Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Zero Trust Architecture in DevSecOps: Enhancing Security in Cloud-Native Environments
Authors: Ravindra Karanam
DOI Link: https://doi.org/10.22214/ijraset.2024.64045
Certificate: View Certificate
Abstract
This comprehensive article explores the implementation of Zero Trust Architecture (ZTA) within DevSecOps workflows, focusing on its application in cloud-native environments. The research examines the fundamental principles of ZTA, contrasting it with traditional perimeter-centric security models, and delves into its relevance in the context of modern software development practices. By investigating key challenges such as perimeter dissolution, dynamic workloads, and identity complexity, the study provides insights into the obstacles organizations face when adopting ZTA. The article presents a detailed analysis of best practices for ZTA implementation, including continuous monitoring, identity-based access controls, micro-segmentation strategies, and comprehensive encryption policies. Furthermore, it emphasizes the importance of continuous learning and adaptability in maintaining an effective security posture. Through case studies and examination of real-world scenarios, the research highlights successful ZTA implementations and derives valuable lessons for practitioners. The article also explores future directions, considering the potential impact of AI, machine learning, edge computing, and evolving regulatory landscapes on ZTA. By synthesizing current research and industry practices, this article offers a holistic view of ZTA in DevSecOps, providing practitioners and researchers with actionable insights to enhance security in increasingly complex and distributed cloud-native ecosystems.
Introduction
I. INTRODUCTION
The rapid adoption of cloud-native technologies and the increasing complexity of modern software architectures have necessitated a paradigm shift in cybersecurity approaches. Traditional perimeter-based security models are no longer sufficient to protect against sophisticated threats in today's dynamic and distributed environments. Zero Trust Architecture (ZTA) has emerged as a promising framework to address these challenges, particularly within the context of DevSecOps workflows [1]. By eschewing implicit trust and enforcing rigorous authentication and authorization for every access request, ZTA offers a robust security posture that aligns well with the principles of continuous integration and delivery.
This article explores the implementation of Zero Trust principles within DevSecOps practices, focusing on key strategies such as micro-segmentation, identity-based access controls, and continuous monitoring. These approaches not only enhance security but also facilitate the agility and scalability demanded by modern software development processes [2]. As organizations increasingly migrate to cloud-native environments, the integration of ZTA within DevSecOps workflows becomes crucial for protecting critical assets, maintaining compliance, and fostering a culture of security-first development.
II. UNDERSTANDING ZERO TRUST ARCHITECTURE
Zero Trust Architecture (ZTA) is a security model that operates on the principle of "never trust, always verify" [3]. This approach assumes that no entity, whether inside or outside the network perimeter, should be automatically trusted. Core principles of ZTA include continuous authentication and authorization, least privilege access, and micro-segmentation. ZTA aims to secure all data, assets, applications, and services regardless of their location or the network's perceived trustworthiness.
Unlike traditional security models that focus on securing the network perimeter, ZTA acknowledges that modern network boundaries are fluid and often undefined. Traditional models operate on an "trust inside, distrust outside" paradigm, which is inadequate in today's cloud-based, mobile-centric environments. ZTA, in contrast, treats every access request as if it originates from an untrusted network, providing a more robust security posture for distributed systems [4].
A. Key Components of ZTA Include
- Identity and Access Management (IAM)
- Multi-factor Authentication (MFA)
- Micro-segmentation
- Continuous monitoring and analytics
- Policy enforcement points
- Data-centric security controls
These components work together to ensure that access is granted based on the principle of least privilege and that all interactions are authenticated, authorized, and encrypted [3].
|
Aspect |
Traditional Security Model |
Zero Trust Architecture |
|
Trust Assumption |
Trust inside, distrust outside |
Never trust, always verify |
|
Network Perimeter |
Well-defined boundary |
Fluid and often undefined |
|
Access Control |
Based primarily on network location |
Based on identity and context |
|
Authentication |
Often one-time, at the perimeter |
Continuous, for every access request |
|
Segmentation |
Coarse-grained, network-level |
Fine-grained, micro-segmentation |
|
Data Protection |
Focus on perimeter defense |
Data-centric security controls |
|
Adaptability to Cloud |
Limited |
Highly adaptable |
Table 1: Comparison of Traditional Security Model vs. Zero Trust Architecture [3-9]
III. THE DEVSECOPS CONTEXT
DevSecOps is an approach that integrates security practices within the DevOps process, emphasizing security automation and collaboration between development, operations, and security teams. DevSecOps workflows typically involve continuous integration, continuous delivery, and continuous monitoring, with security checks and controls embedded throughout the software development lifecycle [5].
