Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Real-Time Object and Face Monitoring Using Surveillance Video
Authors: Obaish Khan, Priyanshu , Rohit Paranjape, Rajas Deshmukh, Rupak Potdukhe, Prof Nirmal Mungale
DOI Link: https://doi.org/10.22214/ijraset.2023.49269
Certificate: View Certificate
Abstract
Face detection is regarding finding or losing a face during a provided image and, if any, reestablishes the position of the image and therefore the options of every face. Safety and security are 2 of the foremost vital human characteristics. during this article we\'ve got prompt face detection and a visible system that may be able to method pictures terribly quickly whereas achieving the very best level of face detection. Facial recognition is that the method of distinctive an individual employing a personal standing to spot a person\'s temperament. during this project, we have a tendency to propose a private verification system that uses face recognition associate degreed generates an unauthorized person warning. The alert are within the variety of associate degree unauthorized image that may be displayed within the application. the invention was created with instant video taken from a camera of mobile or portable computer. individuals and things are being recorded during this video victimisation OpenCV, YOLO and FaceNet. once an individual is found, the system identifies the person. His identity are remodeled to audio and introduced to the user. Similarly, regionally found objects are conferred in audio format to the user.
Introduction
I. INTRODUCTION
Many face acknowledgment calculations planned during a product area having a high location rate, but ordinarily need a few of moments to urge or perceived a single image, depleted handling speed in realtime programs. The program is altered utilizing Python sterilization language. each current face location and face recognition in specific footage, i.e., Object Detection, performed and therefore the planned framework is tried on all customary sites of various appearances, with sound and while not obscuring impacts. Framework execution is surveyed by understanding the face level of each web site. The outcomes uncover that the planned framework are often used to acknowledge faces even in low-goal footage and to point out astounding proficiency.
The issue of security is important during this day and age. Among the few ways used for security functions, face acknowledgment could be a powerful methodology for guaranteeing eudaemonia and security. Face acknowledgment is one amongst the foremost loosely focused on biometry advances and has been created by specialists.
Face identification could be a crucial affiliation for the attendant facial related applications, for instance, facial acknowledgment [l], as its impact squarely influences the exhibition of succeeding applications. during this manner, face location has become an enquiry region within the field of example acknowledgment and computer vision and has been loosely investigated throughout recent a few years.
Many face acknowledgment ways are planned. Introductory exploration on facial acknowledgment zeroed in on the formation of a workmanship highlight and used traditional AI calculations to arrange effective category dividers to seek out and distinguish. Such techniques are restricted in lightweight of the actual fact that the set up of the functioning element is tangled and therefore the exactness of location is low.
The planned framework can have clever computer includes that incorporate individual recognizable proof and individual data. distinctive proof are finished by face acknowledgment and acknowledgment. As per our exploration up till now we've got discovered that facial acknowledgment ought to be attainable utilizing Haar Cascade From Face to urge xml. Accessible within the most noted library OpenCv.
For face acknowledgment we'll use within and out learning calculations to arrange our facial web site model. Indepth learning ways will utilize extraordinarily vast facial informational collections and learn made and incorporated facial portrayals, allowing current models to begin to perform well and later surpass human facial acknowledgment skills.
Likewise we'll see traditional things, for instance, PDA, wallet, key then on to trace and screen in spite of whether or not they are lost. Object securing are finished utilizing opencv and YoloV3 or YoloV4 model. (Consequences be damned) could be a innovative, current system
II. METHODOLOGY
Instruments and innovation utilized:
- Python: Has a vast variety of libraries for applications, for instance, Scikit AI, OpenCV computer scanner, TensorFlow for brain organizations, then forth.
- Java: humanoid involves Java joined of its customizing dialects. Utilizing Java, humanoid applications for speech act and underlying face acknowledgment.
- OpenCV: wont to perform continuous computer vision capacities.
- Consequences be damned: Provides a position that allows the getting of articles about to constant speed. Since versatile delivery utilizes small YOLO, that could be a easy YOLO structure for cell phones and edges.
- Tensor Flow: associate degree open supply programming library and brain network structure and AI applications. it's associate degree adjustable set up and might be circulated to waiters, workstations, cell phones, edge gadgets, then forth.
- Tensor Flow fatless: TensorFlow for cell phones includes a meager and light-weight computer utilizing low power PCs on cell phones and fringe gadgets referred to as Tensor Flow Lite. This very little system takes into thought straightforward utilization of little AI comes and low-power gadgets.
- Keras: Keras could be a profound brain network library that runs over completely different styles Tensor Flow. it's not tough to utilize and considers the preparation of connected learning models utilizing brain networks is easy. Keras contains a number of additional highlights of an analogous brain network layers, structures, gap capacities, then forth that makes it a valuable library for a few applications.
