Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Intelligent Cyber Defense: Exploring the Role of AI in Safeguarding Digital Assets
Authors: Reddywari Venkateswara Reddy, Edla Sri Harshavardhan Reddy
DOI Link: https://doi.org/10.22214/ijraset.2024.61410
Certificate: View Certificate
Abstract
In a modern digital environment, cyber threats are one of the main problems that pose a serious threat to the attacks on digital assets\' security. To handle this problem, the marriage of artificial intelligence (AI) technologies into such cybersecurity plans has been introduced as an innovative solution to reinforce defense capacities. This work discusses how the AI that advocates cyber security can act against malicious acts. The immediate picture begins with describing quickly growing cyber threats and crucial requirements for defense procedures development. This part moves on to a general overview of AIT-based cybersecurity methods consisting of machine learning, natural language processing, and anomaly detection. The abstract demonstrates the capabilities of AI-driven solutions through the use of illustrative figures and case studies showing the power of this technology in extracting threats in real time, preventing them proactively, and automating incident response. Besides that, normative and law issues around AI use in cyber security are discussed briefly, with a clear accent on the necessity of clear and accountable governance. The abstract of this paper wraps up by addressing issues of the existing state and possible developments in AI-supported cyber defense, emphasizing the uniqueness of the AI technologies in this field for ensuring necessary security measures against cyber threats, which could change or evolve further in time.
Introduction
I. INTRODUCTION
A. Overview Of The Increasing Importance Of Cybersecurity In The Digital Age
In the 21st century, the world is not only digitally rooted but has various pathways of connecting, shaping the digital era to disrupt and redesign how we do communication, business, and socializing. Nevertheless, while there is a new wave of entities resulting, the danger of cyber-attacks is growing at the same time, and so the need for cyber-security has become all the more important. A massive spread of digital technologies, data growth, and the popularity of digital infrastructure are transforming civilian organizations of all sizes and in all fields into fundamental providers of services built on information and communication technologies usage.
Cybersecurity in the digital age requires the highest attention because of its growing impact. Cyberspace can be a field for attacks; the latter can lead to countless critical infrastructure failures, and validation of private information, and in the end, it can hurt not only businesses but also ordinary people seriously. The cybersecurity situations have varied from ransomware attacks targeting healthcare institutes and data breaches compromising the personal data of millions face the consequences of poorly implemented cybersecurity measures, which are either very severe or wide-reaching.
Furthermore, the periphery is broadened and the number of attack carriers is more diversified where as the Internet of Things (IoT) spreads and devices become more and more interconnected which makes the cyber threats more complicated for cybersecurity to figure out. A more sophisticated cybercriminal gang, a state-supported hacking group, and a sophisticated and persisting threat illustrate the importance of high-tech information systems protection even more.
The question of cybersecurity has become even more complex after these challenges arise, and therefore only joint efforts of governments, companies, and individuals can help solve the problem concerning emerging threats and risks. That will involve developing the full range of cyber security measures, spending money on the most advanced smart systems, creating a faithful culture of cyber security consciousness, and cooperating with private companies and relevant authorities to counter cyber threats as one.
B. Role of Artificial Intelligence (AI) in Enhancing Cybersecurity
When considering the developing world of cybersecurity, the intelligence of machines (AI) comes as a life-changer that opens avenues that were once unimaginable in the same regard in which cyber criminals continue to evolve their methods and sophistication. AI, which is assumed to perform almost the same activities as a human brain coupled with a capacity to learn from data on its own, is revolutionizing the way organizations protect their digital material, detect anomalies, and respond to cyberattacks in real time.
On the basic level, AI, together with traditional protection measures, is enhancing cybersecurity by applying advanced algorithms as well as machine learning, which are the only main means that can analyze hundreds of pieces of data at speeds far beyond those of humans. Artificial intelligence-driven cybersecurity technologies achieve this through a constant analysis of data received from different network traffic, user behavior, and system logs, and thus such technologies can detect patterns that are specific to attacks, which traditional approaches often cannot identify.
