Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
MQTT Systems: A Survey
Authors: Pujan Hiteshkumar Shah
DOI Link: https://doi.org/10.22214/ijraset.2024.59000
Certificate: View Certificate
Abstract
Abstract: In today\'s era, billions of intelligent devices populate Internet of Things (IoT) environments worldwide, spanning homes, hospitals, factories, and vehicles. Consequently, the interconnected device count continues to surge at a rapid pace. These devices engage in communication with one another and with various services using diverse communication protocols to transport sensor or event data. These protocols facilitate applications in gathering, storing, processing, describing, and analyzing data to address a myriad of challenges. Additionally, IoT endeavors to furnish secure, bidirectional communication between interconnected devices like sensors, actuators, microcontrollers, or smart appliances, and corresponding cloud services. This study shows that into the evolution of Machine-to-Machine (M2M) protocol research, including MQTT, AMQP, and CoAP, spanning the past two decades, underscoring MQTT\'s pronounced growth trajectory. Furthermore, we compile pertinent application domains of MQTT, recognized as the predominant M2M/IoT protocol, via an exhaustive literature review across major digital research repositories. Here quantitative assessment illuminates key MQTT-related studies published in the last five years, facilitating a comparative discourse on MQTT protocol\'s principal attributes, advantages, and constraints. Additionally, we propose a taxonomy to juxtapose the properties and features of diverse MQTT implementations, encompassing brokers and libraries available in the public domain, aiding researchers and end-users in judiciously selecting a broker or client library tailored to their requisites. Ultimately, we finalize the pertinent outcomes of our comparison, spotlighting unresolved issues warranting further research.
Introduction
I. INTRODUCTION
The concept of the Internet of Things (IoT) pertains to a network of interconnected devices embedded with sensors, software, and other technologies, enabling them to gather and exchange data over the internet. These devices span from commonplace objects like household appliances and wearable gadgets to industrial machinery and infrastructure components. IoT aims to establish intelligent, interconnected systems that enhance efficiency, productivity, and convenience across various sectors, including home automation, healthcare, transportation, agriculture, and manufacturing. MQTT (Message Queuing Telemetry Transport) is a lightweight messaging protocol crafted specifically for IoT applications. Operating atop the TCP/IP protocol suite, it's tailored for devices with constraints such as limited bandwidth, high latency, or unreliable networks. MQTT follows a publish-subscribe messaging model, where devices (publishers) dispatch messages to a central broker, which then disseminates them to one or more subscribing devices based on predefined topics. This architecture allows for efficient and scalable communication, facilitating real-time data exchange and event-driven interactions within IoT systems. MQTT's significance in IoT lies in its ability to enable efficient and reliable communication between IoT devices and applications. Its lightweight design suits resource-constrained devices with limitations in processing power, memory, and battery life. The publish-subscribe model fosters asynchronous communication, minimizing network overhead and reducing latency, particularly advantageous in scenarios where devices operate remotely or intermittently connect. Furthermore, MQTT supports various Quality of Service (QoS) levels, enabling devices to specify message delivery guarantees according to their application's reliability requirements. Ultimately, MQTT plays a vital role in fostering seamless connectivity, interoperability, and scalability within IoT environments, contributing to the development of innovative and intelligent IoT solutions. The novelty of this study is that it performs a quantitative evaluation of MQTT-related published works found in Google Scholar, Dimensions, and Scopus; highlights the potential and limitations of use of the MQTT protocol, identifies the annual exponential growth rate in MQTT research works since its appearance in 1999, and gathers the application areas of the MQTT protocol across various domains within IoT. The remainder of this paper is structured and organized as follows: Section II introduces IoT reference model,Section III highlights messaging protocols for IoT communication, basics of publish/subscribe type messaging service and fundamentals of MQTT, Section IV discusses some important MQTT works published over past five years and presents a literature review. Section V defines the scope and method of the literature search conducted in this study and highlights its findings. Section VI introduces various MQTT implementations and compares their features through various taxonomy categories, and Section VII summarizes the revealed open issues and challenges around MQTT and,finally Section VIII concludes this work.
