Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Secure Image Sharing: Innovating Encryption and Concealment Methods
Authors: Rajeev Keshetty, Marineni Tony Dylin, M U Anil Sagar, Dr. Rishi Sayal
DOI Link: https://doi.org/10.22214/ijraset.2024.62138
Certificate: View Certificate
Abstract
Data security techniques, notably concealment of information in encrypted images, play a pivotal role in safeguarding digital assets. Nonetheless, many methods in this domain face challenges in effectively balancing security and embedding capacity. To tackle this issue, we propose a novel approach integrating hybrid coding and Chinese remainder theorem-based secret sharing (CRTSS). Our method employs hybrid coding for concealing data within images, ensuring a robust embedding capacity. Initially, an iterative encryption process encrypts blocks while preserving their spatial correlation. CRTSS is then utilized to distribute these encrypted blocks across multiple shares, ensuring robust security. Leveraging the high geographical correlation within each share, data embedding is performed using the hybrid coding technique, effectively increasing capacity. The proposed method allows for the restoration of the original image without loss, even if some shares are corrupted or missing, as long as enough uncorrupted shares are available. Experimental results indicate superior embedding capacity compared to state-of-the-art techniques, including those relying on secret sharing. We present four variations of the proposed model, comprising two coupled and two separable cases, leading to a high-capacity concealment approach. The efficacy of our approach is demonstrated through experimental validation.
Introduction
I. INTRODUCTION
The rapid expansion of cloud computing and storage has coincided with the advancement of information technology, particularly with the maturation of 5G communication and transmission. Owing to the benefits of cloud computing, an increasing number of users are storing their information on the cloud, particularly multimedia files like photos, audio snippets, and video files. Since user data is stored on distant or cloud servers or is transferred over public networks, it is not necessarily secure and dependable. As a result, both industry and academics now give considerable attention to the data privacy issue. Numerous strategies exist to safeguard data security, including hashing, data concealing, encryption, and secret sharing (SS). Digital images are important data manifestations that have a wide range of uses in fields like legal forensics, photography, medicine, and the military. One of the areas of research interest is visual data concealing for security protection.
The secret data and cover image are the two things that make up the image data concealment system, as is widely known. To create a stego-picture in an undetectable way, secret data is integrated into the cover image. The picture data hiding mechanism should take into account two circumstances. One is that the cover image is superfluous and the secret data is uniquely safeguarded. Another is that, for military and medical purposes, both the cover picture and the secret data are essential, and both need to be error-free on the decoder side. It is obvious that the latter is reversible data hiding (RDH) and the former is irreversible data hiding. Due to its reversibility, Data Encryption is becoming more and more popular. Data Encryption techniques to date have primarily relied on lossless compression, difference expansion (DE), histogram shifting (HS), and pixel error expansion (PEE). These Data Encryption methods seek to achieve a favorable trade-off between modification distortion and embedding capability.
(1) For Data Encryption, we suggest a hybrid coding. The suggested hybrid coding can surpass the payload restriction of a single coding and obtain a high payload since it combines the benefits of several coding methods.
(2) For data concealing, we create a block-based CRTSS with limitations and a new iterative image encryption. There is greater space for data embedding since repeated encryption can precisely retain spatial correlation. Multiple encrypted shares with good spatial correlations can be produced by the planned CRTSS. Preprocessing is not necessary, and it won't cause data growth.
(3) To create a new Data concealment technique, we take advantage of the suggested hybrid coding, the iterative picture encryption, and the block-based CRTSS with limitations. The suggested approach works better in terms of embedding rate than several cutting-edge Data Concealment techniques, according to experimental results.
The rest of this paper is organized as follows. Section II reviews the related work of popular Data Concealment methods. Section III presents the proposed hybrid coding for Encryption. Section IV illustrates the proposed Data concealment method with secret sharing and hybrid coding in detail. The experimental results are discussed in Section V. Finally, Section VI concludes this paper.