- FaceNet: wont to disencumber high notch facial highlights and train face acknowledgment framework.
- Scikit-learn: Contains completely different calculations for gathering, disposing of and partitioning into numerous classifications. AI comes are often used with alternative Python libraries, for instance, SciPy and NumPy. Scikit-advance in addition utilizes SVM (Vector support machines) and FaceNet among getting ready comes to form precise face acknowledgment models.
- Execution Phases:
a. Stage I: during this stage the complete framework is built utilizing Python. The planned framework configuration is meted out utilizing Python scripts for each module. the elemental justification for this approach was to ensure that the complete framework worked fitly. At the purpose once the entire framework was assembled and tried, the code was moved to Java to be used on humanoid. Python is used on a Windows and Linux-based machine to fabricate and check planned execution. At this stage, the framework is predicated on a flexible computer, which supplies admittance to higher computer administrations just like the mainframe and GPU of the computer. All facial acknowledgment and getting models gift were ready during this phase. once the framework is totally assembled and tried for effectiveness, the code is then sent to Java.
b. Stage Il: This was the play of venture execution wherever the entire code was composed Python has been moved to Java to be used on the humanoid application. Qualified models from category I are used squarely within the humanoid application for visual and object acknowledgment. Since the operating framework was at that time created utilizing Python, the principal task at this stage was to include library adjustment to assist humanoid and Java, submit Python code and revamp it to Java to bring ready models into the applying. once the first assignments are finished, the humanoid App is built and introduced on cell phones for testing. humanoid Voice API has likewise been accessorial to ensure that the outcomes are modified over utterly to sound arrangement.
At last, a straightforward client cooperation was made, remembering that the end client of the application needs to faces no troubles in utilizing the framework. The primary models utilized in the face acknowledgment application are prepared in the cloud involving the GPU in Google Collabs and Kaggle as well as unambiguous preparation in the nearby GPU on a compact PC. Afterward, because of the enrollment of another facial covering, the preparation element of the new face model was added to the portable application.
his is to guarantee that new faces can be added straightforwardly to the cell phone without expecting to prepare the new model remotely and download the model to the cell phone.
Pseudocode acquisition start process OpenCV import process import yolo weights, yolo-config, coco.names start line open web camera using OpenCV real-time video capture on device using OpenCV split video in its frames while input frames for processing take one frame while converting the frame to a gray image convert the image into identical NumPy members (or Java matrix) make object discovery using the YOLO binding box around the object labeled item enter the words of objects found in the same audio line the conversion process when the line is empty remove the object at the head ofthe line convert the object name into an audio as output.
System Architecture is described in figure I
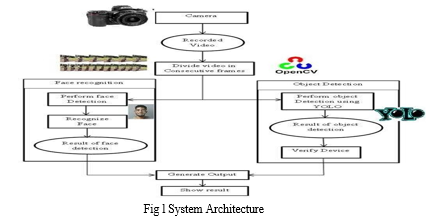
The proposed method is broadly divided into five parts of data collection, data processing, data classification, training and testing. The program uses a variety of image processing techniques to improve image quality and remove hidden pixels, as well as editing edges. The in-depth Convolutional Neural Network (CNN) learning algorithm is used to classify images based on their characteristics. There are two main components of CNN architecture
- A convolution tool that separates and identifies various aspects of an image to be analyzed through a process called Feature Extraction.
- A fully integrated layer that uses the output from the conversion process and predicts the image phase based on the features extracted from previous sections.
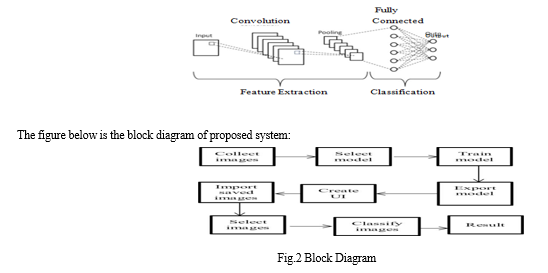
The proposed program compares person-related items during the training period with the latest image provided by the program. If something is missing in the frame the system will highlight that and tell the user which objects is missing in the frame.
If you use human vision in your computer vision application, you can use a pre-trained model or give yourself a model yourself. If you give your model a lot of data, your device will be better able to see what you want and learn to improve it.
After receiving the photos, these results will be categorized. If it is personal based on a person's ID, it will display personal details and update the UI. In the case of objects then comparisons will be made in the previous and current image and it will be determined which object is not in the frame. Item will label and be given a UI to update the list and show missing items.
