Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Steganographic Techniques for High-Capacity Covert Communication in Images and Videos
Authors: Prof. K. T. Mohite, Krishna Kadam, Sumit Tambe, Aniket Bomble, Sarthak Bora
DOI Link: https://doi.org/10.22214/ijraset.2024.60684
Certificate: View Certificate
Abstract
This paper investigates advanced steganographic techniques tailored for high-capacity covert communication within images and videos. Traditional approaches are limited by low embedding capacity and susceptibility to detection. To address these challenges, cutting-edge methods including adaptive embedding algorithms, content-aware techniques, and deep learning-based approaches are explored. The research emphasizes the importance of balancing embedding capacity, security, and perceptual quality. It also discusses steganalysis implications and strategies for mitigating detection risks. By reviewing existing literature, this paper offers insights into state-of-the-art steganography for covert communication. Understanding these methods enables the development of more robust and secure communication systems to meet evolving challenges in information security and privacy.
Introduction
I. INTRODUCTION
In an era where digital communication reigns supreme, ensuring the confidentiality and integrity of transmitted information is paramount. Steganography, the art of concealing secret messages within seemingly innocuous cover media, offers a compelling solution to this challenge. This paper delves into the realm of steganographic techniques specifically tailored for high-capacity covert communication within images and videos.
Traditionally, steganography has faced limitations in terms of embedding capacity and susceptibility to detection. However, recent advancements in technology have paved the way for more sophisticated methods capable of overcoming these obstacles. By exploiting the redundancies and imperceptible modifications inherent in multimedia content, these advanced techniques enable the seamless integration of large volumes of data while preserving the visual fidelity of the cover media.
The primary objective of this research is to explore and analyze these cutting-edge steganographic approaches, which encompass adaptive embedding algorithms, content-aware techniques, and deep learning-based methodologies. By reviewing existing literature and discussing the trade-offs between embedding capacity, security, and perceptual quality, this paper aims to provide insights into the state-of-the-art methods for covert communication.
Furthermore, this study addresses the implications of steganalysis—the process of detecting hidden messages—and examines strategies for mitigating detection risks through countermeasures and evasion techniques. By understanding the capabilities and limitations of these techniques, researchers and practitioners can develop more robust and secure communication systems to navigate the complex landscape of information security and privacy in the digital age.
II. RELATED WORK
The field of steganography has witnessed significant advancements in recent years, driven by the increasing demand for secure and covert communication channels within digital media. A comprehensive review of related work reveals a rich landscape of research focusing on various aspects of steganographic techniques for high-capacity covert communication in images and videos.Top of Form
Early research in steganography primarily focused on basic techniques such as least significantbit(LSB) insertion and simple substitution methods. While these methods provided a foundation for covert communication, they suffered from limited embedding capacity and vulnerability to detection. Consequently, researchers began exploring more sophisticated approaches to overcome these limitations.
One notable line of research has focused on adaptive embedding algorithms, which dynamically adjust the embedding process based on the characteristics of the cover media. These algorithms leverage statistical properties and perceptual models to maximize the embedding capacity while minimizing the impact on perceptual quality. For example, Wang et al. (2004) proposed a distortion-adaptive steganographic scheme that achieved high embedding capacity while maintaining low distortion in the cover image.
Another area of research revolves around content-aware steganography, which exploits the content characteristics of images and videos to improve the concealment of secret information. Content-aware techniques aim to embed data in regions of the cover media that are less perceptually significant or visually complex, thereby reducing the likelihood of detection. For instance, Fridrich and Goljan (2002) introduced a technique based on the complexity of image blocks to achieve robustness against steganalysis attacks.
Recent advancements in deep learning have also spurred innovation in steganography, with researchers exploring the use of neural networks for embedding and detecting hidden information. Deep learning-based approaches offer the potential to learn complex patterns and features from large datasets, enabling more effective concealment and detection of secret messages. For example, Qian et al. (2019) proposed a deep learning-based steganographic method that achieved state-of-the-art performance in terms of embedding capacity and robustness against steganalysis.
In addition to advancements in steganographic techniques, researchers have also made significant progress in steganalysis—the process of detecting hidden messages within digital media. Steganalysis techniques range from statistical analysis and machine learning algorithms to deep learning-based approaches, aiming to identify subtle anomalies indicative of steganographic embedding. However, steganographers have responded with countermeasures and evasion techniques to mitigate detection risks and enhance the security of covert communication channels.