II. RELATED WORK
Numerous Data Concealment techniques have been developed by researchers to date. The current Data Concealment methods can be broadly categorized into four groups: reserving room before encryption (RRBE) [26], [27], [28], [29], [30], [31], [32], [33]; vacating room by encryption (VRBE) [34], [35], [36], [37], [39], [40], [41], [42]; and SS based methods [43], [44], [45], [46], [47], [48], [49]. Together, these four categories comprise the majority of the current Data Concealment methods.
A. VRAE Based Methods
The initial image, which is built on a VRAE framework, was immediately encrypted using conventional image encryption algorithms such stream cipher and the advanced encryption standard (AES) in the early Data Concealment approaches [20], [21], [22], [23], [24], and [25]. The encrypted image in [20] is split up into many chunks. To make room for one hidden bit, the three least significant bits (LSBs) of each block's half pixels are flipped. The original image is simultaneously recovered and secret bits are extracted at the receiver side by using the fluctuation function after the marked image has been directly decrypted. Since then, some advancements in data extraction accuracy have been realized [21], [22]. Since then, some advancements in data extraction accuracy have been realized [21], [22]. Data extraction is not possible in [20], [21], and [22] when the encryption key is not provided. More adaptably, Zhang [23] and Qian and Zhang [24] suggested separable techniques that involve compressing some LSB planes of the stream cipher encrypted image to make more space for data embedding. In this way, data extraction becomes independent of picture recovery and the encryption key. To achieve data concealment, some randomly selected pixels from the stream cipher encrypted image are changed with secret bits in [25] in place of their high bit-planes. Since there are two possible outcomes for a single high bit-plane, "0" and "1," the prediction errors produced by these two outcomes are compared in order to recover the original image.
B. RRBE Based Methods
Despite the stream cipher's strong performance in picture encryption, the loss of pixel spatial correlation makes it challenging to remove an embedding room directly from the encrypted image. Consequently, a few RRBE-based strategies were put forth to help achieve large payloads [26], [27], [28], [29], [30], [31], [32], and [33]. In order to free up space before picture encryption, Ma et al. [26] integrated a few LSBs of the texture area into the smooth area using the conventional RDH technique. Secret data is included in the released room. The patch-level sparse representation method is employed in [27] to significantly reduce the amount of space in the original image. A binary-block embedding (BBE) technique was suggested by A binary-block embedding (BBE) technique was proposed by Yi and Zhou [28]. BBE is used to embed the original image's lower bit-planes into its upper bit-planes, freeing up the lower bit-planes for data hiding. The most important bits (MSBs) were rearranged by Chen and Chang [29] to construct bitstreams, which were then effectively compressed to provide the embedding room. In [30], the same high bit-planes that are successively labeled are compared between the original pixel and its predicted value. Secret bits are stored on the bit-planes with labels. In [31], secret bits are embedded into the embeddable bit-planes in accordance with the labels generated by hierarchically dividing the prediction errors into three magnitudes. In Yin et al. [32], To obtain a high embedding capacity, Yin et al. [32] employed pixel prediction and compressed the high bit-planes of prediction errors. In order to evacuate the huge room prior to encryption, an adaptive L predictor for preprocessing is constructed in Mohammadi's [33] general RRBE framework for Data Concealment.
C. VRBE Based Methods
Although RRBE-based techniques provide outstanding embedding performance, their practical applicability may be limited because the content owner lacks the computational capacity to undertake pretreatment operations or is unaware that the following data is hidden. Some particular encryption-based techniques, especially VRBE-based techniques, were presented to overcome this problem. The encrypted image in [34], [35], and [36] is produced by block permutation and block-based bit-XOR, both of which are capable of maintaining the correlation inside each encrypted block. Next, data concealing is accomplished by using difference compression [36], adaptive block encoding [35], and difference histogram shifting (DHS) [34]. The original image is encrypted in [37] and [38] by using block permutation and disordering bit planes, which transfers the redundant space from the original image to the encrypted image. To remove space for data concealment, high bit-plane portions of the encrypted image are compressed using efficient sparse coding. In order to maintain spatial correlations among image blocks, Yi and Zhou [39] first encrypted the original image using block permutation and block-based modulation. They then used parametric binary tree labeling (PBTL) to insert secret data into the encrypted image. In [40], redundancy is preserved in the encrypted image by employing the CE technique, which encrypts the original image in chunks using the stream cipher.
