Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Malware Scanner Harnessing: The Power of Yara Framework for Precise Threat Detection
Authors: G Manisha, Reddyvari Venkateswara Reddy, B. Supraja, K. Navya Sri, E. Harsha Vardan Reddy
DOI Link: https://doi.org/10.22214/ijraset.2024.59544
Certificate: View Certificate
Abstract
Cyberattacks are getting to be dynamically progressed. As resistance got to be way better and more grounded, the aggressors adjusted and moved forward with their strategies to bypass resistance. In that case a situation, guards must empower numerous defense components in put to extend their defense in a profundity pose. The viable sharing of insights to recognize malware has been continuously challenging for those working to secure data innovation (IT) and mechanical control framework systems. In this circumstance having the capability to recognize noxious records with YARA rules inside the organize may be a must, with free and mind-blowing open-source instruments such as Zeek and YARA, any organization can enable this revelation capability, without having to spend amazing entireties of cash as of now. Through our work, we see that a huge parcel of vulnerabilities happens due to despicably approved inputs, taken after by frail qualifications and despicably secured records. Ransomware attacks have advanced to become more advanced, determined, and irreversible. In 2019, numerous high-profile ransomware developers extorted high-value substances for cash by scrambling their information and erasing any reinforcement records. Once a framework is tainted with a crypto-ransomware assault, it\'ll be extreme to recoup the victim\'s information unless reinforcement is accessible or the malware creator offers the unscrambling key with the casualty. Additionally, ransomware engineers these days receive unused strategies and strategies to spread and avoid location.
Introduction
I. INTRODUCTION
A malware scanner utilizing the YARA framework alludes to a framework that's able to filter records and detect if it could be a malware record utilizing YARA rules. YARA may be a tool/framework pointed at making a difference for malware analysts to recognize and categorize malware tests.
This makes it simple to identify noxious records and keep our frameworks secure from diverse sorts of assaults. It makes a difference to us to know in case it is secure to open the record or not. Distinct vital perspectives of computerized forensic procedure and examination is the distinguishing proof and classification of potential noxious parallels in a framework or an arrangement. On the off chance that malware picks up a decent footing, it can be utilized to blackmail cash, assemble delicate data, screen keystrokes, or even devastate your network or machines.
YARA, which stands for, “Yet Another Recursive Acronym”, is an effective way to help in recognizing and classifying malware like ransomware. YARA is an open-source apparatus that utilizes a rule-based approach to distinguish malware based on signature location, like content or twofold designs. The depictions were built from strings and rationale, and coordinate with designs to classify the test to some kind of families or variations. In conclusion, this paper gives an adaptable and adaptable arrangement for malware analysis and research, that can basic portion of the continuous fight against cyber threats. It trusts to create a major commitment to the worldwide extension of cyber security strategies and the defense of digital infrastructures through this paper. The paper's objective is to form a major commitment to the improvement of cybersecurity methods and the defense of imperative systems and frameworks. Defending computerized environments is made conceivable in an expansive portion by the malware investigation utilizing the YARA system, which leverages the combined endeavors of the cyber security community and keeps upgrading its capabilities.
II. LITERATURE REVIEW
- Veeam: According to Veeam’s 2023 Ransomware Trends Report, 85% of organizations surveyed suffered at least one ransomware attack in 2022. Top data protection companies like Veeam integrate Signature-based malware detection tools to scan backups for health and recoverability.
- A YARA-based Approach for Detecting Cyber Security Attacks: This research paper explains the YARA and detailed information on attack applications and their results. It also interprets detection of malware with YARA.
- A Comprehensive Review on Malware Detection Approaches: This research paper gives a detailed view about what are the existing solutions for malware detection and their disadvantages.
- Rule-Based Approach to Detect IoT Malicious Files: This research paper provides creation of Yara rules and the usage of existing Yara rules. It also talks about how to detect IoT malicious files.
III. OBJECTIVE
The objective of our malware checking is to create a comprehensive and viable arrangement for identifying and relieving potential security dangers posed by malware. Through the integration of Python programming, the YARA system, and a user-friendly interface, our essential objective is to supply clients with a dependable instrument that enables them to defend their frameworks and information against pernicious programs.
At its center, our venture points to address the squeezing required for proactive cybersecurity measures in a progressively interconnected advanced scene. With the multiplication of advanced malware variations focusing on people, businesses, and organizations around the world, there's a basic requirement for open and solid apparatuses that can recognize and neutralize these dangers viably. By leveraging the capabilities of YARA, an effective malware discovery apparatus known for its adaptability and extensibility, we aim to upgrade the discovery capabilities of our arrangement, empowering it to distinguish known malware designs and behaviors precisely.
Besides, our extension looks to democratize malware checking and investigation by providing a user-friendly interface that streamlines the method of filtering records and catalogs for potential dangers. Through instinctive UI components and clear filter result introductions, we aim to enable clients of all levels of specialized mastery to require proactive measures to secure their frameworks from malware diseases. Also, by consolidating highlights such as record determination alternatives, check result logging and execution optimizations, we endeavor to provide a comprehensive arrangement that meets the diverse needs of clients over diverse situations and utilize cases.
