Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
IoT based a Smart Home Automation System Using Packet Tracer
Authors: Varsha T, Shrihari , Dr. Nagaraja G S
DOI Link: https://doi.org/10.22214/ijraset.2023.48514
Certificate: View Certificate
Abstract
The technology is seeing a rapid growth day by day in the life of humans. Rapid growth in technology has led to newer inventions that has made human lives very comfortable. The introduction of Internet Of Things (IOT) has brought a drastic change in the way humans lead their lives. Network plays an important role in each and every technology as it allows connection and communication between different objects and entities of any application. Different models like OSI, TCP demonstrate how computer system communicate over a network. Each of these models have different layers in it. This paper mainly focuses on the application layer which enables effective communication with other applications on different computer systems and different networks. Also the paper discuss different application layer IoT based protocols that work in the application layer by considering the scenario of Smart Home to demonstrate working of each protocol.
Introduction
I. INTRODUCTION
IoT stands for “Internet Of Things”. It defines things and their connection to the internet. IoT enables control of local and remote objects by consuming the integration of network technology. It connects the daily used devices that are present around us as well as the devices that are present over the internet and automates the communication among them. IoT is an emerging technology which usually intends to make the communication between the technological devices and different type of sensors to provide new applications that makes life more easier.
Application layer acts as an interface between an IoT device and network through which they communicate. This layer handles the data formatting and presentation and also serves as the bridge between the device and the network. Some of the application layer IoT based protocols are Constrained Application protocol (CoAP), Message Queue Telemetry Transport protocol (MQTT), Extensible Message and Presence protocol (XMPP), Advanced Message Queuing protocol (AMQP), Representational State Transfer protocol (REST). Choosing these protocols for any application depends on the device usage and also the functionality of the protocol. The IoT network model paper discusses to illustrate the working of these protocols is Smart Home.
Smart Home is designed by making use of the smart objects that helps to improve and automate the home activities. This is done to perform automating activities of smart home which don't involve any user. Such monitoring home environment can be simulated by using different types of the sensors. Smart Home is designed not only to automate the home activities but also to implement security for home.
II. LITERATURE SURVEY
IoT has large potential growth in this ever developing technical world. Key drivers of the traffic generated through the internet are the application protocols. Network traffic can be reduced and reliability can be improved if proper protocols are chosen for specific applications. When the application layer IoT based protocols are implemented on an arm based device as a gateway, the CoAP performs best for smaller payloads and worst for bigger payloads when compared with MQTT and REST [1].
MQTT which is based on HTTP (Hyper Text Transfer Protocol) consumes less energy, offers better performance and also reduces the data overhead to keep 4G or 5G network utilization to low as compared to REST [2]. [4] proposes a model to evaluate the quality of major application layer based IoT protocols in terms of data transmission while performing Machine to Machine communication so as to support the application of IoT based on the real devices and also to detect the real environment condition in the smart simulated environment and monitoring system. MQTT is a data exchange protocol in IoT environment. To increase the security, MQTT uses transport layer security. [4] proposes an enhanced version of MQTT to provide thing to thing security to prevent the data leaks that happen during the data exchange. In [5], the authors discusses the methods of data processing in a 3 - tier IoT structure. As large amount of data is generated through the applications of IoT, each layer in the IoT structure performs different functionalities like data communication, data acquisition and data application.
IoT is playing an important role in the quality of life that the people are leading nowadays. It has emerged as a most useful technology in almost each and every sector. So, it is very important that one should always work in the area of identifying the risks and attacks that are present and that will take place in the IoT systems to make those systems perform more efficiently [6].
III. METHODOLOGY
The underlying principle of IoT is that it tries to establish the connectivity of the internet to make data exchange possible irrespective of the size of the devices that are being used. The application layer IoT based protocols should address and provide solution for some of the challenges faced by the IoT network communication. This is very much important because the data that is used by the IoT systems is more complex than that of the regular networking systems.
Choosing an appropriate protocol for an application matters the most in any sector. Some of the factors for choosing suitable protocol for an application are data latency which provides the speed at which the data need to be transported, reliability which tells the consequences suffered by an IoT application when data leakage happens, bandwidth which gives an estimated amount of data that can be accommodated and transport which helps in selecting the suitable transport protocol for an IoT application.
Each of the application layer based IoT protocol provides different functionality. CoAP is a lightweight and low transmission rate based protocol which makes use of request and response messages. This protocol uses small data packets to ensure that less messages are lost during the communication. CoAP lacks in the security aspect. MQTT is a machine to machine connectivity oriented publish/subscribe protocol which minimizes data loss, network traffic and processing load.
