be a mobile app or a web-based GUI made to enable users to connect conveniently and securely in the real world. Such a method would make secure communication available to non-technical people and spread the advantages of cryptography and steganography to a larger audience. This user-centric approach is vital because it fills the gap between effective encryption methods and everyday usability. Such an application has a significant potential impact. It let people, groups, and companies to transmit private information without worrying about it being intercepted. As a result, personal privacy is improved, and cybersecurity is strengthened in a time when cyberthreats are pervasive. Furthermore, being able to interact securely using an intuitive interface can have significant effects in industries like healthcare, banking, and law where secrecy is crucial. In conclusion, combining steganography and encryption has proven to be a successful method for protecting data while keeping its secrecy. The RSA method is a good starting point for the research, but there are great chances to improve and develop these techniques in subsequent work. We can realize the full potential of secure and covert communication, making this technology useful to people and organizations around the world, by researching various cryptographic methods and creating user-friendly interfaces.
References
[1] Laskar, S. A., & Hemachandran, K. (2012). High Capacity data hiding using LSB Steganography and Encryption. International Journal of Database Management Systems, 4(6), 57. [2] Walia, E., Jain, P., & Navdeep, N. (2010). An analysis of LSB & DCT based steganography. Global Journal of Computer Science and Technology. [3] Nisha, S., & Farik, M. (2017). Rsa public key cryptography algorithm–a review. International journal of scientific & technology research, 6(7), 187-191. [4] Alese, B. K., Philemon, E. D., & Falaki, S. O. (2012). Comparative analysis of public-key encryption schemes. International Journal of Engineering and Technology, 2(9), 1552-1568. [5] W. Ren and Z. Miao, \"A Hybrid Encryption Algorithm Based on DES and RSA in Bluetooth Communication,\" 2010 Second International Conference on Modelling, Simulation and Visualization Methods, Sanya, China, 2010, pp. 221-225, doi: 10.1109/WMSVM.2010.48. (Placeholder1) [6] Dixit, P., Gupta, A.K., Trivedi, M.C., Yadav, V.K. (2018). Traditional and Hybrid Encryption Techniques: A Survey. In: Perez, G., Mishra, K., Tiwari, S., Trivedi, M. (eds) Networking Communication and Data Knowledge Engineering. Lecture Notes on Data Engineering and Communications Technologies, vol 4. Springer, Singapore. [7] S. Gupta and J. Sharma, \"A hybrid encryption algorithm based on RSA and Diffie-Hellman,\" 2012 IEEE International Conference on Computational Intelligence and Computing Research, Coimbatore, India, 2012, pp. 1-4, doi: 10.1109/ICCIC.2012.6510190. [8] Xin Zhou and Xiaofei Tang, \"Research and implementation of RSA algorithm for encryption and decryption,\" Proceedings of 2011 6th International Forum on Strategic Technology, Harbin, Heilongjiang, 2011, pp. 1118-1121, doi: 10.1109/IFOST.2011.6021216. [9] A. G. Devi, A. Thota, G. Nithya, S. Majji, A. Gopatoti and L. Dhavamani, \"Advancement of Digital Image Steganography using Deep Convolutional Neural Networks,\" 2022 International Interdisciplinary Humanitarian Conference for Sustainability (IIHC), Bengaluru, India, 2022, pp. 250-254, doi: 10.1109/IIHC55949.2022.10060230. [10] S. M. Masud Karim, M. S. Rahman and M. I. Hossain, \"A new approach for LSB based image steganography using secret key,\" 14th International Conference on Computer and Information Technology (ICCIT 2011), Dhaka, Bangladesh, 2011, pp. 286-291, doi: 10.1109/ICCITechn.2011.6164800. [11] J. Fridrich, M. Goljan and Rui Du, \"Detecting LSB steganography in color, and gray-scale images,\" in IEEE MultiMedia, vol. 8, no. 4, pp. 22-28, Oct.-Dec. 2001, doi: 10.1109/93.959097. [12] R. Chandramouli and N. Memon, \"Analysis of LSB based image steganography techniques,\" Proceedings 2001 International Conference on Image Processing (Cat. No.01CH37205), Thessaloniki, Greece, 2001, pp. 1019-1022 vol.3, doi: 10.1109/ICIP.2001.958299.
Copyright
Copyright © 2023 Vineela Reddy M, Anudeep Reddy G. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET55617
Publish Date : 2023-09-04
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

