Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Implementing Number Theory in Visual Cryptography for Secure Online Transactions using QR Codes
Authors: Agasthiya Reni Selvasingh, Manikandan K M
DOI Link: https://doi.org/10.22214/ijraset.2023.56117
Certificate: View Certificate
Abstract
In this modern world, due to the excessive availability of the Internet, it is extremely easy for people to communicate and share multimedia contents with each other. Moreover, Online Transactions has also been widely developed, in which secure means of data transfer play the major role. At the same time, secure transfer of personal and copyrighted data has become a critical issue. Visual cryptography (VC) is a useful tool for securing data (i.e. images, texts) that contain sensitive information. As a subset of secret sharing, VC has got importance for its security mechanism, which takes into account both image processing and cryptography. To achieve this goal, we manipulate quick response (QR) code as a container. QR codes generated by a certain system can carry its ordinary message in addition to the secure data. Anyone can read the message, but the secure data can only be obtained using a secret key. In this paper, a specified field of Mathematics, Number Theory is implemented in the concepts of VC for the secure online transactions which is achieved using QR codes.
Introduction
I. INTRODUCTION
Secret sharing of data involves visual cryptography scheme (VCS) which was first proposed by Naor and Shamir in 1995. Based on the original definition of a (k, n)-VCS, a secret image is distributed into n shares in which no secret information will be revealed with possession of fewer than k shares. However, when k or more shares are superimposed, the secret can be easily decrypted. Recently, VCS was developed rapidly and has made great progress in many aspects. All studies contribute a lot to the practical applications of VCS. In earlier times, the only downside of VCS is that the shares in these schemes are meaningless and easily arouse suspicion of some potential attackers when distributed via a public channel. Therefore, the extended VCS (EVCS) was developed as it generates meaningful shares instead of random images. By adding some extra columns into the basic matrices, Wang et al. (Wang, Yi, & Li in 2009) designed a (k, n)-EVCS with poor contrast of shares, to improve its visual performance. And other studies have also been attempted for better results. Nevertheless, the camouflage effect of these shares in VCS schemes was still unsatisfactory since there have been many noisy visible points.
In the time being, Quick Response (QR) code was developed by the Japanese Denso Wave Company. QR code is a two-dimensional code which has been adopted as a universal specification performed by ISO (2006). Such a popularized intelligent terminals, QR codes have been widely used in various fields such as information storage, mobile payment and electronic tickets. For any QR code, we cannot acquire its message by human vision since it is full of dark and light modules which are randomly distributed. These meaningless appearance were similar to the image characteristic of VCS shares. Thus, QR code has considered as the better choice for the mask of VCS share. Therefore, the field of investigations of the VCS and QR codes combinations have attracted considerable attention. In the beginning, QR codes were embedded as a parts of shares to authenticate a VCS by Wang, Liu, & Yan in 2014. Later, a continuous-tone VCS was developed by Yang, Liao, Wu, & Yamaguchi in 2016, where the colour of a secret module was determined by the greyness of black dots. Subsequently, an EVCS based on QR codes was presented with two-level information storage by Liu et al. (Liu, Fu, & Wang, 2016). In this scheme, various standards were to be followed such as a proper scanning, distance and angle are strictly required to decoding the shares, which significantly increases the inconvenience of its practical applications. A (k, n)-EVCS was successful with the help of some concepts of Number Theory. In this method, a secret image to be shared is compressed and encrypted. The process of encryption includes distributing the secret module to n-shares (VCS) and QR code combinations [1].
This simultaneous image compression and encryption technique is an attempt to provide a remedy for both the bandwidth utilization and the encryption problems at the same time. In this paper, Number Theory based Image Compression Encryption (NTICE) is used. NTICE is an algorithm that employs Chinese Remainder Theorem (CRT) in order to generate and solve congruencies and hence obtain simultaneous image compression and encryption.