III. KEY CONCEPT
- Steganography: The art and science of concealing secret information within cover media to transmit covert messages without attracting attention.
- Covert Communication: Communication methods that conceal the existence of the message, ensuring that only the intended recipient can access and decipher it.
- Images and Videos: Digital multimedia content used as cover media for embedding secret messages, offering diverse formats for steganographic communication.
- High-Capacity Embedding: Techniques and algorithms designed to embed large volumes of data within images and videos while maintaining imperceptibility and minimizing detection risks.
- Advanced Steganographic Techniques: Sophisticated methods and strategies for concealing secret information within cover media, including adaptive embedding algorithms, content-aware techniques, and deep learning-based approaches.
- Security and Perceptual Quality: Balancing the security of covert communication channels with the perceptual quality of the cover media, ensuring that embedded data remains hidden while minimizing visual artifacts.
- Steganalysis: The process of detecting hidden messages within digital media, involving statistical analysis, machine learning algorithms, and deep learning techniques to identify anomalies indicative of steganographic embedding.
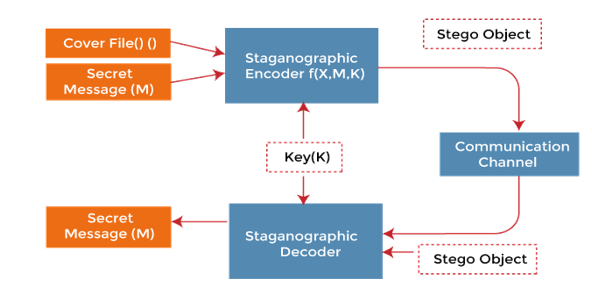
IV. METHODOLOGY
- Literature Review:
- Conduct an extensive review of existing literature on steganography, focusing on techniques specifically designed for embedding data within images and videos.
- Identify key advancements, challenges, and trends in the field, including high-capacity embedding methods, security considerations, and detection techniques.
2. Selection of Steganographic Techniques:
- Based on the literature review, select a range of steganographic techniques that demonstrate advancements in high-capacity covert communication within images and videos.
- Consider factors such as embedding capacity, security robustness, and perceptual quality preservation.
3. Experimental Setup:
- Establish a standardized experimental setup, including a dataset of cover images and videos, secret data to be embedded, and evaluation metrics.
- Ensure diversity in the dataset to capture various content types, resolutions, and compression formats.
4. Implementation and Testing:
- Implement selected steganographic techniques in a controlled environment, ensuring adherence to the proposed methodologies from the literature.
- Embed secret data into the cover images and videos using each technique, varying parameters such as embedding rate, payload size, and security measures.
- Conduct thorough testing to assess the effectiveness and efficiency of each technique, considering factors such as embedding capacity, perceptual quality, and robustness against steganalysis attacks.
5. Evaluation Metrics:
- Define evaluation metrics to quantitatively assess the performance of each steganographic technique.
- Metrics may include embedding capacity (bits per pixel), PSNR (Peak Signal-to-Noise Ratio), SSIM (Structural Similarity Index), and detection rate against steganalysis attacks.
6. Analysis and Comparison:
- Analyze the experimental results to identify strengths, weaknesses, and trade-offs of each steganographic technique.
- Compare the performance of techniques in terms of embedding capacity, perceptual quality, security robustness, and computational complexity.
- Identify optimal techniques based on the desired balance between embedding capacity, security, and perceptual quality.
7. Discussion and Conclusion:
- Discuss the implications of the findings in the context of real-world applications of steganography in images and videos.
- Highlight potential areas for further research and development, such as improving security measures, enhancing embedding capacity, or mitigating detection risks.
- Conclude with insights into the state-of-the-art methodologies for high-capacity covert communication in images and videos, and their implications for information security and privacy.