Subsequently, the redundancy matrix format is employed to free up space for data embedding. In order to obtain high embedding capacity, Yu et al. [41] presented an adaptive difference recovery (ADR) based data hiding technique and subsequently implemented this technique in Data Concealment. A generalized methodology for high-capacity Data Concealment utilizing pixel prediction and entropy encoding was presented by Qiu et al. [42] and is applicable to both the RRBE and VRBE scenarios.
D. SS Based Methods
An original image is converted into an encrypted version and uploaded to the cloud using the Data Concealment techniques mentioned above. Attacks by a third party could compromise the encrypted image and result in incorrect image recovery on the recipient's end. Some secret sharing (SS) based Data Concealment techniques were proposed [43], [44], [45], [46], [47], [48], and [49] in an effort to increase the robustness of RDHEI. Wu et al. [43] used pairwise Shamir's SS [10] to encrypt the original image in order to create the encrypted shares, ensuring that each share's pixel pair difference is equal to that of the original pair. Secret data can be integrated into shares using the DE or DHS technique because of difference preservation. Another SS was proposed by Chen et al. [44]. Another SS-based Data Concealment technique was proposed by Chen et al. [44]. This method encrypts a pair of pixels using a degree 3 polynomial after preprocessing them using the DE technique. The encrypted pixel pair may contain one secret bit inserted in it. One data-hider does the data concealing in [43] and [44].
The original image might not be recovered in the case that the data hider is an attacker for the original image since it might be an unreliable third party. Some multiple data-hiders based Data Concealment approaches using SS were presented [45], [46], [47], [48], and [49] to address this problem. These methods distribute each share to a single data-hider and provide independent data hiding on each share. Two Data Concealment techniques via SS over Galois fields GF(p) and GF(28) were proposed by Qin et al. [45]. These two techniques allow the embedding room to be abandoned in each share by preserving the pixel disparities within the 2x2 blocks of each share after SS. Multiple data-hiders get the encrypted shares in [46], which are produced using a particular Shamir's SS [10]. Through the bit-plane substitution approach, each data hider incorporates secret data into their share. Because Shamir's SS is often built on a finite field Fp with prime size 251, it is not possible to communicate pixels with values larger than 251. Accordingly, in these Shamir's SS based algorithms [43], [44], [45], and [46], the pixels with values more than 251 are prepossessed. CRTSS [8] is used in [47] to encrypt the original image and produce several shares. The additive homomorphism of CRT and the DE method are used in each share to hide data. Pixel enlargement arises from the use of CRTSS [8] and needs to be solved by compressing two MSBs of each share using this method. Because the DE approach is used, this method's embedding capacity is not high, hovering around 0.5 bpp. First presented by Hua et al. [48], cipher-feedback secret sharing (CFSS) is a technique that can be used to share images. An approach called multi-MSB prediction is used to hide data. Using matrix theory, Hua et al. [49] originally presented a matrix-based secret sharing (MSS). To attain a high payload, they subsequently suggested an MSS-RDHEI approach utilizing block error mixture encoding (BEME).
In essence, these high-payload Data Concealment methods nearly take use of certain coding strategies to represent the image context with less information, freeing up space for secret data like BEME [49], PBTL [39], and entropy encoding [42]. These single-coding methods can yet be improved upon, even though they can yield a large payload. In order to introduce a novel Data Concealment approach, we suggest in this study a hybrid coding with a bigger payload.
