Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Terrorist Activities Detection via Social Media Using Machine Learning
Authors: Prof. Hiranwale S. B., Gade Priti, Shinare Sakshi, Jadhav Mrunal, Todmal Rutuja
DOI Link: https://doi.org/10.22214/ijraset.2024.60248
Certificate: View Certificate
Abstract
Perhaps the richest source of human generated text input is social media. Internet users\' opinions, feedback, and criticisms represent their attitudes and feelings towards specific topics and concerns. The sheer volume of such information makes reading it difficult for any group of people. As a result, social media has become a major instrument for propagating their views and influencing or enticing people to join their terrorist actions in general. Social media is the most frequent and straightforward approach to contact a large number of individuals in a short period of time. This research focuses on the construction of a system that can detect terrorism-supporting tweets automatically through real-time analytics using the Apache Spark machine learning framework. The proposed approach is completely reliant on training data and attempts to enhance accuracy.
Introduction
I. INTRODUCTION
In today’s world, social media is arguably a very important factor in both an individual's life and the operation of a them who use the internet. On average, each person has about 5.54 social media accounts, contributing to a total of approximately government. According to statistics, there are roughly 7.72 billion people on the planet, and there are undoubtedly billions of 3.397 billion active social media accounts globally.
It has been discussed how social media affects society, its citizens, and the data it produces as a result. Without a hint of social media's role in it, the development of the 21st century is hardly predictable. Saying that social media is omnipresent in all areas of life—including education, health care, business, disaster management, politics, and the travel and tourist sector—wouldn't be overstating the case. Of ocourse, the use of social media for entertainment and media sharing goes without saying. Despite all the ease that osocial media has to offer, it also has a negative side. The flip side, improper usage of social media, also needs to be taken into consideration. On the one hand, this may appear to be bridging a communication gap and accelerating the dissemination of news among people; on the other hand, many people are abusing it severely. Misuse on a par with acts of genocide, homicides, bombings, conspiracies, etc.
While 76% of UK terrorists use the internet to study and plan their attacks. ASG, a Salafi Jihadist terrorist organization, kidnapped Australian Warren Rodwell in 2013 and held him captive for 472 days. The group utilized YouTube and Facebook to upload ransom videos and provide evidence of life. A thorough literature review indicated that the Islamic State (ISIS) made considerable use of social media to promote their ideology and recruit members and followers. The use of proactive social media methods by three extremist-related groups operating in Asia Pacific has been investigated: Abu Sayyaf in the Philippines, Jamaat-e-Islami in Bangladesh, and the Uyghurs in China. This paper illustrates how these groups provide multiple options to maximize their reach, influence, and effect through the use of social media. Another example of social media misappropriation has been the examination of who displays the social media activity and online presence of media mujahedeen who are thought to be followers of jihadist groups and spread propaganda content online.
II. LITERATURE SURVEY
A model to predict information flow size and survival was developed by [1], with the help of data fetched from one of the popular social networking website Social media. The size of information flow and its survival were analyzed using the zero-truncated negative binomial (ZTNB) regression method for the former and the Cox regression technique for the latter. From a dataset comprising 427,330 entries from social media, researchers uncovered a groundbreaking discovery: sentiment analysis of tweets emerged as a significant predictor for both the magnitude and longevity of information dissemination. Moreover, the presence of URLs and the timing between retweets and hashtags exhibited notable correlations.
In a parallel study, [2] delved into the examination of publicly available communication data sourced from social media platforms to unveil the intricate dynamics of conflict within and between communities, particularly following tragic events. They asserted that the social media data collected following the murder of Fusilier Lee Rigby robustly aligns with the three phases of conflict dynamics outlined by Collins. Furthermore, they scrutinized two pivotal assertions: first, the interactive nature of the conflict, and second, how the granular insights provided by digital data shed light on the intricate web of relationships that emerge and evolve throughout such disputes.
Another interesting study of this event was reported by [3], who worked this case study as a part of computational criminology. They demonstrated the temporal fluctuations in cyberhate, which align with concepts from various criminological theories, such as the diffusion, duration, escalation, and de-escalation of crime.
[4] conducted an analysis of social reactions to the murder of Lee Rigby, utilizing data collected through systematic monitoring of social media platforms. They explored various online behaviors that manifest tangible effects offline.
