Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Fake Product Identification using Blockchain
Authors: Sowmya D, Kruthi H D, Manvitha K V, Monisha Y C, Nagamani S
DOI Link: https://doi.org/10.22214/ijraset.2024.66013
Certificate: View Certificate
Abstract
In recent-years, blockchain has received increasing attention and numerous applications have emerged from this technology. A renowned Blockchain application is the cryptocurrency Bitcoin, that has not only been effectively solving the double-spending problem but also it can confirm the legitimacy of transactional records without relying on a centralized system to do so. Therefore, any application using Blockchain technology as the base architecture ensures that the contents of its data are tamper-proof. This paper uses the decentralized Blockchain technology approach to ensure that consumers do not fully rely on the merchants to determine if products are genuine. We describe a decentralized Blockchain system with products anti-counterfeiting, in that way manufacturers can use this system to provide genuine products without having to manage direct-operated stores, which can significantly reduce the cost of product quality assurance
Introduction
I. INTRODUCTION
Any product is subject to several risk factors such as counterfeiting and duplication, that can affect the brand name, reputation, revenue, or customer satisfaction at all stages of development. Counterfeit products are rapidly being traded and marketed. Full operation of a blockchain system is suggested to identify and monitor counterfeit goods or products, while at the same time combating this phenomenon. Only companies have to spend very little effort, and they don't. longer need to worry about counterfeit products. Due to Counterfeit products, manufacturers are going to lose a lot of money. The reputation of a company's name and its brand value because customers thought that it was a product manufactured by the company That's why, based on a counterfeit product, they look at it. A decentralized distributed ledger technology system can be adopted to resolve this problem. Blockchain is a distributed decentralized-based This is the technology to store data in blocks within a database, and it links with chains. If new data are added to databases, it will update existing data by linking a chain of these records to an existing block. Blockchain does not allow any user to update the existing data each time blockchain will add data as a new block to existing data. Therefore, the data in the blockchain that leads to data security and data protection cannot be deleted or modified. The issue of counterfeit products is being addressed by Blockchain technology.
II. LITERATURE SURVEY
In this section, several authors have presented various Blockchain techniques and methodologies for fake product identification.
In [1] Blockchain technology revolutionizes the foundation of human transactions by eliminating the need for a trusted third-party intermediary and creating a reliable, shared data record system. Its key characteristics include robust security and privacy, achieved through cryptographic public and private key pairs that protect data from unauthorized access as long as private keys remain secure. The technology ensures untrace ability by making blocks immutable once determined; any tampering is immediately detected and rejected by the network nodes. Transparency is another hallmark, with Blockchain maintaining an open, continuous transaction log that allows users to trace data flows clearly. Its decentralized architecture ensures that every node locally handles information verification, delivery, and management, reducing reliance on centralized systems. Furthermore, Blockchain supports flexibility through its open-source nature, enabling users to customize or create new platforms and applications. Users remain anonymous, identified only through unique addresses that protect their privacy. This combination of transparency, security, decentralization, and adaptability makes Blockchain a ground-breaking technology with limitless applications.
In [2], blockchain technology is highlighted as a promising solution to enhance traceability in the agri-food supply chain. It has the potential to provide stakeholders with critical information regarding food quality, safety, and nutrition. However, a lack of expertise in designing user interfaces for traceability applications may result in significant usability challenges.
Addressing these issues is crucial to ensuring the practical adoption of blockchain solutions in this sector. This paper takes a step in that direction by reviewing existing research on blockchain-based agri-food traceability systems. The focus of the review is specifically on the user interface design aspects. By analysing prior works, the paper identifies gaps and challenges that hinder user-friendly designs. It also highlights opportunities for improving the interface to better serve the needs of stakeholders. The aim is to contribute towards the development of more intuitive and effective applications. This effort ultimately supports the broader goal of leveraging blockchain for a safer and more transparent food supply chain.
