Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Analysis of Women Safety in Indian Cities Using Machine Learning
Authors: Dr. G. Ravi Kumar, K. Venkata Giridhar, M. Vaishnavi, N Yesumani
DOI Link: https://doi.org/10.22214/ijraset.2024.59199
Certificate: View Certificate
Abstract
In later times, ladies have been confronting an disturbing rise in viciousness, counting badgering, totally different cities. This frequently starts with stalking and can raise into injurious ambush. In this dialog, we are centering with in the area of social media stages like Twitters, FB, and Insta at advancing the security of ladies in India. These stages give a chance at raise mindfulness and teach individuals approximately taking unequivocal activities against damaging behavior. By utilizing hashtags and spreading messages all inclusive, ladies are enabled to openly express their conclusions and feelings. This empowers us to pick up experiences into their state of intellect while ladies out for working or travel, utilizing open transportation, or within the nearness of new people. It makes a difference us decide whether they feel secure or not in these circumstances.These times, badgering and other shapes of savagery against ladies are common in numerous cities! Stalking is the primary step towards injurious badgering, which is now and then alluded to as manhandle attack? With specific reference to the utilization of various social media stages, counting Twitter, Facebook, and Instagram, our essential center in this consider at with in the task with social media in advancing women\'s security in India. This exposition moreover emphasizes the require for common individuals to assume more duty in several Indian city neighborhoods in arrange to ensure the security of ladies in their quick region. Inside the Twitter app, a tweet comprises content messages, photographs, recordings, sound records, emoticons, and hashtags! These regions, require more consideration in regards with women\'s security, and communal engagement is crucial for improvement.
Introduction
I. INTRODCUTION
In These Advanced times, bullying and other shapes of brutality against women are common in various cities and all over the world. Stalking is the essential step towards harmful bullying, which is presently and after that implied to as abuse assault. With particular reference to the utilization of different social media stages, checking Twitter Tweets, Facebook and Instagram posts, our fundamental center in this consider is on the work of social media Information in progressing women's security in India. This piece in addition emphasizes the require for common people to expect more obligation in a few Indian city neighborhoods in orchestrate to guarantee the security of women in their speedy locale. Interior the Twitter app, The Tweets comprises of substance messages, photos, recordings, sound records, emoticons, and hashtags. These locales, require more thought in terms of women's security, and communal engagement is vital for enhancement. Opposite to common convictions, women have the proper to feel secure, though utilizing social media stages and have to be be secured from Cyber threats. The government's part it to stay in most extreme centrality in actualizing strict laws to ensure the online security with lady at these times. Furthermore, the cooperation of non- profit organizations is imperative to create social mindfulness on these issues and offer back to casualties of online viciousness and badgering towards woman.The progression of social media has driven to both positive and negative impacts in society, especially concerning women's safety. In conclusion, collaboration among government, non profit organizations, and people is vital in making a more secure environment for ladies in India through analyzing the information like messages through Twitter organize with the assistance of a few computerized strategies like wistful investigation, Normal Dialect Preparing at that point Actualizing and processing them with the assistance of Different algorithms like For case XGBoosting Machine Learning Calculation.To Extent quick preparing time and Tall exactness, it is signify to select calculation.
II. LITERATURE SURVEY
- Apoorva Agarwal, Fadi Biadsy and KathleenR. Mckeown: Within the cutting edge day, Twitter has risen as a communal microblogging arrange that can match other shapes of media. As individuals connected, they watch hundreds of millions of stoners and create over 5 hundred carefully on open media stages like FB and millions of "Tweets" each day. One way to degree the Twitter social framework is as a smooth way to memorize almost people's suppositions.