In rundown, the aim of our malware checking is to prepare clients with a strong, available, and dependable apparatus for recognizing and moderating malware dangers viably. By combining the control of Python programming, the YARA system, and user-friendly design principles, we aim to form an arrangement that engages people, businesses, and organizations to protect against the ever-evolving scene of cyber dangers, subsequently upgrading by and large cybersecurity versatility and relieving potential dangers to computerized resources and foundation.
IV. SYSTEM REQUIREMENTS
- Equipment Prerequisites: A devoted server or virtual machine (VM) with adequate assets such as CPU, Smash, and capacity to handle the arranged activity and firewall operations.
- Operating System: The chosen software must be compatible with the desired operating system. Common options include Linux-based distributions such as Virtual Machine,
- Internet Connection: A stable and reliable internet connection is necessary for the firewall to handle incoming and outgoing traffic effectively.
- Software Requirements: YARA framework, python.
V. PROBLEM DEFINITION
The system is described as a "malware scanner utilizing the YARA framework" and is capable of analyzing data and applying YARA regulations to determine whether the data contains malicious software. Malware researchers can utilize the framework or program YARA recognize and categorize malware samples. This makes it simple to identify dangerous files and protects our systems from various forms of intrusion. Knowing whether or not the file can be opened safely is helpful.
VI. EXISTING SOLUTIONS
Although Yara is still a well-known tool for malware examination, there may be other programs that are thought to be less accommodating for an assortment of reasons, like having fewer highlights, having inconvenience scaling, or having a powerless community.
A few of the existing frameworks are as follows:
- Cryptographic Hashing: Using an intriguing string of hexadecimal characters to identify and categorize malware may be a standard technique. Because the record hashes generated are compared to a database of malware markings, which contains information nearly identical to the kind of malware a signature relates to, this enables known malware to be identified and categorized on a machine.
- Fuzzy Hashing: A fuzzy hashing technique divides the data record into a few squares, treats each square separately for the purpose of computing its hash, and then concatenates the hashes of all the squares to obtain the fuzzy hash of the file.
- ClamAV: ClamAV could be a prevalent device to identify pernicious programs or malware. Whereas it calls itself an antivirus motor, it likely won't experience numerous infections, as they have gotten too uncommon. It is more likely to discover other shapes of malware like worms, backdoors, and ransomware. clamAV lo can be utilized in many ki can be used in a variety of ways. ClamAV does not do on-access checking but can be combined with other devices to get comparable usefulness.
- MISP: MISP collects, stores, and conveys security markers and finds dangers. This makes the stage valuable for those included with security episodes and malware investigations. Clients advantage from having a well-tested stage to structure the tremendous number of information focuses accessible when it comes to security dangers. The tooling permits interaction with other devices, like security occurrence and occasion administration (SIEM) and interruption discovery frameworks (IDS).
VII. LIMITATIONS OF THE EXISTING SYSTEM
- Static Analysis Approach: The project's static analysis method analyzes files statically by using predetermined criteria. This implies that malware that displays dynamic behavior or modifies its behavior while running could go unnoticed. Advanced malware tactics such as code obfuscation, packers, and encryption are ineffective against static analysis approaches.
- Only File-Based Malware: The malware scanning is only capable of detecting malicious files; it can miss threats that are only present in network traffic, registry entries, or memory.
- Constant Upkeep and Updates: It takes constant work and resources to maintain and update the scanning infrastructure and the YARA ruleset.
VIII. SCOPE OF THE PROJECT
- Functionality: Our solution will provide core functionality for scanning files to detect malware. It will offer features for file selection, scanning, detection, and result reporting.
- User Interface: We design a user-friendly interface using the Tkinter library to enable easy file selection and display scan progress and results. The interface will prioritize clarity and simplicity to ensure users can understand and act upon the scan results effectively
- YARA Integration: Our solution will integrate with the YARA framework to define rules for detecting malware based on specific patterns and attributes. We will develop custom YARA rules tailored to different malware families or behaviors to enhance detection accuracy.
- Result Reporting: Detected malware will be reported to the user in a clear and understandable format. This includes displaying alerts or notifications about malware detection.
- Testing and Validation: Exhaustive testing will be conducted to approve the exactness and adequacy of our malware scanner. We'll test the arrangement with a different extend of malware tests to guarantee comprehensive location scope.