In [3] Manufacturer’s role involves adding their company to the blockchain by providing the company name and setting a minimum registration fee for sellers or retailers. The manufacturer also retains exclusive rights to list products on the network and can control the distribution status and transfer ownership once a seller purchases the stock. Sellers can pay the minimum fee to register and buy products, tracking their distribution status. After the manufacturer ships a product, its status changes from "Ready to Go" to "Shipped." Consumers can scan the product's QR code to verify ownership transfer and check the product's distribution status. Algorithm is used for adding and distributing products in the system.
In [4], Concept of hash function in blockchain technology serves two critical purposes: collision-resistance and one-way functionality. Collision-resistance ensures that two distinct inputs cannot produce the same hash value, while one-way functionality ensures that it's computationally infeasible to reverse the hash to obtain the original input. The primary use of hash functions is to guarantee data integrity, whether for online or offline transactions, ensuring that files downloaded from an online source are authentic. In blockchain applications, hash functions are widely used for tasks such as generating addresses, implementing Proof of Work (PoW), creating bridge mechanisms, generating random or pseudo-random numbers (PNG), producing new blocks, and creating message digests for signatures (MDS). The importance of hash functions has surged in cryptocurrency applications, where they play a vital role in securing transactions and maintaining blockchain immutability. The SHA256 hash function is the most commonly used hash function in blockchain systems due to its strong security properties and efficiency.
In [5] Decentralized blockchain utilizes the proof-of-work consensus mechanism, where blocks are added by solving mathematical puzzles. This process, known as mining, involves computational effort to prove that nodes have completed the "work," ensuring the block is recorded on the blockchain. Mining typically uses a brute-force trial-and-error approach, and successful miners are rewarded, such as in Ethereum. Additionally, smart contracts are tamper-proof programs stored in blocks, designed to execute automatically when predefined conditions are met. These contracts eliminate the need for third-party involvement and remain unalterable once deployed, ensuring secure and automated agreements.
In [6] This survey paper has covered architecture of cryptocurrencies, smart contracts and general Blockchain based applications. The paper has provided a perspective to describe the Blockchain architectures in relation to cryptocurrencies, smart contracts and other applications. The research advances in consensus are also highlighted with some key development and application frameworks. A detailed discussion with respect to future and open research avenues is also performed, which could help to pave the way for researchers to explore the key challenging areas in the Blockchain field.
In [7] Through reviewing various papers and websites, we identified common loopholes in existing systems, such as the ease of copying QR codes onto fake products, the dependency on mobile devices with specific apps for product authentication, and the complexity of using RFID tags or AI. Additionally, high product enrolment costs pose adoption challenges. To address these, we developed a website to eliminate the need for app installation, leveraging the Qrious library for cost-efficient QR code generation. Our system includes profiles for manufacturers, suppliers, and consumers, efficiently managing data, with MySQL storing user login information. Future enhancements include evaluating second-hand product value by analysing its lifecycle and user history, and introducing separate logins for customers, retailers, and suppliers for improved data management.
In [8] This decentralization characteristic eliminates the need for powerful central authorities and instead transfers control to the individual user making the system fair and considerably more secure. Information recording is performed, and the transactions are vali dated, using a set of rules and algorithms, called consensus protocols, among the Blockchain nodes to ensure that information is consistent and in corruption.
In [9], the network is composed of distributed nodes that function independently from one another. Each node is granted equal rights and responsibilities, ensuring that no single node has undue influence over the system. Furthermore, the design of the network is such that even if one or more nodes experience failure or corruption, the rest of the network remains unaffected. This decentralized structure significantly enhances the reliability of the system by reducing the risk of a single point of failure. Additionally, the robustness of the blockchain is improved as the network can continue to function seamlessly despite potential disruptions at the node level.
In [10] Data is stored in blocks where each block’s hash includes the hash of the previous block, combining with its own details to generate a unique hash. This chaining ensures immutability, as any tampering reflects across all blocks, breaking the chain. A proposed idea tracks product details from manufacturer to customer, allowing customers to verify the product’s authenticity using Blockchain’s secure and transparent technology. Once recorded, product details cannot be altered, ensuring trust. Customers can confirm authenticity by scanning the QR code via phone or verifying through a website using the IPFS protocol, distinguishing genuine products from counterfeits.
