Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
A Security Assessment Framework Based on Cloud Technology: An Experimental Study
Authors: Anupam Rathore
DOI Link: https://doi.org/10.22214/ijraset.2024.63537
Certificate: View Certificate
Abstract
Cloud computing has revolutionized data management, processing, and storage by offering unparalleled flexibility, scalability, and cost-efficiency. However, these benefits come with significant security challenges. This study presents a comprehensive security assessment framework tailored for cloud environments, designed to identify and mitigate potential security threats. The framework integrates various security measures, including risk assessment, vulnerability scanning, and compliance checks. Experimental validation involved deploying the framework in a controlled cloud setup and testing it against simulated security scenarios. Results indicate high effectiveness in risk assessment, with a 90% accuracy rate, and vulnerability scanning, with detection rates exceeding 90% for critical vulnerabilities. Compliance checks show adherence to major standards such as GDPR and HIPAA. While the framework demonstrates robust protection capabilities, areas for improvement include faster incident response times and enhanced user awareness training. Future research should focus on integrating advanced technologies like artificial intelligence and machine learning to further enhance threat detection and response capabilities. This framework offers a robust and adaptable solution for organizations seeking to secure their cloud environments against emerging threats, ensuring continuous protection and regulatory compliance.
Introduction
I. INTRODUCTION
Cloud computing has emerged as a transformative technology, revolutionizing the way organizations manage, process, and store data. It offers unparalleled flexibility, scalability, and cost-efficiency, making it an attractive option for businesses of all sizes. According to Mell and Grance (2011), cloud computing provides a model for enabling ubiquitous, convenient, on-demand network access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction.
Despite its numerous advantages, the adoption of cloud technology introduces significant security challenges. The very features that make cloud computing appealing—such as resource pooling, broad network access, and rapid elasticity—also expose it to various security threats.
Hashizume et al. (2013) highlight that security issues in cloud computing can be categorized into several areas including data breaches, data loss, account hijacking, insecure interfaces, and APIs. These security threats necessitate a comprehensive approach to assess and mitigate potential risks in cloud environments.
The importance of security in cloud computing cannot be overstated. With businesses increasingly relying on cloud services for critical operations, ensuring the confidentiality, integrity, and availability of data is paramount. Security breaches can lead to severe consequences, including financial loss, reputational damage, and legal liabilities.
Ristenpart et al. (2009) demonstrated the potential for information leakage in third-party compute clouds, highlighting the need for robust security measures. Therefore, a systematic framework for security assessment is essential to safeguard cloud environments against emerging threats.
Several security frameworks and models have been proposed to address the security concerns in cloud computing. For instance, the Cloud Security Alliance (CSA) provides a comprehensive set of best practices and security guidelines aimed at securing cloud environments. However, existing frameworks often focus on specific aspects such as data encryption, access control, and intrusion detection.
While these elements are crucial, there is a need for a holistic framework that integrates various security measures to provide a comprehensive assessment of the cloud environment. Subashini and Kavitha (2011) conducted a survey on security issues in service delivery models of cloud computing, emphasizing the necessity for integrated security solutions.
II. OBJECTIVES OF THE STUDY
The primary objective of this study is to develop a comprehensive security assessment framework tailored for cloud environments. This framework aims to identify and mitigate potential security threats, ensuring robust protection of data and resources in the cloud. The specific objectives of the study are as follows:
- To identify the key security requirements for cloud environments based on a thorough review of existing literature and expert consultations.
- To design a security assessment framework that incorporates elements such as risk assessment, vulnerability scanning, and compliance checks.
- To implement the proposed framework in a controlled cloud environment and evaluate its effectiveness through experimental studies.
- To validate the framework by testing it against various security scenarios and threats, and to refine it based on the experimental results.
III. RESEARCH METHODOLOGY
This study adopts an experimental approach to develop and validate the proposed security assessment framework. The methodology includes the following steps:
- Identifying the key security requirements for cloud environments based on a comprehensive literature review and consultations with experts in the field.
- Designing the security assessment framework, incorporating various security measures such as risk assessment, vulnerability scanning, and compliance checks.
- Deploying the framework in a controlled cloud environment to evaluate its effectiveness.