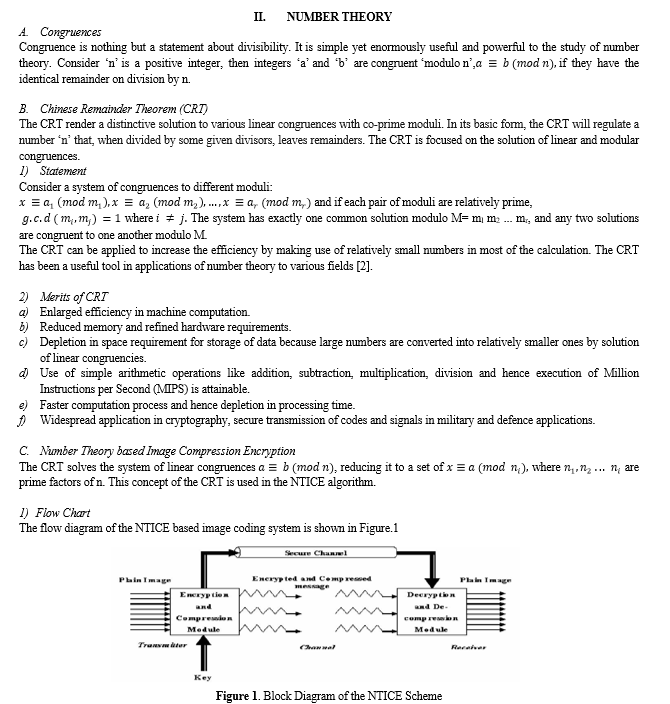

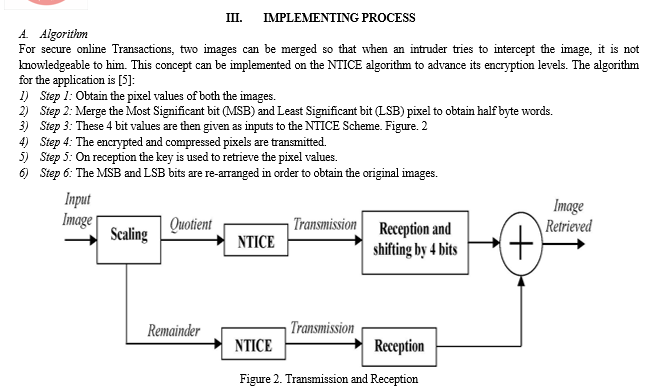
IV. VC FOR QR CODES
The association between VC and QR code is a natural choice, considering that QR code is so widely used nowadays as an information carrier. Recent work is restricted to utilizing the error correction capabilities of the QR code to hide a secret QR code. Utilizing other redundancies in QR code should be a possible direction to explore, including redundancy of un-utilized code words and redundancy of colors. Utilizing the color QR code to design color VC is also a topic worth exploring [4]. Using a color space, more freedom may exist that one can utilize to improve the perceptual quality.
Rani at.al. Proposed a secure system in which they combined between steganography and QR codes [12]. Steganography is considered as the first line of defense in information security as it hides a secret message inside an innocent looking file (container) to transfer the payload under the adversary’s nose without noticing it. Their system consists of two parts. The first one is creating a QR code of the encrypted secret message. The second one is hiding the colored image inside a generated QR code. The concealing process does not generate a visible image distortion and produce a very minimal bit error rate.
Barrera et.al. Implemented a system that utilize QR codes in optical encryption as containers [13]. They choose QR codes as containers in their system because of their tolerance to noise. In addition, QR codes are easy to read using mobile phones’ camera. The results of the proposed method show that their system is more prone to noise compared to normal optical encryption.
Dey et. al. suggested a steganographic system which is based on a randomized intermediate QR host that is embedded with an encrypted secret message [14]. First, the secret message is encrypted then concealed in a QR code. After that, the QR code is camouflaged inside an image. Using double encryption and embedding techniques makes the system hard to break. But on the other hand, it makes the system less time-efficient.
V. SECURE ONLINE TRANSACTIONS
In this technological world, online transaction plays the major role in the transaction methods due to the widely use of e-commerce. Such transactions include online banking and payment on an e-commerce platform, payment through scanning a QR code, and payment using an online social network App. For these transactions to be secure, we need to ensure that both the hardware and the software are secure (i.e.) there exists no Trojan horses unknowingly in the devices.