In [11] MetaMask, integrated with Spolia ether, is used for deploying contracts, adding products, and verifying them securely. A Solidity smart contract manages product data with functions like add (), update (), and show (), enabling data addition, modification, and retrieval while maintaining a history for each product ID. Leveraging blockchain’s immutability and transparency. it ensures a secure and tamper-proof system. This provides an efficient method for product data management on the blockchain.
|
Authors |
Title |
Research focus |
Remarks |
|
Jinhua Ma, Shih-Ya Lin, Xin Chen, 2016 |
Blockchain-Based Application System for Product Anti-Counterfeiting |
The research focuses on acceptance of products based on brand originality. |
The research provides a security for consumer acceptance of products. |
|
Atima Tharatipyakul and Suporn Pongnumkul, 2017 |
User Interface of Blockchain-Based Agri-Food Traceability Applications |
The research focuses on the blockchain technology for supply chain issues. |
The research proposes a method for facilitating bitcoin transactions and cryptocurrency on blockchain. |
|
Nafisa Anjum, Pramit Dutta |
Identifying Counterfeit Products using Blockchain Technology in Supply Chain System, |
The research focuses on proposing the algorithm for adding details of manufacturer, seller and customer. Also provides workflow of product distribution among them. |
The research proposes an algorithm to efficiently manage and trace the distribution process among manufacturers, sellers, and customers, enhancing transparency and accountability. |
|
Muhammad Nasir Mumtaz Bhutta Adnan Nadeem, Amira Khwaja 2021 |
Survey on Blockchain Technology: Evolution, Architecture and Security. |
The research focuses on working of hash function is one-way, which means original data cannot be calculated back from the unique output. |
The study proposes a its security strength lies on one-way characteristic, which is used to protect the integrity of data. |
|
KunalWasnik, Isha Sondawle, Rushikesh Wani and Namita Pulgam 03015 (2022) |
Detection of Counterfeit Products using Blockchain
|
The research paper focuses on concept of Ethereum technology and smart contracts in decentralized blockchain. |
The research paper proposes the blockchain's decentralization, proof-of-work mining, and tamper-proof smart contracts for automated agreements.
|
|
Jasleen kaur matharoo July 2023 |
Fake Product Detection System using Blockchain Technology
|
The research paper focuses on solidity in an object-oriented, high-level language for imple- menting smart contracts. |
The study proposes a solidity for implementing smart contracts. |
|
Shubham Musale, Devanshkar April 2023 |
Authenticity - Blockchain Based Counterfeit Product Detection |
The research paper focuses on generation of QR codes for authentication of product and customer. |
The research emphasizes using QR codes for efficient and secure product and customer authentication. |
|
Kishan Tiwari, Nikita Patil Mar ,2023 |
Fake Product Detection Using Blockchain Technology |
The research paper focuses on programming the exible script coding system can be used to create advanced smart contracts or other decentralized applications. |
The proposed method for programming for execution of advanced smart contracts and DApps. |
|
Prof. Sunil Yadav, Swayamprabha
|
Counterfeit Product Detection System Using Blockchain Technology |
Research focuses on suggesting features like transferring ownership once a seller purchases the product and uploading it to the blockchain.
|
The algorithm for implementing the manufacturer's function is suggested in the paper.