Following the tragic events of the annual Boston Marathon on April 15, 2013, where two homemade pressure cooker bombs detonated near the race's finish line, resulting in the deaths of three individuals and injuring several hundred others, including around sixteen amputations. [5] analyzed social media posts uploaded immediately after the bombings. They identified recurring keywords that preceded official public safety and media reports, indicating the rapid dissemination of information. Individuals in close proximity to the explosions shared messages on social media within minutes of the incident. This facilitated the identification of event locations and details, highlighting the role of social media in the proactive identification and portrayal of emergency events beforehand.
[6] conducted a study on the Boston Marathon tragedy, analyzing the impact of tweet features on the dissemination of two types of messages: real and rumor-related. Utilizing negative binomial analysis, they found that tweet characteristics such as hashtag usage, number of followers, and reaction time influenced message diffusion during the bombing. Remarkably, there was a positive correlation between the number of followers and the spread of messages. Conversely, the relationship between tweet reaction time and message dispersion was found to be negative. Surprisingly, messages without hashtags were found to spread more effectively than those with hashtags.
\Another study of the Boston Marathon attack was conducted by [7], who collected over 18 million tweets from 15,509 Twitter users in Paris on November 13, 2015. They assessed the levels of anxiety, anger, and sadness expressed by users in the aftermath of the attacks. The authors proposed the use of computational focus groups and a completely novel investigation framework to evaluate a social media stream which archives user location and history. The study yielded findings that are unlikely to emerge through alternative media or methodologies.
In this study [8], the Helpers were identified as the primary Convergence Behavior Archetypes, consistently retweeting throughout the crisis. Conversely, the Mourners had the most significant impact through their extensive retweeting activity. These findings suggest that users who generate emotional content are more inclined to retweet extensively. This suggests that users who generate emotional content are more likely to engage in retweeting activities. Additionally, the Detectives disseminated information into other communities the most. The authors not only expanded our understanding of how users converge on social media during crisis situations but also provided valuable insights for crisis managers into user behavior. Knowing which type of behavior on social network has a effective impact, might help in controlling the amount of data that is generated during a crisis situation.
Social media became an essential channel of communication between the emergency responders, government, and the public. This highly facilitated the emergency management of the crises. [9] conducted a thorough analysis aimed at comprehensively understanding trends in crisis communication facilitated by social media. Social media Mate was used to collect the data generated during tweets and also to analyze it. It also highlights the primary hashtags emerging from the crowd, as well as specific social media accounts belonging to individuals, NGOs, and emergency responders. A comprehensive examination was conducted on a total of 67,849 tweets. Researchers identified four main categories of hashtags: those related to social support, terror attacks, geographical locations, and organizations.
The same terrorist attack was also studied by [10]. They analyzed the volume of tweets, the geographical distribution of tweets, and the demographics of users involved. Additionally, they explored whether users in developing countries showed a propensity to tweet, retweet, or reply during terrorist events. Furthermore, they introduced new metrics to assess the reach and impression of tweets during such incidents. Their findings indicated that users from developing countries tend to tweet more, especially during the initial and critical periods of a terrorist incident. Additionally, a significant number of tweets originated from Kenya, with 23% from women and 73% from men. Moreover, original posts received the highest number of tweets, followed by replies and retweets.
III. PROPOSED METHODOLOGY
The system attempted to associate some semantics with all of the real-time data obtained from Social media. The system intended to examine the data to see if there were any patterns. We wanted to know which terms and hashtags were trending the most, as well as who was at the centre of the network graphs. The system sought to know how many unique users the data had and how popular various metrics were for different crises. Another goal of our suggested approach is to determine the crisis orientation of Social media users. To determine who focuses on which behaviour. The system will examine the key parameters like as anxiety, rage, and despair over post attacks. Because a large amount of data is created every day, a system that can generate daily analysis is required. The system desired to be able to view tweets about terrorist acts as they occurred. There was a need to maintain track of tweets relating to terrorist attacks.
