Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Overview of Mobile Technologies in 5G Networking and Communication
Authors: V. Sheela, Dr. P. Rathiga
DOI Link: https://doi.org/10.22214/ijraset.2024.58924
Certificate: View Certificate
Abstract
Fifth-generation technology (5G) is a more recent generation of mobile networks used in wireless communication. Everyone has access to high-speed internet via 5G at anytime, anyplace. 5G is a little bit different because of its new functions, which include linking people and controlling machines, objects, and devices. Differentiated performance and capability brought about by the 5G mobile system will create new user experiences and link new businesses. As a result, it\'s critical to understand how the business may profit from 5G. In this paper presents an evaluation in the area of mobile communication technologies. Technologies including MIMO (Multiple Input Multiple Output), beamforming, network slicing, mm wave frequency, small cell, different antenna technology and mobile edge computing are also included in 5G.
Introduction
I. INTRODUCTION
Mobile networks have grown significantly over the past few years and wireless communication protocols are now common place in our day-to-day activities. Cellular network architecture has continuously improved in order to handle
The rising volume of traffic (voice, data, call, message etc..) and growing user base. Scholars have been searching for improved methods in order to get larger bandwidth, faster connection time and smooth handoffs [1]. In this regard 5G seeks to accomplish some fundamental but highly challenging tasks, such providing extremely high data rates for users travelling at fast speed or ensuring an uninterrupted handover for users. In order to develop a future standard that can enhance the Quality of Service (QoS) in terms of throughput, mobility etc., this has drawn a lot of research attention. Despite being two competing technologies LTE (Long Term Evaluation), Standarazied by 3GPP and worldwide interoperability for Microwave Access (WiMAX), based on IEEE Standards are identical in technical aspects [2][3]. Internet protocol such as IPv4, IPv6, IPv4v6, Ethernet and unstructured are among the protocol data unit session types that are supported, to provide additional characteristics like flexibility, configurability and scalability 5G networks will leverage virtualization and softwarization[4].
The goal of the 5G communication networks is to provide services that totally integrate society and cater to the many needs of highly mobile systems(high throughput, low latency, and enormous connections). Ensuring the specification of human centric cohabitation with machine-type applications part of the different function and performance requirements of 5G Communication networks. With its many cutting-edge technologies supporting a wide range of applications, 5G’s foundation is dynamic, logical, consistent and adaptable. According to the 3GPP NR, the functional division between the two networks (CN and RAN) and the complete architectural structure of the RAN and Core Network were reevaluated. The mobile communication network in contrast to its predecessors, uses a more intelligent architecture that is not limited by Base Station (BS) proximity. Besides intricate infrastructure limitations. Rather it features a flexible deployment that makes use of cutting-edge ideas like Network Function virtualization (NFA), Software Defined Networking (SDN) and Network Slicing(NS) [5][6].
A. Progression from 1G to 5G
First Generation [1G]: The first-generation mobile communication access techniques like FDMA and AMPS. The transmission utilized circuit switching with a data rate of 2.4 kbps, operating in the 800MHz frequency band. The bandwidth was analog, catering to voice applications, allowing people to communicate through talking.
Second Generation [2G]: In the second generation of mobile communication, access techniques such as GSM, TDMA (Time Division Multiple Access) and CDMA (Code Division Multiple Access) were introduced. Transmission utilized circuit switching, achieving a data rate of 10kbps. Operating in frequency bands like 800MHz, 900MHz,1800MHz and 1900MHz, with a bandwidth of 25MHz, 2G facilitated both voice and data applications. Users could now send messages and enjoy improved data services while on the move.
Third Generation [3G]: In the third-generation mobile communication, access techniques such as WCDMA, UMTS, CDMA 2000 and enhancements like HSUPA/HSDPA emerged. Transmission employed both circuit and packet switching, incorporating error correction through turbo codes. With data rate ranging from 384 kbps to 5 mbps, 3G operated across frequency bands like 800MHz, 850MHz, 900MHz, 1800MHz, 1900MHz and 2100MHz, offering a 25MHz bandwidth. This generation supported a wide array of applications, including voice, data and video calling, allowing users to surf the internet and explore mobile applications with enhanced experiences.