III. METHODOLOGIES
A. Proposed Hybrid Coding for RDH
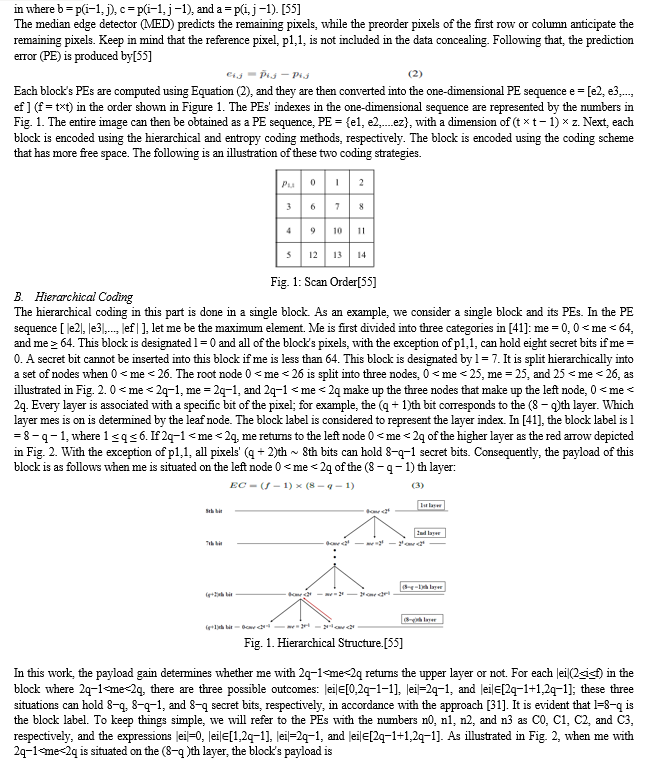
Here, we provide a hybrid coding scheme for data hiding. Entropy coding and hierarchical coding make up the hybrid coding method. Blocks are used to separate an image. Every block is encoded using either hierarchical or entropy coding. Additionally, the block is encoded using the coding technique that has more free space so that the embedding capacity is increased.
Assume that I is the original, 8-bit grayscale image with a size of H×W. First, the original image I is separated into n non-overlapping blocks, denoted by the numbers B1, B2,..., and Z, which are scanned in raster order. Every block has a t×t dimensions. The formula z=⌊H/t⌋×⌊W/t⌋ is evident. The prediction value of a block's pixel pi,j is determined as
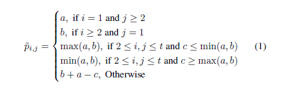




Conclusion
Our innovative Data Concealment technique makes use of hybrid coding and secret sharing. A substantial embedding room for each encrypted share can be achieved by the suggested method\'s combination of block-based CRTSS and iterative encryption, which can effectively pervert correlations within the blocks. Hybrid coding is used in each encrypted exchange to hide data with a large payload. Furthermore, the suggested approach does not call either pre-processing or pixel extension. According to experimental findings, the suggested approach performs better in the payload than a few cutting-edge SS-based Data Concealment techniques. Future Work: Future research will look into how to use the suggested model in additional scenarios, including a combined Data Encryption in images. Expanding the concept of secret sharing to include other forms of multimedia, including audio and video, is also an intriguing avenue to pursue.