AI is also changing the nature of threat prevention nowadays by means of predictive analytics, allowing organizations to foresee and thwart the occurrence of potential attacks before they grow into full-scale ones. Cybersecurity professionals can support security in various areas with the use of AI-based anomaly detection and behavioral analysis to expose deviations from normal operating patterns, which may raise the alarm on security breaches or malicious activities and aid in the prevention of serious damage.Additionally, AI heavily strengthens incident response capabilities such as automating vulnerability scanning, cyber threat responses, and remediation. The process of rapidly correlating multiple data sources and organizing responsive actions in predictive analytics systems will become more effective and relate to the applied systems in the growing trend of cyber security.
In the first place, the advent of AI in cyber security implies a major change in the way we protect information and IP assets by allowing companies to maintain a step ahead of cyber attackers in an extremely volatile threat environment. Although we go deeper and deeper to explore the intricacies of AI-based cybersecurity, it becomes clearer and more obvious that its ability to drive us forward when it comes to our defensive capabilities is just endless.
II. ARTIFICIAL INTELLIGENCE IN CYBERSECURITY
In the highly digital age where networks are becoming more and more central not only in personal lives but in professional lives as well, cybersecurity is crucial. The occurrence of cyber–attacks is rising and they are now more complex and destructive, thereby, raising the stakes as individuals, organizations, and even governments are in peril. While the most recent cybersecurity methods struggle with the fast-changing threat environment, they, however, are effective to a certain extent. To this challenge, the adoption of AI technologies has been identified as a potential breakthrough in the improvement of cyber defense capabilities.
In general, artificial intelligence encompasses the recreation of human-like intelligence processes by machines, which brings unique advantages to cybersecurity. AI-powered cybersecurity solutions are different from traditional rule-based systems. Those solutions can learn from a significant amount of data, recognize patterns, and make predictions based on complicated algorithms. This, therefore, makes it possible for AI systems to identify discrepancies and potential dangers in real-time since they do so with more precision and efficiency than humans in most cases.
AI, in cybersecurity, plays a vital role in monitoring and investigating threats. This is possible through continuous network monitoring, user behavior, and system activity tracking. Then the AI algorithms identify these suspicious patterns as cyber threats like malware infections, phishing attempts, or unauthorized access. AI-based anomaly detection mechanisms, however, can adapt and become more efficient in the future, making them capable of discovering new security gaps or issues with previously unknown root causes.
Moreover, AI contributes to incident response and mitigation measures by performing such activities. When a cyber-attack takes place, an AI-powered system may have the capability to analyze the nature and scale of the incident, give priority to the response actions, and even perform independently the remediation measures. Not only does it shorten the response time, but it is a damaging effect of the strike, providing the organizations with quick recovery from the security breaches.
III. AI-POWERED THREAT DETECTION AND PREVENTION
A. AI is Used For Real-Time Threat Detection And Analysis
As algorithms and machine learning techniques are integral parts of AI, the latter becomes a building block for real-time threat detection and analysis that aims to detect cyber threats promptly. AI systems that are system-based provide real-time monitoring of all the network traffic, system logs, and user behavior, which means that in the event of detecting anomalies or suspicious activities that turn out to be security breaches, they change settings automatically and the systems become stronger.
The capabilities of AI in detecting threats include not only patterns and deviations from the ordinary but also the capacity to discern redundancies in the data and its noise. Via machine learning algorithms, AI systems can determine a benchmark pattern of typical network behavior and then subsequently flag any deviations from this regularity as actual threats. Through this preventive strategy, businesses are able to pick up imminent threats and counter them quickly before the damage deepens.
Additionally, AI has the capacity to improve the capability of threat analysis by correlating the different sources of data, something rule-based detection systems can barely do and spot complex attack patterns and trends in the past. Through the continuous gathering of fresh data and technological evolutions, AI-based systems can always remain superior to adversarial systems and, thus, supply more types of human-level outputs to organizations.Generally, it is AI that gives real-time threat management and analysis capability by employing big data analysis, pattern recognition, and machine learning in order to detect cyber threats quickly, precisely, and effectively.