ZTA principles align well with DevSecOps practices, as both emphasize continuous verification and adaptive security measures. The integration of ZTA into DevSecOps workflows can enhance security posture by ensuring that security controls are consistently applied across all environments, from development to production. This intersection promotes a "shift-left" security approach, where security considerations are addressed early in the development process [4].
In cloud-native environments, where applications are built using microservices and containerization, ZTA becomes particularly relevant. The dynamic nature of cloud-native architectures, with their ephemeral resources and distributed systems, aligns well with ZTA's approach to continuous authentication and authorization. ZTA can help secure the complex interactions between microservices, APIs, and data stores that are characteristic of cloud-native applications [5].
IV. COMMON CHALLENGES IN IMPLEMENTING ZTA IN DEVSECOPS
A. Perimeter dissolution in cloud environments
The adoption of cloud services has led to the erosion of traditional network boundaries. This perimeter dissolution makes it challenging to implement security controls and increases the attack surface. ZTA implementation must address the complexities of securing resources across multiple cloud providers and hybrid environments [6].
B. Dynamic Workloads and Microservices
Cloud-native applications often utilize dynamic workloads and microservices architectures. The ephemeral nature of these components and their frequent scaling and updates pose challenges for implementing consistent security policies. ZTA must be flexible enough to accommodate these dynamic environments while maintaining robust security controls [5].
C. Identity complexity and Management
In a DevSecOps context, managing identities for both human users and non-human entities (such as service accounts and APIs) becomes increasingly complex. Implementing ZTA requires sophisticated identity and access management systems that can handle this complexity while ensuring proper authentication and authorization for all access requests [6].
D. Cultural and Organizational Resistance
Implementing ZTA often requires significant changes to existing security practices and organizational culture. There may be resistance from teams accustomed to traditional security models or concerns about potential impacts on productivity. Overcoming this resistance requires clear communication, training, and demonstrating the value of ZTA in enhancing overall security posture [4].
V. BEST PRACTICES FOR ZTA IMPLEMENTATION IN DEVSECOPS
A. Continuous Monitoring and Visibility
1) Tools and Techniques
Implementing ZTA requires robust monitoring tools that provide real-time visibility into network traffic, user activities, and system behaviors. Security Information and Event Management (SIEM) systems, Network Detection and Response (NDR) tools, and User and Entity Behavior Analytics (UEBA) platforms are essential for maintaining comprehensive visibility [7]. These tools should be capable of collecting and analyzing data from various sources, including cloud services, on-premises infrastructure, and endpoint devices.
2) Integration with existing workflows
To effectively implement continuous monitoring in DevSecOps workflows, security tools must be integrated into existing CI/CD pipelines. This integration allows for automated security checks at every stage of the development process. For instance, vulnerability scanners can be incorporated into build processes, while compliance checks can be automated as part of deployment procedures [8].
B. Identity-based access controls
1) Role-based access control (RBAC)
RBAC is a fundamental component of ZTA, allowing organizations to define and manage user permissions based on their roles within the organization. In a DevSecOps context, RBAC should be implemented across all environments, from development to production, ensuring that users have only the necessary access to perform their duties [9].
2) Attribute-based access control (ABAC)
ABAC extends the capabilities of RBAC by considering additional attributes such as time, location, and device type when making access decisions. This granular approach to access control is particularly valuable in cloud-native environments where context can change rapidly [9].
C. Micro-segmentation Strategies
1) Network Segmentation
Network micro-segmentation involves dividing the network into small, isolated segments to limit lateral movement in case of a breach. In cloud environments, this can be achieved through virtual network segmentation and software-defined networking (SDN) technologies [10].
2) Application-level Segmentation
Application-level micro-segmentation focuses on isolating individual application components and services. This approach is particularly relevant in microservices architectures, where it can help contain potential security breaches and minimize the attack surface [10].
D. Encryption Everywhere
1) Data-in-transit Encryption
Ensuring all data in transit is encrypted is crucial for maintaining confidentiality in a ZTA model. This includes using protocols like TLS for web traffic and VPNs for remote access. In DevSecOps workflows, automation tools should be used to enforce and verify encryption policies across all environments [8].
