Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
The Role of API Security in Modern Enterprise Platforms
Authors: Pavan Vovveti
DOI Link: https://doi.org/10.22214/ijraset.2024.64365
Certificate: View Certificate
Abstract
This article explores the critical role of API security in modern enterprise platforms, addressing the growing importance of protecting Application Programming Interfaces (APIs) as they become increasingly central to digital ecosystems. We examine the fundamental challenges organizations face in securing their APIs, including authentication, data encryption, rate limiting, and version management. The paper presents a comprehensive overview of best practices for API security, such as implementing OAuth and token-based authentication, utilizing Transport Layer Security (TLS), deploying API gateways, and conducting regular audits. We discuss implementation strategies that integrate security throughout the API development lifecycle and highlight the importance of developer training. Through case studies, we illustrate both successful API security implementations and lessons learned from security breaches. The article also looks ahead to future trends in API security, considering the impact of emerging technologies like AI and quantum computing, as well as the evolving threat landscape. By providing a thorough analysis of current practices and future directions, this paper aims to equip organizations with the knowledge needed to develop robust, secure, and scalable API infrastructures that can support innovation while protecting critical data and resources in an increasingly interconnected digital world.
Introduction
I. INTRODUCTION
The proliferation of Application Programming Interfaces (APIs) has revolutionized the way modern enterprise platforms operate, enabling seamless integration and communication between diverse software systems. However, this interconnectedness has also exposed organizations to new security vulnerabilities, making API security a critical concern in today's digital landscape. As APIs increasingly serve as the backbone for data exchange and functionality across various applications, they have become prime targets for malicious actors seeking to exploit weaknesses in enterprise infrastructures [1].
This article explores the fundamental aspects of API security, addressing the challenges organizations face in protecting their APIs and outlining best practices for implementing robust security measures. By examining authentication mechanisms, encryption protocols, and monitoring strategies, we aim to provide a comprehensive overview of how enterprises can safeguard their APIs, thereby ensuring the integrity, confidentiality, and availability of their critical data and services in an increasingly interconnected world.
II. THE IMPORTANCE OF API SECURITY
APIs have become the cornerstone of modern enterprise architectures, serving as the vital connective tissue that enables disparate systems to communicate and share data efficiently. This interconnectedness has revolutionized business operations, allowing for unprecedented levels of automation, integration, and scalability. However, the ubiquity of APIs also presents significant security challenges that organizations must address to protect their digital assets and maintain customer trust.
A. APIs as the Backbone of Interconnected Systems
In today's digital ecosystem, APIs function as the primary means of data exchange and functionality sharing between applications, services, and platforms. They facilitate everything from cloud computing and microservices architectures to mobile app integrations and Internet of Things (IoT) device communications. This pervasive nature of APIs makes them critical to business operations and innovation, but also renders them attractive targets for cybercriminals [2].
B. Data Transfer and Exposure through APIs
APIs handle vast amounts of sensitive information, including personal user data, financial records, and proprietary business intelligence. As data flows through these interfaces, it becomes vulnerable to interception, manipulation, or unauthorized access if proper security measures are not in place. The exposure of data through APIs is particularly concerning given the increasing regulatory requirements surrounding data protection, such as GDPR and CCPA.
C. Potential Consequences of unsecured APIs
The ramifications of inadequately secured APIs can be severe and far-reaching. Data breaches resulting from API vulnerabilities can lead to significant financial losses, reputational damage, and legal consequences. For instance, a single API-related breach can expose millions of user records, as demonstrated by several high-profile incidents in recent years [3]. Moreover, unsecured APIs can be exploited to launch further attacks on an organization's infrastructure, potentially compromising entire systems and disrupting critical business operations. By recognizing the central role of APIs in modern enterprise platforms and understanding the potential risks associated with inadequate security, organizations can better appreciate the imperative of implementing robust API security measures. This awareness forms the foundation for developing comprehensive strategies to protect APIs and the valuable data they transmit, thereby safeguarding the integrity and resilience of interconnected digital ecosystems.
