Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Optimizing Kubernetes Environments: Best Practices for Configuring and Managing Admission Webhooks
Authors: Naresh Kumar Amrutham
DOI Link: https://doi.org/10.22214/ijraset.2024.64789
Certificate: View Certificate
Abstract
Kubernetes has emerged as the leading platform for container orchestration, offering a robust framework for automating the deployment, scaling, and management of containerized applications. As its adoption increases, managing diverse workloads across various environments becomes increasingly complex, necessitating mechanisms for policy enforcement, compliance assurance, and dynamic configuration management. In Kubernetes, admission webhooks provide a means to intercept requests, enabling the mutation and validation of these requests to enforce custom policies. This paper presents comprehensive guidelines for configuring and operating admission webhooks to enhance security, consistency, and operational efficiency in Kubernetes environments. Through this paper, readers will gain hands-on experience in implementing best practices, thereby optimizing the use of admission webhooks to effectively maintain organizational policies and standards.
Introduction
I. INTRODUCTION
Kubernetes is an open-source container orchestration platform initially developed by Google and now maintained by the Cloud Native Computing Foundation (CNCF) [1]. It is designed to automate the deployment, scaling, and management of containerized applications. As the de facto standard for container orchestration, Kubernetes provides a robust framework for running distributed systems with resilience. By abstracting the underlying infrastructure, it allows developers to focus on application development while ensuring high availability, scalability, and efficient resource utilization.
As the adoption of Kubernetes grows, so does the complexity of managing diverse workloads across various environments. This complexity necessitates mechanisms for enforcing policies, ensuring compliance, and dynamically automating configuration changes. Admission webhooks in Kubernetes address these needs by offering a flexible and powerful method to intercept and modify requests made to the Kubernetes API server [2]. They enable cluster administrators to implement custom logic for validating and mutating resources, ensuring that all objects adhere to organizational policies and best practices before being persisted in the cluster. This capability is crucial for maintaining security, consistency, and operational efficiency in modern cloud-native environments.
This paper aims to provide comprehensive guidelines on configuring and operating admission webhooks to ensure they are both efficient and reliable. By following these guidelines, administrators can enhance the security, consistency, and operational efficiency of their Kubernetes environments. Additionally, the paper demonstrates the improvements achievable through the implementation of these best practices, offering readers a hands-on approach to optimizing their use of admission webhooks.
II. BACKGROUND
A. Kubernetes Architecture
Kubernetes is a powerful container orchestration platform that automates the deployment, scaling, and management of containerized applications. At the heart of Kubernetes architecture is the kube-apiserver, which acts as the central management entity for the cluster [3]. The kube-apiserver is responsible for exposing the Kubernetes API, which is used by all components both within and outside of the cluster to communicate and manage the state of the resources.
Below provides an overview of the key Kubernetes components and their roles:
- API Server: The API server also known as kube-apiserver is the central management entity for the entire Kubernetes cluster [3]. It exposes the Kubernetes API, processes REST operations, validates them, and updates the corresponding objects in etcd. As the primary point of interaction for cluster management, the API server's performance and availability are critical to the overall health of the cluster.
- Etcd: etcd is a distributed key-value store that serves as Kubernetes' backing store for all cluster data [4]. It ensures consistency and provides reliable data storage for the cluster state. The health and performance of etcd directly impact the stability of the entire Kubernetes cluster.
- Scheduler: The Kubernetes scheduler is responsible for assigning newly created Pods to nodes [5]. It watches for Pods with no assigned node and selects an appropriate node for them to run on, considering factors such as resource requirements, hardware/software/policy constraints, and affinity/anti-affinity specifications.
- Controller Manager: The Controller Manager runs controller processes that regulate the state of the system, attempting to move the current state towards the desired state [6]. It includes controllers for various Kubernetes resources such as ReplicaSets, Deployments, and Services.
- Kubelet: The Kubelet is an agent that runs on each node in the cluster. It ensures that containers are running in a Pod and reports node and Pod status to the API server. The Kubelet plays a crucial role in maintaining the health of individual nodes and the Pods running on them [7].