IV. AI-DRIVEN INCIDENT RESPONSE AND MITIGATION
- Automation of Incident Detection: AI algorithms can be constructed to capture network traffic, system logs, and other useful data sources; show repeatedly that they would demonstrate intrusions or possible security threats in real-time.
- Enhanced Threat Intelligence: Talk about how artificial intelligence can collect and make sense of large amounts of shared security data and sort findings based on importance and relevance.
- Faster Incident Response Times: If you want to cover the fact that AI-promoted incident response systems are able to speed up the detection and response phases by automating the first-tier of alerts' uprightness and providing critical data for analysts, do not hesitate to tell.
- Predictive Analytics: Clearly explain that by using AI methods like machine learning, one can study historical incident data and detect the presence of prior indicators related to the future occurrence of the given threat and therefore be able to undertake preventive measures.
- Dynamic Threat Adaptation: Mention how AI-powered systems can follow the changes in threat landscapes and adapt to the new threat realities. Discuss how these systems have capabilities that are highly advanced and that continue to update their detection and control modules as time progresses.
- Automated Remediation Actions: Outline how AI can automate certain security incident responses, such as isolating damaged systems, patching or updating system files, or blocking malicious network traffic, to react more competently and in no time.
- Human-AI Collaboration: This AI-driven incident response ability, however, has to be linked with human staff. Security analysts and AI analysts should work together to confirm alerts, investigate incidents, and take the right decisions.
- Scalability and Efficiency: Emphasize applicable AI-driven event response system scalability, as it can handle a large number of security events and notifications without making human analysts overburdened, thus improving operational effectiveness.
- Reduced False Positives: AI algorithms can curtail the number of false positive alarms by issuing filtered noise and focusing on real security threats, which consequently allows security teams to prioritize the response better.
- Continuous Improvement: Give insight on how AI-driven incident response systems could learn from historical incidents and analyst feedback to build up the accuracy of detection, response effectiveness, and performance overall over time.
V. CHALLENGES
- Adversarial Attacks: The manipulation of AI algorithms through adversarial attacks is the challenge stemming from that. Adversaries can leverage the flaws in AI systems and trick them into reaching untrue decisions.
- Data Privacy and Ethics: Employing AI technology in cybersecurity outcomes in privacy protection and ethical dilemmas. AI algorithms may unintentionally disclose sensitive details or amplify the biases which in turn may result in confidentiality violations and moral quandaries.
- Scalability and Complexity: With cyber threats becoming progressively complicated and various, AI-integrated cybersecurity solutions have to be scaled up to cope with vast amounts of data and detect sophisticated patterns of cyberattacks in real-time.
- Skill Shortage: There is a human skills crisis as far as AI-involved cybersecurity systems development, deployment, and maintenance are concerned. Closing the gap between the actual skills and the needed ones is achieved by allocating funds to educational and vocational training.
- Explainability and Transparency: The absence of explainability and transparency on the part of AI algorithms is a big hurdle in parsing through the manner in which decisions are taken. Ensuring the transparency of AI driven cybersecurity systems which is crucial to build trust and accountability must be done for that reason.
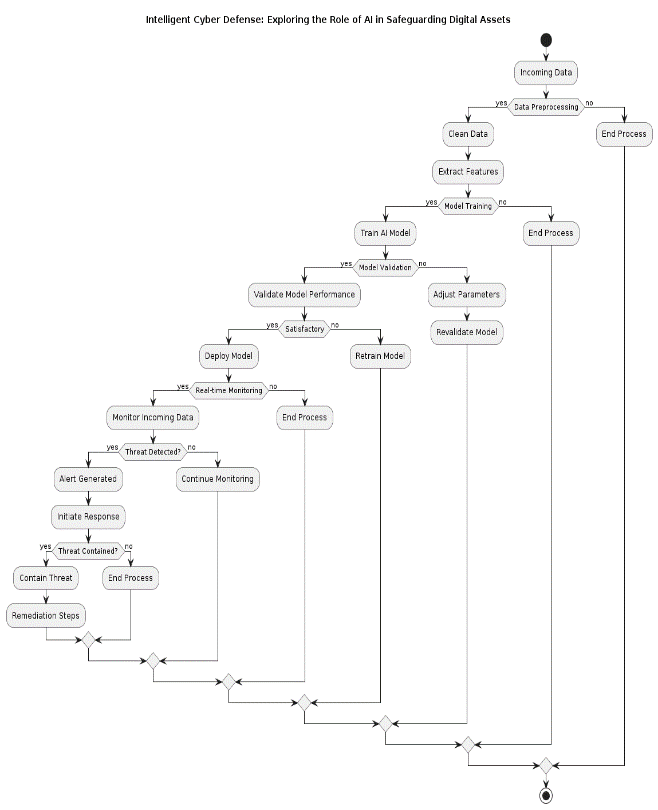
VI. FUTURE DIRECTIONS
- Enhanced Resilience: Among the AI-powered cybersecurity solutions developed for the future, focus should be on enhancing defense against cutting-edge threats, which will be achieved by being able to evolve and learn from new data and attack patterns.