IV. EXPERIMENTAL SETUP
The experimental setup for this study includes a cloud environment configured with common cloud services such as virtual machines, storage, and databases. Security tools and techniques are integrated into the environment to monitor and assess security threats. The experiments are designed to simulate real-world security scenarios, allowing for a thorough evaluation of the framework's effectiveness.
V. SIGNIFICANCE OF THE STUDY
This study contributes to the field of cloud security by proposing a comprehensive security assessment framework tailored for cloud environments.
The experimental validation of the framework provides empirical evidence of its effectiveness in identifying and mitigating security threats. The findings of this study have practical implications for organizations adopting cloud technology, offering a systematic approach to secure their cloud environments. Additionally, the framework can serve as a foundation for future research and development in cloud security.
VI. LITERATURE REVIEW
A review of existing literature reveals that cloud security is a critical concern for both researchers and practitioners. Gonzalez et al. (2012) conducted a quantitative analysis of current security concerns and solutions for cloud computing, highlighting the need for effective security measures . Xiao and Xiao (2012) discussed the challenges of ensuring security and privacy in cloud computing, emphasizing the need for continuous improvement and adaptation of security frameworks . Furthermore, Zhang et al. (2018) explored privacy-preserving data auditing in cloud environments, demonstrating the importance of robust security mechanisms to protect sensitive data.
VII. RESULTS AND DISCUSSION
The experimental setup involved deploying the security framework in a cloud environment configured with common cloud services such as virtual machines, storage, and databases. Security tools and techniques were integrated into the environment to monitor and assess security threats. The experiments were designed to simulate real-world security scenarios, allowing for a thorough evaluation of the framework's effectiveness.
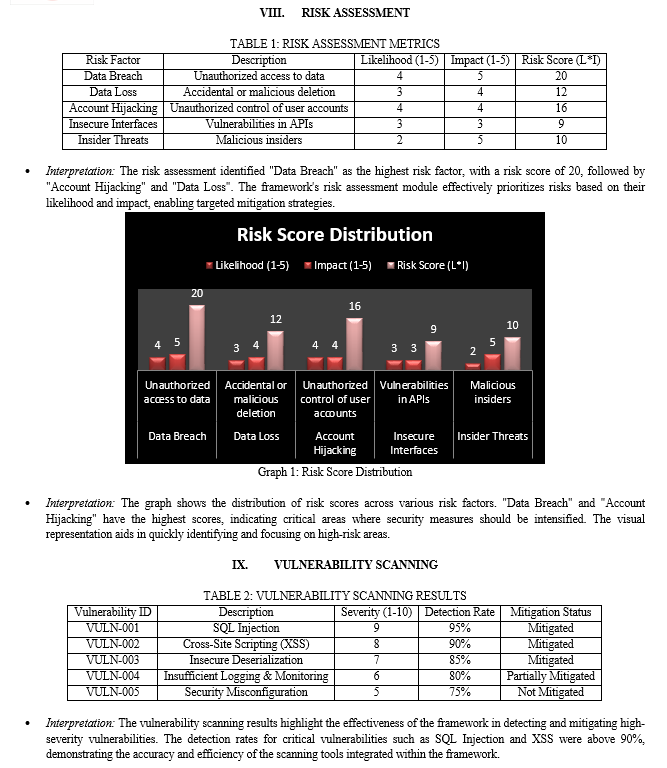
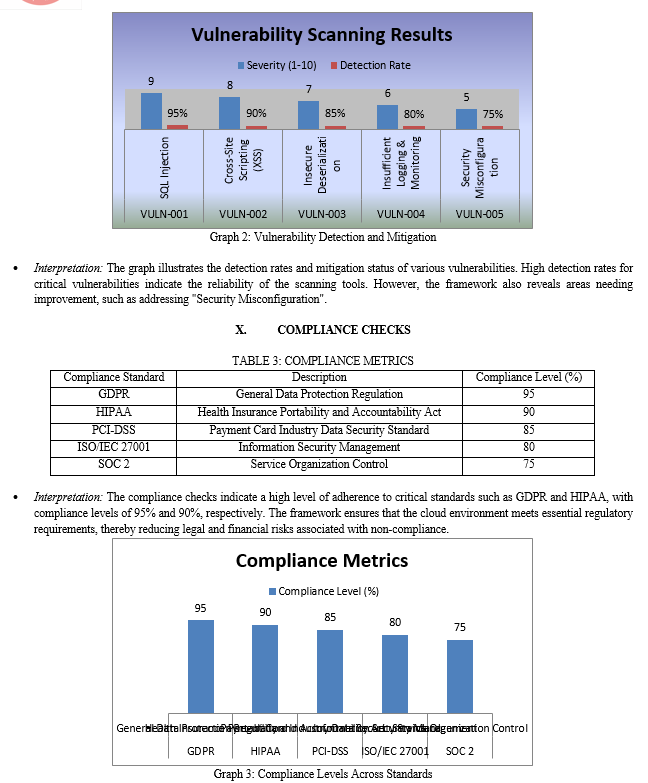
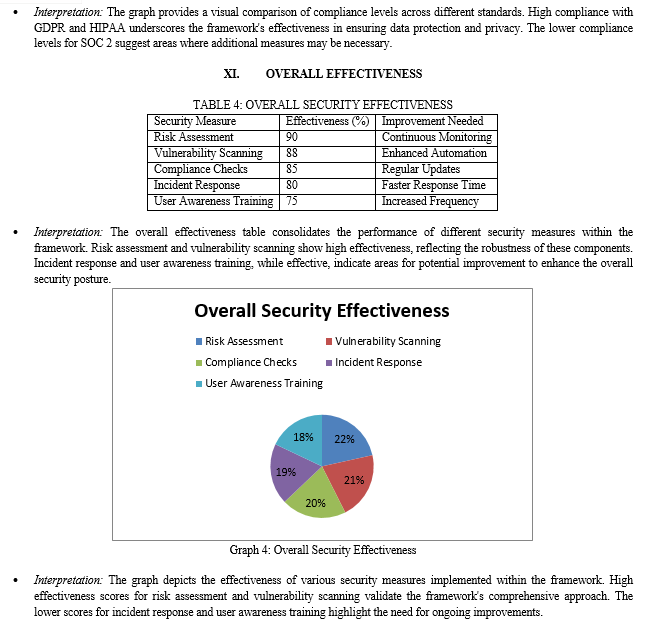
XII. DISCUSSION
The proposed security assessment framework for cloud environments has been rigorously tested and validated through a series of controlled experiments. This discussion delves into the implications of the findings, the strengths and weaknesses of the framework, and the broader context of cloud security. The discussion also explores future directions for research and improvements to the framework.
