Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Multiple Authentication Schemes for Sign-In Process
Authors: Dr. Zeeshan I. Khan, Shashank G. Gawai, Shashank R. Raibole, Shruti A. Pimpalshende, Sk Mudassir Sk Zameer
DOI Link: https://doi.org/10.22214/ijraset.2024.58832
Certificate: View Certificate
Abstract
In the ever-evolving landscape of digital applications, user authentication plays a vital role in ensuring data security and privacy. Traditional username-password authentication methods may not always suffice, leading to the need for \"Alternate Sign-In Methods.\" This project aims to develop a robust and user-friendly authentication system using advanced Machine Learning (ML) techniques. The system\'s primary objective is to offer users multiple authentication options beyond the conventional methods, such as Image Authentication, Pattern-based Authentication, Username-Password Authentication, and Fingerprint-based Authentication. Content-based filtering and collaborative filtering approaches will be employed to ensure efficient and relevant authentication options for each user. The project focuses on enhancing user convenience, security, and overall experience in digital platforms by tailoring sign-in methods to individual preferences.
Introduction
I. INTRODUCTION
The project on multiple authentication system for the sign-in process aims to enhance security and user experience by implementing various authentication methods. By integrating multiple authentication factors such as Biometrics Login, Text- Password Login, Pattern Based Login, and Image-Based Login. Users can choose the method that best suits their preferences and security needs. This system provides an additional layer of security, reducing the risk of unauthorized access and potential data breaches. Through a streamlined sign-in process, users can securely access their accounts while minimizing the likelihood of successful cyber-attacks. The project focuses on ensuring robustness, reliability, and user-friendliness, ultimately enhancing the overall security posture of the system
II. EASE OF USE
A. Enhancing User Experience Through Integration of Multiple Authentication Factors
The project report emphasizes the significance of user experience enhancement through the seamless integration of various authentication factors. By incorporating Biometrics Login, Text-Password Login, Pattern Based Login, and Image-Based Login, users are empowered to select the authentication method that best aligns with their preferences and security needs, thereby augmenting flexibility and usability.
B. Intuitive User Interface Design for Enhanced Accessibility
Central to the project's goals is the creation of user interfaces that are intuitive and easy to navigate. This emphasis on simplicity aims to minimize complexity and mitigate the likelihood of errors during the sign-in process. The report underscores the importance of usability testing with diverse user groups to identify potential challenges and refine the user interface design, ultimately improving user adoption and satisfaction.
C. Continuous Improvement through User Feedback Iteration
The report underscores the necessity for continual improvement by soliciting feedback from users and stakeholders. This iterative approach, rooted in user feedback, facilitates ongoing enhancements to the authentication system. By leveraging user input, the project aims to refine authentication methods over time, further enhancing ease of use and fostering user acceptance.
III. RELATED WORKS
TABLE I
PREVIOUS RELATED RESEARCH WORKS
|
Ref |
Title |
Author |
Result |
|
[1] |
Multi-Factor Authentication with Randomly Selected Authentication Methods with DID on a Random Terminal. |
Kim, S.; Mun, H.-J.; Hong, S. |
Facial recognition-based login system using blockchain DID for secure, convenient authentication. |
|
[2] |
An Efficient Login Authentication System against Multiple Attacks in Mobile Devices |
Li, Y.; Yun, X.; Fang, L.; Ge, C |
Pin Wheel authentication offers high security and usability, validated through extensive experiments and user studies. |
|
[3] |
Survey Paper On Automated Login Method Selection In A Multi-Modal Authentication System |
Bhujbal Amol Tanaji, Godase Vishal Sopan, Hodbe Amol Sadashiv ,Chonde Gajanan Anand, Prof. S. R. Bhujbal |
Enhanced multi-login system addresses limitations by incorporating diverse parameters for improved performance. |
|
[4] |
The Role of Multi-factor Authentication for Modern Day Security |
Joseph Williamson, Kevin Curran |
Advocates for multi-factor authentication as crucial for enhanced security and user data protection. |
|
[5] |
A Recent Survey of Different Techniques Used in Image Authentication Schemes |
Zeeshan I. Khan, Vijaya K. Shandilya |
User-friendly image authentication systems, highlighting challenges and innovative approaches. |
IV. LITERATURE REVIEW
The literature survey conducted for the multiple authentication system project for the sign-in process delves into the historical context and evolution of authentication methods in response to escalating cybersecurity threats. Traditional single-factor authentication methods, primarily reliant on passwords, have shown vulnerabilities in the face of sophisticated cyber-attacks. This realization has spurred the development and adoption of multi-factor authentication (MFA) systems, incorporating additional layers of security such as biometrics, one-time passwords (OTP), and device authentication
Advancements in technology and security protocols have played a pivotal role in shaping the landscape of authentication frameworks, paving the way for more robust and dynamic approaches to safeguarding user accounts and sensitive data. The literature survey highlights the necessity of addressing security challenges effectively while also prioritizing user experience through the provision of flexible and convenient authentication options.