XMPP is XML based protocol which provides real time communication between the devices. The protocol offers high scalability to enable data sharing and local networking.
AMQP is an asynchronous protocol which provides guaranteed message delivery. It implements security through transport layer security and secure socket layer.
REST protocol provides synchronous request response through HTTP. It enables machine to machine communication which provides an added advantage to the IoT applications.
To demonstrate the working of application layer IoT based protocols, the IoT network model of Smart Home is considered. Entire house is monitored by web cameras and owner of the house can have control and access to whole house through the smartphone. Cisco Packet Tracer is used for the simulation and all the dummy models of the daily used devices in the house are used from the simulator only.
Server, IoT devices, routers, switches, smart phone and wires are considered. First all the routers are connected. Then routers are connected with the switches. All the IoT devices, server and smart phone is connected to the switches.
All the routers are given IP address using DHCP protocol. Routing protocol EIGRP is used to configure the routers which enables owner to access the house through smartphone. Smartphone access the server through MQTT protocol to establish machine to machine connectivity by performing sign in to the server. After successful sign in to the server, all the device control will be available through the smartphone as shown in Fig 1.

IV. RESULTS
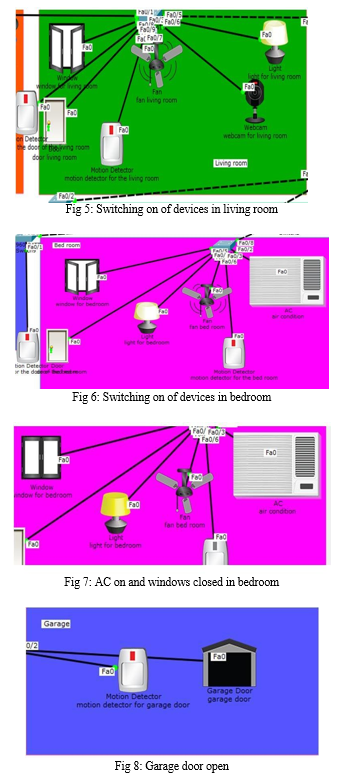
The scenario is illustrated as follows. In front of the house, when motion detector detects something it automatically switch on the web camera as shown in Fig 4. When lawn sprinkler is switched on, the water drain will automatically be on as shown in Fig 4. If the wind is high, then the wind detector detects the high wind and closes all the windows of the house as shown in Fig 4. When someone enters living room, the motion detector automatically opens the door and switch on the fan, light, window, web cam as shown in Fig 5. Same happens in case of bedroom also as shown in Fig 6. In bedroom if the air conditioner is on, then the windows will automatically close as shown in Fig 7. When car enters in front of the garage, then doors of the garage will be automatically opened as shown in Fig 8.

Conclusion
The aim of this research was to illustrate the working of application layer IoT based protocols using Cisco Packet Tracer by considering an IoT network model. Simulation of Smart Home IoT network model successfully demonstrates the working of application layer IoT based protocols. It provides an example of how daily used devices around us makes use of standard protocols in automating the services without any human intervention. The simulation helped in understanding the pros and cons of implementing the same in the real world.