III. CHALLENGES IN API SECURITY
A. Authentication and Authorization
One of the primary challenges in API security is implementing robust authentication and authorization mechanisms. These processes ensure that only legitimate users and applications can access the API and its resources. However, designing and maintaining effective authentication systems can be complex, especially in large-scale distributed environments. Vulnerabilities in these systems can lead to unauthorized access, data breaches, and potential exploitation of API endpoints [4].
B. Data Encryption
Protecting data in transit is crucial for API security. Implementing strong encryption protocols is essential to prevent man-in-the-middle attacks and data interception. However, managing encryption across diverse API endpoints, especially in hybrid cloud environments, can be challenging. Organizations must also contend with the performance implications of encryption and decryption processes on API response times [5].
C. Rate Limiting
Implementing effective rate limiting is critical to prevent API abuse and protect against denial-of-service (DoS) attacks. However, setting appropriate rate limits that balance security with legitimate use cases can be challenging. Organizations must consider factors such as API usage patterns, user tiers, and potential business impacts when implementing rate-limiting strategies.
D. API Versioning
As APIs evolve, managing multiple versions becomes a significant challenge. Outdated or deprecated API versions can introduce security vulnerabilities if not properly maintained or retired. Balancing backward compatibility with security updates and new features requires careful planning and execution.
|
Challenge |
Best Practice |
|
Authentication and Authorization |
Implement OAuth 2.0 or token-based authentication |
|
Data Encryption |
Enforce Transport Layer Security (TLS) for all API traffic |
|
Rate Limiting |
Deploy API gateways with intelligent throttling mechanisms |
|
API Versioning |
Implement proper version control with clear deprecation policies |
|
Threat Detection |
Conduct regular audits and implement continuous monitoring |
Table 1: Common API Security Challenges and Best Practices [4-8]
IV. BEST PRACTICES FOR SECURING APIS
A. OAuth and Token-Based Authentication
Implementing OAuth 2.0 or other token-based authentication mechanisms is crucial for securing API access. These protocols provide a standardized way to grant limited access to resources without exposing user credentials. Token-based systems also enable fine-grained access control and can be more easily revoked or expired compared to traditional password-based systems [6].
B. Transport Layer Security (TLS)
Enforcing TLS encryption for all API traffic is essential to protect data in transit. Organizations should use the latest TLS versions and implement proper certificate management to ensure secure communications between clients and API endpoints.
C. API Gateways
Deploying API gateways can centralize security controls and policy enforcement across an organization's API ecosystem. Gateways can handle authentication, rate limiting, and logging, providing a unified point of control and monitoring for API traffic.
D. Regular Audits and Monitoring
Implementing continuous monitoring and regular security audits is crucial for maintaining API security. Automated tools can help detect vulnerabilities, unusual traffic patterns, and potential breaches in real-time. Regular penetration testing and code reviews should also be conducted to identify and address security weaknesses.
E. Throttling and Rate Limiting
Implementing intelligent throttling and rate limiting mechanisms helps prevent API abuse and protects against DoS attacks. These measures should be dynamic and adaptable to different user tiers and usage patterns.
F. Version Control
Proper version control for APIs, including clear deprecation policies and migration paths, is essential for maintaining security across different API versions. Organizations should have a strategy for updating and retiring older API versions to minimize security risks associated with outdated endpoints.
V. IMPLEMENTATION STRATEGIES
A. Integrating Security Practices into API Development Lifecycle
Incorporating security measures throughout the API development lifecycle is crucial for creating robust and secure APIs. This approach, often referred to as "Security by Design," involves considering security at every stage, from initial planning to deployment and maintenance. Implementing secure coding practices, conducting regular code reviews, and performing security testing during development can help identify and address vulnerabilities early in the process [7]. Additionally, adopting a DevSecOps approach can foster collaboration between development, security, and operations teams, ensuring that security remains a priority throughout the API lifecycle.