Below shows a high-level architecture of Kubernetes cluster with key components.
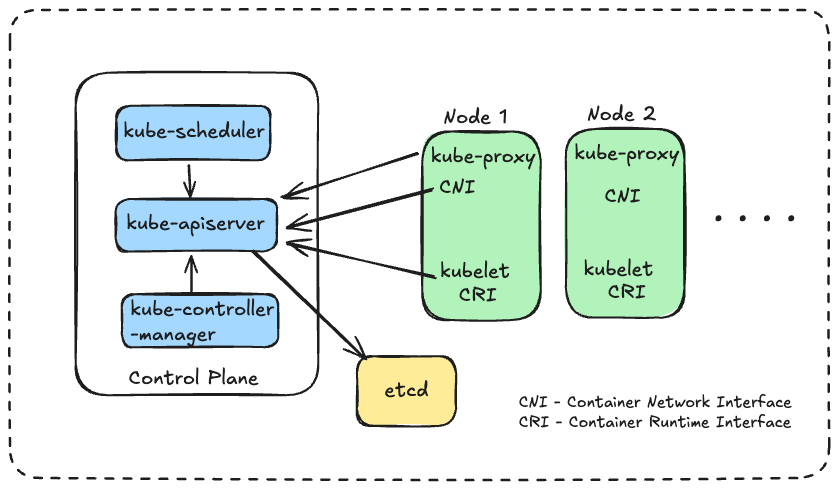
Fig. 1. Architecture of a Kubernetes cluster. From "Enhancing Kubernetes Observability: A Synthetic Testing Approach for Improved Impact Analysis," by Naresh Kumar Amrutham, IJRASET, 2024, p. 469.
The kube-apiserver is particularly relevant to our discussion of admission webhooks. It serves as the front-end for the Kubernetes control plane, processing RESTful API requests, validates them, and updates the state of the resources accordingly. All interactions with the cluster, originating from users, controllers, or any other components should pass through the kube-apiserver. This centralized communication model makes the kube-apiserver an ideal point for implementing admission control mechanisms.
B. Admission Control
Admission control is a critical component of the Kubernetes API request lifecycle. It takes place after an API request has been authenticated and authorized, but before the object is persisted in the etcd database. Admission controllers are plugins that intercept requests to the kube-apiserver, allowing them to modify or reject requests based on custom logic. Figure 2 illustrates the flow of an API request through admission webhooks. At a high level, these admission webhooks take an admission review request as input, mutate or validate the resource included in the request, and return an admission response indicating whether the request is allowed or denied.
Admission webhooks are HTTP callbacks that receive admission requests and do something with them. There are two types of admission webhooks, validating admission webhook and mutating admission webhook. Mutating admission webhooks are invoked first, and can modify objects sent to the API server to enforce custom defaults.
After all object modifications are complete, and after the incoming object is validated by the API server, validating admission webhooks are invoked and can reject requests to enforce custom policies.
- A ValidatingAdmissionWebhook is used to validate requests to the Kubernetes API server. It allows you to enforce custom policies by rejecting requests that do not meet certain criteria.
- A MutatingAdmissionWebhook is used to modify requests to the Kubernetes API server. It allows you to automatically change or add fields to objects before they persisted.
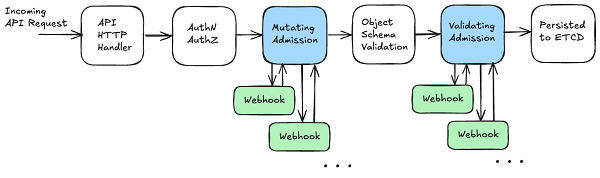
Figure 2: Request flow and component interaction in the Kubernetes API server, emphasizing the admission control phase. Inspired by https://kubernetes.io/blog/2019/03/21/a-guide-to-kubernetes-admission-controllers/
III. CONFIGURING ADMISSION WEBHOOKS
Kubernetes enables the extension of admission controllers by dynamically configuring which resources are subject to specific admission webhooks through the use of ValidatingWebhookConfiguration or MutatingWebhookConfiguration.