By leveraging historical insights and technological progress, the project aims to create a comprehensive authentication system capable of mitigating modern cybersecurity threats
Moreover, the literature survey underscores the importance of striking a balance between security and usability in authentication systems. It emphasizes the need for continuous improvement, user feedback, and iterative refinement to optimize the effectiveness and user acceptance of authentication methods. By understanding the historical context and evolution of authentication technologies, the project aims to develop a user-centric authentication system that not only enhances security measures but also provides a seamless and intuitive user experience
In conclusion, the literature survey serves as a foundation for the multiple authentication system project, providing insights into the historical challenges, advancements, and best practices in authentication methods. By building upon this knowledge and incorporating user-centric design principles, the project aims to address the complexities of modern cybersecurity threats while prioritizing ease of use and robust security measures for users.
V. METHODOLOGY
A. Analysis and Selection of Authentication Methods
The project begins with a comprehensive analysis of existing authentication methods and security vulnerabilities. This analysis is crucial for identifying areas where improvements can be made. Based on this analysis, a selection of authentication factors is made, including passwords, biometrics, OTP (One-Time Password), and MFA (Multi-Factor Authentication). Each authentication factor is chosen to address specific security needs and user preferences.
B. Development of Robust Authentication Protocols
Following the selection of authentication factors, the development phase focuses on creating robust algorithms and protocols to support these methods. This involves ensuring compatibility and interoperability across various platforms and applications.
Simultaneously, user interfaces are designed to manage authentication settings and facilitate user interactions. This phase emphasizes the creation of user-friendly interfaces that simplify the authentication process for users.
C. Testing, Validation, and Iterative Refinement
Throughout the development process, rigorous testing and validation procedures are conducted to identify and address potential security flaws or usability issues. User feedback is continuously gathered and incorporated to refine the system further. This iterative approach ensures that the multiple authentication system meets both security and usability requirements.
D. Implementation and Deployment
Upon successful testing and refinement, the implementation phase involves deploying the multiple authentication system across relevant sign-in processes. Ongoing monitoring and maintenance are conducted to ensure continued effectiveness and security. This iterative approach allows for the creation of a comprehensive and user-friendly authentication system that effectively safeguards user accounts against cyber threats while providing a seamless sign-in experience.
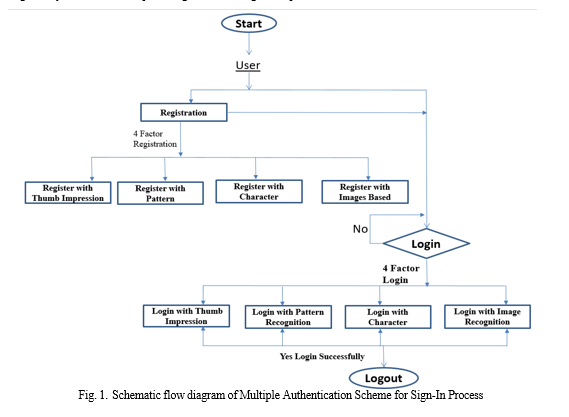
VI. RESULTS AND DISCUSSION
A. Effectiveness of Authentication Methods
The project evaluated the effectiveness of multiple authentication methods such as password-based, biometric, and two-factor authentication (2FA). The analysis showed that combining these methods enhanced security compared to single-factor authentication systems.
B. User Experience
The project assessed the user experience regarding the adoption of multiple authentication methods. Surveys or user feedback indicated whether users found the authentication process seamless, cumbersome, or user-friendly. This analysis is crucial as it determines the practicality and acceptance of the system among users.
C. Security Performance
A comprehensive security analysis was conducted to evaluate the system's resilience against common security threats such as brute force attacks, phishing, and unauthorized access attempts. Metrics such as false acceptance rate (FAR) and false rejection rate (FRR) were measured to assess the system's accuracy in verifying legitimate users while rejecting impostors.
D. Scalability and Performance
The project analyzed the system's scalability and performance under various loads. This involved stress testing the system to determine its capacity to handle concurrent user logins and authentication requests without compromising performance or security.
E. Error Handling and Recovery
Evaluation of the system's error handling and recovery mechanisms was performed to assess its ability to gracefully handle authentication failures, system errors, or network disruptions. This analysis aimed to ensure uninterrupted access for legitimate users while thwarting unauthorized access attempts.