Fourth Generation [4G]: In the fourth-generation mobile communication, access techniques like LTE-A, OFDMA(Orthogonal Frequency Division Multiplexing), SC-FDMA and WiMax were introduced. Transmission utilized packet switching with error correction mechanisms like turbo codes. Offering impressive data rates ranging from 100Mbps to 200Mbps, 4G Operated in frequency bands initially at 2.3GHz, 2.5GHz and 3.5GHz, with a Bandwidth of 100MHz. This generation supported various applications, including voice, data, video calling, HD television and online gaming. The focus was on sharing voice and data seamlessly over fast broadband internet, driven by a unified network architecture and the IP Protocol.
Fifth Generation [5G]: In the fifth-generation mobile communication, access techniques such as BDMA, NOMA (Non-Orthogonal Multiple Access), FBMC and CACA were implemented. Transmission relied on packet switching with error correction using LDPC. The data rates soared from 1.8 GHz, 2.6GHz to 30-300 GHz, with a wide bandwidth spanning 30-300 GHz. This generation expanded beyond mobile internet, supporting applications like voice, data, video calling, ultra HD video and virtual reality. Notably 5G Extended its capabilities to include IoT and V2X, enhancing broadband wireless services.
Table 1: 1G to 5G with techniques
|
Generation |
Techniques |
|
1G |
FDMA, AMPS etc., |
|
2G |
GSM, TDMA, CDMA etc., |
|
3G |
WCDMA, UMTS, CDMA 2000, HSUPA/HSDPA etc., |
|
4G |
LTE-A, OFDMA, SC-FDMA, WiMax etc., |
|
5G |
BDMA, NOMA, FBMA, CACA, MIMO etc., |
II. APPLICATION OF 5G
5G is faster than 4G and offers remote-controlled operation over a reliable network with zero delays. It provides up to 20Gbps of downlink maximum throughput. Furthermore, 5G Compatible with 4G World Wide Wireless Web [7].The application of 5G is diverse and extends far beyond traditional mobile communication. It enables
- Enhanced Mobile Broadband
- Ultra Reliable Low Latency Communication
- Massive Machine Type Communication
- Mission-critical Communication
- Fixed Wireless Access
- Augmented Reality and Virtual Reality
- Smart infrastructure
- Vehicle- to- everything
- Enhanced Mobile Broadband (eMBB): 5G provides significantly faster data rates, facilitating improved mobile internet experiences, Ultra HD Streaming and faster downloads.
- Ultra Reliable Low Latency Communication (URLLC): Its using with reduced latency, 5G supports applications requiring near real time responses, such as autonomous vehicles, remote surgeries and critical industrial processes.
- Massive Machine Type Communication (mMTC): 5G accommodates a massive number of connected devices, enabling the internet of things to flourish. This includes smart cities, smart homes and various IoT applications.
- Fixed Wireless Access: 5G Facilitates high speed wireless internet access for homes and businesses acting as a viable alternative to traditional wired broadband.
- Augmented Reality (AR) and Virtual Reality (VR): 5G is high data rates and low latency enhances AR and VR experiences, opening up possibilities for immersive applications like virtual meetings and gaming.
- Smart Infrastructure: 5G enables the development of smart infrastructure, including smart grids, smart transportation systems, and intelligent city planning.
- Vehicle-to-Everything (V2X): 5G Supports communication between vehicles and other entities, improving road safety, traffic management and enabling connected transportation systems.
The 5G revolutionizes connectivity by providing faster speeds, lower latency and increased capacity, fostering innovations across various industries and transforming how we interact with technology.
III. THE TECHNOLOGY OF 5G
5G Technology represents fifth generation of mobile communication standards, bringing about significant advancements compared to its predecessors. The most recent developments in Frequency Bands, New Waveform Technology, Massive MIMO, Beam forming, Network Slicing, Low Latency, SDN (Software Defined Networking), NFV (Network Function Virtualization) and Enhanced Security techniques are covered in this part.