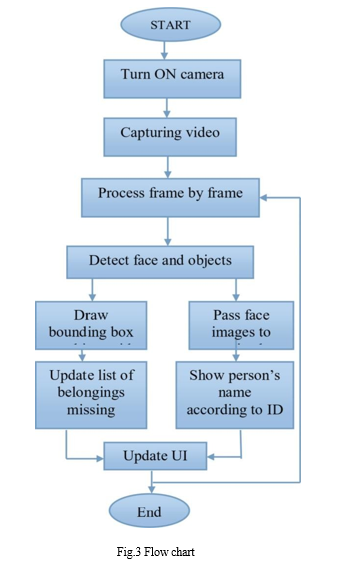
Computer literacy performs three different functions:
- Selects items from background images
- Promotes things as a class - people.
- Characterizes the socioeconomics of the proposed populace with x foundations and lengths and lengths and values
At the most elevated level, there are two variables to think about while moving toward a photographic artist utilizing PC vision applications. To start with, there is the specialized side - how to track down individuals in a photograph or video. The subsequent part is how you can manage the outcomes, and it has to do with the nature of the advantages you get from your application.
Picture Editing: Guess the sort or classification of article in an image. Input: An image with one item, like an image.
Yield: Old Label Location: Find the presence of items in a picture and demonstrate their area in the connection box.
Regularly, critical thinking in photograph or video information starts with formal picture characterization. In the first place, the instrument can involve the calculations in the establishment to distinguish the areas you are keen on. The machine will then think of a rundown of ideas in view of your settings. The last strides for reception are to sort objects in light of models, utilize potential and reestablish classes and areas in the system of your last supported recommendations.
The class you would like, for this situation, is individuals.
The applications distinguish these human articles in the survey region by handling pretrained blocks by consolidating countless pictures with an inside and out man-made reasoning framework. These handling blocks are known as models, and can be prepared to see nearly anything individuals can see.
Conclusion
This project describes the way to establish and establish someone and his or her belongings in real time. The project describes the system wont to acquire things. By victimisation precise CV cameras or drones with embedded reckoning functions, security corporations will acquire correct, updated demographics and mass knowledge to tell worker choices. The system operates in 2 basic steps; it sees someone and things, separates it and eventually sees one thing that\'s not within the frame. One of the key issues involving object detection is that the classification of Associate in Nursing object and also the location of Associate in Nursing object among Associate in Nursing object. the employment of deep neural networks has helped to deal with the subject of object acquisition. However, implementing such techniques on mobile devices needs high standardization and memory resources. thus little deep neural network structures square measure wont to notice one thing like small YOLO provides sensible results and shows that it may be wont to get period of time object once victimisation mobile devices which will facilitate the visually impaired.
References
[1] Prof Nirmal Mungale, Amarja Indapwar, Hemangi Oke, Madhura Chikte, Poonam Barai, Pratima Katre, \"Implementation of Speeded Up Robust Feature Algorithm for Real Time Logo Detection\", International Journal of Scientific Research in Computer Science, Engineering and Information Technology (IJSRCSEIT), Volume 3, Issue 1, pp.1024-1030, January-February-2018. [2] Olegs Nikisins, Rihards Fuksis, Arturs Kadikis, Modris Greitans \"Face recognition system on Raspberry Pi\" International Journal of Research in Advent Technology, Vol.3, No.5, May 2015. [3] Harshal V. Khodaskar, Shashank Mane \"Human Face Detection & Recognition Using Raspberry Pi\" International Journal of Advanced Engineering, Management and Science (IJAEMS) june 2014. [4] Prof. Natali Almeida \"Facial Recognition System applied to Multipurpose Assistance robot for Social Human-robot Interaction (MASHI)\" International Journal of Engineering Trends and Technology (IJETT) - Volume 30; Number-I, December 2015 [5] David Gsponer \"IOT: Building a Raspberry Pi security system with facial recognition\" Bachelor\'s Thesis Degree Programme in Business Information Technology vol. 4, May 2018 [6] Swathi .VI, Steven Fernandes2 \"Raspberry Pi Based Human Face Detection\" International Journal of Advanced Research in Computer and Communication Engineering Vol. 4, Issue 9,May 2017 [7] Saurabh K. Patil, Narendra G. Narole \" Smart Face Recognition Security Based On Raspberry Pi\" International Journal of Engineering Science and Computing, Volume 8 Issue No.3 March 2018. [8] Mr. Shamanth G S \"Face Detection using Raspberry Pi and Python National Conference on Product Design (NCPD 2016),July 2016 [9] Shrutika V. Deshmukh\" Face Detection and Face Recognition Using Raspberry Pi\"September 2015 [10] Dahake, N. N. Mandaogade \"Implementation of Raspberry Pi for Human FaceDetection & Recognition Technical Research Paper Competition for Students (TRPCS-2K17)\", 23 March 2017.
Copyright
Copyright © 2023 Obaish Khan, Priyanshu , Rohit Paranjape, Rajas Deshmukh, Rupak Potdukhe, Prof Nirmal Mungale. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET49269
Publish Date : 2023-02-26
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

