Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Unusual Human Activity Recognition in ATM’S
Authors: Dr Jagadeesha R, Harish A N, Pooja Shree R
DOI Link: https://doi.org/10.22214/ijraset.2024.61792
Certificate: View Certificate
Abstract
This paper addresses the imperative need to enhance Automated Teller Machine (ATM) safety and security through the integration of deep learning and OpenCV. Leveraging Convolutional Neural Networks (CNNs) for feature extraction and Siamese Networks for anomaly detection, our approach aims to fortify ATM systems against threats like skimming and unauthorized access. Realtime image processing with OpenCV facilitates efficient preprocessing. The study critically examines existing methodologies, highlighting vulnerabilities to adversarial attacks and environmental variations. Through rigorous evaluation and adversarial testing, this research of ATM security systems, fostering a more secure financial landscape.
Introduction
I. INTRODUCTION
ATM has established to be an essential machine developed system that has enabled human beings to withdraw their cash easily, 24x7. Since ATMs are handy reservoirs of liquid cash, they are constantly focused via thieves and frauds to borrow the cash saved in ATM. This device is a proactive measure that ensures the protection of the people and prevents physical attacks by predicting the vulnerability of an ATM. With the increasing reliance on Automated Teller Machines (ATMs) for economic transactions, making sure the safety and safety of those systems has turn to been a paramount concern. The ability risks associated with ATM- associated abnormalities including multiple person detection, weapon detection and identification theft, necessitate the improvement of strong security measures. This paper endeavours to address these challenges by harnessing the power of deep learning and OpenCV, aiming to fortify ATM infrastructure against evolving threats. As technological advancements continue to shape the landscape of financial services, our focus on leveraging Convolutional Neural Networks (CNNs) for feature extractions and Siamese Networks for anomaly detection promises a sophisticated approach to augmenting security protocols. This introduction sets the stage for a comprehensive exploration of existing literature, methodologies, with the ultimate goal of contributing to the improvement of resilient and adaptive security systems for ATMs in an era of escalating cyber threats.
A. Overview of Image Processing
The fundamental definition of image processing defines that processing of digital images by removing noise, any type of irregularities that can have crept into the image, both through its formation, transformation, storage and others. In arithmetic analysis, it can be(image) shown as a 2-D functions f (x, y), in which x, y are spatial coordinates and amplitude off at any factor (x, y) are referred as the of values f at that factor. In grey scale images, it’s also called the grey level. When x, y and these intensity values are countable, discrete quantities, it is stated to be digital image. Its miles are crucial that a dip (digital image) consists of estimated range factors, which has coordinates and a value. The ones elements are referred to as picture each element or pixels and are the small part of an image. Numerous techniques were superior over the past a long time. Maximum of those strategies are evolved for reinforcing images received at various photography equipment’s. Image process has become famous due to smooth availability of effective personal computers, algorithms, memory devices, software, etc. Moreover, over the years, their usage has also become very simple and can be of use, not just to researchers and scientists, but to laymen as well, who can also use it in the right way to realize their potential better.