A. Frequency Band Techniques
5G Operates in a range of frequency bands, including sub-6 GHz frequencies for widespread coverage and Figure 1 cover the higher frequency millimeter wave(mmWave) bands for enhanced data rates[9][10].
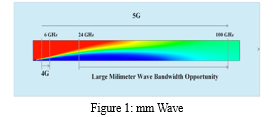
The wireless communications refer to specific ranges of radio frequencies allocated for various purposes. Each frequency band has unique characteristics and is utilized for specific technologies.
- Low-Frequency Band (sub-1GHz): These bands including sub-1GHz frequencies provide wide coverage and better penetration through obstacles. They are often used for long-race communication, such as in rural areas. In 5G, sub-6GHz frequencies fall into this category.
- Mid-Frequency Band (1-6 GHz): Frequencies in this range offer a balance between coverage and data rates. Many existing cellular networks, like 4G LTE, Operate with in range. 5G also utilizes mid frequency bands for widespread coverage and improved capacity[8].
- High-frequency Bands (above 6GHz): mmWave frequencies fall into this category. While they offer very high data rates, they have shorter range and are more susceptible to signal blockage by obstacles. 5G uses high frequency bands for enhanced data rates in densely populated areas[8][9][10].
Different frequency bands serve different purposes in wireless communication, and a combination of these is often used to achieve a balance between coverage, capacity and data rates. The allocation of frequency bands is regulated by international bodies to avoid interference and ensure efficient spectrum utilization[10].
B. New Waveform Techniques
5G employs advanced waveform technologies such as orthogonal frequency division multiplexing(OFDM) and Filter Bank Multicarrier(FBMC) to efficiently transmit data over the airwaves [11].
- OFDM (Orthogonal Frequency Division Multiplexing (OFDM): It is dividing the total bandwidth into multiple orthogonal subcarriers, each carrying a part of the data. Some advantages OFDM is highly resistant to frequency selective fading and allows for efficient spectrum utilization. It mitigates the impact of multipath interference, making it suitable for high data rate transmission [11].
- FBMC (Filter Bank Multi-Carrier): It is also dividing the spectrum into subcarriers, but it uses filter banks to shape the signals in the time and frequency domains. Some advantages FBMC provides improved spectral efficiency, reduced out-of-band emissions, and better performance in scenarios with highly dispersive channels. It is particularly beneficial in environments where traditional OFDM might face challenges.
These wave form technologies play a crucial role in achieving the goals of 5G, such as higher data rates, improved spectral efficiency and enhanced reliability [11] [12].
C. Massive MIMO Techniques
MIMO technology involves using a large number of antennas at both the base station and the device, improving network capacity, data rates and overall performance.
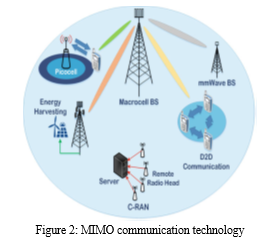
Multiple Input Multiple Outputs: It involves using multiple antennas at both the transmitter (base station) and receiver (user device) to improve communication performance. Figure 2., Here some benefits of MIMO enhancing the data rates, reliability and overall system capacity by exploiting spatial diversity and multipath propagation [13][14].
Massive MIMO: It takes the concept of MIMO to a new level by deploying a large number of antennas, often dozens or even hundreds, at the base station. Some benefits of with a massive number of antennas, Massive MIMO brings several advantages, including increased spectral efficiency, better coverage, improved signal quality and enhanced interference management [14].
Spatial Multiplexing: Massive MIMO leverages the large array of antennas to simultaneously transmit multiple data stream to multiple users a technique known as spatial multiplexing. This spatial multiplexing capability significantly boosts the networks capacity, allowing more users to be served simultaneously [15].