|
|
Antony Roshan Dsouza. Shantala Devi Patil. Amuthabala K 2023 |
Identification of Fake Product Identification using Blockchain |
The research focuses on the implementation of algorithm for distributing the products for the consumers. |
This article proposes the implementation of algorithm for manufacturer, customer and seller. |
|
RM Prakash Ramanathan, Mohamed Mudasir War |
Fake Product Identification using Blockchain |
This research focuses on method of converting manufacturer, seller and consumer data into hash value and will be stored into the Blockchain. |
This article proposes the concept of hash value conversion in blockchain. |
Table I: Summarization of Various Authors
III. RESULT
The proposed system enables manufacturers and suppliers to interact with the blockchain, adding their respective transaction details without altering others' blocks. Smart contracts for these interactions are written in Solidity and tested locally using Ganache, with configuration through truffle-config.js. Contracts are compiled and deployed using Truffle migration files for deployment on the Ethereum blockchain. The interface, built with React, leverages the Web3.js library to interact with the blockchain for actions like sending ether, confirming transactions, and managing smart contract data. MetaMask serves as the wallet for Ethereum blockchain interactions, with accounts from Ganache imported into it. Manufacturers and suppliers confirm transactions via MetaMask to add blocks. End-users can verify product integrity in the supply chain by scanning the QR code.
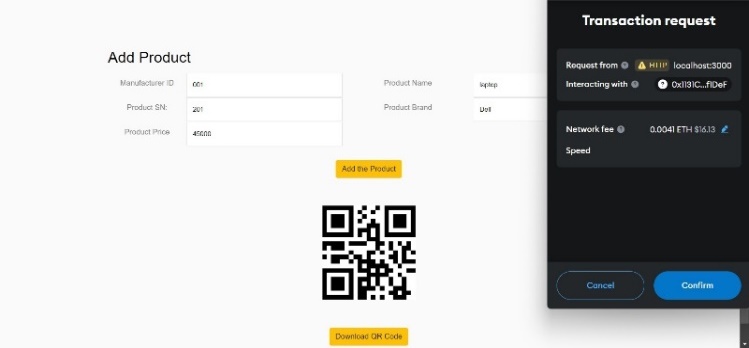
Fig 1: Home Page Fig 2: Add Product
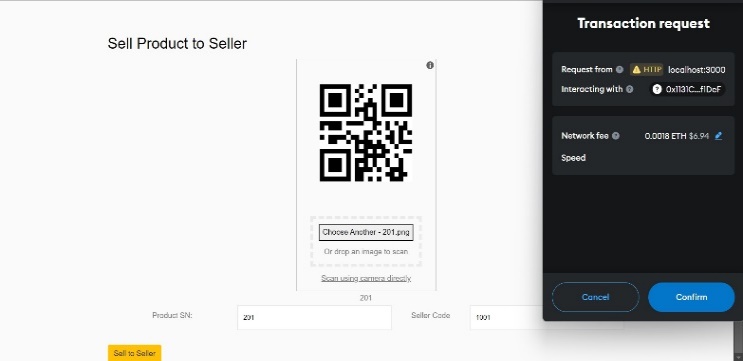
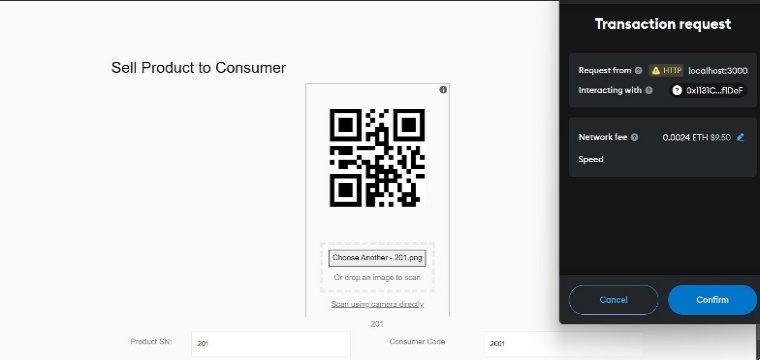
Fig 3: Sell Product to Seller Fig 4: Sell Product to Consumer
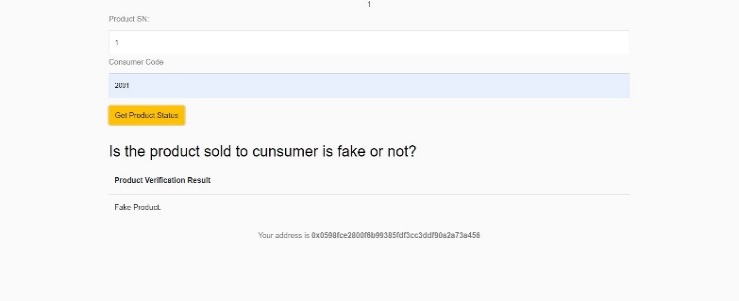
Fig 5: Product Verification
Conclusion
Blockchain is a decentralized system, therefore the local suppliers cannot interfere with the checking or counterfeiting of the product in the proposed system. Manufacturers and Suppliers can use the system to store product details in Blockchain which offers certain properties such as tamper resistance, data consistency and confidentiality that assure the security and privacy of the data on the network. The customer views the product supply chain history and verifies if the product is genuine. Customers can be sure about the integrity of goods they purchase. The proposed system can effectively lower the rate of counterfeiting of branded goods and provide the companies with an easier approach to provide consumers with the confidence that they will not purchase counterfeit goods. This system will help to build trust and good bonding between manufacturer and customer and indeed it will help in improving economy and reducing corruption. Further system can be extended to avoid frauds done in banking, healthcare, voting system, online shopping and soon.