Image processes is utilized in diverse utility which includes
- Remote Sensor
- Medical image
- Non-destructive Evaluated
- Forensic Study
- Textile industries
- Material Sciences
- Film Industries
- Graphic design
- Printing Industries
B. Digital Image Processing
DIP commonly determines the processing of a 2-D image in useful resource of a virtual pc, it shows dip of 2-D data. A virtual image is array of real numbers represented via a finite wide type of data. The principle gain of virtual Image Processing techniques is its versatility, repeatability and upkeep of original information precision
The steps involved:
- Image Pre-processing
- Image Enhancements
- Image Segmentations
- Feature Extractions
- Image Classifications
C. Image Pre-Processing
n this, the image statistics recorded through the usage of sensor in a digicam associated with geometry or contracts value of the pixels may not be very unique, as numerous noises may interfere with these bit values. Those mistakes are related using accurate mathematical models can be both particular or statistical model. Image enhancements are the modification of images via converting the pixel values to enhance its visual effect. Image enhancement involve a group of strategies to Enhance the seen appearance of image each to machines in addition to humans. Every so often, images acquired from satellites and digital camera lacks in comparison and brightness, because of restriction in imaging sub-systems and Heavy Light conditions while capturing the image. Images also have one-of- a-type forms of noises in image. An image enhancement, the purpose is to obtain the positive image functions for the following analysis stages or display. These may involve, contrast or edge enhancement, pseudospoofing, noise filters, sharpening and focusing. Image enhancement is done mainly using feature extraction, analysis of image and displaying. The enhancement system itself the extraction of information of data. It really ensures a unique image characteristic. These algorithms are mainly interactive and applications dependent. Group of strategies to improve the visible look of an image- each to machines in addition to humans. Every so often, images acquired from satellites and digital cameras lack in comparison and brightness because due to the limitations of imaging sub-systems and illumination conditions while capturing the image. Images may have one-of-a-kind varieties of noise. In image enhancement, the aim is to accentuate positive image features for the following analysis stages or display. These may involve contrast or edge enhancement, pseudospoofing, noise filtering, sharpening and magnifying. Image enhancement is useful in feature extraction, image analysis and display. The enhancement system itself does not increase the inherent information in the data. It really emphasizes sure unique image characteristics. These algorithms are typically interactive and application dependent.
Some of these are:
- Noise Filtering
- Contrast Stretching
- Histogram Modification
Considering that we used noise filtering in our paper, we would describe it briefly as technique to clear out needless data from the image. Used to take away various forms of noise from the image. Mostly, one of the features is interacting. numerous filters used, like low pass filters, high pass filters, mean and median is also available. Here, we’ve used the median filter to effectively filter out noise.
D. Image Segmentation
It is the process of partitioning the image into many segments or regions based on certain characteristics, which includes colour, intensity, texture, or other visual properties. The purpose is to simplify the representation an image, making it easier and understand. Segmentation is used in many applications including medical imaging, autonomous driving, and satellite image analysis
E. Image Classification
It is used for naming pixel or organizing pixels primarily based on grey value. It is commonly used methods to extract information. In classification, lot of factors are used for each pixel, In RSA (remote sensing area), the process assumes that an image of geographic vicinity is specified and is gathered in multiple areas of the (EM waves) electromagnetic spectrum also registered. The extracted information strategies depend on study of the spectral reference property of the photograph or image and algorithms are specialized and designed to carry out numerous kinds of spectral analysis.
The method of multiple categorizing can be carried out the usage of any of the two techniques- supervised or unsupervised. In the first classification that is supervised, the specification of the related parameters also accompanies the image for ‘learning’ reason. These are usually referred to as the training sets because of the spectral are used feature of the recognised and for training the algorithm. The various parameters are calculated in every training set. Each pixel, both inside and outside those training sets is checked. They are assigned to the class having best probability in a part. Therefore, in unsupervised categorization, the classification of the class kinds should specify as lesson inside a scene which are not usually called priori. Due to the fact floor truth is missing or floor capabilities inside the scene aren’t nicely determined. The supercomputer is needed to collect the pixel data that are of different spectral classes to statistically determined. The assessment we’ve got used is majorly supervises, which commonly results in a high accuracy rate. Evaluated and assigned to a class of which it has the best probability of being a member. In an unsupervised classification, the identities of the class kinds should be specific as lessons inside a scene which are not usually called priori due to the fact floor truth is missing or floor capabilities inside the scene aren’t nicely defined. The computer is needed to group pixel data into different spectral classes according to some statistically determined criteria. The assessment we’ve got used is majorly supervises, which commonly results in a high accuracy rate.