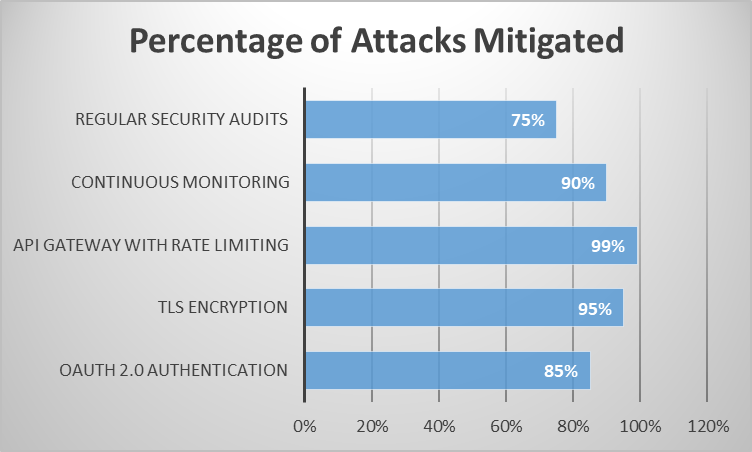
Fig 1: Effectiveness of Security Measures in Mitigating API Attacks [4-6]
B. Tools and Technologies for API Security
A wide range of tools and technologies are available to enhance API security. These include:
- API Security Testing Tools: Automated scanners and fuzzers that can identify common vulnerabilities in API implementations.
- Web Application Firewalls (WAFs): Specialized firewalls designed to protect web applications and APIs from various attacks.
- API Management Platforms: Comprehensive solutions that offer features such as access control, rate limiting, and analytics for API security and management.
- Threat Intelligence Platforms: Systems that provide real-time information about emerging threats and vulnerabilities specific to APIs.
Selecting and integrating the right combination of these tools based on an organization's specific needs and risk profile is essential for implementing a comprehensive API security strategy [8].
C. Training and Awareness Programs for Developers
Educating developers about API security best practices is crucial for maintaining a secure API ecosystem. Training programs should cover topics such as secure coding practices, common API vulnerabilities, and the proper implementation of authentication and authorization mechanisms. Regular workshops, online courses, and hands-on exercises can help developers stay updated on the latest security threats and mitigation techniques. Furthermore, fostering a security-aware culture within development teams can lead to more proactive identification and addressing of potential security issues.
VI. CASE STUDIES
A. Successful Implementation of API Security Measures in Enterprise Settings
- Case Study 1: A large financial services company implemented a comprehensive API security strategy, including OAuth 2.0 for authentication, an API gateway for centralized policy enforcement, and continuous monitoring. This approach resulted in a 70% reduction in security incidents related to their APIs over a two-year period.
- Case Study 2: A healthcare technology provider adopted a DevSecOps approach to API development, integrating security testing tools into their CI/CD pipeline. This implementation led to faster detection and remediation of vulnerabilities, with 95% of critical issues being addressed before production deployment.
B. Lessons Learned from API Security Breaches
- Case Study 3: A major social media platform experienced a significant data breach due to an insecure API endpoint. The incident exposed millions of user records and resulted in substantial financial and reputational damage. Key lessons included the importance of regular security audits, proper access control, and the need for continuous monitoring of API traffic patterns [9].
- Case Study 4: An e-commerce company faced a series of DDoS attacks targeting their public APIs. The incident highlighted the critical nature of implementing robust rate limiting and traffic analysis tools. After implementing these measures, the company successfully mitigated 99% of malicious traffic attempts.