- Barbosa, L., & Feng, J:In this paper, we propose a 2- step opinion examination classification strategy for Twitter, which to begin with classifies messages as subjective and objective, and encourage recognizes the subjective tweets as positive or negative. To diminish the labeling exertion in making these classifiers, instep of utilizing physically explained information to compose the preparing information, as normal administered learning approaches, we use sources of boisterous names as our preparing information. These loud names were given by many assumption location websites over twitter information. To superior utilize these sources, we confirm the potential esteem of utilizing and combining them, giving an investigation of the given names, look at diverse methodologies of combining these sources in arrange to get the finest result; and, propose a more vigorous include set that captures a a lot of theoretical showing of tweet, composed by meta-information related to words and particular characteristic with what tweet can be composed. By utilizing it, we point to handle way better: the issue of need of data on tweets, making a difference on the generalization prepare of the classification calculations; and the loud and one-sided names given by those websites.
- Gupta, B. ,Negi, M. ,Vishwakarma, K. ,Rawat, G., Badhani, P.: Twitter has developed as a major micro blogging site, having over 100 million clients creating over 500 million tweets each day. With such huge gathering of people, Twitter has reliably pulled in clients to communicate their conclusions and point of view almost any issue, brand, company orelse various different point of intrigued. Due to this reason, Twitter is utilized as an enlightening source by numerous organizations, educate and companies. On Twitter, clients are permitted to share their conclusions within the shape of tweets, utilizing as it were 140 characters. This leads to individuals compacting their explanations by using slang, shortened forms, emoticons, brief shapes etc. In conjunction with this, individuals pass on their conclusions by utilizing mockery and polysemy.
- Mamgain,N., Mehta,E., Mital,A., & Bhat, G: In today's world, conclusions and reviews accessible to us are one of the most basic components in defining our sees and impacting the success of a brand, item or benefit. With the coming and growth of social media within the world, partners regularly take to expressing their conclusions on prevalent social media, to be specific Twitter. Whereas Twitter information is greatly instructive, it presents a challenge for investigation since of its humongous and disorganized nature. This paper may be a intensive exertion to plunge into novels space of perform the sentimental analysis of audience suppositions as respecting to the beat collage in Indian. Other than taking extra preprocessing measures just like the extension of Netlingo & expulsion of copy information, a probabilitys show based on the Bayes hypothesis was utilized for spelling adjustment, which is neglected in other investigate ponders. This paper moreover highlightning a difference of the comes about gotten by misusing the taking after machine learning calculations: Naïve Bayes and Bolster Vector Machine and an Fake Neural Organize show: Multilayer Perceptron. Besides, a differentiate has been displayed between four diverse parts of SVM: RBF, straight, polynomial and sigmoid.
- Sahayak, V., Shete, V., & Pathan, A: Twitter site is the popular small scale blogging administrations where client can study and post messages which are 148 characters in length. Twitter messages are also called as Tweets. We are going utilize these tweets as crude information. We'll utilize a strategy that consequently extricates tweets into positive, negative or unbiased assumptions. By utilizing the assumption investigation the client can know the criticism almost the item or administrations some time recently making a buy. The company can utilize assumption investigation to know the supposition of clients approximately their items, with it we are able to analyze client fulfillment and concurring to with they are able to process the item. Estimation examination has gotten to be one of well known inquire about zone in computational phonetics, since of the blast of assumption data from social web locales (i.e., Twitter and Facebook), online gatherings, and blogs as in paper.
- Charniak, E., & Johnson, M: Twitter could be a stage broadly utilized by individuals to precise their suppositions and show opinions on diverse events. Estimation examination which is approaching with analyzing information & recover idea that with epitomizes. Twitter estimation investigation which an advantage with assumption investigation on information through Twitters(tweeting), with arrange to extricate opinions passed on by the client. Within the previous times, as investigate with the work was reliably developed. The reasons below at this can be the challenging arrange with the tweet which make the handling troublesome.
- Kim, S. M., & Hovy, E: Distinguishing assumptions (the full of feeling parts of conclusions) may be a challenging issue. We display a framework that, given a theme, naturally finds the individuals who hold conclusions around that theme and the assumption of each supposition. The framework contains a module for deciding word estimation and another for combining opinions inside a sentence. We explore with different models of classifying and combining assumption at word and sentence levels, with promising comes about.