F. Motivation
Existing research, at the type of anomaly detection from images uses supervised learning and deep learning methods Used a deep learning using anomaly detection from photographic images. Furthermore, there may be some overall performance degradation because of bad parameter and layer choice in the neural network model. In the suggested CNN model for classifying anomalies within the images, we also use a revised number of layers and parameter settings. Furthermore, we ran experiments with diverse CNN model variants and in comparison, the findings to the baseline studies.
II. LITERATURE REVIEW
In this paper [1] Proposed algorithm only uses close morphological operation with disk like structuring element in the preprocessing steps to cope up with low resolution video. It further uses rolling average background subtraction technique to detect foreground object from dynamic background in a scene. Our proposed algorithm is able to recognize the occurrence of uncommon events such as overcrowding or fight in the low-resolution video simply by using statistical property, standard deviation of moving objects
In this paper[2], We are proposing an Enhanced ATM security system by proposing a system to detect unusual event detection even in the low- resolution videos using ARM 7 LPC 2148. The low-resolution camera fitted inside ATM can be used. We are using the inbuilt web camera of the PC or Laptop in designing of the prototype. Usually, the laptop inbuilt web camera resolution is low. Hence, we use the same. By using discussed algorithm, we design a system to detect the unusual activity. Whenever an Unusual event gets detected in ATM then buzzer will be on and also Alert SMS triggering happens from the GSM module to which ARM 7 sends the appropriate commands.
In this paper [3], The system is implemented on the credit card size Raspberry Pi board with extended capability of open-source Computer Vision (Open CV) software which is used for Image processing operation. High level security mechanism is provided by the consecutive actions such as initially system captures the human face and check whether the human face is detected properly or not. If the face is not detected properly, it warns the user to adjust him/her properly to detect the face. Still the face is not detected properly the system will lock the door of the ATM cabin for security purpose. As soon as the door is lock, the system will automatic generates 3-digit OTP code.
The OTP code will be sent to the watchman’s registered mobile number through SMS using GSM module which is connected with the raspberry Pi. Watchman will enter the generated OTP through keypad which is interfaced with the Pi Board. The OTP will be verified and if it is correct then door will be unlocked otherwise it will remain lock.
This paper [4] This system is designed for the detection of abnormal activities, as the people should take possible actions for the prevention of dangerous event.
The abnormal crowd detection is one of the abnormal activities of this system. Here, input will be a video and output by system would be the classification of abnormal activity/object. This object can be a bag or a parcel with specifications of dimensions. For classification of objects support vector machine is used for accurate results.
The proposed method in [5]: Siamese Networks for anomaly detection, OpenCV for preprocessing Thus, the security of the transaction is improved to a greater extent. Sensitivity to environmental changes, false positives with non-malicious anomalies.
III. METHODOLOGY
The methodology of this paper is a complicated approach of enhance Automated Teller Machine (ATM) safety and security. It begins with an in-depth literature review to grasp existing methodologies and challenges. The system integrates deep learning techniques, employing Convolutional Neural Networks (CNNs) for extraction and Siamese Networks for anomaly detection. Real-time image processing using OpenCV ensures efficient preprocessing of surveillance data. Training the system in a complex dataset facilitates robustness, and adversarial testing is conducted to assess resilience against potential attacks attac. Methodology emphasizes adaptability and proactiveness, aiming to address not only known threats but also emerging risks. Rigorous experimentation and performance evaluations validate system, contributing to the advancement of ATM security in the ever- evolving landscape of cybersecurity effectiveness of the proposed system, contributing to the advancement of ATM security in the ever-evolving landscape of cybersecurity.
