Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Spyware Surveillance on Keyboard Through Electronic Messaging Protocol
Authors: Reddyvari Venkateswara Reddy, Gattu Laxmi Priya, K Varshini, Mahankali Varun
DOI Link: https://doi.org/10.22214/ijraset.2024.59835
Certificate: View Certificate
Abstract
The cause of the keylogger characteristic described on this paper is to reveal and file using the programs on the laptop system. The software makes use of the Python programming language and libraries such as pynput, smtplib, pyautogui, and OpenCV. The important features of this keylogger include taking pictures keystrokes, shooting timestamps, viewing energetic window titles, typing search queries, and appearing actions with right mouse clicks. The keylogger runs in the heritage and captures all keystrokes by means of the user, including letters, places, and input key presses. Timestamps are recorded to test the timing of each keystroke. In addition, the program retrieves the title of the active window to offer a description of the keystroke. It also lists the phrases or queries that the user searched for. In addition, the keylogger is programmed to take a screenshot of the display screen and locate a right mouse click on and take a photo of the consumer with a web browser and then e mail those screenshots and pictures to the designated recipient. The electronic mail provider is created the use of the smtplib library, which permits keyloggers to safely ship recorded statistics to an e-mail cope with. Overall, this keylogger function offers high stages of surveillance, allowing diffused tracking of person pastime and providing precious insights into their interactions with the computer machine
Introduction
I. INTRODUCTION
In this electronical era, where generation infiltrates every aspect of our lives, the trouble of keyboard spyware surveillance looms larger than ever. From vicious hackers to government realities, the eventuality for unauthorized access to our keystrokes poses a significant threat to our sequestration and security.
In this composition, we will develop into the world of keyboard spyware surveillance, exploring its types, counteraccusations, and ways to cover ourselves from this invasive trouble.
A. Spyware
Spyware is a sort of bug that's designed to foray your computer or device and collect information without your knowledge or concurrence. Unlike contagions and worms, which primarily aim to beget detriment or spread, spyware works discreetly to cover and collect data. Spyware comes in numerous forms and uses different tactics to insinuate your system.
Keyloggers: These programs record druggies' keystrokes, allowing bushwhackers to collect data similar as watchwords, credit card figures, and other particular information.
Analytics eyefuls: websites store this small piece of information on your device to track your online conditioning and preferences. Tracking eyefuls aren't always considered spyware, but they can be worn for protrusive advertising and stoner profiling.
Trojan nags: Trojan nags: Trojan nags pretend to be licit software in order to trick druggies into downloading and installing it. Previously installed, this Trojan horse can perform colorful vicious conditioning similar to data theft, system theft, and remote control.
Adware: Adware displays unwanted announcements on druggies' bias, frequently generating profit for bushwhackers through pay- per- click systems. Although adware isn't vicious in nature, it can violate stoner sequestration and affect system performance.
Cybersurfer hitchhikers: These programs change your cybersurfer settings without your concurrence, deflect you to unwanted websites, and display protrusive announcements. Cybersurfer stealers can also cover your internet browsing conditioning and collect sensitive data.
Spyware can pose significant pitfalls to your sequestration, security, and finances. This can lead to identity theft, fiscal fraud, and unauthorized access to sensitive information. also, spyware can decelerate down system performance, consume bandwidth, and affect device stability. To cover yourself from spyware, druggies should exercise good cybersecurity habits, including Keep your software up to date and use estimable antivirus and antimalware programs. Trust, avoid suspicious websites and downloads, and be careful when giving authorization to apps. Regularly surveying your device for spyware and other malware can also help descry and remove implicit pitfalls.
- Keylogger
Keylogger is a cunning app or gadget that surreptitiously logs every keystroke you make on your phone or computer. Sensitive information such as credit card details, passwords, emails, and messages are included in this. Keyloggers are routinely used by thieves to steal money, login credentials, and personal information.
There are mostly two kinds:
- Keyloggers for computer programs: These are cunning apps that install on your device covertly. They may originate from malicious websites, email attachments, or software bundles. Once inside, they stealthily input each key event you make and transmit the data to the attacker's server.
- Hardware keyloggers: These are actual hardware items that attach to your PC or slide in between the USB and your keyboard cord. Because they do not requisite installation, they are more difficult to locate. Rather, they quietly monitor your keystrokes while you type.
By collecting your personal information, breaking into your online accounts, or conducting fraud or identity theft, keyloggers can lead to serious issues. Update your software, use reputable antivirus software, stay away from dubious websites and downloads, and exercise caution when entering critical information on public computers to protect yourself. Additionally, to detect and eliminate keyloggers and other malicious software, routinely scan your devices.
