Ijraset Journal For Research in Applied Science and Engineering Technology
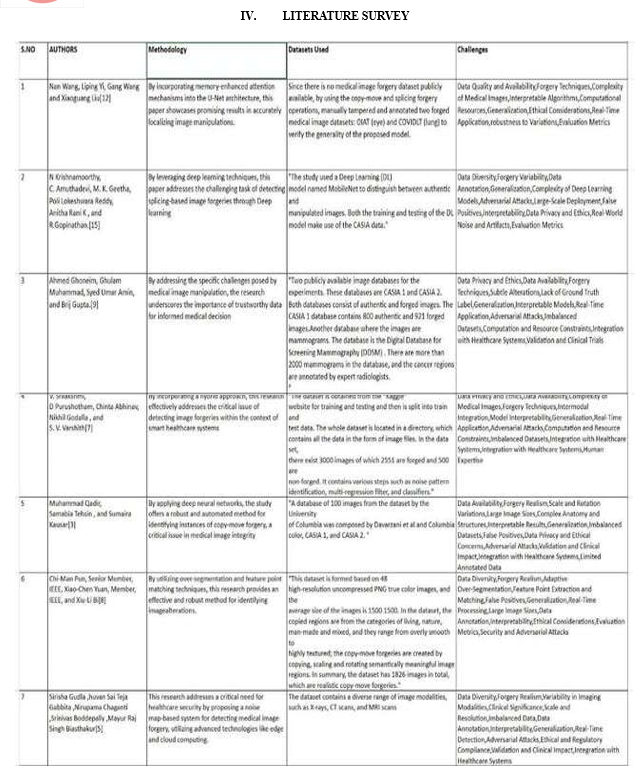
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
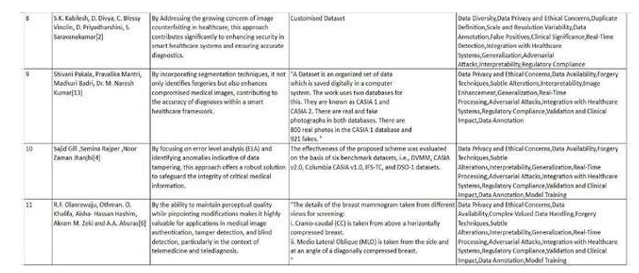
Securing Medical Imaging: A Comprehensive Review and Prospective Paths for Image Authentication
Authors: Aruna S, Akkidasari Varshitha, K L Kalpana, Yash Santosh Karwa, Jyothi R
DOI Link: https://doi.org/10.22214/ijraset.2024.59323
Certificate: View Certificate
Abstract
As medical image authentication systems depend more and more on cutting-edge technologies, the integrity and dependability of diagnostic procedures are seriously threatened by adversarial attacks. This abstract reviews the latest advancements in Deep Learning (DL)-specific image forgery detection techniques, highlighting common splicing and copy-move attacks as well. This survey covers a wide range of methods used in medical image forgery detection and highlights the role that sophisticated models play in maintaining the accuracy of medical images. The study looked at a range of deep learning and machine learning models as well as methods for isolating photos and using Generative Adversarial Networks (GANs) to detect tampering. The results showed that it is possible to reliably recognize intentionally created anomalies in medical imaging. The case studies show that deep learning performs exceptionally well in correctly identifying scans with injected tumours, especially when it comes to the localization of the region of interest. This works well in situations where localization is not feasible, as reduced-negativespace scans show.
Introduction
I. INTRODUCTION
Medical diagnosis and treatment planning have undergone a dramatic transformation in recent years due to the extensive incorporation of digital imaging technologies. Digital imaging modalities have smoothly replaced film-based radiography, improving medical procedures' efficiency but also posing new problems with regard to the quality and authenticity of medical images. The increasing dependence on digital medical imaging raises serious concerns for researchers and healthcare professionals regarding the possibility of malevolent manipulations and inadvertent adjustments.