2) Data-at-rest Encryption
Encrypting data at rest protects information stored in databases, file systems, and cloud storage. Implementing robust key management systems and integrating encryption into data storage processes are essential practices in a ZTA approach [8].
|
Component |
Description |
Benefits |
Challenges |
|
Continuous Monitoring |
Real-time visibility into network traffic, user activities, and system behaviors |
Early threat detection, comprehensive security posture |
Integration with existing workflows, data volume management |
|
Identity-based Access Controls |
RBAC and ABAC implementation across all environments |
Granular access control, the principle of least privilege |
Complexity in managing identities, especially in dynamic environments |
|
Micro-segmentation |
Network and application-level isolation |
Limiting lateral movement, reduced attack surface |
Implementing legacy systems, maintaining performance |
|
Encryption Everywhere |
Data-in-transit and data-at-rest encryption |
Protection of sensitive information, compliance with regulations |
Key management, performance overhead |
|
Continuous Learning |
Staying updated on security trends, and ongoing risk assessment |
Adaptive security posture, improved threat response |
Resource allocation, keeping pace with rapid changes |
Table 2: Key Components of ZTA Implementation in DevSecOps [7-10]
VI. CONTINUOUS LEARNING AND ADAPTABILITY
The rapidly evolving threat landscape necessitates continuous learning and adaptation of security practices. DevSecOps teams must stay informed about emerging threats, new attack vectors, and advancements in security technologies to maintain an effective ZTA implementation [7].
A. Industry Blogs and Publications
Regularly reading reputable security blogs, academic journals, and industry publications helps teams stay informed about the latest security trends and best practices.
B. Conferences and Workshops
Attending security conferences and workshops provides opportunities for hands-on learning, networking with peers, and gaining insights from industry experts.
C. Security Communities and Forums
Participating in online security communities and forums facilitates knowledge-sharing and collaborative problem-solving among security professionals.
Implementing a process for ongoing risk assessment and remediation is crucial for maintaining a strong security posture. This involves regular security audits, penetration testing, and vulnerability assessments, with findings integrated into the DevSecOps workflow for rapid remediation [9].
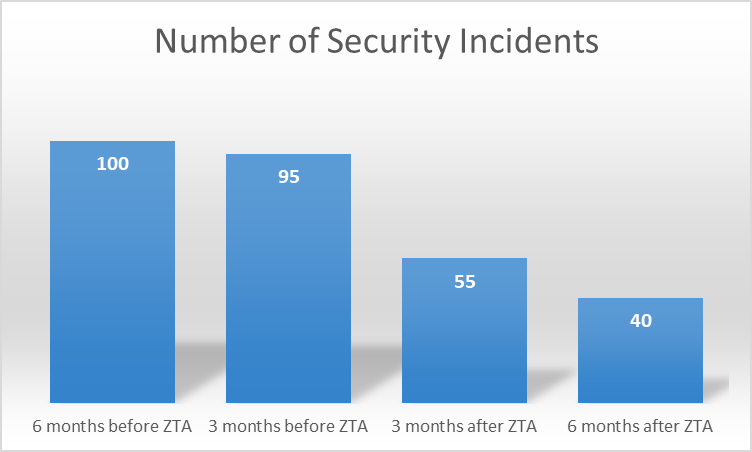
Figure 2: Security Incident Reduction After ZTA Implementation [10]
VII. FUTURE DIRECTIONS AND EMERGING TRENDS
A. AI and Machine Learning in ZTA
AI and machine learning are increasingly being integrated into ZTA solutions to enhance threat detection, automate policy enforcement, and improve the accuracy of access decisions based on behavioral analysis [7].
B. Integration with Emerging Technologies (e.g., edge Computing, 5G)
The adoption of edge computing and 5G networks presents new challenges and opportunities for ZTA implementation. Future ZTA models will need to address the unique security requirements of these distributed, high-performance environments [9].
C. Evolving Regulatory Landscape and Compliance Considerations
As data protection regulations continue to evolve globally, ZTA implementations will need to adapt to ensure compliance with emerging standards while maintaining the agility required in DevSecOps environments [8].