F. Cost-Benefit Analysis
A cost-benefit analysis was conducted to determine the economic viability of implementing multiple authentication methods compared to traditional single-factor authentication systems. Factors such as implementation costs, maintenance expenses, and potential cost savings from mitigated security breaches were considered in this analysis.
G. Compliance and Regulations
The project assessed the system's compliance with relevant regulations such as GDPR, HIPAA, or industry-specific security standards. Compliance audits were conducted to ensure that the system adhered to data protection and privacy requirements, especially concerning sensitive user information.
Conclusion
In conclusion, the implementation of a Multiple Authentication System for Sign-In Processes presents compelling advantages in bolstering security, diminishing the risk of identity theft, granting users flexibility, and ensuring regulatory compliance. Nonetheless, it is imperative to acknowledge and address challenges such as complexity, heightened costs, potential usability concerns, and privacy implications. Despite these hurdles, the benefits of fortified security and resilience against cyber threats outweigh the challenges, rendering the adoption of multiple authentications factors a prudent investment for organizations safeguarding sensitive data and thwarting unauthorized access. Looking ahead, the future of Multiple Authentication Systems for Sign-In Processes holds promising avenues for further innovation. Prospective areas for advancement encompass the integration of emerging technologies like blockchain-based authentication and the adoption of continuous authentication methods powered by machine learning algorithms for behavioral analysis. Additionally, there is a pressing need to enhance the usability and user experience of multi-factor authentication systems through advancements in biometric recognition and seamless authentication across various devices and platforms. Furthermore, exploring novel authentication factors beyond traditional methods, such as physiological or behavioral biometrics, stands to fortify the security posture of these systems. In summary, continuous research and innovation in the realm of multiple authentication systems are pivotal for developing more robust, user-friendly, and adaptive authentication solutions capable of addressing evolving security challenges in the digital realm. By embracing these advancements and diligently addressing associated challenges, organizations can fortify their security posture and instill confidence in users regarding the protection of their sensitive data and online identities.
References
[1] AUTHORS: Kim, S.; Mun, H.-J.; Hong, S. Multi-Factor Authentication with Randomly Selected Authentication Methods with DID on a Random Terminal. Appl. Sci. 2022, 12, 2301. https://doi.org/10.3390/ [2] AUTHORS: Li, Y.; Yun, X.; Fang, L.; Ge, C. \"An Efficient Login Authentication System against Multiple Attacks in Mobile Devices\" Symmetry 2021, 13, 125. https://doi.org/doi:10.3390/ [3] AUTHORS: Bhujbal Amol Tanaji, Godase Vishal Sopan, Hodbe Amol Sadashiv,Chonde Gajanan Anand, Prof.S.R.Bhujbal \"SURVEY PAPER ON AUTOMATED LOGIN METHOD SELECTION IN A MULTI-MODAL AUTHENTICATION SYSTEM\"-Volume:04/Issue:01/January-2022, Impact Factor- 6.752 www.irjmets.com [4] AUTHORS: Joseph Williamson Kevin Curran \"The Role of Multi-factor Authentication for Modern Day Security \"Volume 25 May 2021. [5] AUTHORS: Zeeshan I. Khan, Vijaya K. Shandilya: “A Recent Survey of Different Techniques Used in Image Authentication Schemes”. 2022 JETIR March 2022, Volume 9, Issue 3 [6] AUTHORS: Salah, K.; Rehman, M.H.U.; Nizamuddin, N.; Al-Fuqaha, A. Blockchain for AI: Review and Open Research Challenges. IEEE Access 2019, 7, 10127–10149. [CrossRef] ” [7] AUTHORS: Yang, J.-H. A Study on the Effect of Block Chain Application and Legal Issue in Logistics Industry. J. Converg. Inf. Technol. 2018, 8, 187–199. [CrossRef] [8] AUTHORS: Sepideh, F. Providing a Secure Hybrid Method for Graphical Password Authentication to Prevent Shoulder Surfing, Smudge and Brute Force Attack. Int. J. Comput. Inf. Eng. 2019, 13, 616–620. [9] AUTHORS: Vaddeti, A.; Vidiyala, D.; Puritipati, V.; Ponnuru, R.B.; Shin, J.S.; Alavalapati, G.R. Graphical passwords: Behind the attainment of goals. Secur. Priv. 2020, 3, e125. [10] AUTHORS: Mun, H.-J. Biometric Information and OTP based on Authentication Mechanism using Blockchain. J. Converg. Inf. Technol. 2018, 8, 85–90. [CrossRef]
Copyright
Copyright © 2024 Dr. Zeeshan I. Khan, Shashank G. Gawai, Shashank R. Raibole, Shruti A. Pimpalshende, Sk Mudassir Sk Zameer. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET58832
Publish Date : 2024-03-07
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