A rising number of people are worried about the authenticity and integrity of digital images because of its widespread use in many different fields. With the use of a wide range of methods, image forgery detection has become an important field that protects digital image integrity while revealing modifications. Investigating both active and passive approaches, this study focuses on the use of CT GAN-based techniques as it explores the complex field of image forgery detection. Digital signatures and watermarking are examples of active forgery detection techniques that are essential to keeping digital images unchangeable. Passive methods of detecting forgeries, such as picture splicing and copy-move methods, use sophisticated algorithms and, most importantly, include CT GAN to improve the accuracy of identifying modified elements in images. This research limits its attention to the widely used techniques of image splicing and copy-move detection in the context of medical imaging, where the consequences of fraud can be fatal. The CT-GAN framework is one example of an adversarial technology that offers vulnerabilities that the research highlights and that could jeopardize the integrity of 3D medical images. The study delves into a thorough investigation of multiple strategies, including convolutional neural networks (CNNs), hybrid models, and deep learning techniques, to identify and counteract picture manipulation. It analyzes these techniques' effectiveness critically, pointing out both their advantages and disadvantages, and it deals with the constantly changing problems that emerge from new technology in the field of picture fraud detection. The following chapters cover copy-move forgery detection with CNNs, new segmentation techniques, and aggregation with Bayesian Sum Rule (BSR). Furthermore, in order to strengthen image forgery detection in smart healthcare systems, the research assesses the effectiveness of support vector machines and extreme learning machines in hybrid models.The paper presents a comprehensive overview of the state of picture forgery detection today by highlighting developments in the area while being open about the shortcomings and difficulties encountered by current approaches. By investigating these issues, the study hopes to add to the current discussion on picture authenticity by highlighting advancements and weaknesses in the field of counterfeit detection and suggesting new lines of inquiry.
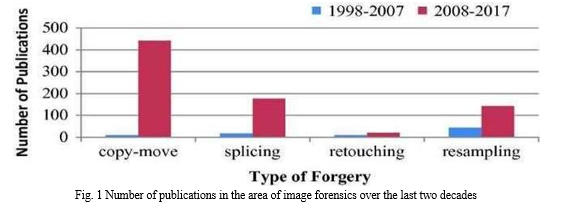
A lot of study has been done in the field of image forgery detection in the last ten years. Figure 1 presents a bar chart that shows the number of publications pertaining to four different categories of forgery detection techniques (copy-move, image splicing, resampling, and retouching)[1] from 1998 to 2017. The detection of copy-move forgeries has significantly increased over the past ten years, highlighting the identification of image splicing. On the other hand, retouching detection has gotten relatively less attention, probably because it is thought to offer a lesser risk because altered images are usually not used for illegal activities. [14]
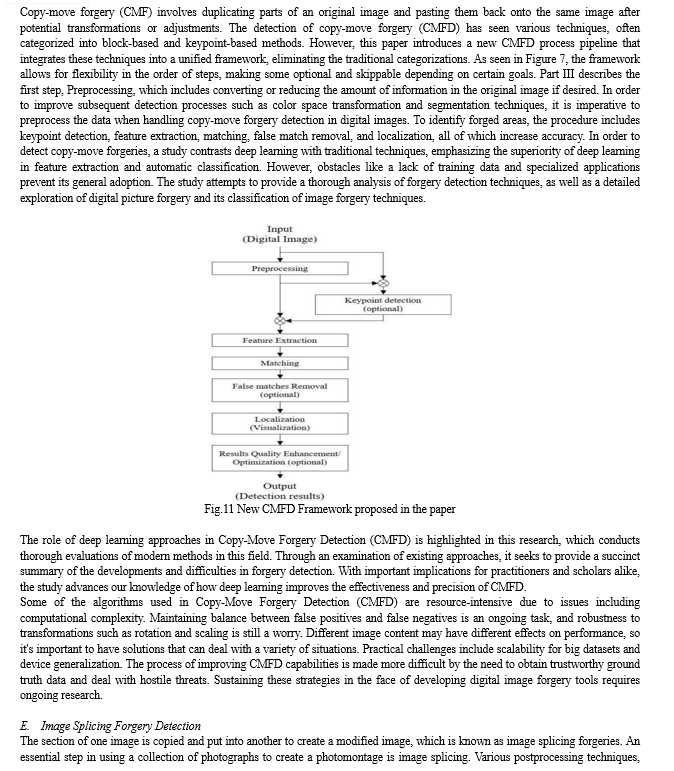
II. TYPES OF DETECTIONS
Image forgery detection employs a range of techniques to ascertain and validate the legitimacy of digital images. These strategies encompass both passive tactics, such as identifying image splicing and detecting copy-move forgery, as well as active methods like employing digital signatures and watermarks. The overarching goal is to expose various forms of image manipulation while upholding the integrity of the visual content.[1] The two primary categories of image forgery detection techniques are:
A. Techniques for Identifying Active Forgeries
- CT GAN-Based Approaches: Integrating cutting-edge advancements, like CT GAN (Generative Adversarial Network) technology, offers a robust means of ensuring tamper resistance. CT GANs can be employed to generate synthetic images that serve as digital signatures, harnessing cryptographic techniques for authentication.[21]
- Digital Watermarking: Digital watermarking remains a stalwart method, introducing visible or invisible watermarks to images for traceability and authentication. This aids in swiftly identifying any unauthorized alterations, complementing the efforts of CT GAN-based approaches.