D. Beamforming Techniques
The Beamforming is commonly used in Wi-Fi routers, cellular base stations, and other wireless communication system to enhance coverage and throughput. Figure 3, 5G utilizes beam forming techniques, directing signals toward specific users rather than broadcasting uniformly. This improves efficiency, signal strength and overall network performance. Beamforming allows the concentration of radio frequency energy in a specific direction rather than broadcasting signals uniformly in all directions [16].
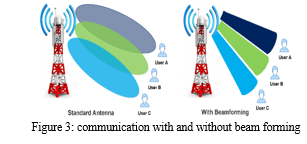
The Dynamically adjusting the phase and amplitude of the transmitted signals from multiple antennas, beam forming steers the signals to reach the intended destination more effectively [17]. They are two types of Beamforming (i) Analog Beamforming (ii) Digital Beamforming.
Analog Beamforming: Its adjust the phase and amplitude of signals at the radio frequency level using analog components. It is simpler but less flexible.
Digital Beamforming: It involves adjusting the signals in the digital domain, offering more flexibility and precision. Digital beamforming is computationally intensive but provides better control.
Some advantages of Beamforming techniques improve signal strength, increased range and Enhanced capacity.
E. Network Slicing
Network allows operators to create virtual network slice tailored for specific applications or services, providing optimized performance and resources based on the requirements of each slice. Network slicing enables the creation of independent, virtualized networks(slices) on a common underlying physical network infrastructure [18].
Each network slice operates as if it were a dedicated network, with its own resources, characteristics and functionalities. Here some benefits of network slicing (i) customization (ii) optimized performance.
- Customization: Network slicing allows customization of network parameters to meet specific requirements of diverse services and application.
- Optimized performance: Different slices can be tailored for specific use cases, optimizing performance for varying demands such as low latency for critical applications or high data rates for broadband services.
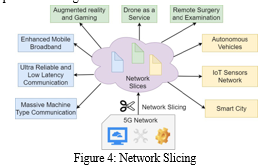
Customization: Network slicing allows customization of network parameters to meet specific requirements of diverse services and application.
Optimized performance: Different slices can be tailored for specific use cases, optimizing performance for varying demands such as low latency for critical applications or high data rates for broadband services.
Here some key components of network slicing (i) Core Network (ii) Radio Access Network
Core Networks: Each Networks slice has its own virtualized core network, providing services and managing traffic independently.
Radio Access Network: Slices can also have dedicated portions of the radio access network, optimizing connectivity.
F. Low Latency
5G aims for ultra-low latency, reducing the time takes for data to travel between devices and the network. This is crucial for application requiring real-time responsiveness, such as augmented reality and autonomous vehicles. It refers to the minimal delay or lag in the transmission of data between two points in a network [19]. In the communication systems including the internet and wireless networks, low latency indicates a quick and near instantaneous response time between sending a command or request and receiving the corresponding acknowledgement. Here some Key points in Low latency
- Response time
- Real Time Communication
- Critical Systems
- Latency materials
- 5G and Low latency
Low latency is a critical characteristic in networks and communications systems, ensuring minimal delays and enabling swift and real time interactions between connected devices or users.
G. SDN and NFV
5G Networks leverages SDN and NFV to enhance the flexibility and scalability, enabling more efficient management and deployment of network resources. SDN separates the control plane from the data plane in networking devices, allowing centralized control and programmability of network resources. Its introduces a software layer known as the SDN Controller, that manages and directs traffic flow in the network [20]. Some key features of SDN (i) Centralized Control (ii) Programmability. The Benefits of SDN its using the improved flexibility and efficient resource utilization.
NFV involves virtualizing and decoupling traditional network function such as routers, firewalls and load balancers from dedicated hardware appliances. These network functions are then implemented as software applications that can run on standard hardware. Some features of Virtualized network function and dynamic scaling. Some benefits of NFV using Cost efficiency and rapid deployment.
H. Enhanced Security Techniques
In 5G focus on improved security features, including better encryption protocols and authentication mechanisms to safeguard user data and network integrity. Enhanced security Techniques of networking and communication involves advanced measures to protect data, systems and users from potential threats.