- Scalability and Future Expansion: The project will focus on scalability and scope for future expansion that includes performance optimization, rule refinement, and expansion
IX. FLOW CHART
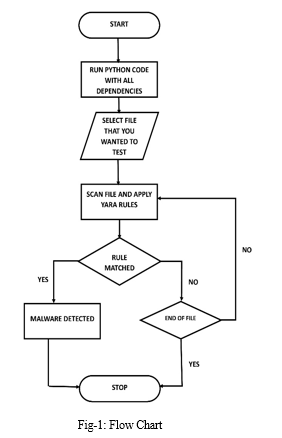
X. ARCHITECTURE
- Client Interface (UI): Make the application's client interface (UI) as basic as conceivable in order with it, select which records to filter, and see how the filter comes about. When planning UI components, utilize a graphical client interface (GUI) toolkit such as Tkinter for Python.
- Malware Scanning Engine: This engine integrates YARA rule compilation and matching functionalities to find probable malware patterns within files. This is the main malware scanning engine that analyzes files using YARA rules.
- File Selection and Input Handling: Provide users with options to select files to scan using file dialog prompts and Handle user input securely to prevent potential security risks such as file path manipulation or code injection.
- YARA Rule Management: Manage YARA rules efficiently, allowing users to load, update, and customize rule sets based on their requirements.
- Scan Result Presentation: Present scan results to users in a distinct and understandable format, indicating whether files are clean or flagged as potential malware.
XI. RESULTS
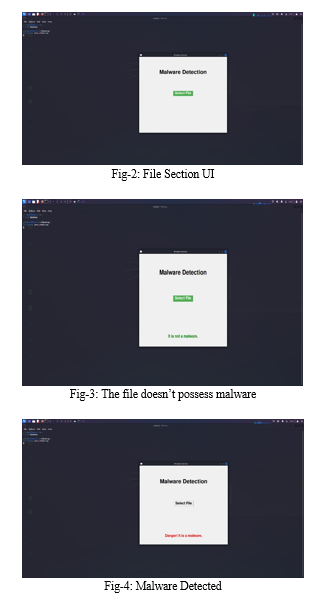
Conclusion
In conclusion, our malware scanning extension represents a noteworthy step towards upgrading cybersecurity strength and moderating the dangers posed by pernicious programs. Through the integration of Python programming, the YARA system, and a user-friendly interface, we have created a comprehensive arrangement that engages clients to distinguish and neutralize malware dangers viably. By leveraging the capabilities of YARA, our arrangement offers exact and solid malware location based on predefined designs and behaviors, empowering clients to recognize both known and rising dangers. The natural client interface rearranges the checking handle, making it open to clients of varying degrees of specialized mastery. Furthermore, highlights such as record determination choices, filter result logging, and execution optimizations upgrade the convenience and viability of the apparatus. Generally, our extension fills a basic requirement for proactive cybersecurity measures in today\'s advanced scene, where the risk of malware looms expansive. By giving clients a capable and open device for malware location, we aim to engage people, businesses, and organizations to secure their frameworks and information from potential security breaches. Moving forward, we stay committed to improving and refining our arrangement to adjust to the advancing risk scene and guarantee proceeded viability in shielding against malware assaults.
References
[1] Abmhara M, Køie GM. \"Cyber security and the Internet of Things: vulnerabilities, threats, intruders and attacks\".Cyber Security Journal and Mobility, 65–88, 2022. [2] Bhat P, Yano ET, Gustasson P. \"Towards a framework to detect multi-stage advanced persistent threats attacks\". in 2018 IEEE 8th Symposium on service-oriented system engineering, IEEE, 390-395, 2018. [3] Si Q. etuveal., “Malware detection using the automated generation of Yara rules on dynamic features”. In Science of Cyber Security: 4th International Conference, SciSec 2017, Matsue, Japan, August 10–12, 2017, Revised chosen Papers, Springer, 315-330, 2017. [4] Nithya Naik, Paul Jekins, Roger Cooke1, Jonathan Gillett and Yachu Jin. [5] According to Sophos How Signature-Based Detection Operates and What Signatures Are, Sophos, Feb. 2014. reached on November 4, 2014. [Online]. https://home.sophos.com/en-us/security news/2014/what-is-a-signature is accessible. [6] W. Lee, “Malware and Attack Technologies,” Cybook: Malware Knowledge Area, no. 1 pp. 3-5, May 2013. [7] M. Sikorsk and A. Honiga, \"Practical Malware Analysis.\" 2012; O\'Reilly, Sebastopol, USA. Page 10 was retrieved on November 9, 2012. [Online]. The following link is available: 9781593272906/learning.oreilly.com/library/view/practical-malware-analysis [8] N. Sarantinous, C. Benzii, O. Arabiate and A. Al-Nemrat, \"Forensic Malware Analysis: The Value of Fuzzy Algorithms in Identifying Similarities,\" 2010 IEEE Trustcom/BigDataSE/ISPA, 2016, pp. 1782-1787, doi: 10.1109/TrustCom.2016.0274.
Copyright
Copyright © 2024 G Manisha, Reddyvari Venkateswara Reddy, B. Supraja, K. Navya Sri, E. Harsha Vardan Reddy. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET59544
Publish Date : 2024-03-28
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