B. Methods for Detecting Passive Forgeries
- Copy-Move Forgery Detection
Incorporating CT GAN in the copy-move forgery detection process enhances the precision of identifying duplicate elements within an image. The synergy of CT GAN with block-based analysis, brute force, or keypoint-based algorithms fortifies the capability to detect subtle manipulations. [3, 17, 18]
2. Picture Splicing Forgery Detection
The detection of picture splicing forgeries undergoes refinement through CT GAN interventions. By amalgamating segments from various sources, CT GAN aids in recognizing modified images more effectively, thus fortifying the overall passive forgery detection. [15, 20]
3. Image Retouching
The focus on identifying alterations made to specific regions within an image gains added sophistication with the integration of CT GAN-based approaches. This ensures a nuanced understanding of subtle retouching, contributing to comprehensive forgery detection.
In the realm of medical imaging, the two prevalent forgery detection methods revolve around image splicing and copymove detection. This discussion will delve deeper into these approaches, shedding light on their applications and efficacy in the context of medical imagery.





B. Image Tampering Detection in Smart HealthCare
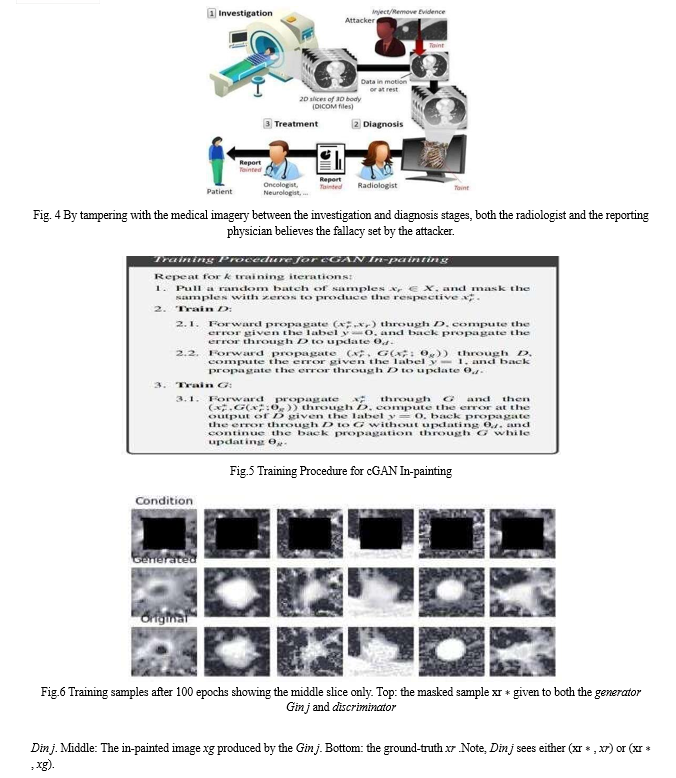
The term "smart health" (s-health) was first used by A. Solanas et al. [19] in their study, which examined how electronic and mobile health services intersect with smart city settings. The widespread use of information and communication technologies (ICT) in urban settings is responsible for the rise of smart cities, and the combination of ICT and mobile technologies in the healthcare industry has led to the development of electronic health services and ubiquitous patient monitoring.The authors introduce s-health, a novel idea that aims to combine electronic and mobile health services with smart city integration, in recognition of the need for a unified framework. The paper establishes the foundation for targeted research, addressing obstacles, and foreseeing countless opportunities for the advancement of healthcare in the future by defining the scope of s-health.