Here some techniques using the enhances security techniques (i) Encryption (ii) Multi Factor Authentication (iii) Zero trust security model (iv) Network segmentation (v) Intrusion Detection and Prevention Systems (vi) Security information and event management (vii) End point Protection (viii) Application Security (ix) Blockchain Technology (x) Threat Intelligence.
Encryption: It involves encoding data in a way that only authorized parties can access it. Advanced encryption algorithms enhance the security of data transit and at rest safeguarding it from unauthorized access [21].
Multi Factor Authentication: MFA adds ab extra layers of security by requiring users to provide multiple forms of identification before gaining access to a system. This often involves a combination of password, biometrics or security token.
Zero trust Security model: Its assume that no entity, whether inside or outside the network, should be trusted by default. Access controls and authentication are continuously evaluated, minimizing the risk of unauthorized access.
Network Segmentation: Its divides a network into isolated segments, limiting the potential impact of a security breach. It helps contain and prevent lateral movement of attackers within the network.
Intrusion Detection and Prevention Systems: Monitors network or system activities for malicious behaviour or security policy violations. It can detect and responds to threats in real time, helping to prevent unauthorized access or attacks.
Security Information and Event Management: Systems collect and analyze log data from various sources in real time to detect and respond to security incidents. They provide insights into potential threats and help in compliance monitoring.
Endpoint Protection: Advanced end point protection includes antivirus, anti-malware and other security features designed to secure individual devices (end points) from various cyber threats.
Application Security: Measures involve securing software applications from security threats. This includes code reviews, vulnerability assessments, and the use of security frameworks to protect against common exploits.
Blockchain Technology: In Certain applications, blockchain technology used to enhance security through decentralized and tamper resistant data storage. It ensures the integrity and transparency of transactions.
Threat Intelligence: Involves gathering information about potential threats and vulnerabilities to better understand and defend against cyber threats. It helps organizations stay proactive in their security measures [22].
Conclusion
In This paper comparing the technology of 5G, The mobile network development from 1G to 5G applications, various research organizations their efforts, and the salient characteristics of 5G. This study includes a thorough comparison of several authors technology on various 5G Technologies in Frequency Bands, New Waveform Technology, Massive MIMO, Beam forming, Network Slicing, Low Latency, SDN, NFV and Enhanced Security techniques. This comparison also highlights the significance of these recently developed technologies and the creation of a secure, scalable, low-latency, and dependable 5G network.
References