The following is an example ValidatingWebhookConfiguration, a MutatingWebhookConfiguration is similar. See the webhook configuration section for details about each config field.
apiVersion: admissionregistration.k8s.io/v1
kind: ValidatingWebhookConfiguration
metadata:
name: "pod-policy.example.com"
webhooks:
- name: "pod-policy.example.com"
rules:
- apiGroups: [""]
apiVersions: ["v1"]
operations: ["CREATE"]
resources: ["pods"]
scope: "Namespaced"
clientConfig:
service:
namespace: "example-namespace"
name: "example-service”
caBundle: <CA_BUNDLE>
admissionReviewVersions: ["v1"]
sideEffects: None
failurePolicy: fail
timeoutSeconds: 5
Let’s expand some of the options that have a significant impact on the way the api requests are handled.
A. Timeouts
Setting appropriate timeouts for webhooks is crucial for maintaining the performance and reliability of both the webhook server and the Kubernetes API server. The timeout configuration determines how long the API server waits for a response from a webhook before considering the call as failed. Below explains why configuring an appropriate timeout is necessary:
- Performance Impact: A longer timeout means that requests can remain in flight for extended periods, especially if the webhook or its dependencies are experiencing issues. This can lead to increased latency and reduced throughput for the API server, as it has to manage these pending requests.
- Resource Utilization: Prolonged timeouts can tie up resources, potentially leading to bottlenecks that affect the entire cluster's performance.
- Default and Recommendations: As of the time of writing, the default timeout for a webhook call is 10 seconds. It is generally recommended to use shorter timeouts to quickly fail and retry or handle errors, thus minimizing the impact on the API server's performance.
- Handling Timeouts: If a webhook call times out, the request is processed according to the webhook's failure policy, which determines whether the request should be allowed or denied.
B. Scope
Defining the scope of webhooks is essential to ensure they only intercept relevant requests, thereby optimizing performance and reducing unnecessary processing.
- Namespace Selector: namespaceSelector option allows you to specify which namespaces the webhook should apply to. By using label selectors, you can target specific namespaces, ensuring that the webhook only processes requests from those namespaces.
- ObjectSelector: Similar to `namespaceSelector`, objectSelector option allows you to filter requests based on labels on the objects themselves. This is useful for targeting specific resources within a namespace.
- Scope Types:
- Namespaced: The webhook will only be triggered for resources that are within a specific namespace. This is useful when you want the webhook to apply only to resources that are scoped to a namespace, such as Pods, Services, or Deployments.
- Cluster: The webhook will only be triggered for cluster-scoped resources. These are resources that are not tied to any specific namespace, such as Nodes, PersistentVolumes, or CustomResourceDefinitions (CRDs).
- *: The webhook will be triggered for both namespaced and cluster-scoped resources. This setting is used when you want the webhook to apply universally across all types of resources in the cluster.
By carefully defining the scope, you can reduce the load on the webhook server and ensure that only pertinent requests are intercepted.
C. Failure Policy
Failure policies determine how the API server should handle webhook failures, such as timeouts or errors.
- Ignore: If the webhook fails, the API server ignores the failure and continues processing the request. This policy is useful for non-critical webhooks where availability is more important than strict enforcement. Use `Ignore` for webhooks that provide additional functionality but are not essential for the operation of the cluster.
- Fail: If the webhook fails, the API server rejects the request. This policy is suitable for critical webhooks where enforcement of policies is essential, even at the cost of availability. Use `Fail` for webhooks that enforce security or compliance policies where failure to enforce could lead to significant issues.
D. Side Effects
Specifying side effects in webhook configurations is important for understanding and managing the impact of webhook operations. Declaring side effects helps Kubernetes understand whether a webhook modifies resources outside of the admission request. This is crucial for operations like dry runs, where no actual changes should be made. Below are the available options:
- None: The webhook does not have any side effects.