References
[1] Y. Du, Z. Yin, and X. P. Zhang, “High capacity lossless data hiding in jpeg bit stream based on general vlc mapping,” IEEE Transactions on Dependable and Secure Computing, vol. 19, no. 2, pp. 1420–1433, 2022. [2] Z. Wang, G. Feng, L. Shen, and X. Zhang, “Cover selection for steganography using image similarity,” IEEE Transactions on Dependable and Secure Computing, pp. 1–13, 2022. [3] Y. Xian, X. Wang, and L. Teng, “Double parameters fractal sorting matrix and its application in image encryption,” IEEE Transactions on Circuits and Systems for Video Technology, vol. 32, no. 6, pp. 4028– 4037, 2022. [4] X. Wang and S. Gao, “Image encryption algorithm for synchronously updating boolean networks based on matrix semi-tensor product theory,” Information sciences, vol. 507, pp. 16–36, 2020. [5] Z. Tang, L. Chen, X. Q. Zhang, and S. Zhang, “Robust image hashing with tensor decomposition,” IEEE Transactions on Knowledge and Data Engineering, vol. 31, no. 3, pp. 549–560, 2019. [6] X. Liang, Z. Tang, J. Wu, Z. Li, and X. P. Zhang, “Robust image hashing with is map and saliency map for copy detection,” IEEE Transactions on Multimedia, pp. 1–1, 2021. [7] X. Liang, Z. Tang, Z. Huang, X. Q. Zhang, and S. Zhang, “Efficient hashing method using 2D-2D PCA for image copy detection,” IEEE Transactions on Knowledge and Data Engineering, pp. 1–1, 2021. [8] C. Asmuth and J. Bloom, “A modular approach to key safeguarding,” IEEE transactions on information theory, vol. 29, no. 2, pp. 208–210, 1983. [9] X. Yan, Y. Lu, L. Liu, and X. Song, “Reversible image secret sharing,” IEEE Transactions on Information Forensics and Security, vol. 15, pp. 3848–3858, 2020. [10] A. Shamir, “How to share a secret,” Communications of the ACM, vol. 22, no. 11, pp. 612–613, 1979. [11] X. Yan, Y. Lu, C.-N. Yang, X. Zhang, and S. Wang, “A common method of share authentication in image secret sharing,” IEEE Transactions on Circuits and Systems for Video Technology, vol. 31, no. 7, pp. 2896– 2908, 2021. [12] J. Tian, “Reversible data embedding using a difference expansion,” IEEE transactions on circuits and systems for video technology, vol. 13, no. 8, pp. 890–896, 2003. [13] Z. Ni, Y.-Q. Shi, N. Ansari, and W. Su, “Reversible data hiding,” IEEE Transactions on circuits and systems for video technology, vol. 16, no. 3, pp. 354–362, 2006. [14] W. Zhang, X. Hu, X. Li, and N. Yu, “Recursive histogram modification: establishing equivalency between reversible data hiding and lossless data compression,” IEEE transactions on image processing, vol. 22, no. 7, pp. 2775–2785, 2013. [15] W. Zhang, X. Hu, X. Li, and Y. Nenghai, “Optimal transition probability of reversible data hiding for general distortion metrics and its applications,” IEEE Transactions on Image Processing, vol. 24, no. 1, pp. 294–304, 2014. [16] C. Yu, X. Q. Zhang, D. Wang, and Z. Tang, “Reversible data hiding with pairwise PEE and 2D-PEH decomposition,” Signal Processing, vol. 196, p. 108527, 2022. [17] D. Wang, X. Q. Zhang, C. Yu, and Z. Tang, “Reversible data hiding by using adaptive pixel value prediction and adaptive embedding bin selection,” IEEE Signal Processing Letters, vol. 26, no. 11, pp. 1713– 1717, 2019. [18] W. Puech, M. Chaumont, and O. Strauss, “A reversible data hiding method for encrypted images,” in Security, forensics, steganography, and watermarking of multimedia contents X, vol. 6819, p. 68191E, International Society for Optics and Photonics, 2008. [19] P. Puteaux and W. Puech, “An efficient msb prediction-based method for high-capacity reversible data hiding in encrypted images,” IEEE Transactions on Information Forensics and Security, vol. 13, no. 7, pp. 1670–1681, 2018. [20] X. P. Zhang, “Reversible data hiding in encrypted image,” IEEE signal processing letters, vol. 18, no. 4, pp. 255–258, 2011. [21] W. Hong, T.