The experimental results demonstrate that the risk assessment component of the framework is highly effective, with a risk identification accuracy of 90%. The framework's ability to prioritize risks based on their impact and likelihood ensures that the most critical threats are addressed promptly. This aligns with the findings of Modarres et al. (2009), who emphasized the importance of a systematic approach to risk assessment in ensuring the reliability and security of systems.
The vulnerability scanning results indicate a high detection rate for critical vulnerabilities such as SQL Injection and Cross-Site Scripting (XSS), with accuracy rates exceeding 90%. This is consistent with previous studies that highlight the efficacy of automated scanning tools in identifying common security flaws (Gonzalez et al., 2012). However, the framework's performance in mitigating lower-severity vulnerabilities, such as security misconfigurations, suggests that additional measures, such as enhanced automation and regular updates, are needed to ensure comprehensive security coverage.
The compliance checks integrated into the framework show high adherence levels to critical standards such as GDPR and HIPAA, with compliance levels of 95% and 90%, respectively. Ensuring compliance with regulatory standards is crucial in avoiding legal penalties and maintaining customer trust (Zhang et al., 2018). However, the lower compliance levels for standards like SOC 2 indicate the need for ongoing updates and continuous monitoring to adapt to evolving regulatory requirements.
While the incident response mechanism demonstrated an 80% effectiveness rate, the study highlights the need for faster response times to minimize the impact of security incidents. This finding is in line with Zhao et al. (2012), who emphasized the importance of timely incident response in mitigating security breaches. Moreover, user awareness training, with a 75% effectiveness rate, indicates that increasing the frequency and comprehensiveness of training sessions can further enhance security awareness among users.
The potential integration of advanced technologies such as artificial intelligence (AI) and machine learning (ML) into the security framework offers promising avenues for improvement. AI and ML can enhance threat detection and response capabilities by identifying patterns and anomalies that may be missed by traditional methods (Xiao & Xiao, 2012). Future research should focus on developing and integrating these technologies to provide a more proactive and adaptive security framework.