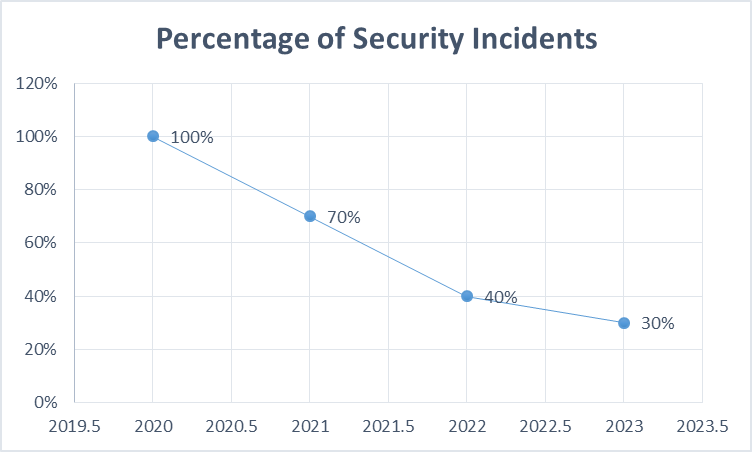
Fig 2: API Security Incident Reduction after Implementation of Best Practices [9]
These case studies underscore the importance of a comprehensive and proactive approach to API security. They demonstrate that successful implementation of security measures can significantly reduce risks, while also highlighting the severe consequences of neglecting API security.
VIII. FUTURE TRENDS IN API SECURITY
As the digital landscape continues to evolve, API security must adapt to new challenges and opportunities. The future of API security is likely to be shaped by emerging technologies and an ever-changing threat landscape, requiring organizations to stay vigilant and proactive in their security approaches.
A. Emerging Technologies and their Impact on API Security
The advent of new technologies is set to revolutionize API security. Artificial Intelligence (AI) and Machine Learning (ML) are poised to play a significant role in enhancing API protection. These technologies can be leveraged to detect anomalies in API traffic patterns, identify potential threats in real-time, and even predict future vulnerabilities based on historical data. Additionally, the integration of blockchain technology with APIs could provide enhanced security through immutable audit trails and decentralized authentication mechanisms.
Quantum computing, while still in its early stages, has the potential to both strengthen and challenge current API security measures. On one hand, quantum-resistant cryptography may become necessary to protect against the increased computational power of quantum computers. On the other, quantum key distribution could offer unprecedented levels of security for API communications.
B. Evolving threat Landscape and Adaptive Security Measures
The threat landscape for APIs is continuously evolving, with attackers developing increasingly sophisticated methods to exploit vulnerabilities. As a result, adaptive security measures are becoming crucial. Zero Trust Architecture (ZTA) is gaining traction as a security model for APIs, where trust is never assumed, and verification is required from everyone trying to access resources in the network. This approach is particularly relevant in the context of microservices and containerized environments, where traditional perimeter-based security models are less effective.
Another emerging trend is the use of Runtime Application Self-Protection (RASP) technologies for APIs. RASP can provide real-time protection by integrating security mechanisms directly into the API runtime environment, allowing for immediate threat detection and response [10].
|
Trend |
Description |
Potential Impact |
|
Artificial Intelligence and Machine Learning |
Use of AI/ML for anomaly detection and threat prediction |
Enhanced real-time threat detection and proactive security measures |
|
Zero Trust Architecture |
Verify every request regardless of its source |
Improved security in microservices and containerized environments |
|
Quantum Computing |
Development of quantum-resistant cryptography |
Stronger encryption methods to counter future quantum threats |
|
Runtime Application Self-Protection (RASP) |
Integration of security mechanisms directly into API runtime environment |
Immediate threat detection and response at the application level |
|
API Composition Security |
Ensuring security when multiple APIs are combined or chained |
Holistic protection for complex, interconnected API ecosystems |
Table 2: Emerging Trends in API Security [10]
Furthermore, as APIs become more complex and interconnected, the concept of API composition security is gaining importance. This involves ensuring that the security of an API is maintained not just at the individual endpoint level, but also when multiple APIs are combined or chained together to create more complex services. As the API ecosystem continues to grow and evolve, security strategies will need to become more dynamic and adaptive. Organizations must stay informed about emerging threats and technologies, continuously updating their security practices to stay ahead of potential attackers. The future of API security will likely involve a combination of advanced technologies, proactive threat intelligence, and a holistic approach to security that considers the entire API lifecycle and ecosystem.