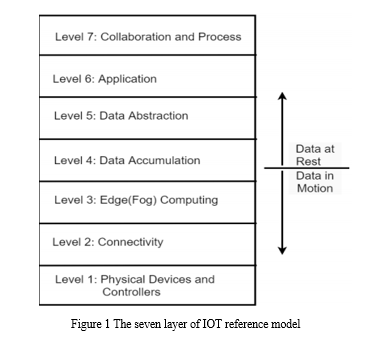
II. IOT REFERENCE MODEL
In an IoT system, things may refer to any sensor or devise, starting from very ordinary tiny things to large living things. Sensors in things work as input sources to produce or collect data, microcontrollers process those data, transmit over internet and actuators work as an output device to control or move something as per the instructions received from the Internet. The connections between people and things are increasing day by day, and the amount of data produced every second is stupendous. The number of smart devices has already outnumbered the number of humans on the planet. Numerous research works suggest that the world is embracing digital infrastructure five times faster than it embraced electricity and telephony.
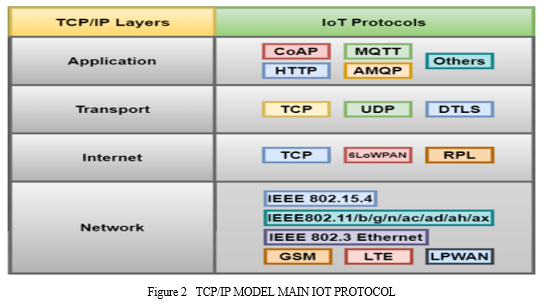
III. MESSAGING PROTOCOLS FOR IOT
The preceding section outlined the reference model of IoT systems, emphasizing the necessity of a dependable communication protocol for its realization. In this subsequent section, we delve into IoT protocols in a broader context, providing an overview of a publish/subscribe (pub/sub) service and offering a detailed introduction to the MQTT protocol.
A. Introduction to Publish/Subscribe Service
In a publish/subscribe messaging service, a "message" denotes the data transmitted through the service, while a "topic" represents a named entity indicating a stream of messages. A "subscription" signifies an interest in receiving messages on a specific topic. The "publisher" or "producer" is a device or program responsible for generating messages and publishing them to the messaging service under a designated topic. On the other hand, a "subscriber" or "consumer" is a device or program that receives messages based on a specified subscription.
B. Basics of MQTT Protocol
MQTT stands for Message Queuing Telemetry Transport, an open standard governed by OASIS and ISO (ISO/IEC PRF 20922), designed as a client-server, publish/subscribe messaging transport protocol. Originating in 1999, it was developed by Dr. Andy Stanford-Clark of IBM and Arlen Nipper of Arcom. This protocol's design principles prioritize minimizing network bandwidth and device resource usage to ensure reliable message delivery. MQTT is capable of transmitting data efficiently over low-bandwidth or unreliable networks while consuming minimal power. Its features include being lightweight, open-source, and conducive to efficient communication.
IV. LITERATURE STUDY
In this section, we provide a summary of notable studies concerning MQTT that have been published in the literature over the past five years. Table 1 presents an overview of significant works related to MQTT. These studies have been classified into four primary topics, which we will discuss next:
A. Advantages of MQTT
Emphasized the lightweight nature of the MQTT protocol for communication with resource-constrained devices. They demonstrated its effectiveness by developing a module for an EjsS (Easy Java/Javascript Simulations) educational tool to communicate with Arduino-based devices. Their experiments showed that MQTT can facilitate communication between web-based educational tools and hardware platforms without adding complexity for educators.
Highlighted the suitability of MQTT for IoT-centric wireless sensor networks interfacing with the Internet and implementing cloud-based machine learning algorithms. They discussed MQTT's advantages, disadvantages, and its compatibility with IoT applications, particularly in semantic data extraction and device integration.
One proposed an SDN-based fog computing architecture with integrated broker functionalities at edge switches. They found that this architecture significantly improved message delivery throughput compared to traditional setups involving clients and end hosts.
B. Comparison of MQTT with Other IoT Protocols
A survey conducted a detailed evaluation of four widely used messaging protocols: MQTT, CoAP, AMQP, and HTTP for IoT systems. This study provides an overall comparison of the characteristics of these protocols, offering insights into their strengths and limitations through in-depth analysis based on various criteria. By considering static components and empirical evidence from the literature, the author presents a comprehensive overview of messaging protocols, aiding end-users in selecting the most suitable protocol for their requirements. A paper compared the performance of MQTT with protocols based on ICN architecture and HTTP. They proposed enhancements to MQTT for better performance and concluded that MQTT performs better than HTTP. They suggest that protocols based on ICN architecture are better suited for IoT systems. An experimental evaluation of AMQP and MQTT protocols over unstable and mobile networks, assessing message loss, latency, jitter, and saturation boundary values. Their findings indicate that AMQP follows a LIFO order during message bursts, while MQTT maintains packet delivery order. Additionally, AMQP prioritizes security, whereas MQTT is more energy-efficient. The authors recommend using AMQP for building reliable messaging platforms over WLAN and MQTT for connecting edge nodes in constrained environments.