- NoneOnDryRun: The webhook has side effects, but they are not executed during a dry run.
By accurately specifying side effects, you ensure that the webhook behaves predictably and that Kubernetes can handle operations like dry runs correctly. This is particularly important for maintaining the integrity and reliability of the cluster's operations.
IV. RUNNING WEBHOOK SERVICES
A. Deployment Considerations
- Resource Allocation: Allocate sufficient CPU and memory resources to handle the expected load. Under-provisioning can lead to performance bottlenecks, while over-provisioning can waste resources. Use Kubernetes resource requests and limits to ensure that webhook services have the necessary resources while preventing them from consuming excessive resources that could impact other workloads.
- Scaling: Implement horizontal scaling to handle increased load. Use Kubernetes Horizontal Pod Autoscaler (HPA) to automatically adjust the number of replicas based on CPU utilization or custom metrics. Consider the use of load balancers to distribute incoming requests evenly across multiple instances of the webhook service.
- High Availability: Deploy webhook services in a highly available configuration to prevent single points of failure. This can be achieved by running multiple replicas across different nodes. Use Kubernetes features like Pod Disruption Budgets to maintain a minimum number of available replicas during maintenance or upgrades.
B. Security Best Practices
Securing webhook communications is critical to protect sensitive data and ensure the integrity of the admission control process:
- TLS Encryption: Use Transport Layer Security (TLS) to encrypt communications between the Kubernetes API server and webhook services. This prevents eavesdropping and tampering with data in transit. Ensure that webhook services are configured with valid TLS certificates, and consider using a certificate management solution like cert-manager to automate certificate issuance and renewal.
- Authentication and Authorization: Implement authentication mechanisms to verify the identity of clients connecting to the webhook service. This can be done using client certificates or other authentication methods. Use role-based access control (RBAC) to restrict access to the webhook service, provide only required access that webhook is required to interact with.
C. Monitoring
Effective monitoring is essential for maintaining the performance and reliability of webhook services. This section highlights the key metrics that should be tracked.
1) controller_runtime_webhook_latency_seconds:
- This metric is a histogram representing the latency of processing admission requests by the webhook controller runtime [8].
- Latency histograms help in analyzing the distribution of request processing times, enabling the detection of slow or stalled requests.
- Monitoring this metric assists in ensuring that admission decisions are made promptly, which is critical for maintaining the responsiveness of the Kubernetes API server.
2) controller_runtime_webhook_requests_in_flight:
- Indicates the current number of admission requests being actively processed by the webhook.
- Tracking the number of in-flight requests helps in understanding the webhook's load and concurrency level.
- An unusually high number of concurrent requests may signal performance issues or the need for scalability improvements.
3) apiserver_admission_webhook_admission_duration_seconds:
- This histogram measures the latency of admission webhooks from the perspective of the Kubernetes API server. It is identified by the webhook name and is broken down by operation, API resource, and type (validating or mutating) [9].
- Provides insights into how admission webhooks impact the overall latency of API server operations.
- Monitoring this metric can help in optimizing admission webhook performance to reduce their impact on API server responsiveness.
4) apiserver_admission_webhook_rejection_count:
- Counts the number of times admission requests are rejected by webhooks. It identifies rejections by webhook name, admission type (validating or mutating), operation, and includes labels for error types and rejection codes.
- Counts the number of times admission requests are rejected by webhooks. It identifies rejections by webhook name, admission type (validating or mutating), operation, and includes labels for error types and rejection codes.
- A high rejection rate may indicate issues with the admission policies or that clients are frequently attempting invalid operations.
5) Additional Metrics: Track metrics that provide information on the current number of webhook service replicas and cgroup resource usage—such as CPU, memory. Monitoring these metrics ensures that the webhook services are appropriately scaled and operating within resource constraints, aiding in performance optimization and resource management.