A Trojan horse is a malicious program, in hardware or in software, residing in a client or a server, trying to compromise the security of a computer system or a communication system. However, considering the diverse sources of Apps and software’s installed on a computer or cell phone, one cannot guarantee that their device is Trojan-free. Using such insecure devices causes our transactions insecure. This maybe because, a Trojan horse may monitor all messages from bank sever to a user’s device and may be able to modify these messages. Furthermore, there are two habitual attacks on the communication between the bank sever and the client computer.
A. (2,2) – VCS algorithm using QR codes
This design makes use of the visual cryptography scheme (VCS) algorithm, which is used to secure transactions between users. It is based on a (2, 2) VCS, where two shares are generated and the two shares are required to be stacked to present the original image.
The algorithm itself is bidirectional, such that the input can be encrypted at one end, then once again decrypted at the other. Both the encryption and decryption of images, the QR codes, are done at the server’s side for increased security as to not allow any possibility of tampering at the client’s side. The service starts with a merchant requesting a payment to be commenced providing a specific amount to be expected. There are various application that creates the accustomed QR code with provided merchant information from the server itself, feeds it into VCS, and transports one of the produced shares to the merchant in the form of a QR code which is to be scanned. The other share will be kept in the server [18]. Scanning the QR code will prompt the server to acquire the related twin share, combine both shares, and complete a successful transaction.
The Figure. 3 presents the process of generating two shadows from a QR code while the right side of the same figure shows the process of verifying a QR code upon scanning.

VI. FUTURE WORKS
The algorithm can be extended to higher levels of encryption and compression by increasing the key length. Also, specialized hardware can be developed for the transmission and reception modules, to calculate the computation time and to deploy Number Theory based Image Compression Encryption.
In this scheme, various standards were to be followed such as a proper scanning, distance and angle are strictly required to decoding the shares, which significantly increases the inconvenience of its practical applications. In future works, these standards can be removed by various algorithms.
Conclusion
In this paper, the implementation of Number Theory in VC for secure online Transaction using QR codes was discussed. These QR codes have been enormously used in recent years since they speed up the payment process and provide users with ultimate convenience. However, QR-based online payment systems are vulnerable to different types of attacks. Hence, transaction processing must be secured to protect the integrity and confidentiality of every payment process. Moreover, the online payment system need to provide authenticity for both the sender and receiver of each transaction. In this paper, the online transaction security of the proposed QR-based system is provided using visual cryptography. This algorithm provides a simple and user-friendly interface for users to carry out payment transactions in user-friendly secure environment. The online payment technology has evolved greatly in businesses and has vastly enhanced customer experience. As the payment process is invisible to the user, technological substitutions are looking for ways to make the payment process faster, more secure, and innovative. In online payments, no mistakes can be afforded as the convenience of online payment systems has also opened up an extensive set of cyber-attacks. These attacks include data theft, denial of service, fraud and forgery, among others. The security of the proposed system is unique in the sense that it adapts a one-in-all algorithm to provide the needed security services: confidentiality, integrity, and authentication, using visual cryptography embedded through Number Theory.