C. Limitations of MQTT
A paper illustrated the lightweight design principle of MQTT, which omits data encryption during transmission. While several MQTT brokers implement encryption as a separate feature via TLS, this adds overhead. The default plaintext data exchange in MQTT poses a significant security threat. A meaningful paper examined the increasing security attacks on smart devices communicating over networks using various IoT protocols. They highlighted security issues surrounding MQTT and other protocols, noting the unequal abilities of MQTT-based broker implementations for entity authentication or encryption. The authors reviewed existing security methods for securing communication channels and proposed a novel approach called "Value-to-Keyed-Hash Message Authentication Code (Value-to-HMAC)," which achieves better performance than traditional symmetric-key encryption algorithms without compromising information integrity.
V. SUMMARY OF RESEARCH TRENDS
Based on our survey findings, MQTT emerges as one of the most widely adopted IoT protocol solutions. While MQTT's lightweight design facilitates data exchange in plaintext, presenting a security concern, many MQTT broker implementations address this by incorporating encryption as an additional feature atop TLS. However, this approach may introduce some performance overhead. Presently, numerous MQTT brokers utilize the CONNECT control type message packet for authentication purposes. Clients are typically required to send usernames and passwords with the CONNECT message to validate the connection; failure to do so results in connection refusal.

VI. ACKNOWLEDGMENT
I would like to extend my sincere gratitude to Mr. Akash for his guidance and support as our university guide. His mentorship has been invaluable in shaping our project and guiding us through its various stages. Additionally we express our appreciation to Mr. Kalpit for his mentorship and support as internship mentor. His expertise and insights have greatly contributed to our learning and professional development.
Conclusion
In the context of the Internet of Things paradigm, fundamental components such as data sources play a pivotal role. Regardless of the communication technology utilized in deploying and operating an IoT/M2M network, the independent data-generating devices heavily depend on specialized messaging protocols designed for M2M communication within IoT applications. This paper introduces a variety of M2M communication protocols that have emerged over the past 20 years and surveys the evolution and usage of MQTT, which stands as the most prevalent M2M/IoT protocol. Through a comprehensive analysis of recent literature, we highlight the main features, advantages, and limitations of the MQTT protocol and its broker implementations compared to other IoT protocols. Our findings, presented through graphs and comparison tables, delve into the current utilization of MQTT and its application areas. Regarding our future endeavors, the plan to conduct detailed performance measurements and usage evaluations of specific MQTT broker implementations as an extension of this study.
References
[1] V. Karagiannis, P. Chatzimisios, F. Vazquez-Gallego, and J. Alonso-Zarate,‘‘A survey on application layer protocols for the Internet of Things,’’ Trans.IoT Cloud Comput., vol. 3, no. 1, pp. 11–17, 2015. [2] Cisco. The Internet of Things Reference Model. Accessed: Aug. 23, 2020.[Online]. Available: http://cdn.iotwf.com/resources/71/IoT_Reference_Model_White_Paper_June_4_2014.pdf [3] Z. Ning, F. Xia, X. Hu, Z. Chen, and M. S. Obaidat, ‘‘Social-oriented adaptive transmission in opportunistic Internet of smartphones,’’ IEEETrans. Ind. Informat., vol. 13, no. 2, pp. 810–820, Apr. 2017, doi:10.1109/TII.2016.2635081. [4] Curtin University. Introduction to the Internet of Things. Accessed:Aug. 23, 2020. [Online]. Available: https://study.curtin.edu.au/offering/mooc-introduction-to-the-internet-of-things–iot1x [5] R. Buyya, J. Broberg, and A. M. Goscinski, Cloud Computing: Principles and Paradigms. Hoboken, NJ, USA: Wiley, 2011.
Copyright
Copyright © 2024 Pujan Hiteshkumar Shah. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET59000
Publish Date : 2024-03-13
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