2. Functionality of Keyloggers
When the selection key is pressed, a connection is created by closing the open circuit under each male and female key on the keyboard. Pressing this key causes the ROM keyboard to display the program's text, numbers, and graphics. Or see photos. The runtime system receives this information and stores it for a while before displaying it on the screen. Three resins come together to form the keys of the keyboard, and when there relies a secret, the relationship is created by slightly changing the circle when connecting to better words. Keyloggers reveal keystrokes and record the results. Some are exceptionally difficult because they go into the packaging process and capture images of what's happening on the screen. Human keyloggers can collect many types of information, both hardware and software. Keyloggers are computer applications that use the keyboard and device to operate gadgets to capture keystrokes. The term "hardware keylogger" describes the actual device that connects to the keyboard. It comes with a CPU that stores the generated keystrokes in its internal memory. No facts are marked or stored on the target device. To be fair, keyloggers are used as an authentication method. Keyloggers are viable to monitor behavioral biometrics when users log in using power gestures. Each puzzle has a unique key.
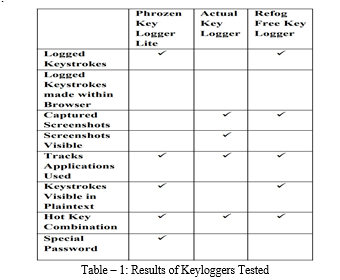
II. RELATED WORK
A. Keyloggers: Cybersecurity Dangers
Cyber ??attackers are still distributing malware to users and using this information to track victims, steal money, or do other malicious things. Infections caused by malware such as rootkits, spyware, keyloggers, and spyware. Teens can show off their talents online and make people laugh on Destiny. Cyber ??crimes have turned into crimes today. Despite advances in hardware and software infrastructure, cyber attacks continue. Keyloggers are nearly impossible to detect and block, making them easier to use than some other viruses. Arun Kumar, University of Petroleum and Energy Sciences, Dehradun; Akashdeep Bhardwaj, University of the South Pacific; Sam and Gounder note that keyloggers can upload screenshots of keystrokes online, preventing browsers from capturing them. Additionally, numeric keypads are encouraged to eliminate this discrimination.
B. Detecting and Preventing Keyloggers
A keylogger is a form of rootkit malware that counts keystrokes on the console and stores them in a message. This allows sensitive information, including passwords, PINs, usernames and passwords, to be recovered without impacting customers. Keyloggers speak and act in many ways, including online advertising, email newsletters, e-commerce and social media. Antivirus software is often used to detect and block keyloggers. But keyloggers are rare. This article bring forth precise information about keyloggers, their types, functions and principles. Finally, we can review existing research and examine some potential defenses.
C. Keylogger Technology Overview
Keylogger is a sort of rootkit malware that records keyboard keystrokes and stores them in a log file. This allows your personal information, comprise passwords and PINs, to be stolen and dispatch to attackers without requiring information from the customer. Keyloggers pose a threat to all personal and business activities, including email communications, online transactions, e-commerce, and information systems. I usually use antivirus software to perceive and block keyloggers. However, it cannot detect unknown keyloggers. This document provides a brief overview of keyloggers, their types, trends and methods. This article uses the BlackBerry case study as a real-world example. Finally, we can examine the current discovery process.
D. Keystroke Log: Is the password strong enough?
Users are advised to choose stronger passwords, especially for important accounts, and understand the techniques hackers use when launching phishing and social engineering attacks.
The widespread malware used in network attacks include viruses and worms. Keyloggers are designed for eavesdropping keystrokes on various devices. Although it is not given the same importance as other diseases, but considered dangerous due to the same risk. In this case, having a counter sign does not ensure security because keyloggers record every keystroke. This article will introduce the functionality and security measures of keylogging software.
III. OBJECTIVE
The best of the proposed gadget is to develop a complete crucial captive result appropriate for ethical monitoring functions, similar as maternal supervision of children's online conditioning or organizational oversight of hand genre get Central to this ideal is the perpetration of superior algorithms to successfully cover and document keystrokes entered on a laptop tool. This capability permits druggies to song and dissect stoner exertion while icing translucency and obligation. One critical detail of the proposed gadget is its steady storehouse gadget, which employs essential encryption ways to protect captured keystrokes from unauthorized get entry to. Through using strong encryption protocols, the machine guarantees the protection of touchy information and preserves the sequestration of recorded data. Likewise, the proposed system includes a dispatch assertion characteristic to ameliorate translucency and enable activate movement.
Druggies have the capability to confess dispatch announcements whilst certain word thresholds are met or unique key phrases are connected, making an allowance for visionary monitoring and reaction to implicit security pitfalls or policy breaches. Overall, the primary quit of the proposed machine is to present a reliable and secure way of taking pictures and storing keystrokes for ethical tracking purposes.