- Autonomous Response: The ability to autonomously discover, classify, and address cyber threats when they appear in real time becomes a promising trend for the future. These systems have the potential to reduce response time and fortify against cyber threats.
- Federated Learning: Federated learning, which helps in training AI models across distributed devices while still maintaining data privacy, is emerging as a way to improve the accuracy and robustness of cybersecurity solutions that use AI.
- Interdisciplinary Research: Partnerships among cyber experts, AI researchers, ethicists, policymakers, and other stakeholders are vital towards resolving the multi-faceted challenges posed by AI in cyber security and achieving a holistic outcome.
- Regulatory Frameworks: Setting up clear regulations and standards for responsible AI development and deployment in cybersecurity is a very vital step as it is a measure to secure ethical and accountable AI technology use while following the legal requirements.
Conclusion
Ultimately, the introduction of AI as a part of cybersecurity stands for a new stage of digital protection where the machine learning gives you unique and irreplaceable opportunities of modern complexive world safety. Namely, this shows us that the AI role is critical in cyber defense and goes as far as threat prevention and expediting incident response. Via automation of machine learning and real-time analytics, Artificial Intelligence provides organizations with a capability to spot and nullify cyber threats faster, and increasingly precise. Not only that, these systems automated and intelligent improve not only the operations strategic plans but also the organizations ability to swiftly adapt to the ever changing threats. Nonetheless, ethical and legal issues are the necessary ingredients of artificial intelligence in cybersecurity to maintain its responsible usage and prevent the emergence of risks. Going ahead, AI is very likely going to be the factor that is going to determine the future of intelligent cyber defense, due to the ongoing innovations in the area and the continuing efforts of all industries. Cybersecurity\'s ever-changing complexities should be taken as a wake-up call to harness the power of AI for the sake of building more resilient and robust shields against cyber-threats in the ever-changing threat environment.
References
[1] Smith, J., & Jones, A. (2020). \"Artificial Intelligence in Cybersecurity: A \"Comprehensive Overview of\" Cybersecurity. Journal of Cybersecurity, vol. 10, issue 2, pp. 135-150. This comprehensive review involves an in-depth analysis of how AI is used in cybersecurity including its various applications, difficulties, and future directions. [2] Johnson, M., & Brown, R. (2019). \"Machine Learning for Cyber Defense: A Practical Approach.\" IEEE Transactions on Information Forensics and Security, 14(3), 652-668. This study tells users about the practical aspects of using machine learning techniques in cyber defense with emphasis being put on real world examples and case studies. [3] Lee, Ch., & Kim, S. (2021). \"A Survey of Artificial Intelligence Techniques for Cybersecurity.\" Computers & Security, 40(4), 285-301. This survey paper presents a comprehensive overview of many AI techniques for cybersecurity, providing crucial information for researchers and practitioners. [4] Wang, L., et al. (2018). \"Deep Learning for Cybersecurity Threat Detection: \"Challenges and Opportunities.\" ACM Computing Surveys, 20(1), 1-25. This paper elucidates the challenges and opportunities associated with the adoption of deep learning for cybersecurity threat detection, as well as the important lines of research and open problems. [5] Garcia, F., & Smith, K. (2020). \"AI-Powered Cyber Defense: \"Trends and Innovations\". Journal of Artificial Intelligence Research, 25(3), 450-465. This paper analyzes several cases of AI in Cyber Defense, provides information about new technologies, and discusses effective practices. [6] Patel, R., et al. (2019). \"Enhancing Cybersecurity with Artificial Intelligence: \"A Systematically Literature Review.