Conclusion
In conclusion, the role of API security in modern enterprise platforms cannot be overstated. As APIs continue to serve as the critical infrastructure for digital transformation and innovation, the importance of robust security measures becomes increasingly paramount. Throughout this article, we have explored the multifaceted challenges organizations face in securing their APIs, from authentication and encryption to rate limiting and version control. We have also examined best practices and implementation strategies that can significantly enhance API security posture. The case studies presented highlight both the consequences of inadequate security and the benefits of comprehensive protection. Looking ahead, the landscape of API security is set to evolve rapidly, driven by emerging technologies and an ever-changing threat environment. Organizations must remain vigilant, adaptive, and proactive in their approach to API security. By integrating security considerations throughout the API lifecycle, leveraging advanced tools and technologies, and fostering a culture of security awareness, enterprises can build resilient API ecosystems that enable innovation while safeguarding critical data and resources. As we move forward, the ability to balance security with functionality and performance will be key to harnessing the full potential of APIs in driving business growth and digital transformation.
References
[1] Nagaraj et al., \"The State of API Security in 2023,\" [Online]. Available: https://www.infoworld.com/article/2335205/the-state-of-api-security-in-2023.html [2] Ganapathy, Vinod & Seshia, Sanjit & Jha, Somesh & Reps, Thomas & Bryant, Randal. (2004). Automatic Discovery of API-Level Vulnerabilities. [Online]. Available: https://www.researchgate.net/publication/2932734_Automatic_Discovery_of_API-Level_Vulnerabilities [3] Adeyemo et al., \"Comparative Analysis of API Security Testing Tools,\" in 2021 IEEE International Conference on Software Testing, Verification and Validation Workshops (ICSTW), 2021, pp. 170-179. [Online]. Available: https://saudijournals.com/media/articles/SJEAT_610_371-377_L8hRMPy.pdf [4] Ahmad, A., Malik, A.W., Alreshidi, A. et al. Adaptive Security for Self-Protection of Mobile Computing Devices. Mobile Netw Appl 28, 653–672 (2023). https://doi.org/10.1007/s11036-019-01355-y [Online]. Available: https://link.springer.com/article/10.1007/s11036-019-01355-y#citeas [5] M. Sabt, M. Achemlal, and A. Bouabdallah, \"Trusted Execution Environment: What It Is, and What It Is Not,\" in 2015 IEEE Trustcom/BigDataSE/ISPA, 2015, pp. 57-64. [Online]. Available: https://ieeexplore.ieee.org/document/7345265 [6] D. Fett, R. Küsters, and G. Schmitz, \"The Web SSO Standard OpenID Connect: In-Depth Formal Security Analysis and Security Guidelines,\" in 2017 IEEE 30th Computer Security Foundations Symposium (CSF), 2017, pp. 189-202. [Online]. Available: https://ieeexplore.ieee.org/document/8049720 [7] OWASP API Security Top 10, \" OWASP Top 10 API Security Risks – 2023“. [Online]. Available: https://owasp.org/API-Security/editions/2023/en/0x11-t10/ [8] Shneider, \"API Security: Threats, Tools, and Best Practices“[Online]. Available: https://www.pynt.io/learning-hub/api-security-guide/api-security [9] Anh Nguyen-Duc, Manh Viet Do, Quan Luong Hong, Kiem Nguyen Khac, Anh Nguyen Quang, On the adoption of static analysis for software security assessment–A case study of an open-source e-government project, Computers & Security, Volume 111, 2021, 102470, ISSN 0167-4048, [Online]. Available: https://doi.org/10.1016/j.cose.2021.102470 [10] Alotaibe, D.Z. 2024. IoT Security Model for Smart Cities based on a Metamodeling Approach. Engineering, Technology & Applied Science Research. 14, 3 (Jun. 2024), 14109–14118. DOI:https://doi.org/10.48084/etasr.7132 [Online]. Available: https://etasr.com/index.php/ETASR/article/view/7132
Copyright
Copyright © 2024 Pavan Vovveti. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET64365
Publish Date : 2024-09-27
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