By perfecting translucency through dispatch bulletins and icing the confidentiality of recorded records, the device allows druggies to successfully control and alleviate pitfalls related to virtual relations even as esteeming sequestration and confidentiality businesses.
IV. SYSTEM REQUIREMENTS
A. Hardware Requirements
- Minimum 64 MB RAM
- 20 MB Free Disk Space.
B. Software Requirements
- Windows OS
- Visual Studio Code
- Python modules.
- pynput module
- smtplib
- pyautogui
- OpenCV
4. End User G-Mail.
V. METHODOLOGY
This article explores a way to manage spyware on your keyboard using a Python script that sends data to email, saves data to a log file, and encrypts files for added protection.
A. Understanding Spyware Monitoring
Spyware is malicious software that monitors and collects information from computers without the client consent. It can capture keystrokes, track browsing habits, and even type passwords. Keyboard monitored spyware works by infiltrating the user’s device with malicious software or phishing attacks. Once installed, the spyware is able to cleverly record all keystrokes, including sensitive information such as passwords, affinity card details and personal messages and then transfer this data to a hacker's email account for delivery use again. Monitoring your keyboard activity can lead to breaches of privacy, phishing, and hacking.
B. Python Script For Monitoring
Python, a versatile programming language, which helps in generating spyware surveillance scripts. Scripts can be created to capture keystrokes, record data, and send periodic reports via email. The main goal of spyware surveillance is to release data captured on remote servers controlled by hackers. By configuring python scripts to send encrypted log files as email attachments, cybercriminals can access sensitive information remotely without alerting the user This stealth technique allows hackers to steal data a it is valuable that no one will see.
C. Sending Data to Email and Saving in Log File
The Python script can be programmed to periodically ship the captured keystrokes to a specified electronic mail address. Additionally, the script can store the records in a log report on the laptop for future reference.
D. Time Stamp And Active Window Title Being Recorded
The python script records keystrokes and the title of the current window and the time of the event. This data helps define the user’s actions and actions by placing keystrokes in context.
* The program or application that is now in focus is reflected in the title of the active window. Timestamps help create an event timeline by giving chronological information about the keystrokes captured.
E. Using the Mouse to Take Screenshots
The Python script is configured to record a screenshot each time the user presses the right mouse button, adding an additional layer of data capture. The ability to visually monitor the user's actions and screen interactions is made possible by this capability.
* Screenshots improve the whole surveillance process by providing a visual depiction of the user's actions. Mouse clicks cause the screenshot to be taken, ensuring that pertinent information is gathered when it is needed.
F. Gathering Images from Webcams
The Python software also takes pictures from the user's camera in a more sophisticated spying method. This feature gives the data collection a human touch and makes it possible to identify and keep an eye on the individual.
* Webcam photos help with user verification and recognition by giving a clear view of the user's face. It is important to take privacy into consideration while using webcam capture to track keystrokes.
G. Email Data Transmission
The Python script is configured to email the gathered data—which includes keystrokes, window titles, timestamps, screenshots, and camera images—to a designated recipient. This guarantees remote access to the recorded data and real-time monitoring.
* Data transfer via email makes it possible to monitor activities remotely and with ease. The use of secure encryption and authentication mechanisms is important in order to avert unapproved access to the data.
Block Diagram

Conclusion
In summary, the described keylogger project provides a sophisticated solution for monitoring and recording user activities on computer systems. Leveraging Python and libraries like pynput, smtplib, pyautogui, and OpenCV, it records keystrokes comprehensively, including characters, spaces, and input, along with timestamps for tracking Exactly. Active window titles and search queries enrich monitoring data. Additionally, the keylogger is capable of capturing screenshots and user images during right-click events, integrating them seamlessly into email reports sent securely via smtplib. This tool provides discreet monitoring while providing valuable insights into user interactions. With features like keystroke logging, window tracking, search query logging, and media collection, it ensures in-depth monitoring. Upholding felony and moral suggestions stay critical at some point of development and implementation. Ultimately, this venture objectives to enhance virtual safety, empowering users to shield their facts.