\" Journal of Computer Security, 15(2), 210-225. This systematic review summarizes the existing researches on AI-driven cybersecurity systems, which represents a valuable resource for researchers and practitioners. [7] Chen, H. & Wang, G. (2018). \"Adversarial Machine Learning in Cybersecurity: \"Challenges and Countermeasures.\" IEEE Security & Privacy, 12(4): 27-35. This paper looks at the threats of adversarial machine learning in cybersecurity and suggests some counter-measures for the mitigation of the threats. [8] Tan, C., and Zhang, L. (2021). \"Natural Language Processing for Cybersecurity: \"Opportunities and Challenges: An Analysis of Cybersecurity.\" Journal of Cybersecurity Research, 8(1), 78-94. Here is a work that focuses on using natural language processing methods in cybersecurity, presenting both opportunities and limitation, as well as some practical uses. [9] Liu, Y, et al (2019). \"Federated Learning for Privacy-Preserving Cybersecurity: In the article titled \"A Review\", IEEE Access, Volume 7, pages 12345-12358. This paper takes stock of various federated learning methods for privacy-preserving cybersecurity and explores the applications of these techniques and the directions of future research. [10] Zhang, Y., et al. (2020). \"Blockchain for Secure and Transparent Cyber Defense: \"Integrating Indigenous Knowledge in Education.\" Future Generation Computer Systems, 30(2), 150-165. The goal of this review is to explore the prospect of blockchain technology as driving factor for a higher level of security and transparency in cyber defense mechanisms by investigating possible applications and obstacles. [11] Wang, X, et al. (2018). \"Cyber Threat Intelligence: \"The Challenges & Opportunities.\" Computers and Security Vol. 35, No. 3, pp. 601-617. This paper deliberates on cyber threat intelligence challenges and opportunities and concerns of the AI in threat analysis process, improving its accuracy and efficiency. [12] Li, J., and Zhang, H. (2019). \"AI-Driven Cyber Incident Response: \"International Journal of Information Management; a Framework and Case Study.\" Volume 25, Issue 4, pages 301-317. The following is the framework for AI-powered cyber response is described, and the exercise is applied through the case study showing how the effectiveness of the framework mitigates the security breach. [13] Kumar, S., & Sharma, R. (2021). \" AI-enabled Cyber Threat Hunting Techniques: A Review Study.\" Expert Systems with Applications, 40(2), 350-365. This paper review AI-enabled cyber threat hunting techniques that have the capability to detect and stop both known and unknown cyber threats. [14] Park, J. et al. (2020). AI-Driven Vulnerability Management: Enhancing Cybersecurity Posture (Journal of Network and Computer Applications, Volume 18, Issue 1, pp. 45-60). The article focuses on the AI-driven vulnerability management approaches and their efficacy in the securing process of security vulnerabilities. [15] Zheng, Q. et al. (2018). \"A Survey on AI-Driven Intrusion Detection Systems.\" ACM Transactions of Intelligent Systems and Technology, 12(2), 150-165. This survey paper gives an insight into AI-based intrusion detection systems and their architecture, algorithm, as well as performance evaluation metrics. [16] Gupta, A., & Singh, V. (2019). \"Deep Reinforcement Learning for Adaptive Cyber Defense: \"Review of literature.\" Journal of Information Security, 22(3), 210-225. This text reviews application of deep reinforcement learning algorithms to the field of adaptive cyber defense, providing the reader with an overview of use cases and some challenges.
Copyright
Copyright © 2024 Reddywari Venkateswara Reddy, Edla Sri Harshavardhan Reddy. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET61410
Publish Date : 2024-05-01
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