-S. Chen, and H.-Y. Wu, “An improved reversible data hiding in encrypted images using side match,” IEEE Signal Processing Letters, vol. 19, no. 4, pp. 199–202, 2012. [22] X. Liao and C. Shu, “Reversible data hiding in encrypted images based on absolute mean difference of multiple neighboring pixels,” Journal of Visual Communication and Image Representation, vol. 28, pp. 21–27, 2015. [23] X. P. Zhang, “Separable reversible data hiding in encrypted image,” IEEE transactions on information forensics and security, vol. 7, no. 2, pp. 826–832, 2011. [24] Z. Qian and X. P. Zhang, “Reversible data hiding in encrypted images with distributed source encoding,” IEEE Transactions on Circuits and Systems for Video Technology, vol. 26, no. 4, pp. 636–646, 2015. [25] X. Wu and W. Sun, “High-capacity reversible data hiding in encrypted images by prediction error,” Signal processing, vol. 104, pp. 387–400, 2014. [26] K. Ma, W. Zhang, X. Zhao, N. Yu, and F. Li, “Reversible data hiding in encrypted images by reserving room before encryption,” IEEE Transactions on information forensics and security, vol. 8, no. 3, pp. 553–562, 2013. [27] X. Cao, L. Du, X. Wei, D. Meng, and X. Guo, “High capacity reversible data hiding in encrypted images by patch-level sparse representation,” IEEE transactions on cybernetics, vol. 46, no. 5, pp. 1132–1143, 2016. [28] S. Yi and Y. Zhou, “Binary-block embedding for reversible data hiding in encrypted images,” Signal Processing, vol. 133, pp. 40–51, 2017. [29] K. Chen and C.-C. Chang, “High-capacity reversible data hiding in encrypted images based on extended run-length coding and block-based msb plane rearrangement,” Journal of Visual Communication and Image Representation, vol. 58, pp. 334–344, 2019. [30] Z. Yin, Y. Xiang, and X. P. Zhang, “Reversible data hiding in encrypted images based on multi-msb prediction and huffman coding,” IEEE Transactions on Multimedia, vol. 22, no. 4, pp. 874–884, 2020. [31] C. Yu, X. Q. Zhang, X. P. Zhang, G. Li, and Z. Tang, “Reversible data hiding with hierarchical embedding for encrypted images,” IEEE Transactions on Circuits and Systems for Video Technology, vol. 32, no. 2, pp. 451–466, 2022. [32] Z. Yin, Y. Peng, and Y. Xiang, “Reversible data hiding in encrypted images based on pixel prediction and bit-plane compression,” IEEE Transactions on Dependable and Secure Computing, vol. 19, no. 2, pp. 992–1002, 2022. [33] A. Mohammadi, “A general framework for reversible data hiding in encrypted images by reserving room before encryption,” Journal of Visual Communication and Image Representation, vol. 85, p. 103478, 2022. [34] F. Huang, J. Huang, and Y.-Q. Shi, “New framework for reversible data hiding in encrypted domain,” IEEE transactions on information forensics and security, vol. 11, no. 12, pp. 2777–2789, 2016. [35] Y. Fu, P. Kong, H. Yao, Z. Tang, and C. Qin, “Effective reversible data hiding in encrypted image with adaptive encoding strategy,” Information Sciences, vol. 494, pp. 21–36, 2019. [36] Z. Tang, S. Xu, H. Yao, C. Qin, and X. Q. Zhang, “Reversible data hiding with differential compression in encrypted image,” Multimedia Tools and Applications, vol. 78, no. 8, pp. 9691–9715, 2019. [37] Z. Liu and C. Pun, “Reversible data-hiding in encrypted images by redundant space transfer,” Information Sciences, vol. 433, pp. 188–203, 2018. [38] C. Qin, X. Qian, W. Hong, and X. P. Zhang, “An efficient coding scheme for reversible data hiding in encrypted image with redundancy transfer,” Information Sciences, vol. 487, pp. 176–192, 2019. [39] S. Yi and Y. Zhou, “Separable and reversible data hiding in encrypted images using parametric binary tree labeling,” IEEE Transactions on Multimedia, vol. 