III. RELATED WORKS
In the quest for innovation and efficiency, modern projects frequently rely on existing solutions as fundamental building blocks for development. That method doesnt only reminds the expertise and advancements of those who came before us but also nurtures a collaborative ecosystem where ideas can evolve and confront new challenges. In our project, we wholeheartedly embrace this ethos, conscientiously integrating elements from existing solutions to enrich our endeavor. These existing solutions serve as guiding lights, offering insights and frameworks that shape the direction of our project.
A. NLP(Natural Language Processing)
Computational methods are exceptionally associated in Ordinary Lingo Taking care of (NLP) to assessment, get, and make information on human lingos. It incorporates a large values with errands like machine interpretation, named substance assertion, doubt testing, and substanance classification. NLP calculations distill structure and meaning from substance data by applying neural frameworks, quantifiable models, and etymlogical rules. Its livelihoods consolidate a wide amplify of zones, checking chatbots, virtual arsssitstants, data recovery systems, and estimation testing devices, progressing robotized planning and tongue comprehension!
B. A. Sentimental Analysis
The tweets picked up from Twitter API given by Twitter itself. With the nearness of Twitter API, its has number of methods available for wistful examination of information on social media. A few accessible libraries were utilized in this venture. Here's how to extricate feelings from a tweet:
- Beginning with downloading the thoughtful word reference
- In it the position download the Twitter testing enlightening collections and include them as a commitment to the program.
- Clean tweets by dispensing with the halt words and repetitive letters.
- Tokenize each word and apportion solidarity to the words within the dataset and bolster it to the program.
- For each word, differentiate it and positive conclusions and negative sentiments word reference and a short time later increment the great tally or critical number of the common expression.
- At long last, given the positive check and negative tally, the result rate around feeling to conclude the limit which is orchestrated in Great, Critical, and Fair-minded. Engineers have done diverse wistful investigations .
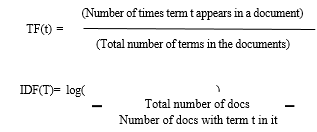
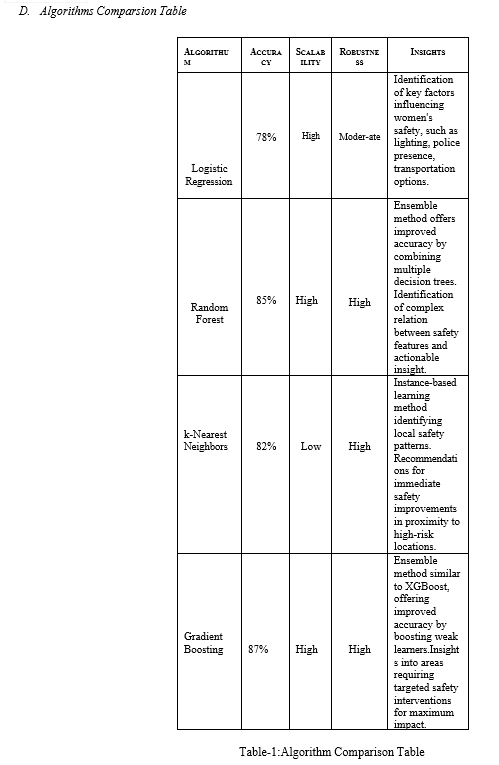
C. XGBoosting Algoritum
Extraordinary Angle Boosting, or XGBoost for brief, could be a effective machine learning strategy that exceeds expectations at taking care of both organized and unstructured information. It is based on the slope boosting design and finds utilize in gathering learning procedures. The adaptability of the approach makes it fitting for dealing with expansive datasets, and regularization procedures are coordinates into the calculation to anticipate overfitting issues. Iteratively progressing expectation precision, XGBoost makes utilize of an gathering of choice trees. Due to its flexibility and steadfastness, it has been broadly utilized for a assortment of ML applications, counting relapse, positioning examination, and classification.