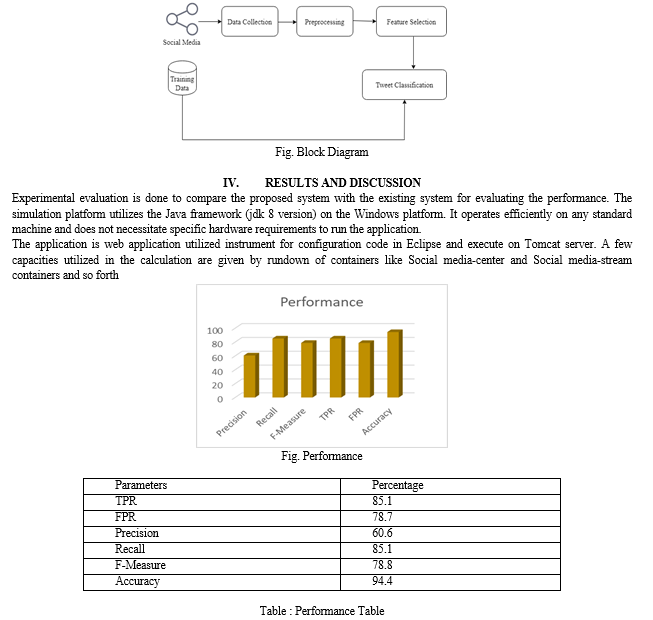
Conclusion
With the increased use of social media, the current work focused mainly on use of social media as a tool for terrorism. India which is known to be one of the wide countries in the world with having more than 65% of its youth below age-group of 35; social media plays vital role in the life of this young youth. The proposed systems will try to analyze a common platform to manifest the progress of counter-terrorism strategies in this digital world; There is scope for verifying the changed sentiments of the user before and after an attack. Given the studies reported and analyses conducted thus far, it is imperative to escalate the scale of data analysis to a larger extent and, importantly, on a regular basis. This approach should be implemented not only to identify acts of terrorism on social media but also as a safety tool for preventive measures and post-attack examination. The study can also include a machine learning approach to train a system to automatically classify the tweets and do a sentiment analysis of the tweets/comments.
References
[1] M. Mirbabaie, D. Bunker, A. Deubel and S. Stieglitz, Examining Conver-genceBehaviour During Crisis Situations in Social Media-A Case Study on the Manchester Bombing 2017, In International Working Conference on Transfer and Diffusion of IT, Springer, Cham. pp. 6075, June 2018. [2] M. L. Williams and P. Burnap, Cyberhate on social media in the aftermath of Woolwich: A case study in computational criminology and big data, British Journal of Criminology, vol. 56(2), pp. 211238, 2015 [3] Roberts, C., Innes, M., Preece, A., and Rogers, D. (2017). After Woolwich: Analyzing open source communications to understand the interactive and multi-polar dynamics of the arc of conflict. The British Journal of Criminology, 58(2), 434-454. [4] Martin Innes, Colin Roberts, AlunPreece and David Rogers (2018) Ten Rs of Social Reaction: Using Social Media to Analyse the Post-Event Impacts of the Murder of Lee Rigby, Terrorism and Political Violence, 30:3, 454-474, DOI: 10.1080/09546553.2016.1180289 [5] C. A. Cassa, R. Chunara, K. Mandl, and J. S. Brownstein, Social media as a sentinel in emergency situations: lessons from the Boston marathon explosions, PLoS currents, vol. 5, 2013 [6] J. Lee, M. Agrawal and H. R. Rao, Message diffusion through social network service: The case of rumor and non- rumor related tweets during Boston bombing 2013, Information Systems Frontiers, vol. 17(5), pp. 9971005, 2015 [7] P. Burnap, M. L. Williams, L. Sloan, O. Rana, W. Housley, A. Edwards and A. Voss, Tweeting the terror: modelling the social media reaction to the Woolwich terrorist attack, Social Network Analysis and Mining, vol. 4(1):206, June 2014. [8] Y. R. Lin, D. Margolin, and X. Wen, Tracking and analyzing individual distress following terrorist attacks using social media streams, Risk analysis, vol. 37(8), pp. 15801605, 2017. [9] T. Simon, A. Goldberg, L. Aharonson-Daniel, D. Leykin, and B. Adini, Social media in the crossfire the use of social media in the Westgate Mall terror attack in Kenya, PloS one, vol. 9(8), pp. e104136, 2014. [10] F. R. Ishengoma, Online social networks and terrorism 2.0 in developing countries, arXiv preprint arXiv, 1410.0531. 2014
Copyright
Copyright © 2024 Prof. Hiranwale S. B., Gade Priti, Shinare Sakshi, Jadhav Mrunal, Todmal Rutuja. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET60248
Publish Date : 2024-04-13
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