The concept of S-health, which was presented in this talk, goes beyond M-Health (mobile health) to include smart city sensing. Although both ideas share health technology, there are some significant distinctions between them. Patient data serves as the main information source in mobile health, with a constant focus on the user. However, by combining data from a second, independent source—the sensing infrastructure of a smart city—s-health goes beyond patient-generated data.This distinction modifies information flows in addition to expanding the sources of information. In contrast to m-health, which is focused on individualized user-centric data exchange, s-health addresses both user- and city-centric issues. The integration of smart city data impacts not just personal health results but also more general urban behavioural changes. One example is when ambulances arrive on time by modifying traffic lights, which goes above and beyond what can be done with conventional mobile health interventions.
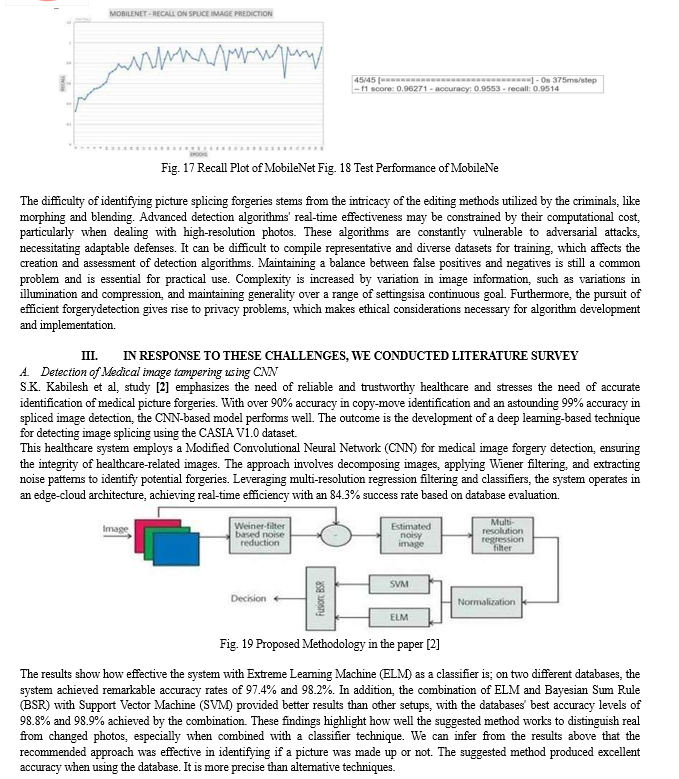
While edge computing and the Internet of Things enable Smart Healthcare Systems (SHS) to provide enhanced security, flexibility, and efficiency, V. Srilakshmi [7] highlights the susceptibility of system integrity to image fraud. Extreme Learning Machines (ELM) and Support Vector Machines (SVM) are two methods used in a suggested model for image forgery detection to address this problem. The findings are aggregated using the Bayesian Sum Rule (BSR). By incorporating this model into SHS, security is improved, system vulnerabilities are decreased, and the integrity of vital medical images used in treatment operations is guaranteed.
It contains various steps such as noise pattern identification, multi-regression filter, and classifiers. This is shown in the following six steps:
- Step 1: To create the red, green, and blue components, convert the raw image.
- Step 2: For every component, apply a different Weiner filter.
- Step 3: Subtract filtered image from raw image to obtain noise pattern.
- Step 4: By applying a multi-regression filter to process the noise pattern, weights depending on image intensity are provided.
- Step 5: Feed the weighted output through different kernels into SVM and ELM classifiers. Step 6:To get the final result, combine the classifier scores using the Bayesian sum algorithm.