V. BEST PRACTICES AND RECOMMENDATIONS
Effective configuration and management of admission webhooks are essential for maintaining a secure, efficient, and reliable Kubernetes environment. This section summarizes key guidelines and best practices for setting up and operating admission webhooks, ensuring their optimal performance and contribution to the cluster's overall health.
A. Minimize Dependencies for High Throughput
Having numerous dependencies in a webhook service can lead to increased latency and reduced throughput, especially under high load conditions. Each additional dependency introduces potential points of failure and can slow down the admission process if those services are unresponsive or slow.
- Simplify Dependencies: Design webhook services to be as stateless and self-contained as possible.
- Example: If a webhook needs to validate configurations against a standard set of rules, embed these rules within the webhook service rather than fetching them from an external service on each request.
B. Implement Appropriate Timeouts
Dependencies, such as external services or databases, may become unresponsive or experience delays. Without proper timeouts, webhooks could hang while waiting for responses, leading to increased latency to kube-apiserver.
- Set Dependency Timeouts: Configure timeouts for all external calls within the webhook to prevent indefinite waits.
- Example: When calling an external policy service, set a timeout of 2 seconds. If the service does not respond within this time, the webhook should handle the timeout gracefully, possibly by rejecting the request or using a default policy.
C. Utilize Caching Mechanisms
For data that does not change frequently (stationary data), repeatedly fetching it from external sources can be inefficient.
- Implement Caching: Use in-memory caches or local data stores to hold stationary data, refreshing it at defined intervals.
- Example: Cache commonly used configurations or policy data within the webhook pod, updating the cache every 5 minutes.
D. Avoid Circular Dependencies on the API Server
Webhooks that rely on the Kubernetes API server can create circular dependencies, especially if the API server depends on the webhook's responsiveness to process requests.
- Use Informers: Leverage Kubernetes informers to watch and cache resource states locally, reducing direct calls to the API server.
- Example: Instead of querying the API server for resource states during each webhook invocation, use informers to maintain an up-to-date local cache.
E. Analyze and Plan for Throughput
Understanding the expected load on your webhook is crucial for resource planning and ensuring performance requirements are met.
- Estimate Throughput and Perform Performance Analysis: Analyze historical data or conduct load testing to estimate request volumes and assess webhook performance under load.
- Example: Estimations can be made by analysing the request rate from various clients and historical data.
F. Leverage Horizontal Pod Autoscaling (HPA)
Workloads in Kubernetes can be variable, and webhooks need to scale accordingly to handle peak loads.
- Implement HPA: Configure Horizontal Pod Autoscalers to automatically adjust the number of webhook replicas based on CPU utilization or custom metrics.
- Example: Set up HPA to scale the webhook deployment between min and max replicas based on CPU usage exceeding 70%.
G. Ensure Pod Disruption Budgets (PDBs) are Configured
To maintain high availability, especially during cluster maintenance events or node failures, it is important to ensure that a minimum number of webhook replicas are always running.
- Configure PDBs: Establish Pod Disruption Budgets for webhook deployments to restrict the number of pods that can be voluntarily evicted at any one time.
- Example: Set a PDB that requires at least 2 out of 3 replicas to always be available.
H. Conduct Peer Reviews
Code and configuration changes can introduce unexpected issues. Peer reviews help catch potential problems early.
- Implement Peer Review Processes: Have webhook code and configuration changes reviewed by team members before deployment.
- Example: Use code review tools like Gerrit or GitHub Pull Requests to facilitate reviews, focusing on logic correctness, security implications, and compliance with best practices.
I. Target Specific Resources
Webhooks should be scoped to operate only on the resources they are intended to manage to improve efficiency and reduce unnecessary processing.
- Use Namespace and Object Selectors: Configure webhooks with namespaceSelector and objectSelector fields to limit their scope.
- Example: A webhook intended to enforce policies on Pods in the production namespace should be configured with a namespaceSelector that includes only that namespace.
J. Avoid Circular Deployment Dependencies
Deploying webhooks that interfere with their own deployment process can lead to deadlocks and deployment failures.