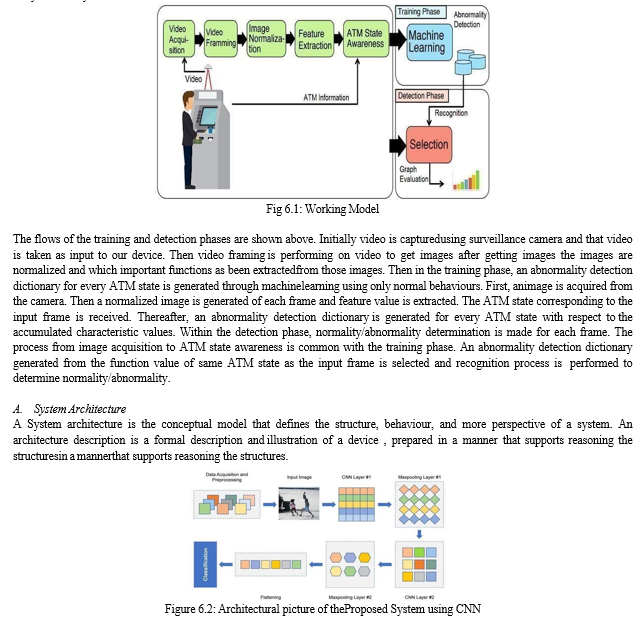 System using CNN The figure 6.2 indicates the system architecture for the proposed method. Here we are able to see that the anomaly image input is fed into the anomaly detection system, in which it is pre-processed, then features are extracted. Then the extracted features are fed to SoftMax classifier that is the last part of CNN. The input image is pre-processed and converted to grey scale image to find Threshold value based on input image. Based on Threshold value further image sharpening is done, then further process is carried out. The system which is being used currently performs the task of detecting the type anomaly. The input image is fed into system to find out edges and after sharpening the edges, features are been extracted and then fed into classifiers which can be trained according to the available dataset to detect the anomaly.
System using CNN The figure 6.2 indicates the system architecture for the proposed method. Here we are able to see that the anomaly image input is fed into the anomaly detection system, in which it is pre-processed, then features are extracted. Then the extracted features are fed to SoftMax classifier that is the last part of CNN. The input image is pre-processed and converted to grey scale image to find Threshold value based on input image. Based on Threshold value further image sharpening is done, then further process is carried out. The system which is being used currently performs the task of detecting the type anomaly. The input image is fed into system to find out edges and after sharpening the edges, features are been extracted and then fed into classifiers which can be trained according to the available dataset to detect the anomaly.
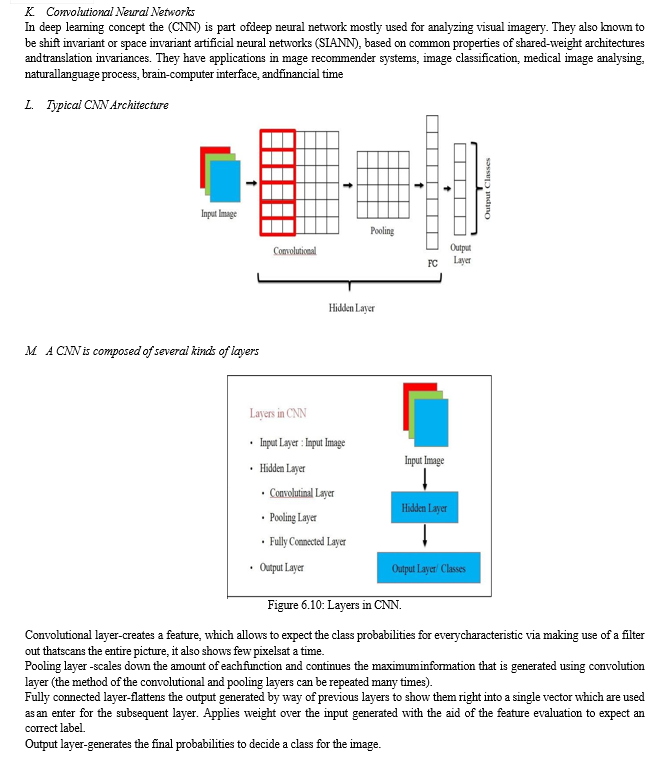
The proposed system has the following steps for detection of anomaly
- RGB to grey scale
- Noise Removal
- Thresholding
- Image Sharpening
- Feature Extraction and Classification
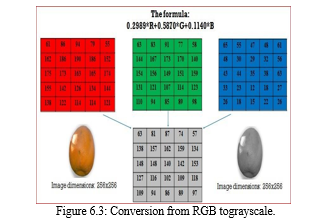
B. Conversion from RGB to Greyscale
The first step in pre-processing is converting the image from RGB to Greyscale. We can be obtained by applying the below formula to the RGB image. The figure 6.4 depicts the Conversion from RGB to grayscale.