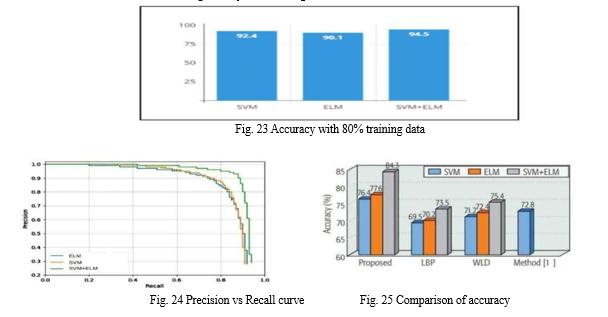
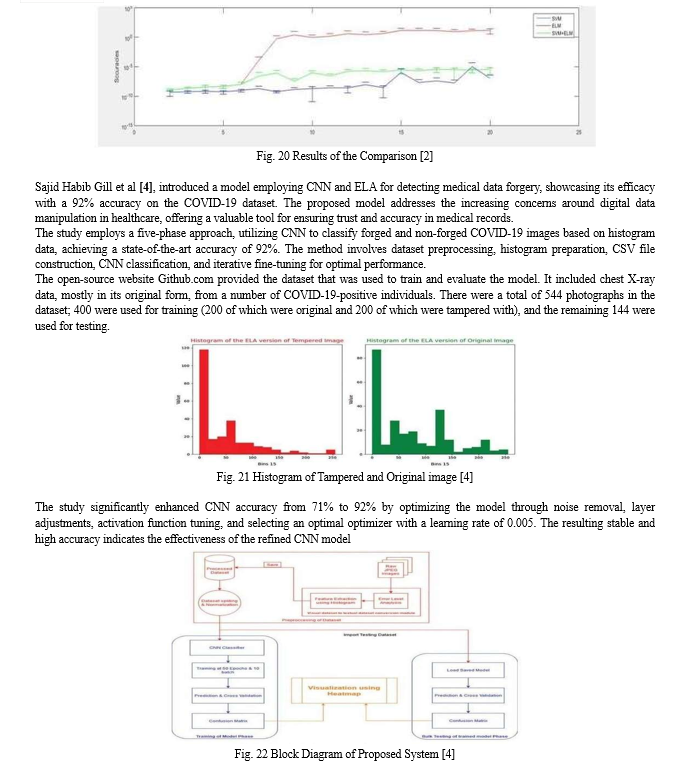
The results show that the hybrid model, which combines SVM and ELM, detects photo forgeries with a higher accuracy of 94.5% than the individual accuracies of SVM (92.4%) and ELM (90.1%). The proposed method, which makes use of core cloud resources as well as edge computing, is adaptable to a range of use cases. Its ability to successfully classify forged and unforged photographs serves as an example of this, demonstrating the synergy between edge computing empowerment and the potency of the SVM-ELM combination.
C. Other Approaches Related to Medical Image Forgery Detection
Rithin Krishna Dilipkumar [10] highlighted the need for strong cybersecurity measures in the context of medical picture forgeries and the possible repercussions of incorrect diagnoses and unethical practices in his study. This worry stems fromthe fact that medical professionals are not required by law to verify the authenticity of medical photos, which emphasizes the significance of precise detection methods.
The main objective of the study is to provide a trustworthy approach for identifying changed medical photographs. The goal of this project is to reduce the possibility of false positives and stop any abuse, which could have serious consequences for the healthcare sector.
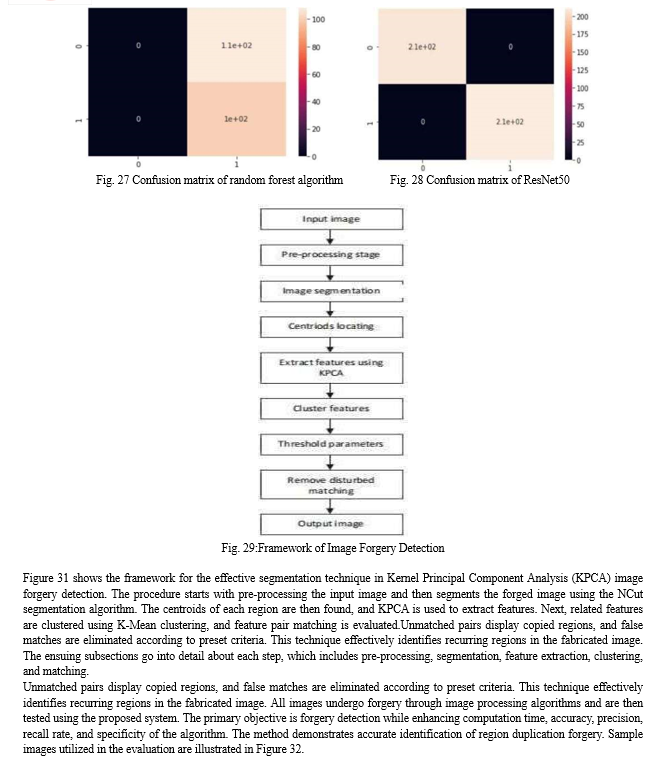
An effective method for categorizing CT scan pictures using machine learning and deep learning—more specifically, the Random Forest and ResNet50 algorithms—is described in Samir Elmuogy's 2021 paper. In order to demonstrate a thorough methodology for medical image forgery detection, the research entails opening a Jupyter Notebook via PyCharm, loading a dataset of human lung CT scans, standardizing image scales, defining and training Random Forest and ResNet-50 models, specifying the Rectified-Adam optimizer, and iteratively testing and training until the desired accuracy is achieved.