- Exclude Webhook Resources from Webhook Configuration: Ensure that webhooks do not act on the resources necessary for their own deployment.
- Example: Configure the webhook to ignore resources having labels “admission-webhook/ignore=true”, and apply this label to the webhook's deployment resources.
K. Return Correct Admission Response Codes
Returning appropriate HTTP status codes is essential for the API server and clients to correctly interpret the outcome of admission webhook processing.
- Ensure Accurate Response Codes: Implement logic in webhooks to return the correct status codes based on the outcome of the admission review.
- Example:
- Return HTTP 200 OK with allowed: true in the admission response when a request is permitted.
- Return HTTP 403 Forbidden with allowed: false and a meaningful message when a request is denied due to policy violations.
- Return HTTP 500 Internal Server Error when an unexpected error occurs within the webhook.
Conclusion
In conclusion, as Kubernetes solidifies its position as the leading platform for container orchestration, the complexity of managing diverse workloads necessitates robust mechanisms for policy enforcement and resource management. Admission webhooks are crucial in this ecosystem, enabling administrators to implement custom logic for validating and mutating requests made to the Kubernetes API server. This capability not only enhances security and compliance but also ensures that all resources adhere to organizational standards before being persisted in the cluster. This paper has provided comprehensive guidelines for effectively and reliably configuring and operating admission webhooks. By focusing on key aspects such as timeout settings, scope definition, failure policies, and security best practices, administrators can optimize the performance of their webhook services while minimizing potential risks. Adopting these guidelines allows organizations to enhance the operational efficiency, security, and consistency of their Kubernetes deployments, ultimately leading to more resilient and manageable cloud-native applications. As Kubernetes continues to evolve, the importance of admission webhooks will only increase, making it essential for practitioners to stay informed about best practices and emerging trends in this area. By leveraging the power of admission webhooks, organizations can ensure that their Kubernetes environments remain secure, compliant, and optimized for the demands of modern application development.
References
[1] Cloud Native Computing Foundation, \"Kubernetes,\" CNCF Projects, 2024. [Online]. Available: https://www.cncf.io/projects/kubernetes/ [2] Kubernetes Documentation, \"Dynamic Admission Control,\" Kubernetes.io, 2024. [Online]. Available: https://kubernetes.io/docs/reference/access-authn-authz/extensible-admission-controllers/ [3] Kubernetes Documentation, \"kube-apiserver,\" Kubernetes Components Reference, 2024. [Online]. Available: https://kubernetes.io/docs/reference/command-line-tools-reference/kube-apiserver/ [4] CoreOS, \"etcd: A distributed, reliable key-value store,\" etcd Documentation, 2024. [Online]. Available: https://etcd.io/ [5] Kubernetes Documentation, \"kube-scheduler,\" Kubernetes Components Reference, 2024. [Online]. Available: https://kubernetes.io/docs/reference/command-line-tools-reference/kube-scheduler/ [6] Kubernetes Documentation, \"kube-controller-manager,\" Kubernetes Components Reference, 2024. [Online]. Available: https://kubernetes.io/docs/reference/command-line-tools-reference/kube-controller-manager/ [7] Kubernetes Documentation, \"kubelet,\" Kubernetes Components Reference, 2024. [Online]. Available: https://kubernetes.io/docs/reference/command-line-tools-reference/kubelet/ [8] Kubernetes Special Interest Groups, \"Controller Runtime Webhook Metrics,\" GitHub Repository, 2024. [Online]. Available: https://github.com/kubernetes-sigs/controller-runtime/blob/main/pkg/webhook/internal/metrics/metrics.go [9] Kubernetes Documentation, \"Kubernetes Metrics Reference,\" Instrumentation Guide, 2024. [Online]. Available: https://kubernetes.io/docs/reference /instrumentation/metrics/
Copyright
Copyright © 2024 Naresh Kumar Amrutham. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET64789
Publish Date : 2024-10-25
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

