Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Real Time Threat Intelligence System for Malware Detection
Authors: Chetana Patil, Sufiyan Ali Khan, Mohammed Tahir K, Shoail S Khan
DOI Link: https://doi.org/10.22214/ijraset.2024.61086
Certificate: View Certificate
Abstract
We introduce a framework that represents real-time threat intelligence, a Python Project employing techniques for machine learning and behavioral analysis to quickly identify potential malware in scanned documents. The system integrates behavioral analysis for the purpose of detecting malware to improve security with machine learning, continuously evaluate new data, identify risks and isolate suspicious information. When an unsafe file is detected, the user interface will display the corresponding message.
Introduction
I. INTRODUCTION
Cybersecurity threats are wide-ranging and ever-changing; It requires new solutions to protect the digital ecosystem. Malware or malicious software has become sophisticated and requires the development of effective repair tools. To meet this requirement, a system for real-time threat detection was implemented in our project. Traditional signature-based search engines are often inefficient for new and rapidly changing systems. Our system will use a sophisticated method such as machine learning techniques to analyze and classify applications based on complex tasks rather than relying on simple signatures. By constantly refreshing its knowledge base with the latest threat intelligence, the system maintains its robustness and ability to respond to emerging threats. This feature, combined with the intuitive Pit desktop application, not only enables users to detect known malware, but also prevents potential threats through periodic review and feedback. This approach demonstrated in detail, including data collection process and feature extraction technology, and the use of powerful machine learning models. The user-friendly PyQt desktop application acts as an interface for users to interact with the system, making malware difficult to detect by people without technical expertise. System architecture, results of rigorous testing, and a general discussion of the strengths, limitations, and future prospects of our real-time threat detection malware.: Proactive and adaptive protection against malware threats. By combining machine learning with real-time threat intelligence, our goal is to help digital communities find solutions to ever-changing cybersecurity challenges. Casual use is used to evade the exploratory signature process. Our system tackles this challenge by using a machine learning-centric approach where applications are evaluated against a comprehensive set of criteria. This fine-grained analysis allows the system to identify subtle patterns that indicate malicious behavior, thus improving the ability to detect previously unseen threats. The project is completed by the Python-based Jupyter library, which provides a powerful and effective platform for creating and training learning models. Integration of the PyQt desktop application further expands the penetration of our system, providing users with a better understanding of interactions with malware detection capabilities. The complexity of the process is illustrated in detail by the selection and preprocessing of the dataset, discrimination extraction, and the architecture of the machine learning model. Additionally, the integration of real-time threats will be explained and its importance in the context of threat prevention will be emphasized. An extensive discussion will follow, highlighting strengths, limitations, and potential avenues for future development. Our malware detection real-time threat intelligence is designed at its core to not only leverage the power of the digital environment, but also to enhance integrated defense against a dynamic landscape of cybersecurity threats. Jupyter notebooks for Python provide a flexible and flexible environment for developing and training machine learning models. The user interface is built using PyQt, which provides a desktop application that translates the complexity of malware detection into an intuitive user interface. A revolution in malware detection comes from the process of distinguishing between normal and malicious files. Unlike traditional signature techniques, Machine learning has the capability to adapt to changes in malware behavior and identify hitherto unseen threats. The main objective of this project is to develop and implement a machine-level malware detection system that leverages the potential of machine learning algorithms. With this new approach, we aim to increase the speed, accuracy and flexibility of malware detection, thereby strengthening computers' ability to prevent cyber disasters. I can't do it.
The project will examine the core principles of machine learning and examine various extraction and selection methods to enhance accuracy of detection algorithms. Evaluation of these strategies will include the utilization of common data to facilitate analysis of the countermeasures developed and comparison of their performance in malware detection. Increasing complexity ChatGPT Our project delivers real-time threat intelligence for malware detection, combining machine learning with regular updates for unblocked protection. In contrast to traditional approaches, our system analyzes complex signatures rather than simple signatures to identify evolving threats. Even non-technical users can interact with the user-friendly PyQt desktop application. Our approach addresses malware vulnerability, keeping users one step ahead of emerging threats. We build and train machine learning models to efficient and effective benchmarking using Python-based Jupyter Notebooks. The program aims to harness the potential of machine learning to improve the digital environment and solve ever-changing security challenges.