References
[1] Yuqiao Cheng, Zhengxin Fu, Bin Yu, Gang Shen, General Construction for Extended Visual Cryptography Scheme Using QR Codes, International Journal of Digital Crime and Forensics Volume 11, Issue 1, January-March 2019. [2] Residue number system, http://en. wikipedia. orglw/index.php?title=Residuenumber_system&oldid= 71288485. [3] Vikram Jagannathan, Aparna Mahadevan, R. Hariharan and E. Srinivasan, Number Theory Based Image Compression Encryption and Application to Image Multiplexing, IEEE - ICSCN 2007, MIT Campus, Anna University, Chennai, India. Feb. 22-24, 2007. Pp 59-64. [4] Andr, P.S., Ferreira, R.A.S.: Colour multiplexing of quick-response (QR) codes. Electron. Lett. 50(24), 1828–1830 (2014). [5] Vikram Jagannathan, Aparna Mahadevan, Hariharan R., Srinivasan E., \"Simultaneous color image compression and encryption using number theory\", Proceedings of ICIS 05, 2005, pp. 1. [6] Yan, B., Xiang, Y., Hua, G.: Improving the visual quality of size-invariant visual cryptography for grayscale images: an analysis-by-synthesis (AbS) approach. IEEE Trans. Image Process. 28(2), 896–911 (2019). [7] Bin Yan, Yong Xiang, Guang Hua, Improving Image Quality in Visual Cryptography, Signals and Communication Technology, more information about this series at http://www.springer.com/series/4748, ISSN 1860-4862 ISSN 1860-4870 (electronic) Signals and Communication Technology ISBN 978-981-13-8288-8 ISBN 978-981-13-8289-5 (eBook). [8] Cheng, Y., Fu, Z., Yu, B.: Improved visual secret sharing scheme for QR code applications. IEEE Trans. Inf. Forensics Secur. 13(9), 2393–2403 (2018). [9] Nisha, S., Madheswari, A.N.: Prevention of phishing attacks in voting system using visual cryptography. In: 2016 International Conference on Emerging Trends in Engineering, Technology and Science (ICETETS), pp. 1–4 (2016). [10] Yan, B., Chen, N., Yang, H.M., Hao, J.J.: Local blackness preserving visual cryptography for grayscale secret images. J. Inf. Hiding Multimed. Signal Process. 9, 370–382 (2018). [11] Yan, B., Xiang, Y., Hua, G.: Improving the visual quality of size-invariant visual cryptography for grayscale images: an analysis-by-synthesis (AbS) approach. IEEE Trans. Image Process. 28(2), 896–911 (2019). [12] S. R. M. Mary and E. K. Rosemary, ‘‘Data security through QR code encryption and steganography,’’ Adv. Comput., Int. J., vol. 7, nos. 1–2, pp. 1–7, Mar. 2016. [13] J. F. Barrera, A. Mira, and R. Torroba, ‘‘Optical encryption and QR codes: Secure and noise-free information retrieval,’’ Opt. Express, vol. 21, no. 5, pp. 5373–5378, Mar. 2013. [Online]. Available: http://www. opticsexpress.org/abstract.cfm?URI=oe-21-5-5373 [14] S. Dey, K. Mondal, J. Nath, and A. Nath, ‘‘Advanced steganography algorithm using randomized intermediate QR host embedded with any encrypted secret message: ASA_QR algorithm,’’ Int. J. Mod. Educ. Comput. Sci., vol. 4, no. 6, pp. 59–67, Jun. 2012. [15] S. Tiwari, \"An Introduction to QR Code Technology,\" 2016 International Conference on Information Technology (ICIT), Bhubaneswar, 2016, pp. 39-44. [16] Kamal, Sawsan & Ameen, Basheer. (2016). A New Method for Ciphering a Message Using QR Code. Computer Systems Science and Engineering. 6. 19-24. [17] M. F. Tretinjak, \"The implementation of QR codes in the educational process,\" 2015 38th International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), Opatija, 2015, pp. 833-835. [18] Jianfeng Lu, Zaorang Yang, Lina Li, Wenqiang Yuan, Li Li, and Chin- Chen Chang, “Multiple Schemes for Mobile Payment Authentication Using QR Code and Visual Cryptography,” Mobile Information Systems, vol. 2017, Article ID 4356038, 12 pages, 2017. [19] Yang, Ching-Nung & Liao, Jung-Kuo & Wu, Fu-Heng & Yamaguchi, Yasushi. (2016). “Developing Visual Cryptography for Authentication on Smartphones”. 189-200. 10.1007/978-3-319-44350-8_19. [20] Sangeeta Singh. May 2016. “QR Code Analysis” International Journal of Advanced Research in Computer Science and Software Engineering,Volume 6, Issue 5, ISSN: 2277 128.
Copyright
Copyright © 2023 Agasthiya Reni Selvasingh, Manikandan K M. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET56117
Publish Date : 2023-10-12
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