- Step1: Pre-processing.
- Step2: Features extraction utilizing counting vectorization, word level TF-IDF and n-gram levelTF-IDF. Then Converting the Text into Vectors.
3. Step3: Fit the training dataset, it learns the model
4. Step4: XGBoosting classifier is utilized to predict the values as the XGBoosting initializtion is done, the accurate calculation of the model will be done inlcuding all the three vectorization techniques.
IV. METHODOLOGY
Within the Estimation Investigation the taking after steps are major to distinguish the positive, negative or unbiased of the twitter post.
They are:
- Collecting the Dataset: The information is assembled from the twitter utilizing API. Application program interface (API) is utilized to accumulate the information. Twitter site could be a source which comprises of clients tweets.

2. Pre-Processing the Data-set: In Information Pre- processing evacuating boisterous, disconnected information, inconsistent and incomplete info from dataset. For the most part, in twitter we have to be evacuate URLs, extraordinary characters, Re-tweets, hash labels.
3. Feature Extraction: In this work, we utilized Sack of Words to extricate highlights from content archives. After extraction, these highlights used at training the ML calculations. It makes a language of the clear large number of novel words happening in all the reports within the arrangement set. Sack of words highlights containing term frequencies of each word in each record, i.e. the number of event and not sequence or arrange of words things. This will be done by Tally Vectorizer strategy in Python.
4. Classification: A classification issue is associated within the occasion that the abandon variable may be a title or category,in our work “Positive” or “Negative”.
V. PROPOSED SYSTEM
The method known as "Sentimental Analysis CLASSIFICATION" reports the tweets that are chosen and given by the Twitter program. According to the existence of the Twitter app, there are a few strategies accessible for emotive investigation of social media information.
- A Downturn in Exchange The crevice between the genuine and sad commerce charts is decreased when a social organize demonstrate makes a G-graph.
- A commerce chart is developed, and substances and their connections in social mass media are associated.
- The chart appears the likelihood with regard to different topics. Individuals tend to utilize diverse terms and a prepared collection of information that includes condensation since Twitter contains tweets that are unbiased, negative, and positive in expansion to the brief handbooks.
- Agreeing to advanced NLP, these prompts are touchy sufficient to esteem their sentiments.
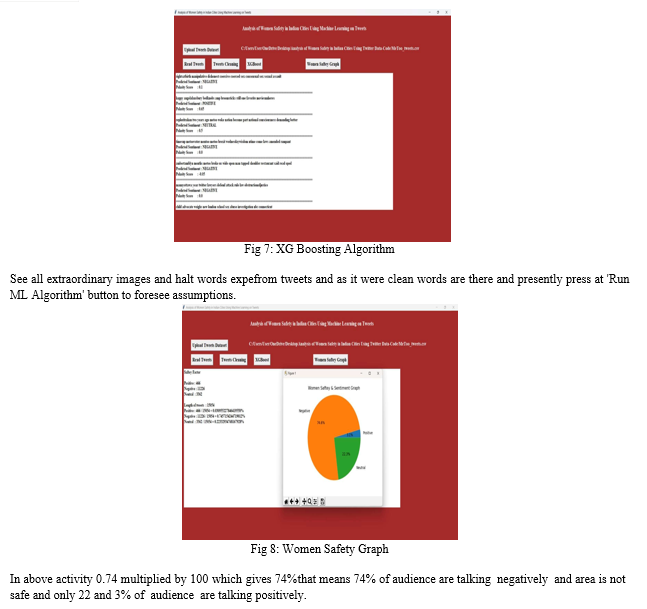
This expansion proposes a strategy for evaluating women's security through the examination of social media organizing messages, particularly tweets almost women's security issues gotten through the utilize of the MEETOO hashtag.