II. LITRETURE SURVEY
[1]. Malware investigation & location utilizing machine learning: This article examines the risk of malware to computer security and the confinements of conventional signature-based discovery strategies. It highlights the guarantee of machine learning (ML) innovation in recognizing already obscure malware by analyzing complex highlights. The viability of machine learning-based look motors depends on cautious building, suitable machine learning calculations, and great information. This ponder highlights the significance of plan building in preparing models with great information. Advances such as convolutional neural systems (CNN) and irregular neural systems (RNN) appear guarantee in precisely recognizing malware. The focal points of machine learning incorporate tall precision and programmed look, but there are moreover challenges such as the quality of the information. [2]. Malware Location Utilizing Machine Learning Strategies: This article covers the advancing scene of malware discovery by tending to the deficiencies of conventional antivirus assurance strategies. It prescribes machine learning and profound learning as successful strategies for malware location. The inquire about particularly centers on classifying malware from picture representation of malware utilizing bolster vector machines (SVM) and convolutional neural systems (CNN). The point is to center on early discovery through compelling methodologies and utilize machine learning models for complex investigation. In spite of the fact that it has focal points such as early location and progressed methods, challenges such as picture representation overhead and information reliance stay. [3]. Antagonistic Machine Learning Assaults on Interruption Location Frameworks: Study of Methodologies and Resistances: The world is examining the vulnerabilities of interruption discovery frameworks (IDS) for preparing abuses (AML) assaults that posture genuine cyber dangers. It talks about how machine learning can be utilized to move forward the viability of IDSs in recognizing unused assaults. In any case, it influences forecast and classification by highlighting the affectability of AML frameworks to antagonistic input annoyances. In this consider, different assaults against IDS are inspected and defense procedures to decrease these dangers are displayed. In spite of the fact that the viability of interruption location has expanded, challenges stay, such as destitute get to to reaction and exchange to the scene. [4]. Information mining classification strategy for behavioral malware discovery: This article centers on utilizing information mining classification innovation to distinguish malware. It varies from signature-based and behavior-based malware discovery and highlights the restrictions of the previous in combating the noxious behavior of malware. This consider highlights the significance of behavior examination in recognizing real terrible behavior, particularly in negative circumstances. Information mining strategies utilize information records containing malware and well-developed computer program to form classifications for malware discovery. Whereas giving solid location and precise comes about, challenges stay, such as versatility to energetic malware behavior. [5]. Utilizing Machine Learning for Mechanized System-Level Malware Location: A Comprehensive Audit: This article gives a comprehensive survey of machine learning strategies for programmed system-level malware location. It distinguishes the confinements of signature-based location and the guarantee of machine learning in fathoming these issues. This work centers on different machine learning methods, extraction methods, and benchmarks to assess the execution of location frameworks. Whereas it gives understanding into tending to the restrictions of signature-based discovery, issues such as restricted capacity to depend on great preparing information and utilize information consistency are too recognized. [6]. Investigation of Malware Location Utilizing ML: This article gives an diagram of the malware discovery handle with eight modern facilitating alterations from conventional strategies such as behavior and signature-based show. He talks approximately the expanding risk of online extortion and the require for progressed security items. This ponder examines heuristic examination, inactive and energetic examination as new techniques for viable malware detection. While machine learning is sweet at finding the most excellent arrangements, challenges stay, such as the developing malware list and reliance on diverse information sources. [7]. Malware classification investigate utilizing machine learning and profound learning: This paper presents a orderly approach to machine learning for versatile malware location. Addresses the advancing nature of portable malware dangers and vulnerabilities in portable working frameworks.
The consider looks at different machine learning, discovery and assault vectors to shed light on future inquire about in portable cybersecurity. Whereas we offer valuable data to move forward portable malware location, we too acknowledge the challenges of generalizing our discoveries to other stages. [8]. Investigate on Machine Learning Procedures for Malware Examination: This article analyzes machine learning methods utilized in malware examination to unwind the complexity and volume of malware. It classifies information science concurring to its purposes, sources of data, and machine learning strategies. This ponder gives an outline of the issues and issues, counting subjective information and investigation of current patterns. In any case, a few impediments were famous, such as inadequately detail of the comes about and the need of particular cases. [9]. Mechanized level malware discovery utilizing machine learning: A comprehensive audit: This comprehensive whitepaper analyzes the current state of malware location with subtle elements on measuring the machine learning scene. It evaluates different machine learning, extraction methods, and assessment strategies. This work gives knowledge into the restrictions of signature-based discovery and the guarantees of machine learning. In any case, we recognize that there are inclination issues in utilizing distinctive information and depending on great information. [10]. Framework Outline of Machine Learning Strategies for Versatile Malware Location: This record addresses key issues in portable security by assessing machine learning strategies for versatile malware discovery. It appears the drawbacks within the working of the portable phone and their affect on different exercises. This think about conducted a subjective writing audit comparing administered and unsupervised strategies for versatile malware location. Whereas shedding light on future investigate, it too highlighted the challenges in generalizing the discoveries to other stages.
III. AIM AND OBJECTIVES
The aim and Objectives of this paper are:
A. Aim
Create a real-time malware detection environment to continuously monitor the system to detect malicious files. The model identifies the archive as suspicious. This is where the random forest model comes into play.