21, no. 1, pp. 51–64, 2019. [40] Z. Liu and C. Pun, “Reversible data hiding in encrypted images using chunk encryption and redundancy matrix representation,” IEEE Transactions on Dependable and Secure Computing, vol. 19, no. 2, pp. 1382–1394, 2022. [41] [41] C. Yu, X. Q. Zhang, G. Li, S. Zhan, and Z. Tang, “Reversible data hiding with adaptive difference recovery for encrypted images,” Information Sciences, vol. 584, pp. 89–110, 2022. [42] Y. Qiu, Q. Ying, Y. Yang, H. Zeng, S. Li, and Z. Qian, “High-capacity framework for reversible data hiding in encrypted image using pixel prediction and entropy encoding,” IEEE Transactions on Circuits and Systems for Video Technology, vol. 32, no. 9, pp. 5874–5887, 2022. [43] X. Wu, J. Weng, and W. Yan, “Adopting secret sharing for reversible data hiding in encrypted images,” Signal Processing, vol. 143, pp. 269–281, 2018. [44] Y. Chen, T. Hung, S. Hsieh, and C. Shiu, “A new reversible data hiding in encrypted image based on multi-secret sharing and lightweight cryptographic algorithms,” IEEE Transactions on Information Forensics and Security, vol. 14, no. 12, pp. 3332–3343, 2019. [45] C. Qin, C. Jiang, Q. Mo, H. Yao, and C. Chang, “Reversible data hiding in encrypted image via secret sharing based on GF (p) and GF (28),” IEEE Transactions on Circuits and Systems for Video Technology, vol. 32, no. 4, pp. 1928–1941, 2022. [46] B. Chen, W. Lu, J. Huang, J. Weng, and Y. Zhou, “Secret sharing based reversible data hiding in encrypted images with multiple data-hiders,” IEEE Transactions on Dependable and Secure Computing, vol. 19, no. 2, pp. 978–991, 2022. [47] Y. Ke, M. Zhang, X. P. Zhang, J. Liu, T. Su, and X. Yang, “A reversible data hiding scheme in encrypted domain for secret image sharing based on chinese remainder theorem,” IEEE Transactions on Circuits and Systems for Video Technology, vol. 32, no. 4, pp. 2469–2481, 2022. [48] Z. Hua, Y. Wang, S. Yi, Y. Zhou, and X. Jia, “Reversible data hiding in encrypted images using cipher-feedback secret sharing,” IEEE Transactions on Circuits and Systems for Video Technology, vol. 32, no. 8, pp. 4968–4982, 2022. [49] Z. Hua, Y. Wang, S. Yi, Y. Zheng, X. Liu, Y. Chen, and X. Zhang, “Matrix-based secret sharing for reversible data hiding in encrypted images,” IEEE Transactions on Dependable and Secure Computing, 2022. [50] L. Qu, F. Chen, S. Zhang, and H. He, “Cryptanalysis of reversible data hiding in encrypted images by block permutation and co-modulation,” IEEE Transactions on Multimedia, vol. 24, pp. 2924–2937, 2021. [51] L. Qu, H. He, and F. Chen, “On the security of block permutation and coxor in reversible data hiding,” IEEE Transactions on Circuits and Systems for Video Technology, vol. 32, no. 3, pp. 920–932, 2022. [52] P. Bas, T. Filler, and T. Pevn`y, “Break our steganographic system: The ins and outs of organizing boss,” in International workshop on information hiding, pp. 59–70, Springer, 2011. [53] P. Bas and T. Furon, “Image database of bows-2,” Accessed: Jun, vol. 20, 2017. [54] G. Schaefer and M. Stich, “Ucid: An uncompressed color image database,” in Storage and Retrieval Methods and Applications for Multimedia 2004, vol. 5307, pp. 472–480, International Society for Optics and Photonics, 2003. [55] C. Yu, X. Zhang, C. Qin and Z. Tang, \"Reversible Data Hiding in Encrypted Images With Secret Sharing and Hybrid Coding,\" in IEEE Transactions on Circuits and Systems for Video Technology, vol. 33, no. 11, pp. 6443-6458, Nov. 2023, doi: 10.1109/TCSVT.2023.3270882.
Copyright
Copyright © 2024 Rajeev Keshetty, Marineni Tony Dylin, M U Anil Sagar, Dr. Rishi Sayal. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET62138
Publish Date : 2024-05-15
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