Conclusion
In conclusion, it is critical that we address the growing threat of adversarial attacks with ever-more-advanced and flexible solutions as we traverse the changing terrain of medical image authentication. Strong approaches that go beyond conventional forgery detection are desperately needed, as the complex interactions between technical developments and the vulnerabilities present in medical image data highlight. In the face of splicing and copy-move attacks, the paper emphasizes how important Deep Learning (DL) is to maintaining the integrity of diagnostic processes. Investigating state-of-the-art DL-specific forgery detection methods, such as those based on Generative Adversarial Networks (GANs), shows a promising path toward increased precision and robustness. The efficacy of machine learning and deep learning models in protecting the confidentiality of diagnostic data is highlighted by the high confidence levels that have been shown in identifying artificial deformities in medical imaging. Interestingly, deep learning combined with regionof-interest localization is a powerful method to identify subtle abnormalities, especially in tumor injection scans. These conclusive findings highlight how important it is to secure the accuracy of medical images and highlight how urgent it is to address the numerous issues raised by digital manipulations in the fields of medical diagnosis and treatment planning. The unrelenting advancement of deep learning techniques is a beacon in the quest to strengthen the validity of medical imaging. It shows the way toward a future in which the accuracy of diagnostic data will not falter in the face of changing adversarial threats.
References
[1] Shijo Easow, Dr. L. C. Manikandan.: “A Study on Image Forgery Detection Techniques.” International Journal of Computer (IJC), Vol. 33 No. 1 (2019), https://ijcjournal.org/index.php/InternationalJournalOfComputer/article/view/1411 [2] S.K. Kabilesh, D. Divya, C. Blessy Vinolin, D. Priyadharshini, S. Saravanakumar.: “Detection of Duplicate Medical Image using Convolution Neural Network.” International Journal of Scientific Research in Science, Engineering and Technology Volume 9 | Issue 12 | May-June 2022, https://ijsrset.com/IJSRSET22912114 [3] Muhammad Qadir, Samabia Tehsin, Sumaira Kausar, \"Detection of Copy Move Forgery in Medical Images Using Deep Learning\", 2021 International Conference on Artificial Intelligence and Mechatronics Systems (AIMS), pp.1-6, 2021, https://ieeexplore.ieee.org/document/9466005 [4] \"Extended forgery detection framework for covid-19 medical data using convolutional neural network,\" Computers, Materials & Continua, vol. 68, no.3, pp. 3773–3787, 2021, https://www.techscience.com/cmc/v68n3/42466 [5] Sirisha Gudla, Bhuvan Sai Teja Gabbita, Nirupama Chaganti, Srinivas Boddepally, Mayur Raj Singh Biasthakur.: “FORGERY DETECTION OF MEDICAL IMAGE.” Journal of Engineering Sciences ICETT- Vol 14 Issue 05(S), pp.11-19, 2023, https://jespublication.com/special-issue.php [6] R.F. Olanrewaju, Othman. O. Khalifa, Aisha- Hassan Hashim, Akram M. Zeki and A.A. Aburas.: “Forgery Detection in Medical Images Using Complex Valued Neural Network (CVNN).” Australian Journal of Basic and Applied Sciences, 5(7), pp. 1251-1264,2011,https://www.researchgate.net/publication/232708501_Forgery_detection_in_medical_images_using_Complex _Valued_Neural_Network_CVNN [7] V. Srilakshmi, D Purushotham, Chinta Abhinav, Nikhil Godalla, S. V. Varshith.: “Hybrid Model for Image Forgery Detection In Smart Healthcare.” International Conference on Computer, Electronics & Electrical Engineering & their Applications (IC2E3), 2023, https://ieeexplore.ieee.org/document/9466005/citations#citations [8] C. -M. Pun, X. -C. Yuan and X. -L. Bi, \"Image Forgery Detection