The Characteristic Tongue Gadget Pack (NLTK) and the Python programming tongue will be utilized to assemble and plan tweets in arrange to extricate pivotal information. The estimation and substance of the tweets will be assessed utilizing the XG Boost calculation, which is well-known for its capacity to handle both organized and unstructured information.
Extraordinary Angle Boosting, or XGBoost for brief, will be a effective machine learning strategy that exceeds expectations at taking care of both organized and unstructured information. It is related up on slope boosting design and finds utilize in gathering learning procedures. The adaptability of the approach makes it fitting for dealing with expansive datasets, and regularization procedures are coordinates into the calculation to anticipate overfitting issues. Iteratively progressing expectation precision, XGBoost makes utilize of an gathering of choice trees. Due to its flexibility and steadfastness, it can be used for a assortment of ML applications, counting relapse, positioning examination, and classification.


Conclusion
All through the term sheet we utilize examined almost various ML calculations which could offer assistance to organizing and analyzing the colossal sum of Tweeting information gotten counting huge number of Texts and content messages shared each cycle. This ML calculations are exceptionally compelling and valuable as it arrives to analysis with expansive sum of info include with SPC calculation and direct logarithmic Calculate Show approaches which offer assistance to assist categorize the information into significant bunches. Back VM with however another shape at ML calculation that\'s exceptionally prevalent in extricating Valuable data through the Tweeting and receive a thought around at stats of ladies security in India.
References
[1] Apoorv Agarwal, Fadi Biadsy,and Kathleen R. Mckeown. \"Contextual phrase-level polarity analysis using lexical affect scoring and syntactic n-grams.\" Proceedings of 12th Conference of European Chapter of the Association for Computational Linguistics. Association for the Computational Linguistics, 2009. [2] Barbosa, L., & Feng, J. (2010, August). Robusted sentimental detection on twitter from biased and noisy data. In Coling 2010: Posters (pp. 36-44). [3] Gupta, B., Negi, M., Vishwakarma, K., Rawat, G., Badhani, P., & Tech, B. (2017). Study for Twitter sentiment analysis using ML algorithms on Python. International Journal of Computer Applications, 165(9), 29-34. [4] Mamgain,N., Mehta, E., Mittal, A., & Bhatt, G. (2016, March). Sentimental analyzing of top colleges in India utilizing Twitter data. In 2016 international conference on computational techniques in information and communication technologies (ICCTICT) (pp. 525-530). IEEE. [5] Sahayak, V., Shete, V., & Pathan, A. (2015). Sentiment analysis on twitter data. International Journal of Innovative Research in Advanced Engineering (IJIRAE), 2(1), 178-183. [6] Charniak, E., & Johnson, M. (2005, June). Coarse-to- fine n-best parsing and maxent discriminative reranking. In Proceedings of the 43rd Annual Meeting of the Association for Computational Linguistics (ACL’05) (pp. 173-180). [7] Kim, S. M., & Hovy, E. (2004). Deterninating the sentiments of opinions. In COLING 2004: Proceedings of the 20th International Conference at Computational Linguistics (pp. 1367-1373). [8] Bermingham, A., & Smeaton, A. F. (2010, October). Classifying sentiment in microblogs: is brevity an advantage?. In Proceedings of the 19th ACM international conference on Information and knowledge management (pp. 1833-1836). [9] Klein, D., & Manning, C. D. (2003, July). Accurately unlexicalized parsing. In Proceeding with the 41st annually meeting of the association for computational linguistics (pp. 423-430). [10] Gamon, M. (2004). Sentimental classifications on customers feedback data: noise data, largely feature vectors, and the role of linguistics of analysis. In COLING 2004: Proceeding of 20th international conference on computational linguistics (pp. 841-847).
Copyright
Copyright © 2024 Dr. G. Ravi Kumar, K. Venkata Giridhar, M. Vaishnavi, N Yesumani. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET59199
Publish Date : 2024-03-20
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