References
[1] Naif Alzahrani and Nirupama Bulusu. Block-supply chain: A new anti-counterfeiting supply chain using nfc and blockchain. In Proceedings of the 1st Workshop on Cryptocurrencies and Blockchains for Distributed Systems, pages 30–35, 2018. [2] Kevin A Clauson, Elizabeth A Breeden, Cameron Davidson, and Timo thy K Mackey. Leveraging blockchain technology to enhance supply chain management in health care :: An exploration of challenges and opportunities in the health supply chain. Blockchain in healthcare today, 2018. [3] Chris Dannen. Introducing Ethereum and solidity, volume 1. Springer, 2017. [4] Roshan Jadhav, Altaf Shaikh, MA Jawale, AB Pawar, and P William. System for identifying fake product using blockchain technology. In 2022 7th International Conference on Communication and Electronics Systems (ICCES), pages 851–854. IEEE, 2022. [5] Randhir Kumar and Rakesh Tripathi. Traceability of counterfeit medicine supply chain through blockchain. In 2019 11th international conference on communication systems & networks (COMSNETS), pages 568–570. IEEE, 2019. [6] Donghang Lu, Pedro Moreno-Sanchez, Amanuel Zeryihun, Shivam Bajpayi, Sihao Yin, Ken Feldman, Jason Kosofsky, Pramita Mitra, and Aniket Kate. Reducing automotive counterfeiting using blockchain: Benefits and challenges. In 2019 IEEE International Conference on Decentralized Applications and Infrastructures (DAPPCON), pages 39 48. IEEE, 2019. [7] Sachin Modgil and Vandana Sonwaney. Planning the application of blockchain technology in identification of counterfeit products: Sectorial prioritization. IFAC-PapersOnLine, 52(13):1–5, 2019. [8] Satoshi Nakamoto. Bitcoin: A peer-to-peer electronic cash system. Decentralized business review, page 21260, 2008. [9] Michael Nofer, Peter Gomber, Oliver Hinz, and Dirk Schiereck. Blockchain. Business & Information Systems Engineering, 59:183–187, 2017. [10] T Shreekumar, Puneet Mittal, Sukhwinder Sharma, Rajesh N Kamath, Sreeja Rajesh, and B Nruthya Ganapathy. Fake product detection using blockchain technology. JOURNAL OF ALGEBRAIC STATISTICS, 13(3):2815–2821, 2022. [11] Edvard Tijan, Sa? sa Aksentijevi´c, Katarina Ivani´c, and Mladen Jardas. Blockchain technology implementation in logistics. Sustainability, 11(4):1185, 2019.
Copyright
Copyright © 2024 Sowmya D, Kruthi H D, Manvitha K V, Monisha Y C, Nagamani S. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET66013
Publish Date : 2024-12-19
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