Using Adaptive OverSegmentation and Feature Point Matching,\" in IEEE Transactions on Information Forensics and Security, vol. 10, no. 8, pp. 1705-1716, Aug. 2015, https://ieeexplore.ieee.org/document/7086315 [9] A. Ghoneim, G. Muhammad, S. U. Amin and B. Gupta, \"Medical Image Forgery Detection for Smart Healthcare,\" in IEEE Communications Magazine, vol. 56, no. 4, pp. 33-37, April 2018, https://ieeexplore.ieee.org/document/8337892 [10] Rithin krishna Dilipkumar.: “Medical Image Forgery Detection.” Masters thesis, Dublin, National College of Ireland, 2022, https://norma.ncirl.ie/id/eprint/5998 [11] V. Kalpana, M. Jayalakshmi, V. Vijaya Kishore. Medical Image Forgery Detection By A Novel Segmentation Method With KPCA. Cardiometry; Issue 24; November 2022; p.1079-1085; DOI: 10.18137/cardiometry.2022.24.10791085; https://www.cardiometry.net/issues/no24-november2022/medical-image-forgery [12] N. Wang, L. Yi, G. Wang and X. Liu, \"MemAU-Net: Memory-Enhanced Attention U-Net for Medical Image Forgery Localization,\" 2023 International Joint Conference on Neural Networks (IJCNN), Gold Coast, Australia, 2023, pp. 1-7, https://ieeexplore.ieee.org/document/10191370 [13] Shivani Pakala, Pravalika Mantri, Madhuri Badri, Dr. M. Naresh Kumar.: “Forgery Detection in Medical Image and Enhancement using Modified CLAHE Method.” Journal of Survey in Fisheries Sciences, Vol. 10 No. 4S (2023): Special Issue 4, https://sifisheriessciences.com/journal/index.php/journal/article/view/1419 [14] Meena, K.B., Tyagi, V. (2019). “Image Forgery Detection: Survey and Future Directions.” In: Shukla, R.K., Agrawal, J., Sharma, S., Singh Tomer, G. (eds) Data, Engineering and Applications. Springer, Singapore. https://doi.org/10.1007/978-981-13-6351-1_14 [15] N. Krishnamoorthy, C. Amuthadevi, M. K. Geedtha, P. L. Reddy, A. R. K. S and R. Gopinathan, \"Splicing Image Forgery Detection by Deploying Deep Learning Model,\"2022 InternationalConference on Automation, Computing and Renewable Systems (ICACRS), Pudukkottai, India, 2022, pp. 1116-1120, https://ieeexplore.ieee.org/document/10029055 [16] M. S. Rana, M. N. Nobi, B. Murali and A. H. Sung, \"Deep fake Detection: A Systematic Literature Review,\" in IEEE Access, vol. 10, pp. 25494-25513, 2022, https://ieeexplore.ieee.org/document/9721302 [17] S. Teerakanok and T. Uehara, \"Copy-Move Forgery Detection: A State-of-the-Art Technical Review and Analysis,\" in IEEE Access, vol. 7, pp. 40550-40568, 2019, https://ieeexplore.ieee.org/abstract/document/8673945 [18] A. B. Z. Abidin, H. B. A. Majid, A. B. A. Samah and H. B. Hashim, \"Copy-Move Image Forgery Detection Using Deep Learning Methods: A Review,\" 2019 6th International Conference on Research and Innovation in Information Systems (ICRIIS), Johor Bahru, Malaysia, 2019, pp. 1-6,https://ieeexplore.ieee.org/document/9073569 [19] A. Solanas et al..:\"Smart health: A context-aware health paradigm within smart cities,\"in IEEE Communications Magazine, vol. 52, no. 8, pp. 74-81, Aug. 2014, https://ieeexplore.ieee.org/document/6871673 [20] S. Walia and K. Kumar.: \"Characterization ofsplicingin digitalimages using grayscale co-occurrence matrices,\"2019 Twelfth International Conference on Contemporary Computing (IC3), Noida, India, 2019, pp. 1-6, https://ieeexplore.ieee.org/document/8844881 [21] Yisroel Mirsky, Tom Mahler, Ilan Shelef, Yuval Elovici.: “CT-GAN: Malicious Tampering of 3D Medical Imagery using Deep Learning.” 28th USENIX Security Symposium (USENIX Security 19) https://www.usenix.org/conference/usenixsecurity19/presentatio
Copyright
Copyright © 2024 Aruna S, Akkidasari Varshitha, K L Kalpana, Yash Santosh Karwa, Jyothi R. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET59323
Publish Date : 2024-03-22
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