References
[1] U. Tandale, B. Momin and D. P. Seetharam, \"An empirical study of application layer protocols for IoT,\" 2017 International Conference on Energy, Communication, Data Analytics and Soft Computing (ICECDS), 2017, pp. 2447-2451, doi: 10.1109/ICECDS.2017.8389890. [2] J. Hofer and S. Pawaskar, \"Impact of the Application Layer Protocol on Energy Consumption, 4G Utilization and Performance,\" 2018 3rd Cloudification of the Internet of Things (CIoT), 2018, pp. 1-7, doi: 10.1109/CIOT.2018.8627133. [3] Abdi, A. (2018). Designing Smart Campus Using Internet of Things. International Journal of Computer Science Trends and Technology (IJCST), V 6 I 3 PP 109-116. [4] T. keophilavong, Widyawan and M. N. Rizal, \"Data Transmission in Machine to Machine Communication Protocols for Internet of Things Application: A Review,\" 2019 International Conference on Information and Communications Technology (ICOIACT), 2019, pp. 899-904, doi: 10.1109/ICOIACT46704.2019.8938420. [5] W. -T. Su, W. -C. Chen and C. -C. Chen, \"An Extensible and Transparent Thing-to-Thing Security Enhancement for MQTT Protocol in IoT Environment,\" 2019 Global IoT Summit (GIoTS), 2019, pp. 1-4, doi: 10.1109/GIOTS.2019.8766412. [6] L. Zhenhui, \"Data Processing Strategy in Internet of Things Application System,\" 2020 International Conference on Big Data & Artificial Intelligence & Software Engineering (ICBASE), 2020, pp. 86-89, doi: 10.1109/ICBASE51474.2020.00026. [7] T. K. Boppana and P. Bagade, \"Security risks in MQTT-based Industrial IoT Applications,\" 2022 IEEE International Conference on Omni-layer Intelligent Systems (COINS), 2022, pp. 1-5, doi: 10.1109/COINS54846.2022.9854993. [8] Alexandria, A. (2014). Enabling communication between wireless sensor networks and the internet of things-ACOAP communication stacks. International journal of Science and Engineering, 6-7 Vol.5. [9] A l-Emran, M., Malik, S. I., & Al-Kabi, M. N. (2020). A Survey of Internet of Things (IoT) in Education: Opportunities and Challenges. In Toward Social Internet of Things (SIoT): Enabling Technologies, Architectures and Applications (pp. 197-209). Springer, Cham [10] Mumtaz, S., Alsohaily, A., Pang, Z., Rayes, A., Tsang, K. F., & Rodriguez, J. (2017). Massive Internet of Things for industrial applications: Addressing wireless IIoT connectivity challenges and ecosystem fragmentation. IEEE Industrial Electronics Magazine, 11(1), 28-33. [11] Stoyanova, Y. Nikoloudakis, S. Panagiotakis, E. Pallis, and E. K. Markakis, “A Survey on the Internet of Things (IoT) Forensics: Challenges, Approaches, and Open Issues,” IEEE Communications Surveys and Tutorials, vol. 22, no. 2, pp. 1191–1221, 2020. [12] M. Chernyshev, Z. Baig, O. Bello, and S. Zeadally, “Internet of things (IoT): Research, simulators, and testbeds,” IEEE Internet of Things Journal, vol. 5, no. 3, pp. 1637–1647, jun 2018. [13] G. Tuna and R. Das¸, “Wireless sensor network-based health monitoring system for the elderly and disabled,” International Journal of Computer Networks and Applications, vol. 2, no. 6, pp. 247–253, 2015. [Online] Available: http://www.ijcna.org/issues.php?vol=2& issue=6http://files/107/Vol-2-issue-6-M-02.pdf [14] R. Das¸, G. Tuna, and A. Tuna, “Design and implementation of a smart home for the elderly and disabled,” International Journal of Computer Networks and Applications, vol. 2, no. 6, pp. 242– 246, 2015. [Online]. Available: http://www.ijcna.org/issues.php?vol=2& issue=6http://files/109/Vol-2-issue-6-M-01.pdf [15] R. Das, A. Tuna, S. Demirel, and M. K. Yurdakul, “A survey on the internet of things solutions for the elderly and disabled: Applications, prospects, and challenges,” International Journal of Computer Networks And Applications, vol. 4, no. 3, pp. 84–92, jan 2017. [Online]. Available: http://www.ijcna.org/Manuscripts/IJCNA-2017-O- 08.pdfhttp: //files/111/IJCNA-2017-O-08.pdf [16] I. I. Patru, M. Carabas¸, M. B ? arbulescu, and L. Gheorghe, “Smart ? home IoT system,” Networking in Education and Research: RoEduNet International Conference 15th Edition, RoEduNet 2016 - Proceedings, 2016. [17] T. Malche and P. Maheshwary, “Internet of Things (IoT) for building smart home system,” in 2017 International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud), 2017, pp. 65–70. [18] H. Singh, V. Pallagani, V. Khandelwal, and U. Venkanna, “IoT based smart home automation system using sensor node,” Proceedings of the 4th IEEE International Conference on Recent Advances in Information Technology, RAIT 2018, pp. 1–5, 2018. [19] W. A. Jabbar, M. H. Alsibai, N. S. S. Amran, and S. K. Mahayadin, “Automation System for Smart Home,” 2018 International Symposium on Networks, Computers and Communications (ISNCC), pp. 1–6, 2018. [20] F. Yalcinkaya, H. Aydilek, M. Y. Erteen, and I. Nihat, “IoT based Smart Home Testbed using MQTT Communication Protocol,” Uluslararas? Muhendislik Arastirma ve Gelistirme Dergisi, p. 317, 2020.
Copyright
Copyright © 2023 Varsha T, Shrihari , Dr. Nagaraja G S. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET48514
Publish Date : 2023-01-03
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