Advantages of converting RGB colour space to Gray
To store single colour pixel of an RGB colour image we will need 8*3 = 24 bits (8 bit for each colour component).
only 8 bit is needed to store single pixel of the image. So, we will need 33 % less memory to store grayscale image than to store an RGB image.
Grayscale images are much easier to work within a variety of task like in lots of morphological operation and image segmentation hassle, it’s miles less complicated with single layered image (Grayscale image) than a three-layered image (RGB colour image).
It is also easier to differentiate functions of an image when we deal with a single layered image Noise Removal:
C. Noise Removal
Noise removal is a process of removing or reducing the noise from the image. The noise removal algorithms reduce or remove the visibility of noise through smoothing the whole image leaving regions close to contrast boundaries.
D. Thresholding
Thresholding is a type of image segmentation, where we change each pixel of an image to make the image easier to analyse. Most frequently, we use thresholding as a way to select areas of interest of an image, while ignoring the parts we are not concerned with. We use Otsu Thresholding.
E. Image Sharpening
Image sharpening refers to any enhancement method that highlights edges and best details of an image. Growing yields a greater sharpened image. Image sharpening is done by means of such as to the unique image a signal proportional to a high-pass filtered version of the image.




Conclusion
In conclusion, the implementation of unusual human activity recognition in ATMs holds considerable promise for enhancing security features and safeguarding financial transactions. By leveraging advanced technologies which includes machine learning and computer vision, ATMs can now go beyond traditional security measures to detect and respond to unusual behaviours in real-time.
References
[1] SudhirGoswami, JyotiGoswami, Nagresh Kumar, “Unusual Event Detection in Low Resolution Video for enhancing ATM security”, 2nd International Conference on Signal Processing and Integrated Networks (SPIN), 2015. [2] Saleem Ulla Shariff ; MaheboobHussain ; Mohammed FarhaanShariff, “Smart unusual event detection using low resolution camera for enhanced security”, 2017 International Conference on Innovations in Information, Embedded and Communication Systems (ICIIECS), 17-18 March 2017 [3] Jignesh J. Patoliya ; Miral M. Desai, “Face detection based ATM security system using embedded Linux platform”, 2017 2nd International Conference for Convergence in Technology (I2CT), 7-9 April 2017. [4] SharayuSadashivPhule ; Sharad D. Sawant, “Abnormal activities detection for security purpose un attainded bag and crowding detection by using image processing”, 2017 International Conference on Intelligent Computing and Control Systems (ICICCS), 15-16 June 2017. [5] G. Renee Jebaline, S. Gomathi, “A Novel Method to Enhance the Security of ATM using Biometrics,” 2015 International Conference on Circuit, Power and Computing Technologies [ICCPCT] 978-1-4799- 70759/15/$31.00 ©2015 IEEE. [6] Vikas Tripathi, Durgaprasad Gangodkar, Vivek Latta, and Ankush Mittal, “Robust Abnormal Event Recognition via Motion and ShapeAnalysis at ATM Installations”, Journal of Electrical and Computer Engineering, Volume 2015. [7] S.Shriram, Swastik B.Shetty, Vishnuprasad P. Hegde , KCR Nisha, Dharmambal V , “ Smart ATM Surveillance System”, 2016 International Conference on Circuit, Power and Computing Technologies [ICCPCT]
Copyright
Copyright © 2024 Dr Jagadeesha R, Harish A N, Pooja Shree R. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET61792
Publish Date : 2024-05-08
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