B. Objectives
- Behavioral Analysis: This approach doesn't just rely on static parameters like signatures or attributes. It observes how data behaves in different contexts, enabling better assessment of potential malicious behavior by analyzing interactions with the system.
- Training for Accuracy: Before real-time deployment, the model undergoes training to recognize patterns associated with threats. Through exposure to various examples of benign and malicious behavior, it enhances its ability to differentiate between them during scanning.
- Real-Time Scanning: Files are immediately subjected to analysis upon entry into the system. Users can monitor the scanning progress in real-time and receive updates on scanned files. This swift identification and response to any suspicious activity enhance overall system security.
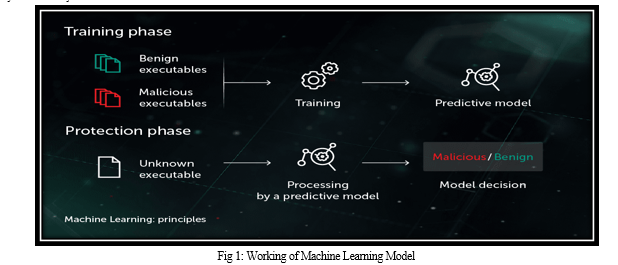
IV. IMPLEMENTATION AND DESIGN
A. Proposed System
A system that include real-time threat intelligence use technologies such as machine learning and deep learning models, alongside behavioral analysis. Study, including exclusion of questionable information. Automatic Threat Detection: These systems use threat detection techniques to quickly identify and respond to emerging threats. Electronic tools can analyze vast datasets and identify patterns suggesting potential threats. Information. This integration increases the overall visibility of the security environment. They help develop and implement effective response strategies to minimize the impact of climate change.
B. Modules
- Module 1: Machine Learning Models Used
- Description of random forest models for behavior analysis.
- Details to be learned and how to extract or create them.
- Overview of virtual virus and hybrid analysis-based API testing tools.
- Contribution to overall development.
2. Module 2. Front-end Components
Front-end GUI Design using PyQt
- Graphical user interfaces (GUIs) play an significant role in improving the user experience using software.
- GUIs provide an intuitive way to interact with complex systems.
- Efficiency and ease of use are crucial in cybersecurity and threat intelligence.
- Integrating PyQt into the system allows for the development of visually appealing and responsive GUI applications.
- PyQt offers robust tools for crafting interfaces, enhancing the overall user experience.
- The integration of PyQt offers flexibility and scalability for future development.
- Using PyQt's features and functionalities, the aim is to develop a GUI that meets system requirements and improves user experience.
- Various aspects of the GUI will be explored to facilitate interaction with the underlying system.
- The research aims to demonstrate the conceptual GUI design in cybersecurity applications and showcase the capabilities of PyQt.
- By combining powerful back-end algorithms with intuitive front-end interfaces, effective solutions for real-time malware and threat detection can be delivered.
3. Module 3. Integrated Development Environments (IDEs):
Visual Studio
- Visual Studio supports multiple languages and features recovery tools.
- Debugging capabilities help identify and fix problems in the codebase.
- Integration with Git enables seamless collaboration.
- Extensive presence in the Visual Studio Marketplace allows for customization with extensions.
- Cross-platform support enables app development across various platforms.
- Cloud integration with Microsoft Azure simplifies building, deploying, and managing cloud-native applications.
- Visual Studio simplifies development life and fosters innovation.
- Enhanced cross-platform capabilities improve reach and accessibility.
- Deep integration with Microsoft Azure utilizes the power of the cloud to deliver robust solutions.
- Visual Studio remains the foundation of software development, providing tools and resources for innovation.
- It allows developers to create interactive solutions with unparalleled functionality and ease of use across different platforms.
V. METHODOLOGY
- Documentation: Real-time threat detection for malware begins with thorough documentation of processes and procedures. This includes documenting protocols for analyzing network traffic, monitoring system files, and identifying potential vulnerabilities.
- Analyzing Network Traffic: The first step involves monitoring network traffic to detect any suspicious activity. This includes analyzing connections for anomalies, such as unexpected data transfers or unusual patterns.
- Using Signature-Based Detection: Employing a signature-based detection mechanism to identify known malware based on predefined patterns and signatures. This method involves comparing file characteristics against a database of known threats to detect similarities.
- Behavioral Analysis: Implementing behavioral analysis techniques to identify malware that may not have specific signatures. This involves monitoring file behavior and system interactions to detect anomalies indicative of malicious activity.
- Multi-Source Data Collection: Real-time threat detection relies on various Sources, including network connections, endpoints, and threat intelligence feeds. This comprehensive approach enhances the system's ability to identify and respond to emerging threats.