[1] H.Harry and T. Antti, “LTE for UMTS Evolution to LTE advanced “, Second edition john wily and sons, Ltd., 2014. [2] Y. Chun-Chuan, C. Jeng-Yueng, M. Yi-Teng, and L. Ching-Hsiang, “Adaptive load based and channel -aware power saving for non-real-time traffic in LTE,” EURASIP journal on wireless communication and networking, pp 1-13, 2015. [3] P. Nevres, S.Sargento, F. Fontes, T.M. Bohnert and J. monterio “Quality of Service Differentiation in Wi MAX Networks”, Trends in Telecommunication Technologies. [4] Vision on software networks and 5G white paper, pp.1-38 jul 2017.[online] Available: https://5g-ppp.eu/wp-content/uploads/2014/02/5G-PPP_SoftNets_WG_whitepaper_v20.pdf. [5] S. Ahmadi, 5G NR: Architecture Technology Implementation and Operation of 3GPP New Radio Standards, New Delhi, India:Academic, 2019. [6] 5G; System Architecture for the 5G System (3GPP TS 23.501 Version 15.2.0 Release 15), vol. 15, pp. 4-220, 2018. [7] Agiwal, M.Roy, A. Saxena, N. Next generation 5G Wireless networks: A comprehensive survey. IEEE Common, surv 2016, 18, 1617-1655. [8] Pi, Z.; Khan, F. An introduction to millimeter-wave mobile broadband systems. IEEE Commun. Mag. 2011, 49, 101–107. [Google Scholar] [CrossRef] [9] Busari, S.A.; Mumtaz, S.; Al-Rubaye, S.; Rodriguez, J. 5G millimeter-wave mobile broadband: Performance and challenges. IEEE Commun. Mag. 2018, 56, 137–143. [Google Scholar] [CrossRef] [10] Hong, W.; Baek, K.H.; Ko, S. Millimeter-wave 5G antennas for smartphones: Overview and experimental demonstration. IEEE Trans. Antennas Propag. 2017, 65, 6250–6261. [Google Scholar] [CrossRef] [11] Mehta, H.; Patel, D.; Joshi, B.; Modi, H. 0G to 5G mobile technology: A survey. J. Basic Appl. Eng. Res. 2014, 5, 56–60. [Google Scholar] [12] Buzzi, S.; Chih-Lin, I.; Klein, T.E.; Poor, H.V.; Yang, C.; Zappone, A. A survey of energy-efficient techniques for 5G networks and challenges ahead. IEEE J. Sel. Areas Commun. 2016, 34, 697–709. [Google Scholar] [CrossRef] [Green Version] [13] Chataut, R.; Akl, R. Massive MIMO systems for 5G and beyond networks—Overview, recent trends, challenges, and future research direction. Sensors 2020, 20, 2753. [Google Scholar] [CrossRef] [PubMed] [14] Vouyioukas, D. A survey on beamforming techniques for wireless MIMO relay networks. Int. J. Antennas Propag. 2013, 2013, 745018. [Google Scholar] [CrossRef] [15] Mae, M.; Ohnishi, W.; Fujimoto, H. MIMO multirate feedforward controller design with selection of input multiplicities and intersamplebehavior analysis. Mechatronics 2020, 71, 102442. [Google Scholar] [CrossRef] [16] Vouyioukas, D. A survey on beamforming techniques for wireless MIMO relay networks. Int. J. Antennas Propag. 2013, 2013, 745018. [Google Scholar] [CrossRef] [17] Rashid-Farrokhi, F.; Liu, K.R.; Tassiulas, L. Transmit beamforming and power control for cellular wireless systems. IEEE J. Sel. Areas Commun. 1998, 16, 1437–1450. [Google Scholar] [CrossRef] [Green Version] [18] Ni, J.; Lin, X.; Shen, X.S. Efficient and secure service-oriented authentication supporting network slicing for 5G-enabled IoT. IEEE J. Sel. Areas Commun. 2018, 36, 644–657. [Google Scholar] [CrossRef] [19] Parvez, I.; Rahmati, A.; Guvenc, I.; Sarwat, A.I.; Dai, H. A survey on low latency towards 5G: RAN, core network and caching solutions. IEEE Commun. Surv. Tutor. 2018, 20, 3098–3130. [Google Scholar] [CrossRef] [20] Bhatt, C.; Sihag, V.; Choudhary, G.; Astillo, P.V.; You, I. A Multi-Controller Authentication approach for SDN. In Proceedings of the 2021 International Conference on Electronics, Information, and Communication (ICEIC), Jeju, Korea, 31 January–3 February 2021; pp. 1–4. [Google Scholar] [21] Nowaczewski, S.; Mazurczyk, W. Securing Future Internet and 5G using Customer Edge Switching using DNSCrypt and DNSSEC. J. Wirel. Mob. Netw. Ubiquitous Comput. Dependable Appl. 2020, 11, 87–106. [Google Scholar] [22] Abhishta, A.; van Heeswijk, W.; Junger, M.; Nieuwenhuis, L.J.M.; Joosten, R. Why would we get attacked? An analysis of attacker’s aims behind DDoS attacks. J. Wirel. Mob. Netw. Ubiquitous Comput. Dependable Appl. 2020, 11, 3–22. [Google Scholar].
Copyright
Copyright © 2024 V. Sheela, Dr. P. Rathiga. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET58924
Publish Date : 2024-03-11
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