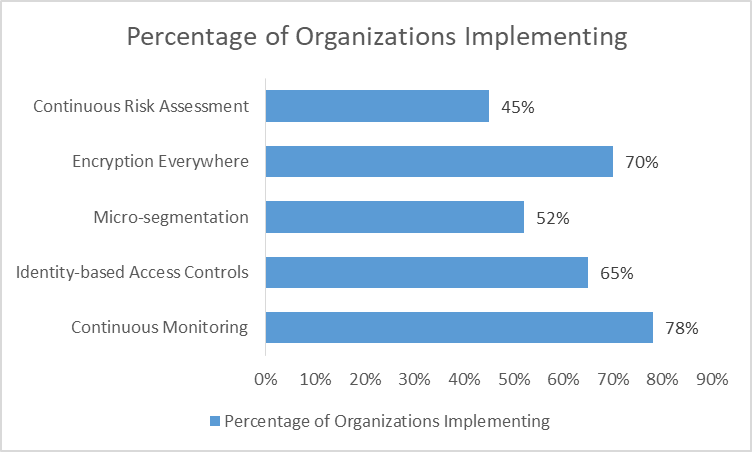
Figure 2: Adoption of Zero Trust Architecture Components in Organizations [7-10]
Conclusion
In conclusion, the integration of Zero Trust Architecture (ZTA) within DevSecOps workflows represents a paradigm shift in securing cloud-native environments. As organizations continue to embrace digital transformation and cloud technologies, the traditional perimeter-based security model becomes increasingly inadequate. ZTA, with its core principles of \"never trust, always verify\" and continuous authentication, offers a robust framework to address the complex security challenges of modern, distributed systems. By implementing best practices such as continuous monitoring, identity-based access controls, micro-segmentation, and ubiquitous encryption, organizations can significantly enhance their security posture. The success of ZTA in DevSecOps hinges on a commitment to continuous learning, adaptability, and a culture of security awareness throughout the organization. As we look to the future, the integration of AI and machine learning, along with the challenges posed by emerging technologies like edge computing and 5G, will further shape the evolution of ZTA. Ultimately, the adoption of ZTA principles in DevSecOps not only strengthens security but also facilitates the agility and innovation necessary for organizations to thrive in an increasingly digital world. As cyber threats continue to evolve, ZTA provides a flexible and resilient approach to security that can adapt to the changing landscape, ensuring that organizations can confidently navigate the complexities of cloud-native development while maintaining robust protection for their critical assets and data.
References
[1] S. Rose et al., \"Zero Trust Architecture,\" NIST Special Publication 800-207, 2020. [2] J. Diogenes and E. Zamora, \"Implementing Zero Trust: The Microsoft Way,\" IEEE Security & Privacy, vol. 19, no. 1, pp. 64-71, 2021. [3] R. Ward and B. Beyer, \"BeyondCorp: A New Approach to Enterprise Security,\" ;login:, vol. 39, no. 6, pp. 6-11, 2014. [Online]. Available: https://research.google/pubs/pub43231/ [4] D. Eidle, S. Y. Ni, C. DeCusatis and A. Sager, \"Autonomic security for zero trust networks,\" 2017 IEEE 8th Annual Ubiquitous Computing, Electronics and Mobile Communication Conference (UEMCON), New York, NY, USA, 2017, pp. 288-293. [Online]. Available: https://ieeexplore.ieee.org/document/8249052 [5] S. Bou-Harb, C. Fachkha, M. Pourzandi, M. Debbabi and C. Assi, \"Communication security for smart grid distribution networks,\" IEEE Communications Magazine, vol. 51, no. 1, pp. 42-49, 2013. [Online]. Available: https://ieeexplore.ieee.org/document/6400437 [6] I. Indu, P. M. R. Anand and V. Bhaskar, \"Identity and access management in cloud environment: Mechanisms and challenges,\" Engineering Science and Technology, an International Journal, vol. 21, no. 4, pp. 574-588, 2018. [Online]. Available: https://www.sciencedirect.com/science/article/pii/S2215098617317750 [7] C. Ngo, P. Membrey, Y. Demchenko and C. de Laat, \"Security Framework for Virtualized Infrastructure in VLAN Environment,\" 2011 IEEE Third International Conference on Cloud Computing Technology and Science, Athens, Greece, 2011, pp. 945-950. [Online]. Available: https://ieeexplore.ieee.org/document/6133234 [8] S. Ransbotham and S. Kude, \"Security Analytics: Having It Both Ways,\" MIT Sloan Management Review, vol. 57, no. 3, pp. 1-5, 2016. [Online]. Available: https://sloanreview.mit.edu/article/security-analytics-having-it-both-ways/ [9] D. Dasgupta, A. Roy and A. Nag, \"Toward the design of adaptive selection strategies for multi-factor authentication,\" Computers & Security, vol. 63, pp. 85-116, 2016. [Online]. Available: https://www.sciencedirect.com/science/article/pii/S0167404816300822 [10] J. V. Pawar and M. A. Anuradha, \"Network security and types of attacks in network,\" Procedia Computer Science, vol. 48, pp. 503-506, 2015. [Online]. Available: https://www.sciencedirect.com/science/article/pii/S1877050915007413
Copyright
Copyright © 2024 Ravindra Karanam. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET64045
Publish Date : 2024-08-22
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