- Analyzing Network Traffic: The first step involves monitoring network traffic to detect any suspicious activity. This includes analyzing connections for anomalies, such as unexpected data transfers or unusual patterns.
- Using Signature-Based Detection: Employing a signature-based detection mechanism to identify known malware based on predefined patterns and signatures. This method involves comparing file characteristics against a database of known threats to detect similarities.
- Behavioral Analysis: Implementing behavioral analysis techniques to identify malware that may not have specific signatures. This involves monitoring file behavior and system interactions to detect anomalies indicative of malicious activity.
- Multi-Source Data Collection: Real-time threat detection relies on various Sources, including network connections, endpoints, and threat intelligence feeds. This comprehensive approach enhances the system's ability to identify and respond to emerging threats.
VI. Acknowledgment
The fulfillment and the successful completion of my assignment would be incomplete without giving acknowledgement to the individuals who made it possible and whose unwavering support and guidance steered my endeavors towards triumph.
We take great pride in being part of the ICEAS family, an institution that stood by us throughout our journey.
We extend our sincere gratitude to our mentor, Mrs. Chetana Patil, Assistant Professor in the Dept of CS&E at ICEAS, for her meticulous guidance and corrections on various documents. She devoted significant effort to review the documents and provided necessary corrections whenever needed. Our heartfelt thanks to Dr. Dhananjaya V, Professor and Head of the Dept of CS&E at ICEAS, whose inspiration and invaluable assistance helped us channel our efforts in the right direction. We like to express thanks to our Management and Principal, Dr. Jalumedi Babu, for their unwavering support.
We would like to acknowledge the faculty members and supporting staff of the Dept of CS&E at ICEAS for their assistance in completing the project. Lastly, we are grateful to our parents and friends for their unconditional support and assistance throughout the course of our project..
Conclusion
Advancing real-time threat intelligence systems represents a significant advance in proactive malware detection and security system. The system leverages the potential behavioral analysis to provide rapid threat analysis and continuous monitoring of data for risks. Integration of instant scanning and user-friendly interface increases overall security by providing users with quick visibility and control. Going forward, further improvement and optimization of algorithms and processes will continue to improve the capacity to deal with ever-changing threats. With its active and critical approach to real-time detection, real-time threat intelligence is at the forefront of modern cybersecurity, providing critical protection for computer technology in today\'s digital environment.
References
[1] Malware analysis & detection using machine learning parshva doshi, darsh patel, vishal padia, omkar solanki cyber security, mumbai, india. [2] Malware detection, sakshi joshi, kls vpp, belagavi, karnataka, india, santosh mahagaonkar, nict solutions &research belagavi, karnataka, india. [3] Adversarial attacks detection systems: a survey on strategies and defense, afnan alotaibi, saudi arabia, murrad, taiz university, taiz 6803, yemen. [4] Behavioral malware detection monire norouzi,1alireza souri,2and majid samad zamini young researchers and elite club, islamic azad university, hadishahr branch, hadishahr, iran department of computer engineering, islamic azad university, hadishahr branch, hadishahr, iran department of computer engineering, islamic azad university, sardroud branch, sardroud, iran. [5] Automated system-level malware detection using machine learning: a comprehensive review nana kwame gyamfi *, nikolaj goranin, dainius ceponis and habil antanas cenys department of information systems, vilnius gedimino technical university, 10223 vilnius, lithuania; [6] A survey on malware detection using ml prof. pritam ahire1, mohanki shreya 2, shreya shinde 3, preeti pisal 4, manasi manikumar5 1, 2, 3, 4, 5computer engineering, savitribai phule pune university. [7] Malware classification manish goyal, ik gujral punjab technical university, kapurthala, punjab, india raman kumar, ik gujral punjab technical university, kapurthala, punjab, india. [8] Survey of machine learning techniques for malware analysis daniele uccia, leonardo aniellob, roberto baldonia a research center of cyber intelligence and information security, “la sapienza” university of rome b cyber security research group, university of southampton. [9] Automated system-level malware detection using machine learning: a comprehensive review nana kwame gyamfi, nikolaj goranin, dainius ceponis and habil antanas cenys. department of information systems, vilnius gedimino technical university, 10223 vilnius, lithuania. [10] A systematic overview for mobile malware detection yu-kyung kim, 1 jemin justin lee, 2 myong-hyun go, 1 hae young kang, 1 and kyungho lee 1 1 institute of cyber security & privacy, korea university, seoul, republic of korea 2 center for information security technology, korea university, seoul, republic of korea.
Copyright
Copyright © 2024 Chetana Patil, Sufiyan Ali Khan, Mohammed Tahir K, Shoail S Khan. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET61086
Publish Date : 2024-04-26
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