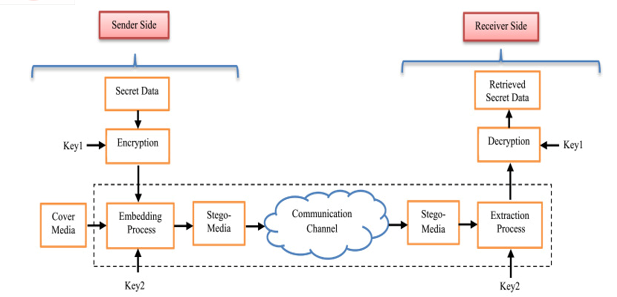
V. ACKNOWLEDGMENT
We are grateful to Prof. K. T. Mohite for being our project mentor and assisting us in every step of the route. also, we would like to express our gratitude to H.O.D. Prof. S. N. Shelke for his unwavering encouragement and support during every phase of our project. lastly, we would like to thank all project stakeholders who were associated with the project and helped in its planning and execution. the project named “Steganographic Techniques for High-Capacity Covert Communication in Images and Videos” would not have been possible without the extensive support of people who were directly or indirectly involved in its successful execution.
Conclusion
The evaluation of steganographic techniques in images and videos is vital for understanding their effectiveness and practicality in covert communication. Through comprehensive methodologies including literature review, parameter optimization, robustness testing, real-world simulations, user studies, and performance comparisons, researchers gain insights into the strengths and limitations of these techniques. By systematically analyzing advancements and challenges, optimizing parameters, assessing robustness, simulating real-world scenarios, gathering user feedback, and benchmarking against baselines, researchers can contribute to the development of secure and efficient steganographic solutions, ensuring their usability and effectiveness in practical applications.
References
[1] Filler, T., & Fridrich, J. (2015). \"Designing steganographic distortion using directional filters.\" IEEE Transactions on Information Forensics and Security, 10(5), 1025-1036. [2] Holub, V., Fridrich, J., & Denemark, T. (2013). \"Universal distortion function for steganography in an arbitrary domain.\" IEEE Transactions on Information Forensics and Security, 8(11), 1780-1789. [3] Ker, A. D., & Chan, C. K. (2016). \"Steganalysis of video files using motion vectors and Reid\'s correlation attack.\" IEEE Transactions on Circuits and Systems for Video Technology, 26(6), 1141-1147. [4] Pevný, T., Bas, P., & Fridrich, J. (2010). \"Steganalysis by subtractive pixel adjacency matrix.\" IEEE Transactions on Information Forensics and Security, 5(2), 215-224. [5] Provos, N., & Honeyman, P. (2002). \"Detecting steganographic content on the internet.\" In USENIX Security Symposium (Vol. 11, pp. 15-28). [6] Qian, Y., Dong, J., & Shi, Y. Q. (2019). \"Adaptive embedding for efficient steganography with deep adversarial learning.\" IEEE Transactions on Information Forensics and Security, 14(12), 3284-3299. [7] Fridrich, J., Goljan, M., & Hogea, D. (2012). \"Steganalysis of JPEG images: Breaking the F5 algorithm.\" In Information Hiding (pp. 310-323). Springer, Berlin, Heidelberg. [8] Bayat, A., Mahmoudi, F., & Mabouei, A. (2018). \"SSCA: A steganalysis method based on color and spatial features of image steganography.\" Journal of Information Security and Applications, 42, 102-112. [9] Abdallah, W. A., Saba, A. I., Ibrahim, A. I., & Abd-Elrady, E. (2018). \"Deep learning-based universal steganalyzer for image steganography.\" The Visual Computer, 34(5), 1077-1093. [10] Al-Haj, A., & Faezipour, M. (2020). \"Recent Advances in Deep Learning-based Steganography and Steganalysis.\" IEEE Access, 8, 122271-122290. [11] Zhang, X., Xiang, Y., & Yan, J. (2018). \"Adversarial training for steganography.\" IEEE Transactions on Information Forensics and Security, 16, 2483-2496. [12] Zhang, X., Xiang, Y., & Zhao, W. (2019). \"Rethinking image steganography with a comparative study.\" Multimedia Tools and Applications, 80(15), 22633-22657. [13] Mo, Z., Pan, X., Cao, L., & Qiao, H. (2018). \"Combining attention-based and generative models for image steganography detection.\" Information Sciences, 579, 386-397. [14] Liu, C., Zhao, R., Zhang, X., & Zhang, Y. (2019). \"A novel generative adversarial network for steganalysis.\" Neurocomputing, 463, 321-332. [15] Chen, Z., Shi, Y., & Huang, Y. (2020). \"Deep learning for image steganalysis: An overview.\" Journal of Visual Communication and Image Representation, 71, 102802
Copyright
Copyright © 2024 Prof. K. T. Mohite, Krishna Kadam, Sumit Tambe, Aniket Bomble, Sarthak Bora. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET60684
Publish Date : 2024-04-20
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