References
[1] T. Holz, M. Engelberth and F. Freiling, \"Learning more about the underground economy: A case-study of keyloggers and dropzones\", Computer Security–ESORICS 2009: 14th European Symposium on Research in Computer Security, pp. 1-18, September 21-23, 2009. [2] B. K. Mohanta, M. K. Dehury, B. Al Sukhni and N. Mohapatra, \"Cyber physical system: Security challenges in internet of things system\", 2022 Sixth International Conference on I-SMAC (IoT in Social Mobile Analytics and Cloud) (I-SMAC), pp. 117-122. [3] M. Davarpanah Jazi, A.-M. Ciobotaru, E. Barati et al., \"An introduction to undetectable keyloggers with experimental testing\", International Journal of Computer Communications and Networks (IJCCN), vol. 4, no. 3, pp. 1-5, 2014. [4] B. Kumar and S. Roy, \"An empirical study on usability and security of e-commerce websites\", Research in Intelligent and Computing in Engineering: Select Proceedings of RICE 2020, pp. 735-746, 2021. [5] G. Savithri, B. K. Mohanta and M. K. Dehury, \"A brief overview on security challenges and protocols in internet of things application\", 2022 IEEE International IOT Electronics and Mechatronics Conference (IEMTRONICS), pp. 1-7, 2022. [6] A. Bhardwaj and S. Goundar, \"Keyloggers: silent cyber security weapons\", Network Security, vol. 2020, no. 2, pp. 14-19, 2020. [7] D. Damopoulos, G. Kambourakis and S. Gritzalis, \"From keyloggers to touchloggers: Take the rough with the smooth\", Computers & security, vol. 32, pp. 102-114, 2013. [8] B. Kumar, S. Roy, A. Sinha, V. Kumar et al., \"Invo-substitute: Threelayer encryption for enhanced e-commerce website security using substitution cipher and involution function\", Journal of Pharmaceutical Negative Results, pp. 1621-1640, 2023. [9] A. Dwivedi, K. C. Tripathi and M. Sharma, \"Advanced keylogger-a stealthy malware for computer monitoring\", Asian Journal for Convergence in Technology (AJCT), vol. 7, no. 1, pp. 137-140, 2021, ISSN 2350-1146. [10] R. Rahim, H. Nurdiyanto, A. Saleh A, D. Abdullah, D. Hartama and D. Napitupulu, \"Keylogger application to monitoring users’ activity with exact string-matching algorithm\", Journal of Physics: Conference Series, vol. 954, pp. 012008, 2018. [11] Y. A. Ahmed, M. A. Maarof, F. M. Hassan and M. M. Abshir, \"Survey of keylogger technologies\", International journal of computer science and telecommunications, vol. 5, no. 2, 2014. [12] N. Adhikary, R. Shrivastava, A. Kumar, S. K. Verma, M. Bag and V. Singh, \"Battering keyloggers and screen recording software by fabricating passwords\", International Journal of Computer Network and Information Security, vol. 4, no. 5, pp. 13, 2012. [13] M. Dadkhah and M. D. Jazi, \"A novel approach to deal with keyloggers\", Oriental Journal of Computer Science & Technology, vol. 7, no. 1, pp. 25-28, 2014. [14] E. Ladakis, L. Koromilas, G. Vasiliadis, M. Polychronakis and S. Ioannidis, \"You can type but you can’t hide: A stealthy gpu-based keylogger\", Proceedings of the 6th European Workshop on System Security (EuroSec), 2013. [15] S. Ortolani and B. Crispo, Noisykey: Tolerating keyloggers via keystrokes hiding, HotSec, 2012. [16] S. Ortolani, C. Giuffrida and B. Crispo, \"Bait your hook: a novel detection technique for keyloggers\", Recent Advances in Intrusion Detection: 13th International Symposium RAID 2010, pp. 198-217, September 15-17, 2010. [17] V. Prajapati, R. Kalsariya, A. Dubey, K. Mehta and M. Patil, \"Analysis of keyloggers in cybersecurity\", International Journal for Research in Applied Science Engineering Technology (IJRASET), vol. 8, no. 10, pp. 466-474, 2020. [18] S. Sivarajeshwaran, G. Ramya and G. Priya, \"Developing software based key logger and a method to protect from unknown key loggers\", International Journal of Innovative Science and Modern Engineering (IJISME), vol. 7, pp. 2319-6386, 2015. [19] K. Subramanyam, C. E. Frank and D. H. Galli, \"Keyloggers: The overlooked threat to computer security\", 1st Midstates Conference for Undergraduate Research in Computer Science and Mathematics, 2003. [20] B. Tschinkel, B. Esantsi, D. Iacovelli, P. Nagesar, R. Walz, V. Monaco, et al., Keylogger keystroke biometric system, Research Gate, 2017. [21] S. Yadav, A. Mahajan, M. Prasad and A. Kumar, \"Advanced keylogger for ethical hacking\", International Journal of Engineering Applied Sciences and Technology, vol. 5, pp. 634-638, 2020. [22] C. Wood and R. Raj, \"Keyloggers in cybersecurity education\" in Security and Management, Citeseer, pp. 293-299, 2010.
Copyright
Copyright © 2024 Reddyvari Venkateswara Reddy, Gattu Laxmi Priya, K Varshini, Mahankali Varun. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET59835
Publish Date : 2024-04-05
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