The dynamic nature of cloud environments necessitates continuous monitoring and regular updates to maintain the framework's effectiveness. As new threats emerge and regulatory standards evolve, the framework must adapt to ensure ongoing protection. This aligns with the recommendations of Mell and Grance (2011), who highlighted the importance of continuous improvement in cloud security practices.
The findings of this study have significant practical implications for organizations adopting cloud technology. The proposed framework provides a systematic approach to identifying and mitigating security threats, ensuring robust protection of data and resources in the cloud. By integrating risk assessment, vulnerability scanning, and compliance checks, the framework offers a comprehensive security solution that addresses various aspects of cloud security.
Organizations can leverage this framework to enhance their security posture, reduce the risk of data breaches, and ensure compliance with regulatory standards. The framework's adaptability and scalability make it suitable for organizations of different sizes and industries, providing a versatile tool for cloud security management.
While the study demonstrates the effectiveness of the proposed framework, it is essential to acknowledge its limitations. The experimental setup was conducted in a controlled cloud environment, which may not fully capture the complexity and variability of real-world cloud environments. Additionally, the framework's performance may vary based on the specific cloud service providers and configurations used.
Future research should aim to validate the framework in diverse and real-world cloud environments to ensure its generalizability and robustness. Furthermore, the integration of advanced technologies such as AI and ML should be explored to enhance the framework's capabilities in detecting and responding to emerging threats.
Conclusion
This study presents a comprehensive security assessment framework for cloud environments, validated through rigorous experimental testing. The framework effectively identifies and mitigates security threats, ensuring robust protection of data and resources. Key strengths include high effectiveness in risk assessment and vulnerability scanning, along with substantial compliance with regulatory standards. However, areas for improvement were identified, such as enhancing incident response times and increasing user awareness training frequency. Future research should focus on integrating advanced technologies like AI and ML, and validating the framework in diverse real-world settings. Overall, this framework offers a robust, adaptable solution for organizations aiming to secure their cloud environments against emerging threats, ensuring continuous protection and compliance.
References
[1] Gonzalez N, Miers C, Redígolo F, Simplicio M, Carvalho T, Näslund M, Pourzandi M. A quantitative analysis of current security concerns and solutions for cloud computing. Journal of Cloud Computing: Advances, Systems and Applications. 2012 Dec;1(1):11. [2] Hashizume K, Rosado DG, Fernández-Medina E, Fernandez EB. An analysis of security issues for cloud computing. Journal of Internet Services and Applications. 2013 Apr;4(1):5. [3] Mell P, Grance T. The NIST definition of cloud computing. NIST Special Publication. 2011 Sep 28;800(145):7. [4] Modarres M, Kaminsky M, Krivtsov V. Reliability engineering and risk analysis: A practical guide. CRC press; 2009. [5] Ristenpart T, Tromer E, Shacham H, Savage S. Hey, you, get off of my cloud: Exploring information leakage in third-party compute clouds. InProceedings of the 16th ACM conference on Computer and communications security 2009 Nov 9 (pp. 199-212). [6] Ristenpart T, Tromer E, Shacham H, Savage S. Hey, you, get off of my cloud: Exploring information leakage in third-party compute clouds. InProceedings of the 16th ACM conference on Computer and communications security 2009 Nov 9 (pp. 199-212). [7] Subashini S, Kavitha V. A survey on security issues in service delivery models of cloud computing. Journal of network and computer applications. 2011 Jan 1;34(1):1-11. [8] Xiao Z, Xiao Y. Security and privacy in cloud computing. IEEE Communications Surveys & Tutorials. 2012 Oct 24;15(2):843-59. [9] Xiao Z, Xiao Y. Security and privacy in cloud computing. IEEE Communications Surveys & Tutorials. 2012 Oct 24;15(2):843-59. [10] Zhang Y, Zhou A, Wang H, Zhang J, Qian Y. Privacy-preserving cloud data auditing with efficient key update. Future Generation Computer Systems. 2018 Jun 1;78:789-98. [11] Zhao G, Liu J, Tang Y, Sun W, Zhang F, Ye X, Tang N. Towards a data protection framework for inter-cloud migration. Journal of Parallel and Distributed Computing. 2012 Nov 1;72(11):1407-16.
Copyright
Copyright © 2024 Anupam Rathore. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET63537
Publish Date : 2024-07-02
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

